We delve into an unconventional phishing marketing strategy targeting mobile subscribers, examining a real-world example of a sophisticated attack aimed at customers of a prominent Czech financial institution. Notably, this system stands out for its ability to install a phishing utility from an external website without requiring user consent or permission for third-party app installation. For iOS users, this move may shatter traditional notions of security within the confines of their mobile ecosystem. On Android devices, this scenario may arise due to the silent installation settings of certain APK types, which are often configured by the Google Play store upon further examination.
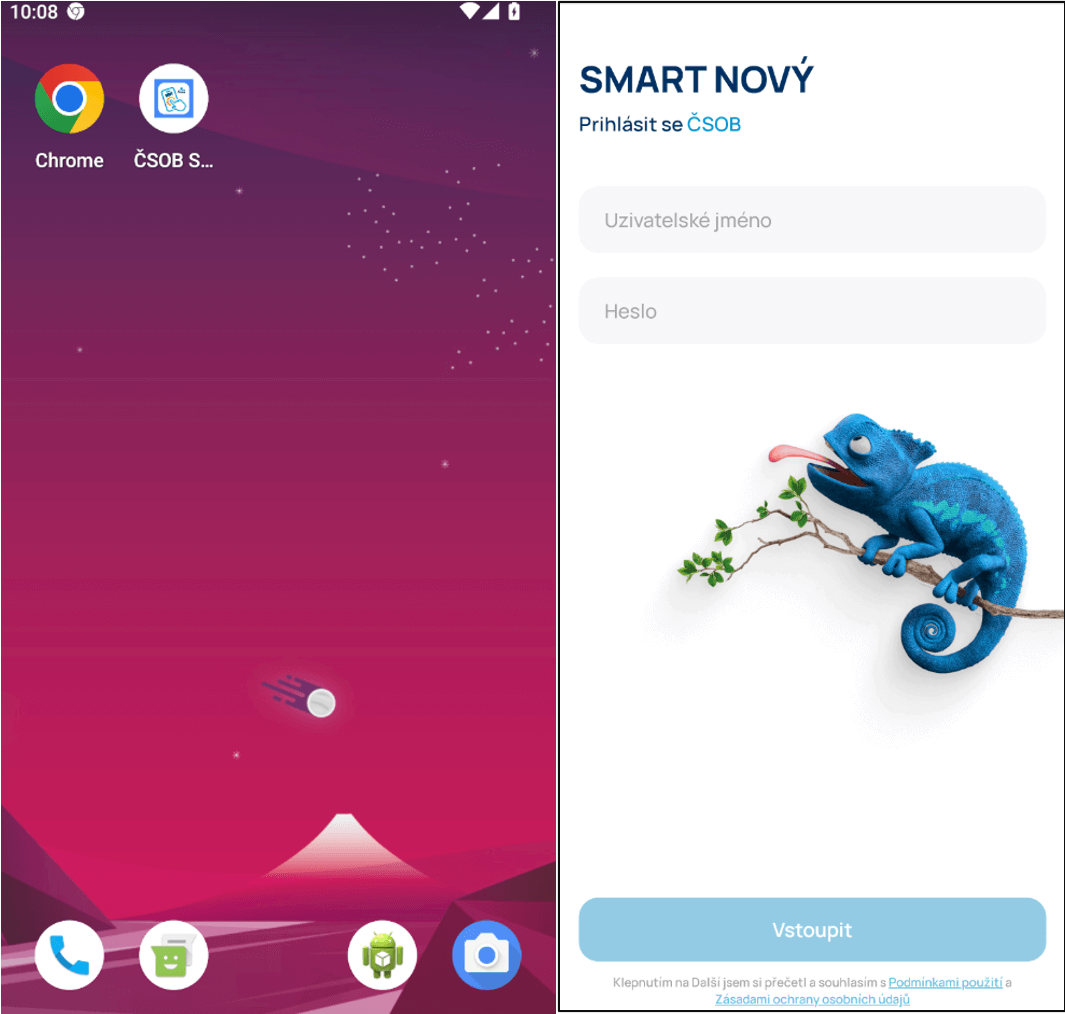
Phishing websites targeting iOS users prompt victims to add a Progressive Web App (PWA) to their home screens, whereas on Android devices, the PWA installation occurs only after users confirm custom prompts within the browser. On this level, the phishing applications masquerading as genuine banking software exhibit a remarkable resemblance to their authentic counterparts, making it increasingly difficult to discern the two. PWAs are primarily web applications that simulate a native experience by bundling website functionality into a standalone utility, further augmented by the use of native system prompts. Pioneering Web Applications (PWAs), indistinguishable from websites, boast a unique characteristic: they are cross-platform, allowing PWA phishing campaigns to effectively target both iOS and Android users.
The malware was first detected in Poland in July 2023, with a second instance identified in November of the same year by ESET analysts utilizing their Model Intelligence service in Czechia. Two instances of cell banking campaigns were detected outside of the Czech Republic, targeting the Hungarian OTP Bank and the Georgian TBC Bank respectively.
- Phishing attacks are evolving by combining traditional tactics with innovative approaches, targeting both Android and iOS users via Progressive Web Apps (PWAs) and Android-specific WebAPKs.
- Without warning, inserting a Progressive Web App (PWA) or Web Application Package (WebAPK) silently installs a third-party application on a user’s device.
- On Android devices, suspicious WebAPKs that appear to be genuine apps distributed through the official Google Play Store have been discovered, raising concerns about potential phishing attacks.
- Notwithstanding notable efforts to target Czech bank customers, our research also uncovered a phishing application targeting a Hungarian financial institution, as well as another aimed at a Georgian financial institution.
- Primarily based on the C&C servers utilized and backend infrastructure, we conclude that two totally different risk actors have been working the campaigns.
- Following the detection of anomalous activity on distinct digital platforms, we were able to promptly inform affected financial institutions to enable proactive measures against potential threats.
Overview
ESET researchers discovered a sophisticated network of phishing attacks targeting mobile users, employing a trio of distinct URL generation methods (illustrated in Figure 1). These mechanisms encompass automated voice calls, SMS messages, and malicious social media advertising.
The automated voice notification alerts users when their banking app is outdated, prompting them to select a numerical option via their phone’s keypad. Upon clicking the suspicious link, a phishing URL is disseminated via SMS. This information was disseminated through a Twitter post.
An initial supply of information via SMS was delivered by broadcasting messages randomly to all Czech mobile phone numbers. A malicious message was sent, containing a fraudulent link and text aimed at tricking recipients into accessing the URL.
Malicious advertisements were disseminated by posting ads on Meta’s platforms, including Instagram and Facebook. These ads featured a call to action, such as a limited offer for customers who “obtain an update below”. The platform allows threat actors to define their target audience based on demographic criteria such as age, gender, and more. Targeted advertisements will subsequently appear in a user’s social media feed.
Upon accessing the URL provided during the initial phase, Android users are presented with a convincingly authentic phishing webpage that masquerades as the genuine Google Play store page for the targeted banking app or a counterfeit site for the device. Two separate marketing initiatives have been undertaken. The marketing campaign may adapt dynamically using Google Play assets, potentially mimicking Apple App Store visuals based on consumer-agent data acquisition. It appears that we did not detect this approach in our investigated cases.
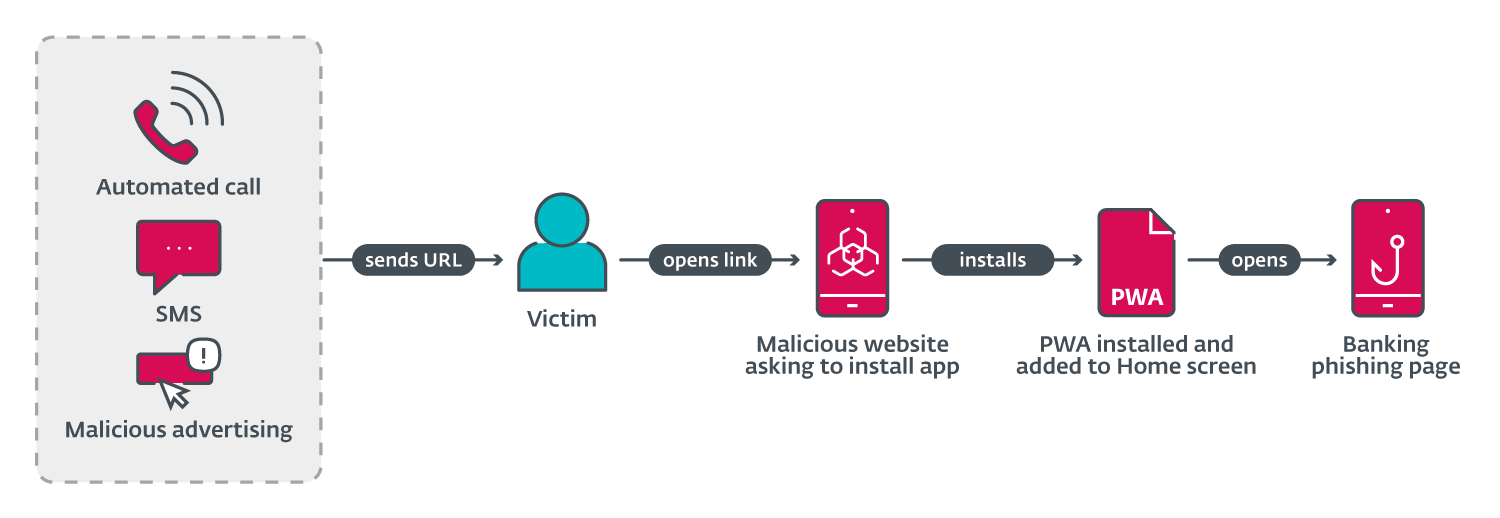
Victims are asked to adopt a novel paradigm for the banking system, as illustrated by Figure 2. Upon activating the misleading marketing campaign, clicking the “Set up/Replace” button triggers the immediate download and installation of malicious software from the website on the user’s mobile device, either in the form of a downloadable APK for Android users only or as a Progressive Web App (PWA) for both iOS and Android users, unless the campaign is based on WebAPK. Significantly, this setup process circumvents traditional browser warnings about installing unknown applications, taking advantage of Chrome’s WebAPK capabilities, which cybercriminals exploit to bypass security measures.
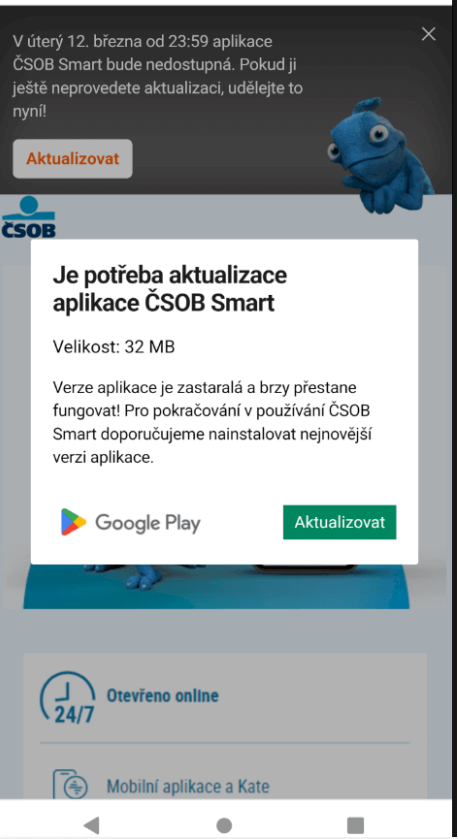
For iOS users, the process differs slightly. An animated pop-up provides instructions on how to add the phishing Progressive Web App (PWA) to their home screen (as depicted in Figure 3). The popup successfully mimics the native iOS prompt’s aesthetic. Ultimately, users of iOS devices should not be alerted about installing an app that may pose a risk to their phone.
Upon installation, users are asked to provide their online banking login credentials to access their accounts via the newly launched mobile banking application. All submitted info is distributed to the attackers’ C&C servers.
Timeline
We initially discovered a pioneering instance of phishing via Progressive Web Apps (PWAs) in early November 2023, followed by the emergence of WebAPKs in mid-November 2023. C&C servers that obtained info from phishing purposes have been first found in March 2024 (as could be seen in Determine 4), with knowledge in them confirming that they have been in all probability not operational earlier.
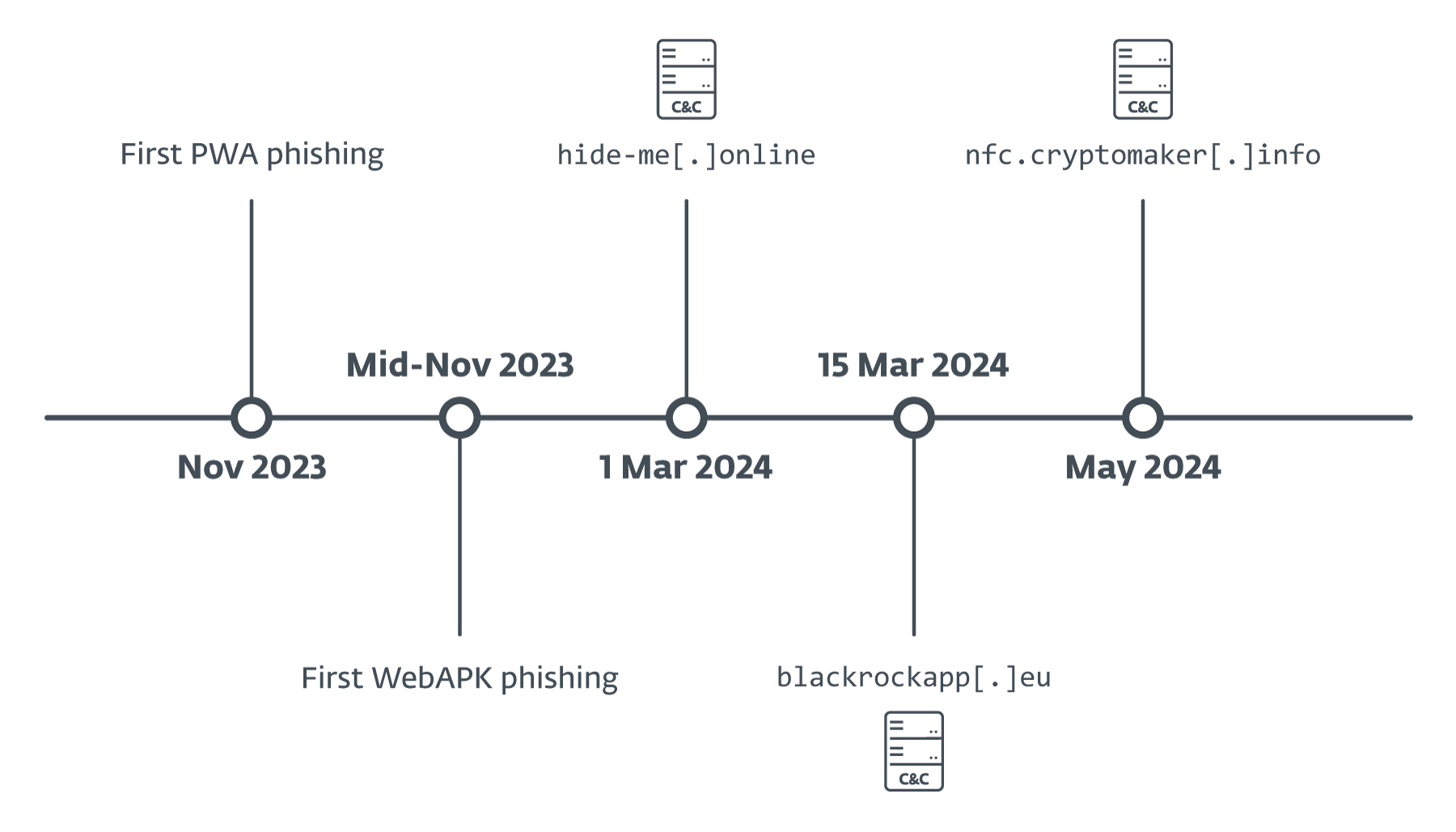
One notable exception was the server, discovered in May 2024, yet it had already been leveraged for an exercise stemming from a marketing campaign aimed at the Georgian TBC Bank in February 2024.
Technical evaluation
We scrutinize the effectiveness of a marketing campaign launched against a prominent Czech financial institution, leveraging cutting-edge WebAPK technology. We provide a concise overview of the fundamental concepts behind Progressive Web Apps (PWAs) and WebAPKs.
PWA and WebAPK purposes
PWAs
The feasibility of this phishing marketing campaign and technique relies heavily on the advancements in progressive web applications (PWAs). Briefly, Progressive Web Apps (PWAs) are web applications built using traditional web technologies that can run on multiple platforms and devices. Upon installation, these applications are seamlessly integrated onto the individual’s mobile device via a pop-up setup prompt or can be chosen manually through a supported browser’s dropdown menu options.
The key feature here enables the smooth integration of applications into a separate window, allowing users to access and launch them effortlessly from the menu bar or home screen. Upon setup, Progressive Web Apps (PWAs) on a household screen are distinguished by the browser’s brand overlaid onto the PWA’s icon (Figure 5).

PWAs also boast the advantage of a unified codebase across multiple platforms, leveraging modern browser APIs and even native code capabilities, courtesy of. Progressive web apps can function offline, as determined by requirement six. These staff serve as a proxy system, retrieving information from the native cache when a web connection is unavailable.
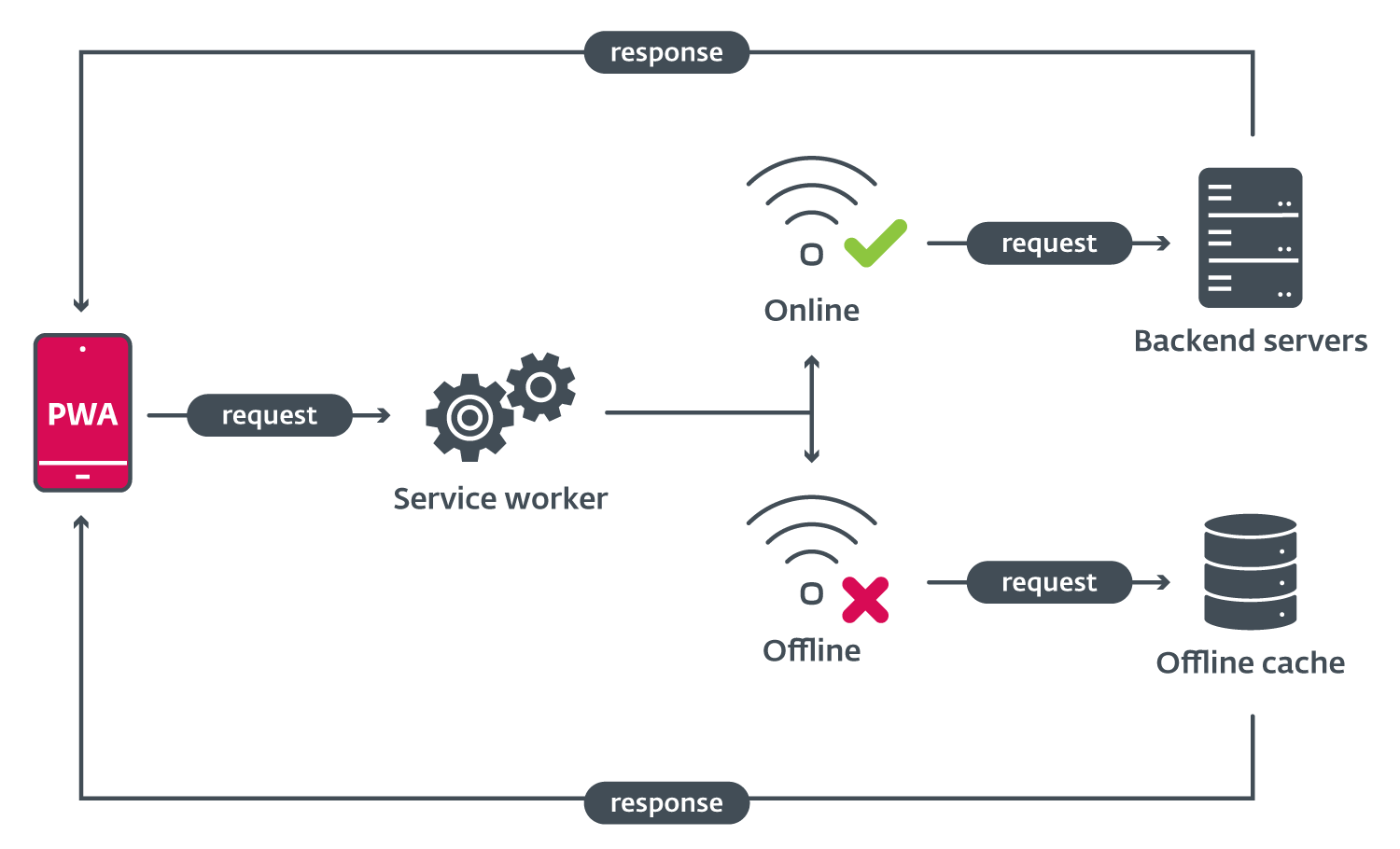
The conduct of all appliances is documented in a unified file known as the manifest. It is a document that defines the brand identity, outlines the net utility scope, identifies sources, and provides a scripted guide for repairing employees on the appliance, as well as the type of launcher. The risk actor can outline the application, resulting in a Progressive Web App that behaves similarly to a traditional mobile app.
While Progressive Web Apps (PWAs) can be designated as the default handler for specific file formats, this capability is currently in an experimental phase and not supported on mobile devices? This could potentially lead to risky actors creating malicious programs that register as the default handler for, say, all PDF files, thereby allowing them to easily create a sophisticated espionage app with far-reaching implications? Despite these limitations, granting entry to browser APIs still allows Progressive Web Apps (PWAs) to request access to features such as the microphone, geolocation, camera, and other supported browser capabilities; consequently, spyware PWAs may pose a risk.
WebAPKs
WebAPKs can be considered an enhanced version of progressive web apps, as the Chrome browser converts a PWA into a local Android application – essentially, an APK – that offers an upgraded model. These WebAPKs are designed to resemble native apps, with their icons often lacking the browser’s distinctive emblem, as illustrated in Figure 7. Within a PWA/WebAPK phishing scheme, scammers attempt to deceive customers by creating a fake application that mimics the genuine banking utility of a reputable financial institution. The era of WebAPKs is currently uniquely backed by Google Chrome alone.

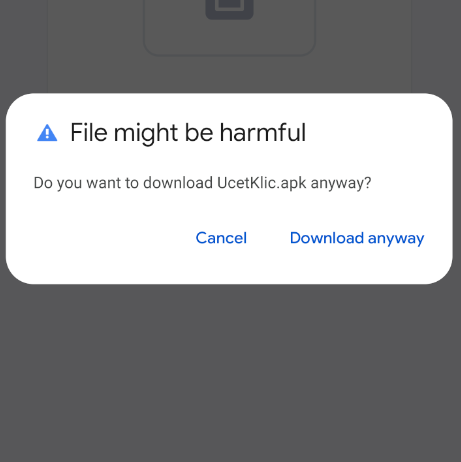
However, deploying a WebAPK into an Android package (apk) does not yield any “L” warnings, mirroring the scenario illustrated in Figure 8, where users are typically instructed to look out for such alerts. The application will also prevent installation if third-party sources are not permitted to be used for setup.
Phishing stream
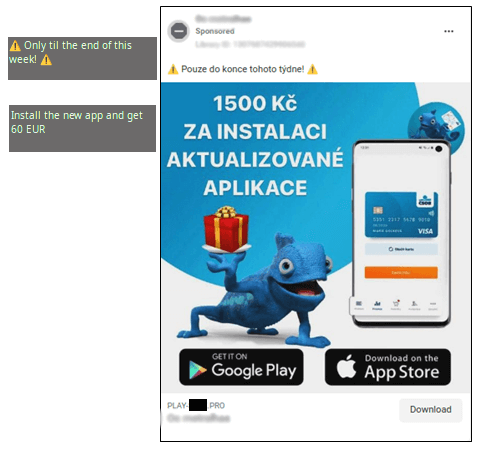
The various supply mechanisms employed in our monitored campaigns were discussed in our earlier overview. When a sophisticated phishing marketing campaign targeted a prominent Czech financial institution, the operation started with malicious Facebook ads disseminating a phishing link (see Figure 9). These ads are typically registered in bulk, consisting of five to six ads each, with each registration occurring separately over time. The risk actor employed custom-created Meta accounts and likely exploited compromised accounts.
Malicious ads incorporated a blend of the financial institution’s official mascot, a blue chameleon, alongside its logos and text, which either enticed users with promises of monetary rewards for installing the app or cautioned them about a critical update.
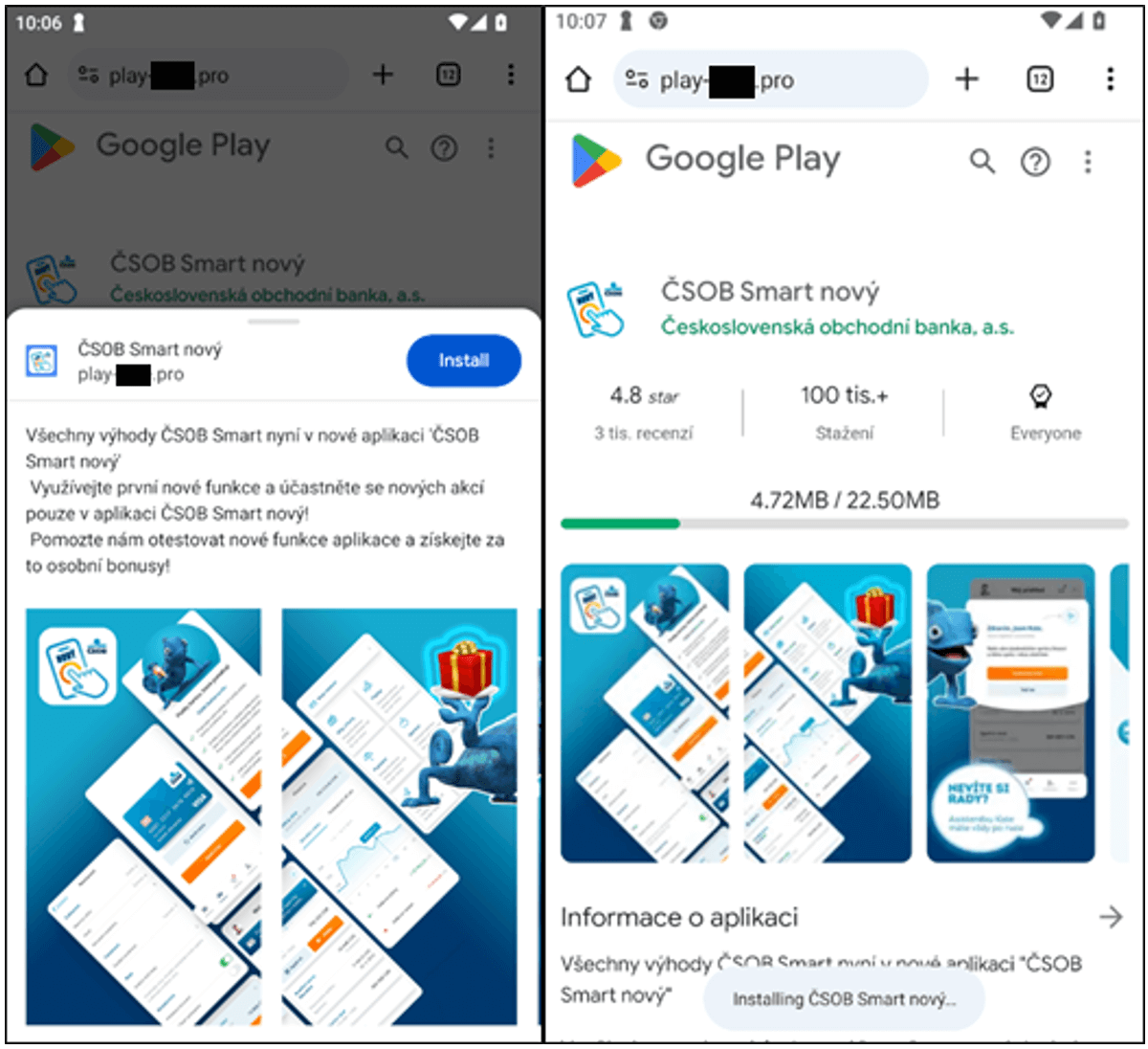
In a targeted social engineering attack, an attacker utilized a time-sensitive offer of financial incentive to lure unsuspecting individuals into clicking on a harmful link. Following the link, users are presented with a seemingly authentic yet fabricated Google Play webpage (Determine 10). The origin from which the phishing WebAPK is obtained.

Does the request contain a valid Cell Consumer? When the user accesses the setup interface using their mobile device, the “Setup” button triggers a pop-up prompting them to initiate the installation process. If the Consumer-Agent header indicates that the user is accessing from a desktop, the setup button remains inactive and offers no functionality. The instant animation mimics Google Play’s signature transitions, further bolstering the credibility and authenticity of this promotional endeavour.
The campaign’s reliance on Google Play visual cues and animations unmistakably caters to Android users. Various publicized initiatives targeted users of specific iOS (including twelve) and Android platforms. The websites exploited the visibility of a familiar utility on the landing page, prompting unsuspecting users to install an updated version. Android users have been prompted to install WebAPKs, while iOS users are directed to Progressive Web Apps (PWAs).
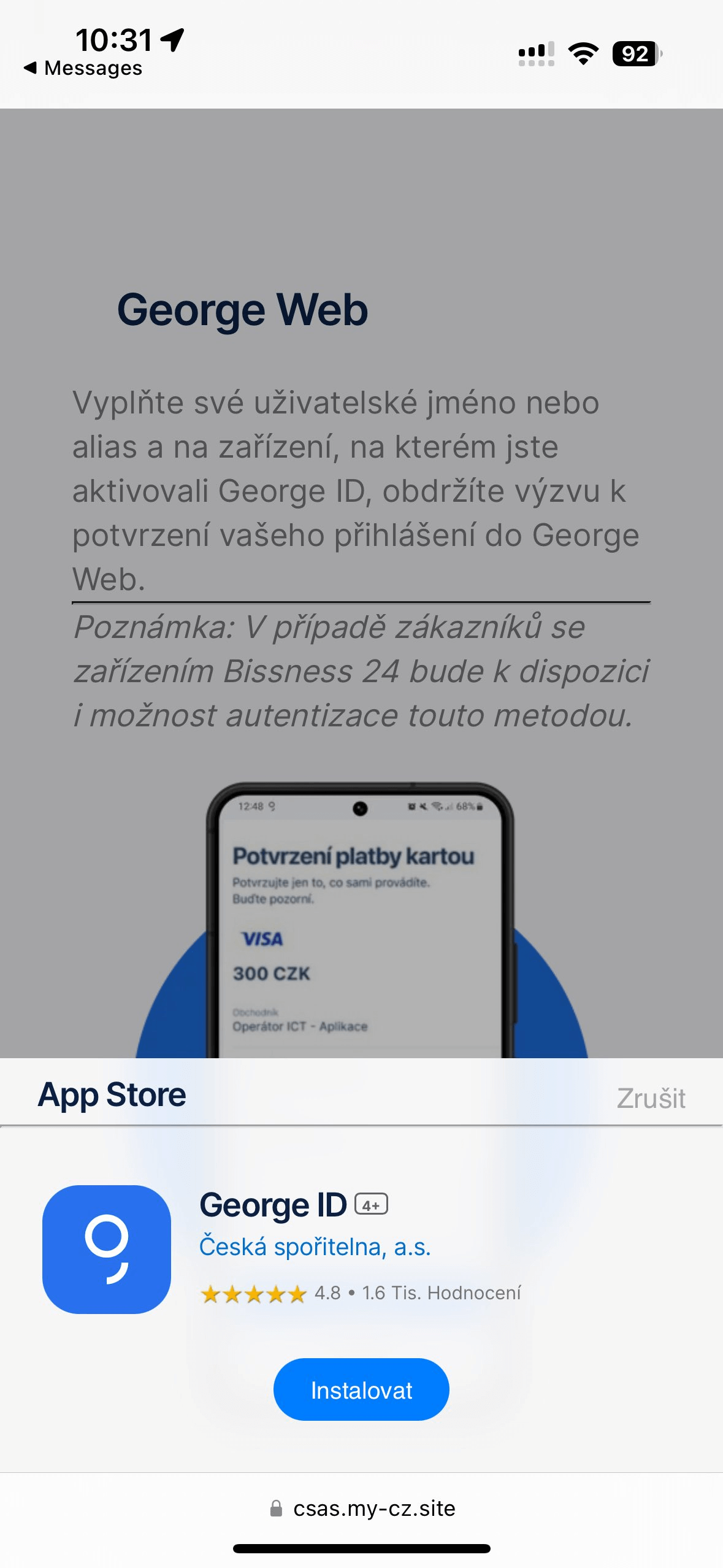
Following setup, the phishing PWA/WebAPK is seamlessly integrated onto the individual’s device home screen, whereupon launching it leads directly to a deceptive login webpage, as demonstrated in Figure 13.
Furthermore, the device’s data tab reveals a critical fact: the app was downloaded from the Google Play Store, consistent with standard practice. This applies universally to all WebAPK applications.
The phishing utility and phishing URL referenced in this submission have been reported to ČSOB. Phishing scams have never been available for download on the official Google Play store.
C&C infrastructure
Primarily based on the truth that the campaigns used two distinct C&C infrastructures, we have now decided that two separate teams have been working the PWA/WebAPK phishing campaigns in opposition to Czech and different banks.
One group used a Telegram bot to log all entered info right into a Telegram group chat through the official Telegram API, and one other used a standard C&C server with an administrative panel. The second team is responsible for executing the marketing campaign featured in one of our forthcoming blog posts.
Telegram bots
Stolen login credentials were recorded on a backend server and subsequently transmitted to a Telegram group chat, where the compromised banking login information was disseminated. HTTP calls were made to deliver messages to the designated group chat of the risk actor’s group via the official Telegram Application Programming Interface (API). This isn’t a novel tactic and is frequently employed in diverse phishing toolkits.
Upon launching the phishing webpage of the Progressive Web App, a pop-up warning message appears prominently at the top of the screen (refer to Figure 15). The initial discovery revealed a stack hint comprising particulars about the Telegram API and bot token utilized, which was discernibly displayed on the login screen itself.
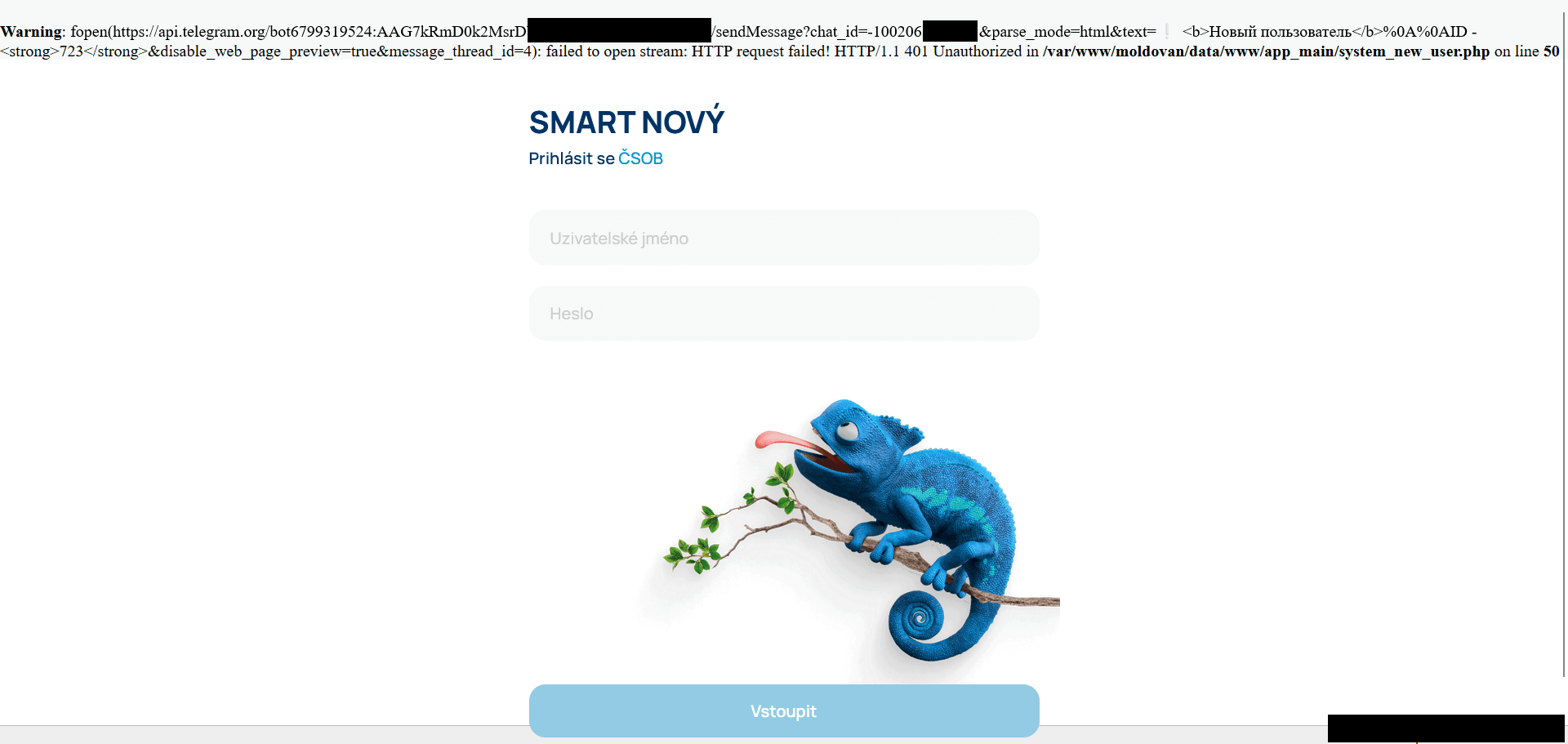
Initially, we discovered that the threat actor had stored all data within a Telegram group chat for recordation purposes. All sensitive information regarding compromised customers of the affected financial institution was promptly reported to their respective banks.
C&C servers
During the assessment of a Progressive Web App (PWA), it was observed that user data was sent to a distinct backend server. Upon inspection of the contacted C&C server, we uncovered an operator panel (Determine 16) that included delicate info of victims, at the moment energetic phishing URLs, and a full historical past of visiting victims.
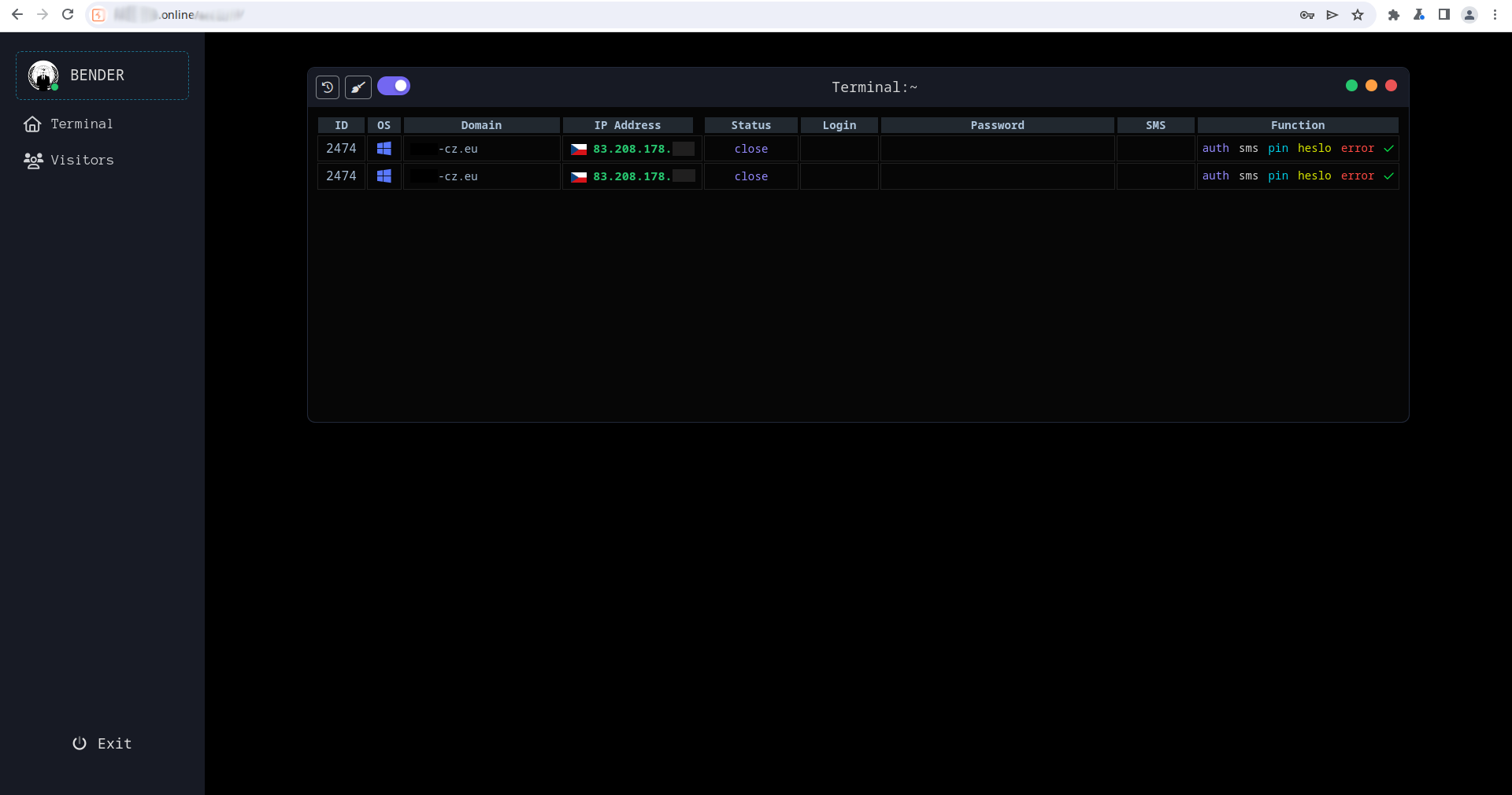
The risk actors didn’t keep put, and after the primary C&C area was deactivated () they continued to ascertain extra domains and even ready a very new malicious marketing campaign, operated from the identical panel. The second marketing campaign will be thoroughly examined in our forthcoming analysis.
Following the insights gleaned from the expert panel, we were able to swiftly reach out to the impacted financial institutions and provide robust support to the customers who had been affected.
Conclusion
A cutting-edge phishing method has emerged, seamlessly integrating time-tested social engineering tactics with the versatility of Progressive Web Apps’ capabilities. A sophisticated scheme targeting Android users has been uncovered, involving fake websites mimicking the official Google Play store page for popular apps, with hackers leveraging WebAPK technology to replicate the targeted application’s functionality.
A significant majority of identified cases have been located within the borders of the Czech Republic, with only two exceptions being detected in neighboring Hungary and Georgia respectively.
As a result of two drastically totally different C&C infrastructures have been employed, we have now decided that two totally different teams are accountable for the unfold of the phishing apps.
As the platform is deployed, we expect counterfeit applications to emerge and spread rapidly, making it challenging to distinguish legitimate apps from malicious ones.
All sensitive information uncovered during our examination was swiftly transmitted to the relevant financial institutions for their prompt consideration and action. We additionally negotiated the takedowns of a number of phishing domains and C&C servers.
IoCs
Recordsdata
| Android/Spy.Banker.CIC | Android cell phishing app | ||
| Android/Spy.Banker.CLW | Android cell phishing app |
Community
| Cloudflare, Inc. | 2024‑03‑05 | C&C server. | ||
| NETH LLC | 2024‑02‑21 | C&C server. | ||
| Cloudflare, Inc. | 2024‑04‑07 | C&C server. | ||
| Internet hosting Ukraine LTD | 2023-11-29 | Distribution server. | ||
| Cloudflare, Inc. | 2024-01-18 | Distribution server. |
MITRE ATT&CK methods
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Phishing | Malicious actors initially distribute malware through deceptive marketing tactics or large-scale phishing schemes. The device, after initial configuration, is hijacked to facilitate fraudulent phishing schemes. | ||
| Enter Seize: GUI Enter Seize | Sensitive information is compromised through sophisticated phishing attacks that masquerade as legitimate login pages for targeted financial institutions. | ||
| Utility Layer Protocol: Internet Protocols | PWA and WebAPK-based phishing applications transmit login credentials via JavaScript interfaces, concurrently monitoring user activity. |

