A passkey is a specific authentication method that can be used universally like a password but provides additional security features. Passkeys are distinct from passwords in that they combine personal and public cryptographic keys to verify users, whereas traditional passwords rely solely on a specific combination of characters.
In alignment with Google’s pioneering approach, one of the primary benefits of passkeys is their resistance to phishing attacks, eliminating the need for users to memorize complex password combinations featuring numbers and special characters.
As online threats continue to adapt and evolve, consider incorporating passkeys as a proactive measure to bolster the security of your digital assets and sensitive information.
Discovering the art of passkey mastery, this text delves into the intricate mechanics behind its operation, highlighting the paramount importance of leveraging this ingenious security measure to safeguard against potential threats.
What’s a passkey?
A passkey is a code or sequence of characters used for access to a secured system, machine, group, or service, enabling authorized individuals to enter and utilize the restricted area. Passkeys are sometimes used alongside usernames or consumer IDs to authenticate.
Once you’ve set up a passkey, the next step is to complete the authentication process by logging in, which may involve using biometric data such as fingerprints or facial recognition. When individuals rely heavily on passkeys, the login process becomes an effortless, automated routine for them; however, for nefarious entities, it can be a virtually insurmountable barrier to entry.
Passkey implementations offer unparalleled versatility, allowing users to configure them for cloud-based synchronization or hardware-enforced authentication, depending on their preferences regarding software, services, or devices.
How do passkeys work?
Upon initial login, users seeking access to an app or website equipped with password management capabilities are prompted to create a unique passkey. As a secure authentication method, this passkey may soon become a necessary requirement, offering users the flexibility to access it via either biometric or private PIN-based authentication, depending on personal preference and device capabilities.
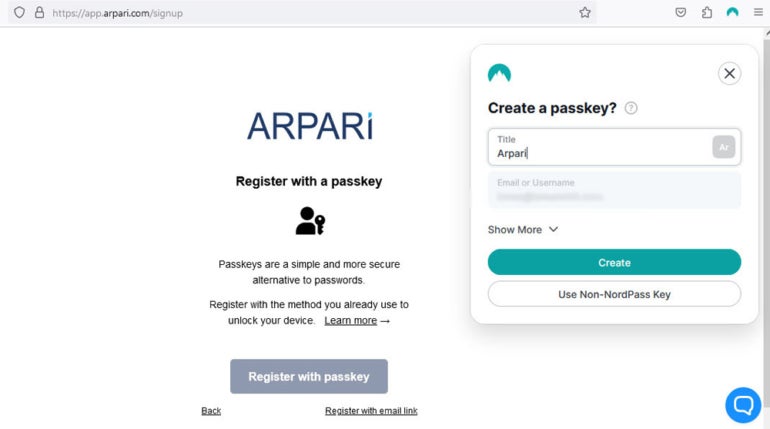
During this stage, two mathematically connected cryptographic keys are generated: a public key, which remains associated with the website, service, or software, tied to the user’s account; and a private key, stored securely on the individual’s hardware or cloud storage.
To register with a passkey instead of a traditional password, start by downloading and installing the passkey software from a reputable provider. Once installed, launch the software and follow the on-screen instructions to create your unique passkey identifier. This identifier will be used to authenticate your identity when logging in or accessing secure resources. Next, navigate to the registration page for the service or platform you want to access, such as an online banking portal or email account. Look for the option to register with a passkey and click on it. You will then be prompted to enter your existing login credentials, followed by your newly created passkey identifier. Confirm your entry and wait for the system to verify your identity before granting access.
With passkey authentication seamlessly executed in the background, consumers enjoy a hassle-free login experience, requiring only a single click to access their account.
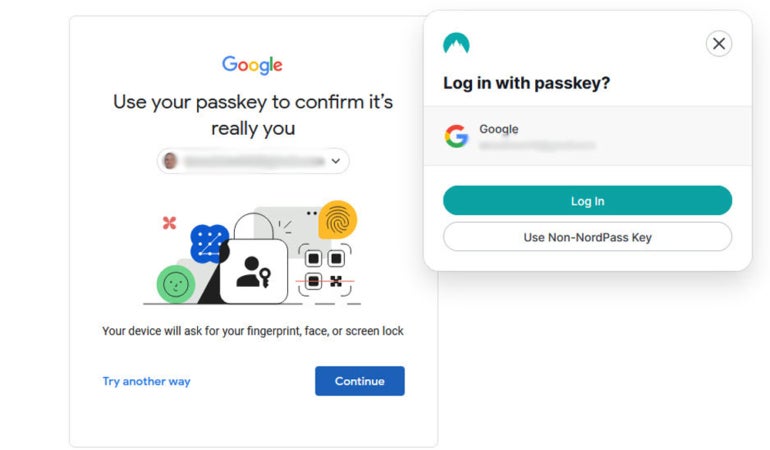
Throughout login sessions, a seemingly authentic “issue” is randomly dispatched to customers’ devices by the service or software, prompting them to authenticate using their unique personal keys upon prompt resolution.
The application or website can confirm the authenticity of the personal key by utilizing its corresponding public key to validate the response. Authentication is successfully validated when a consumer’s verified digital signature, linked to their response, matches the unique, randomly generated challenge. If the signatures do not match, entry is promptly denied.
Passkeys aren’t a new name for traditional passwords; they’re fundamentally distinct in their design and usage. Unlike passwords that require users to memorize and enter complex strings of characters, passkeys leverage existing biometric authentication methods like fingerprints or facial recognition. This shift eliminates the need for users to create and manage separate passphrases, reducing friction and increasing security.
The key differences between passkeys and passwords lie in:
- Passwords may fall victim to illicit acquisition through brute-force attacks, social manipulation, or compromised knowledge, whereas the security of passkeys is significantly more challenging to breach, although not entirely impossible. Hackers might attempt to physically steal your device or gain unauthorized access to your cloud storage by cracking your PIN code or circumventing the biometric authentication mechanism.
- Effective password management necessitates that customers create and securely store multiple complex credentials or utilize a reputable password manager, although this approach poses its own set of challenges and vulnerabilities. Passkey robots seamlessly authenticate customers via their device’s built-in unlocking mechanisms, simplifying and streamlining the process for effortless access.
- Passwords can be used across any device without additional setup; however, passkeys are typically limited to specific hardware. While cloud-based passkeys can span multiple units, customers should be aware that their personal keys will likely be stored on someone else’s servers instead of locally.
The utilization of a passkey offers several benefits, including enhanced security, streamlined authentication processes, and increased accessibility. By employing a unique access code, organizations can safeguard sensitive information from unauthorized entry, thereby minimizing the risk of data breaches and cyber attacks. Additionally, passkeys simplify the sign-in process for users, eliminating the need to memorize complex passwords or manage multiple login credentials.
- When an individual uses the same password repeatedly to access a particular account, they inadvertently create a vulnerability that can be exploited by cybercriminals. If such a password falls into the wrong hands, the attacker gains unrestricted access. Passkeys leverage cryptographic key pair expertise to generate unique authentication credentials per login, rendering hackers powerless to guess or pilfer sensitive information. Passkeys offer robust security against brute-force attacks and phishing attempts, remaining unexposed even in the event of a data breach.
- Passkeys leverage your device’s authenticator, akin to a biometric login or PIN code, providing a native two-factor authentication (2FA) safeguard for your account. Regardless of whether your personal secrets are stored locally on your device or in the cloud, any potential hacker would need to first authenticate with your machine before gaining unauthorized access and compromising your account.
- Passkeys eliminate the need for memorization or frequent updates, simplifying the login process by requiring only a single button press, outshining traditional password authentication. Although users enable two-factor authentication (2FA) to strengthen account security, the system does not insist on additional verification for every individual login; instead, once a user logs in, 2FA remains active for all subsequent account access within the same session.
Bytes.
Numerous devices from top-tier technology manufacturers are compatible with passkeys. The Passkey expertise was developed to ensure seamless compatibility, meeting the stringent demands of major technology players – including Apple, Google, and Microsoft – as well as all leading internet browsers.
Can passkeys be shared?
While the development of passkey expertise remains ongoing, some companies have mooted the possibility of shared credentials among customers – provided that the exact passkeys are securely stored in the cloud and beyond the grasp of would-be hackers. Sharing account entries with household, friends, and colleagues becomes an effortlessly rapid process, thereby elevating the overall user experience through this convenient feature. Despite these concerns, it remains unclear how this feature would be safely implemented within an organizational context.
As companies increasingly rely on cloud providers, it’s crucial they consider relinquishing ownership and management of credential administration to focus on core business functions, acknowledging that a breach in the cloud could have devastating consequences.
Bound passkeys, either hardware-bound or cloud-based, are stored on secure devices such as safety key tokens, physical authentication tokens, or specialized hardware embedded in laptops and desktops. Due to its unique characteristics, the passkey cannot be transferred or duplicated in any way. Hardware-bound passkeys may serve as a viable alternative for companies seeking to prevent employees from duplicating or disseminating keys across departments.
Are passkeys safer than passwords?
Generally, passkeys prove to be more secure than traditional passwords. Despite these factors, their security hinges on multiple variables: the efficacy of cryptographic techniques employed to protect private and public keys, the integrity of the machine’s authenticator, and the reliability of the passphrase response provider.
Customers can take steps to make passkeys even safer. Passkeys leverage your machine’s existing credentials as a secondary form of authentication, thereby enhancing the security of your personal keys when you opt for biometric login instead of relying solely on a PIN. Minimizing your browser’s cookie assortment and regularly clearing cached credentials are effective practices for bolstering overall internet security. Additionally, it is essential to enhance the security of passkeys by incorporating robust safeguards and controls, such as encrypting hard drives, utilizing secure protocols, and configuring robust firewalls.
Can a passkey be hacked?
While passkeys may be vulnerable to hacking, the risk is exponentially higher than compromising a password, due to their inherently complex nature. Passkeys, shielded by multiple layers of protection, combine native machine authentication and robust encryption for secure handling. Purchasing the personal key alone is insufficient, as authenticating with the native machine beforehand remains crucial for accessing online accounts, even when utilizing cloud-based passkey options.
Passkeys could potentially replace traditional passwords for some users, but they’re unlikely to entirely supplant password managers. Passkeys are a type of public key that’s stored securely on devices, eliminating the need for users to memorize or store complex login credentials. However, password managers still offer several advantages: they can generate and remember unique passphrases for each account, provide additional security features like password auditing and breach monitoring, and often include other functionality like digital wallet storage.
As the industry continues to evolve, I predict that passkeys will gradually supplant traditional passwords and password management systems, with the shift currently still in its early stages. As password expertise advances and more companies adopt it, we’ll likely see passwords phased out even among home users.
The way forward for passkeys in expertise lies in seamless integration with existing authentication systems, bolstered by robust security protocols and user-friendly interfaces to ensure widespread adoption.
Currently, most advancements in passkey technology are accurately centered on providing more practical options for developers and organizations to utilize, with the ultimate goal of accelerating widespread adoption.
Currently, passkeys generated within a solitary ecosystem do not seamlessly integrate with those from other platforms. When consumers generate a passkey using their iPhone, it becomes impractical, if not impossible, to apply that same passkey on a Windows laptop or transfer all their passkeys between environments seamlessly.
While this limitation primarily affects native passkey devices found in newer Apple, Windows, and Android environments. As third-party key providers expand into the market, the industry’s focus is shifting towards seamless cross-platform support and effortless portability, ultimately elevating the customer experience.

