
Picture: Shutterstock.
And the satellite-based broadband service provider has recently taken steps to address concerns about the potential safety and privacy implications of its geo-location practices for user devices, following new analysis on this issue. Researchers claim that by leveraging publicly available information from Apple, including data on billions of devices globally, including non-Apple units like Starlink programs, they were able to track the destruction of Gaza as well as the actions and, in many cases, identities of Russian and Ukrainian troops?
The issue lies in how Apple aggregates and freely disseminates information regarding the precise location of every Wi-Fi access point detected by its devices. Apple leverages this location data to provide its devices with a crowd-sourced, power-efficient alternative to continuously seeking Global Positioning System (GPS) coordinates.
Devices like each Apple and other smartphones possess a unique Wi-Fi Preferred Setting (WPS) that collects specific hardware identifiers from all nearby wireless access points within their cellular devices’ range. Every document the MAC address tackles, that is, each WiFi entry-level device uses, commonly referred to as an Access Point or Router.
Occasionally, Apple and Google’s cellular devices proactively adjust their locations through GPS queries or utilize nearby mobile towers and BSSIDs as reference points. The combination of data enables Apple and Google entities to pinpoint their location within mere feet or meters, thereby allowing mobile phones to continue displaying intended routes even when GPS signals are unavailable.
Using Google’s WPS, a WiFi device sends a list of nearby Wi-Fi access points’ BSSID identifiers and signal strengths via an API request to Google, which then returns the device’s estimated location. Google’s Wi-Fi Positioning System (WPS) necessitates at least two Basic Service Set Identifiers (BSSIDs) to estimate the location of a device with reasonable accuracy.
Apple’s Wi-Fi-based Positioning System (WPS) can also accept a list of nearby BSSIDs. Instead of calculating the device’s location by analyzing the detected access points and their received signal strengths and then providing the result to the user, Apple’s API simply returns the available nearby wireless networks. Using approximately eight distinctive BSSIDs, the system determines an individual’s location primarily through the recognition of notable landmarks.
Google’s WPS calculates a user’s location and broadcasts it to connected devices. Apple’s Wireless Precise Positioning System (WPS) supplies its devices with a substantial amount of data regarding the locations of recognized entry points, allowing them to perform their own estimation calculations.
Researchers at the University of Maryland have posited that Apple’s APIs, characterized by their verbosity, could be leveraged to track the movement of individual entities across almost any defined geographic space. The University of Maryland team disclosed that they devoted an entire month to initial API experimentation, submitting over a billion randomly generated BSSIDs to test the system’s placement capabilities.
While analyzing the vast array of randomly generated BSSIDs, researchers found that a mere three million of these unique identifiers have been acknowledged by Apple’s Wi-Fi geolocation API thus far.
A researcher with a doctorate discovered that they could primarily avoid requesting unassigned BSSIDs by referencing the list of BSSID ranges allocated to specific device manufacturers, thereby minimizing unnecessary scanning and optimizing wireless network utilization. Maintained by the Institute of Electrical and Electronics Engineers (IEEE), the organization that can also sponsor the venue, Rye is scheduled to host the UMD analysis presentation at this time.
Between November 2022 and November 2023, a team led by Levin and Rye plotted the areas returned by Apple’s WPS (Wireless Personal Network System) services, revealing a comprehensive global perspective on regions with more than two billion Wi-Fi hotspots. The map verifies geolocated entry points across almost every corner of the globe, with the notable exceptions being most of China, vast tracts of central Australian and African deserts, and dense rainforest regions of South America.
The following heatmap visualizes the BSSIDs identified by the University of Maryland crew through a random guessing exercise.
By geofencing specific, smaller regions outlined by Apple’s location API, the researchers proposed monitoring how Wi-Fi entry points shifted over time. If a company’s data breach involves millions of customer records being compromised, it could lead to severe financial consequences, including class-action lawsuits and reputational damage. By deploying geofences around Ukraine’s conflict hotspots, authorities were able to pinpoint the location and movement of Starlink terminals used by both Ukrainian and Russian military forces.
The ability to test this stems from the fact that each Starlink terminal, comprising the dish and associated hardware necessary for a customer to access internet services via a constellation of orbiting Starlink satellites, is equipped with its own Wi-Fi router, whose presence will automatically be detected by nearby Apple devices with location services enabled.
The proliferation of Starlink routers across Ukraine: a visual representation of digital connectivity and global reach. Picture: UMD.
The University of Maryland’s Space Analytics Laboratory successfully geo-fenced multiple conflict zones in Ukraine, pinpointing at least 3,722 Starlink satellite terminals deployed within the country’s boundaries.
Researchers uncovered evidence of seemingly autonomous units being deployed by military personnel into combat areas, potentially compromising pre-existing deployment strategies and troop placements. “Our findings also provide insight into the diverse range of countries where individuals who have fled Ukraine have settled, thereby corroborating existing research on the global dispersal of Ukrainian refugees.”
During a conversation with KrebsOnSecurity, the University of Maryland team revealed that their discovery went beyond identifying Russian military pre-deployment websites; they also found that by pinpointing the origin of troop deployments in disputed regions, it became remarkably simple to determine the source of these units.
“This database includes residential addresses from around the globe,” Levin explained. “We’re able to identify individuals who have enlisted with the Ukraine Overseas Legion.”
Simplified maps pinpoint the origins of BSSIDs entering Donbas and Crimea regions of Ukraine. Picture: UMD.
According to Levin and Rye, they disclosed their research to Starlink in March 2024, noting that Starlink revealed it had initiated software upgrades in 2023 aimed at randomizing the Base Station IDs (BSSIDs) of its entry points.
SpaceX declined to comment on Starlink’s parentage. According to the researchers, a recent graphic illustrating their understanding of Starlink’s BSSID monitoring data shows a significant decline in the number of geo-locatable Starlink units via Apple’s API over the past month.
Researchers at UMD have publicly showcased a graphic demonstrating their ability to track the deployment and movement of Starlink satellites using a significant decline in BSSID signal strength over the past month.
The company also disseminated a written confirmation acquired from Starlink, confirming that the initial Starlink Person Terminal routers relied on a static BSSID and MAC address.
In February 2023, a software update was rolled out that introduced randomness to the primary router’s MAC address (BSSID). Subsequent software updates have introduced randomness to the Basic Service Set Identifier (BSSID) of WiFi extenders linked to the primary router, enhancing security and mitigating potential threats. As part of an ongoing effort to enhance overall system reliability, software updates featuring randomized repeater performance enhancements are currently being rolled out across all regions in a phased manner.
The information presented in your paper is based on data collected from Starlink’s primary routers and/or repeaters, which had previously received randomization updates.
Researchers specifically focused on the Israel-Hamas conflict in Gaza, successfully tracking the migration and disappearance of units throughout the Gaza Strip as Israeli forces scaled back efforts and bombing campaigns crippled critical infrastructure, severely impacting daily life and humanitarian response.
As time passed, however, the number of Gazan BSSIDs with geolocation capabilities remained consistently unresponsive. As of the end of the month, only approximately 28 percent of the distinct BSSIDs had been identified within the Apple WPS network.
By late March 2024, Apple had observed that users could opt out of having their WiFi access point identifiers collected and shared by Apple simply by appending “_nomap” to the beginning of their network’s SSID. When setting up a secure Wi-Fi network, consider adding “_nomap” to the community identifier.
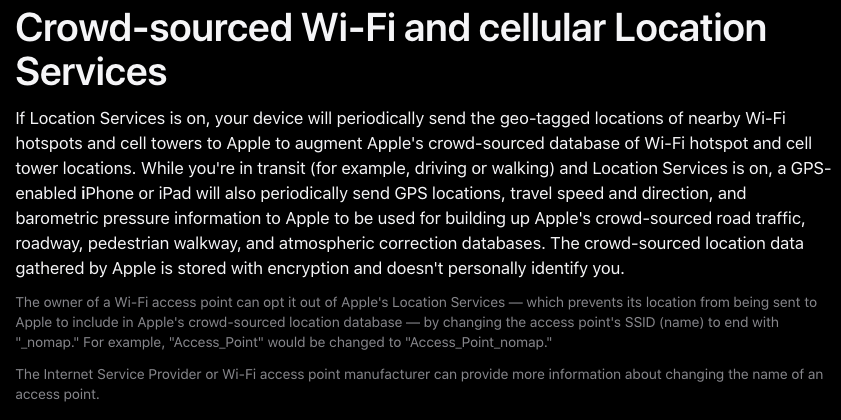
Apple has updated its privacy and network providers policy in March 2024, allowing users to opt-out of having their Wi-Fi network’s SSID listed by its service by appending “_nomap” to the network’s name.
Apple had long reversed the “_nomap” flag on SSIDs, but only explicitly mentioned it in a support article earlier this year.
Rye noted that Apple’s response effectively addressed the most egregious aspect of their criticism: the absence of an opt-out mechanism for users to decline participation in data collection prior to its implementation.
According to him, if you don’t own Apple products but someone nearby possesses one, your Wi-Fi network’s identifier will likely be stored in Apple’s database. “What’s crucial to recognize at this point is that every entry-level user is being monitored, without their consent, regardless of whether they use an Apple device or not.” Only after disclosing this information to Apple did they finally enable users to make their own decisions.
Researchers are calling on Apple to incorporate robust safeguards, including proactive measures to prevent potential abuses of its location API.
“Levin characterized Apple’s privacy update in March as a crucial first step.” However, this knowledge poses a profoundly serious privacy vulnerability. I’d expect Apple to implement stricter controls on API usage, such as limiting query rates, to prevent users from amassing enormous amounts of data.
Researchers at the University of Maryland acknowledged omissions in their study to safeguard the identities of tracked individuals, highlighting potential risks associated with their methods for those fleeing abusive relationships or stalkers?
As devices are relocated between cities and countries, the potential motivations behind these transfers remain unclear, leaving researchers to ponder whether this phenomenon is driven by changes in ownership or strategic business decisions between original and acquiring entities. While there may not be a direct correlation between the number of Wi-Fi routers and customers, some residential routers are designed to serve only a few users. Customers in high-risk situations, such as those escaping domestic abuse or stalking, pose a significant concern: their mere online presence and the fact that their router is connected could potentially reveal their new location.
Researchers argue that Wi-Fi entry points generated by a cellular device’s embedded modem, through the use of a cell phone hotspot, do not pose a location privacy risk to their users because such hotspots automatically choose a randomized BSSID upon activation.
“Trendy Android and iOS devices often default to selecting a random BSSID when activated in hotspot mode,” he noted. Hotspots have already implemented the most robust privacy protection measures. Units that differ in type don’t follow this.
In fact, researchers discovered that widespread use of journey routers tends to exacerbate potential privacy risks.
As a consequence of their nomadic nature, journey routers are frequently employed on campers or boats, leading to a significant diversity of them being transferred between campgrounds, RV parks, and marinas. These services are frequently employed by tourists who move between apartments and hotels during their travels. Evidence exists of military personnel utilizing these devices as they mobilize from residential areas and bases to combat regions.
A duplicate of the University of Maryland’s analysis is available for download as a PDF.
Added response from Apple.

