Scams
Your cellphone number serves as more than just a means of contacting you; it also poses a vulnerability that scammers can exploit. They can target you with malicious messages, potentially gaining access to your bank account or stealing confidential corporate information.

Last month, we explored how scammers operate and the ways in which data breaches and phishing campaigns can facilitate their efforts to acquire sensitive information. Here is the rewritten text:
This blog post delves deeper into the significance of cellphone numbers as valuable targets, and examines the perilous consequences that unfold when they fall prey to compromise.
The $cam trade
Online scammers continuously devise various forms of fraudulent schemes. In recent years, a plethora of illicit operations has emerged, primarily engineered by prison cartels operating in Southeast Asia. These syndicates exploit unsuspecting individuals, forcing them to participate in complex schemes that mimic the tactics of skilled con artists.
Scammers often employ tactics beyond construction fraud, such as manufacturing urgent situations or utilizing various deceptions, including false financial institution claims, fake charities, and AI-powered schemes.
At the core of numerous online scams lies phishing and other malicious attacks. Their success stems primarily from the low-cost and high-reward characteristics of these ventures, coupled with their scalability and potential for growth, despite the added complexity of enforcing cross-border legislation. To justify the costs, a single successful “phish” could be enough to fully repay your entire operation.
Throw me some numbers
Cellphone numbers seamlessly integrate into this scenario, serving as a vital component that enables scammers to achieve their malicious objectives, particularly when combined with other tactics, allowing them to orchestrate sophisticated attacks.
Smishing and hacking
Cybercriminals may deceive you into downloading malware disguised as harmless links or attachments, which can stealthily install spyware, adware, or other malicious software on your device, compromising your personal data and security. Alternatively, scammers may send you messages purporting to authenticate your identity or prompt you to divulge sensitive information, luring you onto phony websites designed to pilfer your login credentials and confidential data.
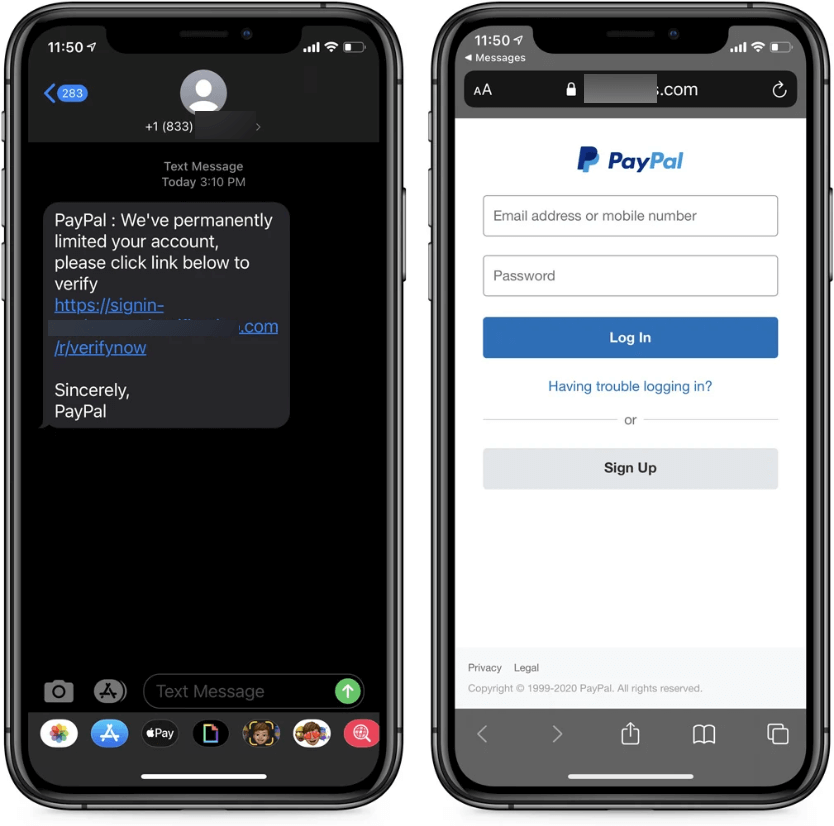
The proliferation of GoldPickaxe malware has been marked by its use of a sophisticated, multi-stage social engineering scheme in its iOS iteration, which lures victims into providing their Cell Machine Administration profile credentials, thereby granting attackers complete control over the affected device’s management.
Name-forwarding scams involve cybercriminals hijacking a victim’s phone number to receive calls and messages intended for the legitimate owner.
Despite the proliferation of digital communication, cellphone calls and messages remain an essential means of personal connection.
- In name-forwarding scams, fraudsters typically initiate contact with either you or your service provider, ultimately diverting phone calls from your cell phone number to a number under their control. While a legitimate supplier may request verification, scammers have potentially gained access to more of your personal information through unknown means, making it easier for them to execute this fraud.
- Fraudsters can deceive your cellular provider into activating a new SIM card with an outdated phone number, thereby successfully porting your number to their device. This scam is significantly more intrusive than porting your number, as you’ll also forfeit access to your cell phone network as a result. For years, SIM swapping has posed a significant threat to individuals, necessitating meticulous analysis of the victim’s life to verify the authenticity of their identity and prevent such attacks.
- Scammers often impersonate your identity using tactics such as VoIP technology or company spoofing, along with various other deceptive strategies. Due to this vulnerability, malicious actors can conceal their identities while perpetuating financial frauds and other illicit activities by impersonating you or a trusted associate.
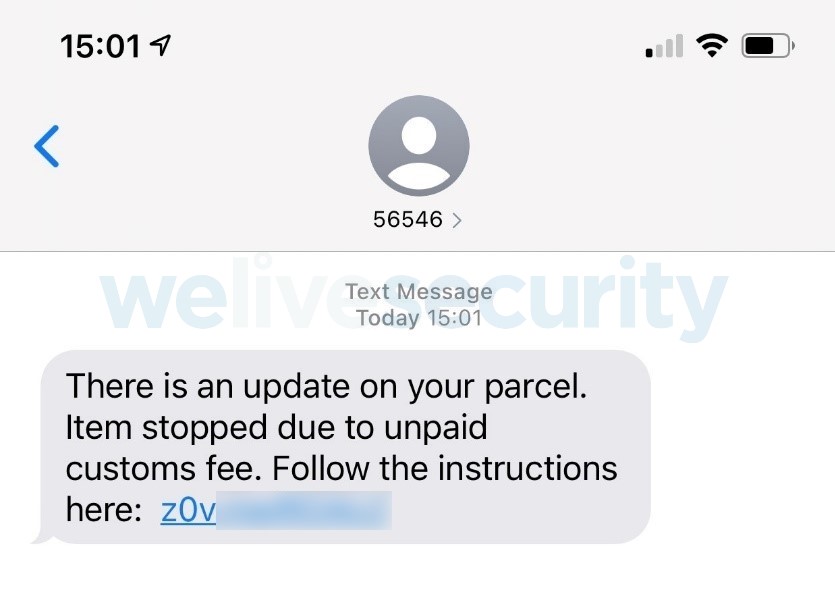
What’s behind the surge in scams that pose significant risks to unsuspecting consumers? Recently, numerous online businesses have come to rely heavily on cellphones as a means of verifying identities and restoring accounts, creating an environment ripe for exploitation. Exceeding the recommended number of devices authorized on your cellphone account can compromise your security and potentially circumvent essential safety measures, including two-factor authentication. Furthermore, scammers may masquerade as you, potentially deceiving your connections and even compromising your professional reputation in the process.
Phishing for company knowledge
As a result, many employees now regularly utilize personal or corporate mobile devices to access and review their work-related emails and communications. While this creates challenges, as computer systems are no longer the sole entry points for attempted compromises. Scammers often assume the identities of corporate executives or accounting departments to solicit cash transfers under the guise of “business” purposes.
Scammers’ ultimate goal is often to gain unauthorized access to a company’s systems and financial resources. While the human element plays a crucial role in these systems, as well. While haste is understandable, we often fail to verify the authenticity of requests before acting on them, creating an open door for sophisticated phishing attacks that can ultimately compromise companies’ security.
CEO fraud
As a financial expert in a leading accounting firm, I would focus on precision and accuracy to ensure timely and compliant reporting. As soon as you receive an unexpected phone call on your cell phone, you find yourself scrambling to respond to an urgent request from your boss, urging you to transfer funds for a crucial business transaction that requires prompt attention. Such scams are . Because the name appears to originate from a high-ranking official, you may hesitate to question its authenticity – and you wouldn’t be the only one thinking that way.
Information related to CEO fraud, a specific type of Business Email Compromise (BEC) fraud, is presented. Currently, AI has amplified the potency of these scams, allowing fraudsters to convincingly impersonate individuals.
In such perilous situations, swift and decisive action is paramount.
Elevating the protection internet
Fortunately, there are just a few simple ways that individuals and companies can protect themselves from cellphone scams.
- When receiving an unsolicited communication, avoid engaging with the sender until their identity is verified. Prior to providing any confidential information, clarify with the requesting party that the inquiry is genuine and obtain explicit consent before proceeding.
- To prevent unwanted SIM swaps and forwarding, request that your service provider lock your account against unauthorized changes using additional security measures to ensure thorough verification checks are performed before any modifications can be made.
- To avoid scammers from accumulating more information about you, consider While impersonation often relies on adopting the persona of someone familiar, it’s actually more effective when the individual limits their public exposure and doesn’t seek to draw attention to themselves?
- To combat fraud effectively, consider replacing SMS-based two-factor authentication with a more secure option: app-based verification. If you don’t use a password manager, crooks may easily compromise your accounts.
- Phishing attacks, whether initiated through messages or phone calls, can often be identified by robust technology. Companies that diversify their supply chains and invest in strategic partnerships may help overcome such threats.
As the conclusion suggests, due to the typical cellphone quantity serving as an entry point for risk actors, it often leads to massive corporate breaches and substantial financial losses in the thousands. While it’s essential to maintain confidentiality, ideally the information should be treated similarly to a unique identifier, ensuring optimal protection.
As phishing remains a pervasive threat, maintain high alertness and remember that verification and authorization are crucial safeguards to ensure your online security.
Why not test your phish-spotting skills in a quick and fun quiz right now?

