
A sprawling infostealer malware campaign spanning thirty distinct initiatives, targeting a diverse range of populations and operating systems, has been exposed, linked to the criminal organization “Marko Polo.”
Malicious actors leverage an array of distribution channels, including malvertising, spear phishing, and identity impersonation in online gaming, cryptocurrency, and software spheres, to disseminate a staggering 50 malware payloads, comprising notable strains such as AMOS, Stealc, and Rhadamanthys.
According to Recorded Future’s Insikt Group, which has been tracking the Marko Polo operation, this malware marketing campaign has already affected hundreds and could result in financial losses totaling tens of millions.
Based on the pervasive nature of the Marko Polo marketing campaign, Insikt Group estimates that potentially tens of thousands of devices worldwide may have been compromised, putting at risk sensitive personal and corporate data.
“This raises significant concerns about individual privacy and business sustainability.” Producings tens of millions of dollars in illicit income, this operation starkly illustrates the devastating financial consequences of such cybercrimes.
Setting high-value traps
The Insikt Group’s research suggests that Marko Polo primarily exploits spear phishing tactics via direct messages on social media platforms to target high-value individuals, including cryptocurrency influencers, avid gamers, software developers, and others likely to handle valuable information or assets?
Victims are duped into installing malware by engaging with seemingly legitimate job opportunities or collaborative missions that have been cleverly disguised to deceive them.
Manufacturers impersonating brands include Fortnite (gaming), Get Together Icon (gaming), RuneScape (gaming), Rise Online World (gaming), Zoom (productivity), and PeerMe (cryptocurrency).
Marko Polo leverages proprietary brands unrelated to existing endeavors, including Vortax/Vorion and VDeck (assembling software), Wasper and PDFUnity (cooperation platforms), SpectraRoom (cryptographic communication), and NightVerse (web3 game).
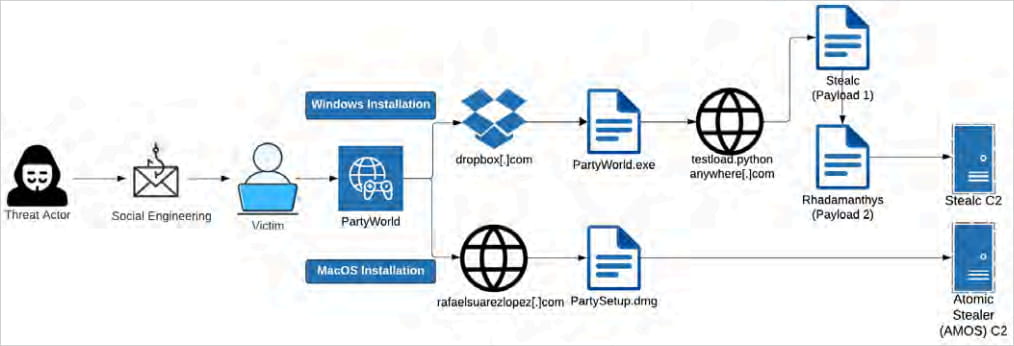
Victims may be lured to fake online platforms purporting to offer digital interactions, gaming, or socializing opportunities, which actually serve as vectors for malware distribution. Various malicious campaigns disperse malware through executable files (.exe or .dmg) embedded in torrent content.
Hitting Windows and macOS
Marco Polo’s toolkit is versatile, showcasing the threat actor’s ability to withstand a multitude of platform-agnostic and vector-based attacks.
On Windows, HijackLoader is employed for exfiltrating sensitive data, a lightweight info-stealer designed to harvest information from web browsers and cryptocurrency wallet applications, or a more specialized variant that targets a wide range of programs and data types.
In a recent update, Rhadamanthys incorporated a malicious clipper plugin that enables diversion of cryptocurrency funds to attacker-controlled wallets, enhances capability to delete Google Account cookies, and facilitates evasive maneuvers against Windows Defender detection.
When using macOS, Marko Polo employs AMOS. The malicious stealer, launched in mid-2023, was reportedly made available for rent by cybercriminals at a monthly rate of $1,000, allowing its operators to extract diverse data stored in internet browsers.
A malicious actor using the AMOS exploit may potentially force-brute MetaMask seed phrases, subsequently gaining unauthorized access to sensitive data stored within Apple’s Keychain feature, including WiFi passwords, saved login credentials, bank card information, and other securely encrypted data residing on macOS devices.
Malicious cyber campaigns that involve the deployment of information-stealing malware have made significant strides in recent years. The malicious actors behind these threats are now targeting victims through a range of vectors, including phishing emails, social engineering tactics, and exploiting vulnerabilities in software applications.
These stolen credentials are subsequently exploited to conduct information theft campaigns, as exemplified by the notable case of a major company, and trigger chaos by orchestrating unprecedented cyber attacks.
To safeguard against the risk of infostealer malware infection, exercise caution when interacting with unknown links and only download software from its official source websites to maintain system security.
The malware used by Marco Polo is detectable by most contemporary antivirus software programs, thus, prior to execution, scanning downloaded content can effectively disrupt the infection process before it begins.

