Researchers at ESET have discovered a sophisticated campaign targeting a European government entity, exploiting vulnerabilities in air-gapped systems. The marketing campaign, attributed to GoldenJackal, a notorious cyberespionage Advanced Persistent Threat (APT) group targeting authorities and diplomatic entities, spanned from May 2022 to March 2024. In a thorough examination of the toolkit employed by the group, our findings indicate that GoldenJackal launched an attack on a South Asian embassy in Belarus back in 2019, specifically targeting the embassy’s air-gapped systems using tailored tools.
This blog post uncovers previously unknown instruments attributed to GoldenJackal, relying on victimology, coding patterns, and functional parallels with existing toolsets.
- A sophisticated cyberactor, known as GoldenJackal, leveraged a tailored arsenal of tools to target air-gapped systems at a South Asian diplomatic mission in Belarus, with activities dating back to at least August 2019. For the first time ever, we are making public our descriptions of these instruments.
- The inaugural public presentation of the highly versatile GoldenJackal toolkit was showcased at multiple events spanning from May 2022 to March 2024, with a focus on delivering this innovative solution to a national government agency in a European Union country.
- The GoldenJackal toolkit offers a comprehensive suite of features for conducting targeted network compromise and persistence operations. Malicious programs are exploited to collect sensitive information, track data flows, extract data, and disseminate information, configuration files, and instructions to other compromised systems.
- It is unclear what the ultimate objective of GoldenJackal’s activities truly is, but it seems plausible that the primary goal might involve pilfering sensitive information, possibly targeting prominent systems that are not necessarily connected to the internet.
GoldenJackal profile
The Golden Jackal cybercrime group has been active since at least 2019. The platform specifically focuses on targeting authorities and diplomatic entities across Europe, the Middle East, and South Asia. The group remains largely anonymous and was first publicly referenced in 2023 by a single source. The toolset comprises five C#-based implants: JackalControl, JackalSteal, JackalWorm, JackalPerInfo, and JackalScreenWatcher, designed to facilitate covert surveillance activities.
Overview
In May 2022, our team discovered a novel toolset that defied attribution to any known Advanced Persistent Threat (APT) group. As soon as the attackers utilized a software similar to one publicly documented by Kaspersky, we were able to drill deeper and uncover a link between the openly published GoldenJackal toolkit and this novel tool.
By extrapolating from this information, it appears we successfully identified an earlier instance of a deployment where the publicly disclosed toolset was used, as well as an older toolset possessing the capability to target air-gapped systems. This in-depth look at the publicly uncharted toolsets sheds light on the technical aspects, while also offering valuable insights into GoldenJackal’s methodologies, tactics, and protocols.
Victimology
GoldenJackal has concentrated its efforts on governmental entities within Europe, the Middle East, and South Asia. We identified the presence of GoldenJackal surveillance devices at a South Asian diplomatic mission in Belarus during both August-September 2019 and again in July 2021.
Incidents of limited scope and scale of attacks on authorities and diplomatic installations in the Middle East and South Asia began surfacing in 2020.
Recently, according to ESET’s telemetry data, a national authority group in a European Union country faced repeated attacks from May 2022 to March 2024.
Attribution
The campaigns described on this blog post ultimately deployed at least one instrument linked to the notorious GoldenJackal Advanced Persistent Threat (APT) group, with no specific timeframe provided. In line with the Kaspersky report’s findings, we refrain from attributing GoldenJackal’s activities to a specific nation-state. There may be, nonetheless, one clue that may level in direction of the origin of the assaults: within the GoldenHowl malware, the C&C protocol is known as , which is an expression usually utilized by Turla (see our ) and . It appears that the developers behind GoldenHowl are likely a Russian audio company, judging by this clue.
Breaching air-gapped programs
To minimize the risk of compromise, highly sensitive networks are often isolated, severing all connections with other networks. Frequently, organizations prioritize safeguarding their most valuable initiatives, much like securing high-stakes processes such as voting systems and industrial management programs that control critical infrastructure, akin to energy grids. Those that may be of utmost interest to potential attackers are often precisely these networks?
While it was noted in our previous whitepaper that compromising an air-gapped network requires significantly more resources than breaching an internet-connected system, this inherently implies that the development of attack frameworks targeting air-gapped systems has thus far been the exclusive domain of Advanced Persistent Threat (APT) groups. The primary objective of these attacks is always to conduct espionage, occasionally accompanied by.
In a remarkable display of technical prowess, GoldenJackal has successfully developed and deployed not one but two sophisticated toolsets capable of circumventing the security of air-gapped systems within just five years. The ingenuity displayed by this collective truly showcases their adaptability. A sophisticated attack on the South Asian embassy in Belarus employed novel tools previously unseen in any other instance. The marketing campaign relied on a trifecta of components: GoldenDealer, which transmitted executables to the isolated network via USB surveillance; GoldenHowl, a versatile backdoor boasting a range of features; and GoldenRobo, a file gathering and exfiltration tool.
In the latest spate of attacks against law enforcement agencies in Europe, notorious hacker GoldenJackal upgraded their toolkit to a cutting-edge, highly modular platform. This modular strategy is employed not only in designing malicious instruments (as seen with GoldenHowl), but also in their roles: they are utilized to collect and process valuable data, disseminate information, configurations, and instructions to other programs, and to extract sensitive information.
Technical evaluation
Preliminary entry
Thus far, we have not had the opportunity to revisit and refine the initial compromise vector observed in our campaign telemetry data. According to a report by Kaspersky, GoldenJackal employed Trojanized software programs and malware-laced documents to achieve its malicious goals.
The mysterious toolset from 2019
The earliest attack linked to GoldenJackal, targeting a South Asian embassy in Belarus, took place in August 2019. According to available information, the toolset employed in this assault remains publicly uncharted. We have exclusively encountered these custom-made instruments once, and never again:
- A malware component capable of delivering executable files to isolated computer systems via compromised USB devices. We’ve named this part GoldenDealer.
- A newly discovered malware, dubbed GoldenHowl, has been identified as a sophisticated backdoor featuring a suite of malicious modules capable of wreaking havoc on compromised systems.
- A malicious file collector and exfiltrator, known as GoldenRobo.
The evidence outlining the assault is clearly presented in Figure 1. Since the preliminary assault vector is unclear, it’s reasonable to infer that both GoldenDealer malware and an unidentified worm component have likely gained access to a vulnerable PC with internet connectivity, allowing potential exploitation. When a USB drive is inserted at any given moment, the unknown portion duplicates itself alongside the GoldenDealer component, transferring them to the drive. While we did not detect this particular component, similar functionality has been observed in other toolsets employed by the group during subsequent attacks.
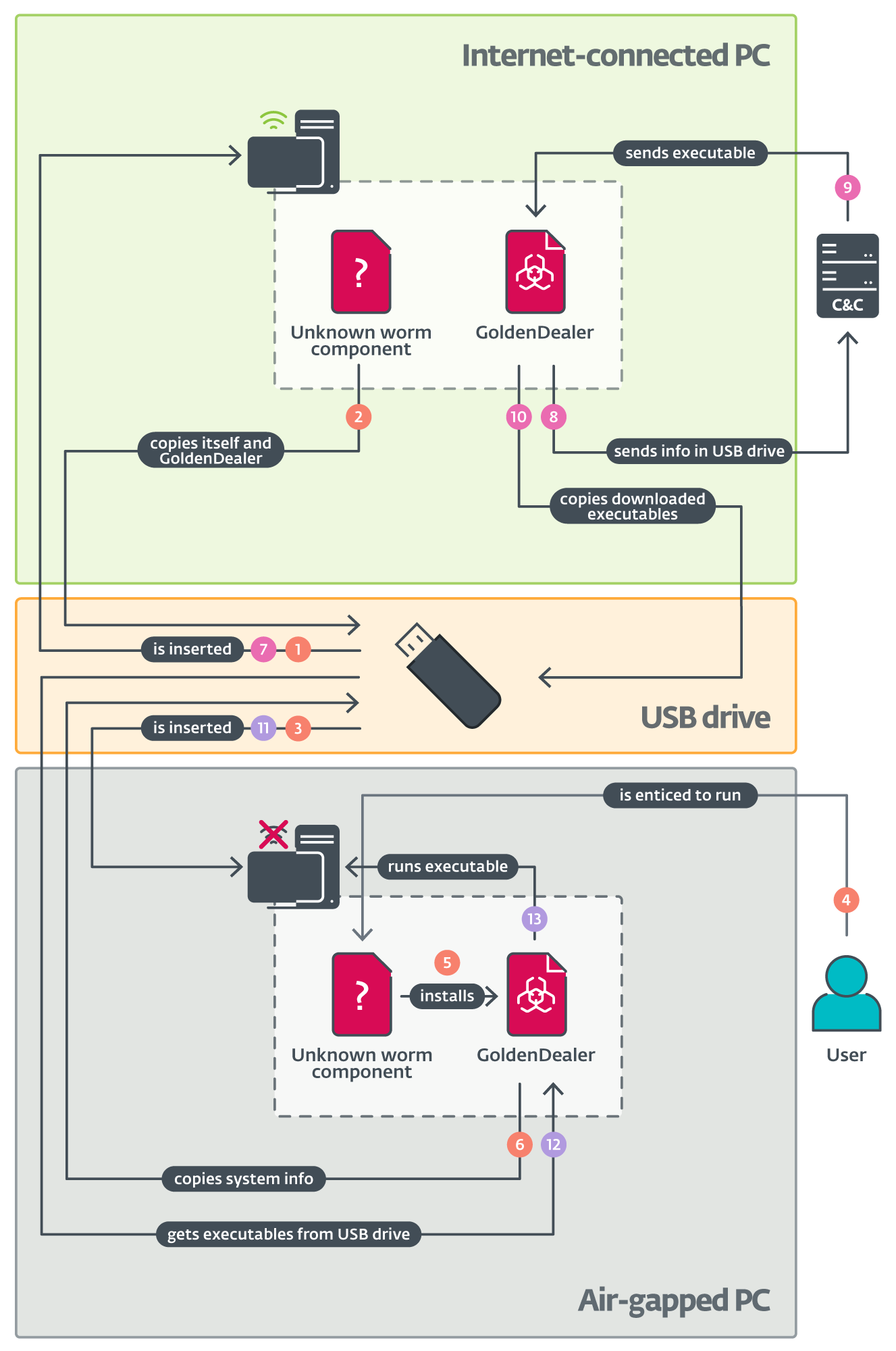
It’s possible that this unknown component locates the final modified file on the USB drive, conceals it, and rebrands itself with the identity of the file, now attributed to JackalWorm. When inserted into an air-gapped system, the part cleverly employs a folder icon to pique the user’s curiosity, thereby encouraging them to run it, as designed by the perpetrator, JackalWorm.
When the drive is once more inserted into the internet-connected PC, GoldenDealer takes the details about the air-gapped PC from the USB drive and sends it to the C&C server. The server responds with a list of executables to be executed on the isolated machine. When reinserted into the air-gapped PC, GoldenDealer extracts the executables from the drive and executes them. Since the GoldenDealer system is already in place, there is no need for customer interaction, thereby eliminating any potential delays or inefficiencies.
We’ve recently observed that GoldenDealer has been utilizing GoldenHowl on a computer connected to the internet. Whereas we didn’t observe GoldenDealer instantly executing GoldenRobo, we noticed the latter additionally operating on the linked PC, used to take information from the USB drive and exfiltrate them to its C&C server. Despite initial appearances suggesting otherwise, there exists an additional, previously overlooked component that replicates data from the isolated PC onto the USB drive.
GoldenDealer
The component showcases the integration of removable storage devices on both isolated and networked computers, as well as internet connectivity capabilities. Primarily based on the latter, it may well obtain executable information from a C&C server and conceal them on detachable drives, or retrieve them from these drives and execute them on programs that don’t have any connectivity.
This system can operate either with or without optional command-line arguments. When provided with command-line arguments, this program relocates a specified file to a fresh destination and then executes its functionality using the API in silent mode, without opening a graphical user interface.
To prevent potentially sensitive information from being exposed in Windows Explorer, GoldenDealer sets a registry value to zero, thereby disabling the feature that allows hidden files to be displayed.
When GoldenDealer ceases to operate as a service, it initiates the creation of a new service entity, which commences operations before ultimately exiting. In cases where the service cannot be successfully provisioned, persistence is ensured through the creation of an entry within a designated registry key.
The desk containing configuration information used by GoldenDealer displays a comprehensive checklist. The malware was discovered to be operating from within a specific listing that was part of the noticed attack. Additional details regarding this information are provided in subsequent sections.
Desk 1. Configuration information utilized by GoldenDealer
| Retailer standing fields. | |
| Retailer executable information despatched by the C&C server. | |
| Retailers provide information on all compromised computers within the community. | |
| Used as a mutex. If this file remains open, it indicates that a GoldenDealer occurrence is currently underway. |
The contents of configuration information are formatted in JSON and stored either securely (XOR) or encrypted on the disk. XOR encryption operates on a single byte basis, utilizing a unique one-byte key that increments in accordance with a defined multiplier.
Community connectivity thread
To determine whether a PC is connected to the internet, GoldenDealer periodically sends a GET request every 15 minutes. If the connection proves unreliable or remains unresponsive, the PC will automatically assume a disconnected status. Maps to Cloudflare’s DNS resolver, and the expected behavior is to retrieve a document and a static code. The half just isn’t related right here, however is used for C&C communication. GoldenDealer primarily generates this consumer identifier based on:
- The present username, revealed through the API’s insightful discovery process.
- The primary serial interface available on the system’s logical drives. The lack of clarity suggests that this installation method doesn’t necessarily dictate where the operating system is placed.
The two input strings are separately hashed using an operation, yielding distinct numerical values which are then XOR-ed together to generate a unique identifier for the user.
To ensure accurate tracking of community connectivity status, GoldenDealer employs a global variable that can take on one of the following values:
- Malware has been detected to be operational, and subsequent checks have not confirmed connectivity.
- PC lacks internet connectivity.
- – PC has web connectivity.
If the standing is , a thread is signaled to obtain executable information from the C&C server, and one other thread is signaled to repeat the executables to USB drives. A thread to execute executables from drives and run them will be signalled when the status is true. Whenever standing modifications are made, the configuration file is instantly updated with the latest values. Fields on this file are:
- – community connectivity standing.
- A range of seconds without a website? The worth metric is incremented every 15 minutes and resets to zero whenever a connection is established. If the malware is set to delay for a short period before concluding that the PC lacks connectivity, no such pause was observed in the samples we analyzed.
- – unknown. The discipline of cybersecurity is surprisingly overlooked by malware developers.
- – checklist with hashes of executables downloaded from the C&C server.
Downloader thread
The thread continuously monitors community connectivity every 30 minutes, taking further action only when the PC is connected to the internet. First, a GET request is distributed to , simply to let the C&C server know that one other request is to comply with. The request from the client simply fails to receive a response from the server. If the request fails, another attempt will be made to a secondary server, likely with notification of the failure, as the thread does not continue execution in this scenario. The URLs are typically hardcoded within the malware, rendering them non-configurable in the analyzed samples.
When communication proves profitable, GoldenDealer initiates a request to discuss further. The server responds with an array of JSON-formatted objects, containing the following key-value pairs:
- A binary payload disguised as a base64-encoded string, awaiting decoding to reveal its executable contents.
- Whether the executable will run or not is determined by the presence of an array.
- The FNV-1a hash of a null input string is undefined.
- – date and time when the executable was obtained from the C&C server.
The contents of the final two fields are usually not related, as a result of they’re calculated by the downloader thread, changing unique information despatched by the C&C server. Regardless of the situation, these values are stored as decimal points.
When a dispatch from the server matches the configured checklist, GoldenDealer will execute the relevant executable file only if its MD5 hash does not exist in the stored list of hashes within the configuration domain. Linked PCs can seamlessly acquire and transfer executables across various platforms via USB drives, allowing for effortless execution of downloaded files. Upon execution, the program’s hash is appended to a unique identifier, ensuring it can only be launched once per user instance. Every executable is written within the working directory with the value of the file as its filename. JSON files containing information about acquired executables are stored persistently on the local disk.
As the ultimate step, the downloader thread collates details about the compromised system and transmits them to. The configuration file is up-to-date for storing this information accurately. Determine 2 reveals a part of the JSON object with the data despatched to the C&C server. As a convention, all string inputs are internally represented as arrays of decimal code points to facilitate processing. For user clarity and improved comprehension, these strings are displayed visually as human-readable text within the system’s graphical representation. Instead, the value is undoubtedly dispatched.
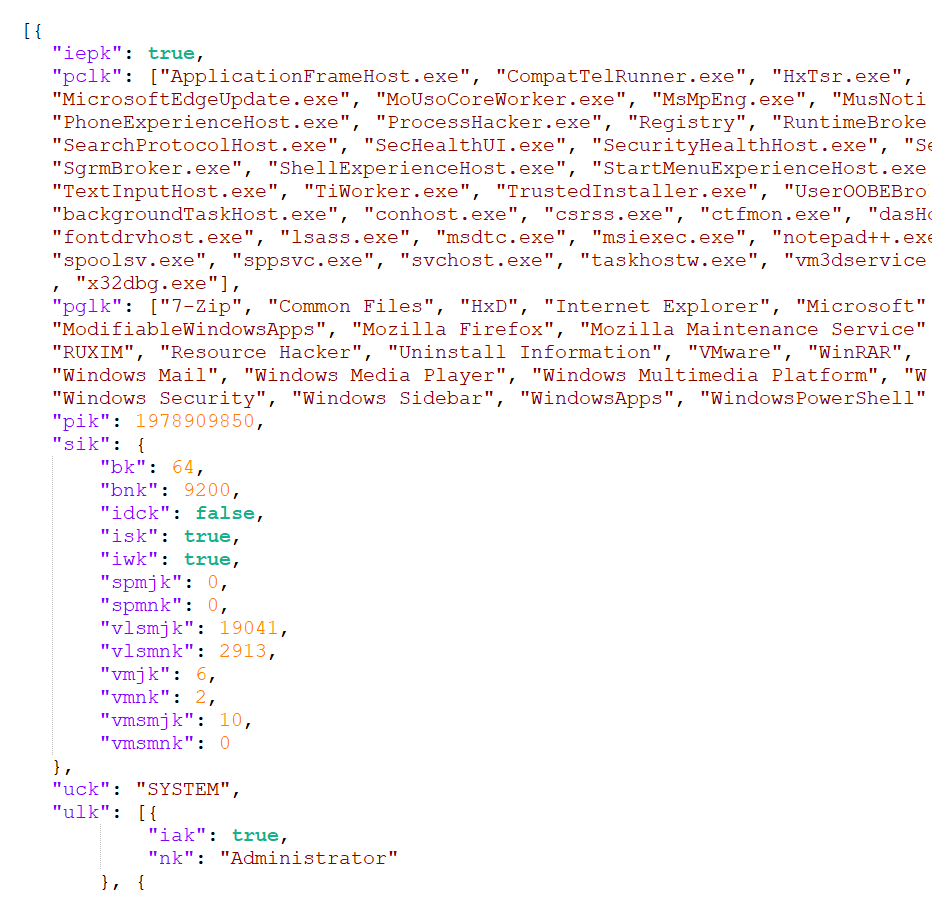
The members are:
- Whether the GoldenDealer process is elevated is indicated by a Boolean value.
- An array of operational processes
- An array of put-in applications in each directory.
- – the ,
- Details regarding the operating system’s functional architecture, including the model, construct, and service pack quantity; structural composition; and binary flags signifying whether the OS is executing on a server, area controller, or workstation.
- The consumer operating the GoldenDealer course
- An array of customers, each accompanied by a Boolean value denoting their administrative privileges status.
The USB monitoring thread was established to track and analyze the performance of USB connections across multiple linked PCs.
The GoldenDealer software generates a dedicated window to display the installation of removable drives, utilizing a tailored event handler that captures drive insertions while ignoring other system events.
As soon as a USB drive has been inserted, this thread promptly patches one byte within the master boot record (MBR) of that drive. It searches for the specific offset where the string resides and replaces the original byte with a period (.). The script then verifies whether the second one has also been updated, and terminates the process if this is not the case. The USB thread running on air-gapped PCs accomplishes a dual task: it updates the secondary PC, then verifies if the primary PC has already received the patch. To process the data on the USB drive, it was necessary that the drive had been inserted into both a connected PC and an air-gapped PC separately?
If the examination proves profitable, a discreetly concealed listing is generated and saved to the USB drive, containing two crucial pieces of information inscribed within.
- – this file has the identical contents as (all of the executables despatched by the C&C server). The tool is designed to transfer executables to isolated applications for execution on air-gapped systems.
- A database containing intelligence gathered from isolated computers. The malware is initially created in an empty state and later populated through a process that takes place on air-gapped PCs using the USB thread. The contents of this file are appended to the native file (see Desk 1), to be despatched to the C&C server by the downloader thread.
The security of air-gapped PCs, those isolated from the internet’s prying eyes, has long been a topic of fascination. But what about USB monitoring? Can we still keep tabs on these devices, despite their physical separation from the digital world?
A recent study delves into the realm of possibilities, presenting an innovative approach to monitor air-gapped PCs via USB. By leveraging the subtle changes in device behavior caused by malicious activity, researchers have developed a clever method to identify potential threats. This breakthrough has significant implications for the detection and mitigation of attacks against sensitive systems.
SKIP
The copying process of the USB drive’s executable files to a native file is complimentary to the previous description. It takes the file containing the executables on the USB drive and replicates its content to a natively generated file. The process also transfers the native file containing information about the air-gapped system’s configuration, along with its contents, to a designated file stored on the USB drive. The code snippet that facilitates acquiring system information and executing executables is presented within this thread.
GoldenHowl
GoldenJackal’s 2019 toolset includes another notable software, GoldenHowl, a Python-based backdoor featuring multiple modules that enable various malicious capabilities. The software is packaged as a self-extracting archive containing both reliable Python executables and libraries, as well as malicious script components. Three documents reveal the contents of one of these archives. The attackers replaced the original Python executable, version 2.7.15, with a malicious file named `. This section is designed for execution on personal computers with internet access, considering its capabilities.
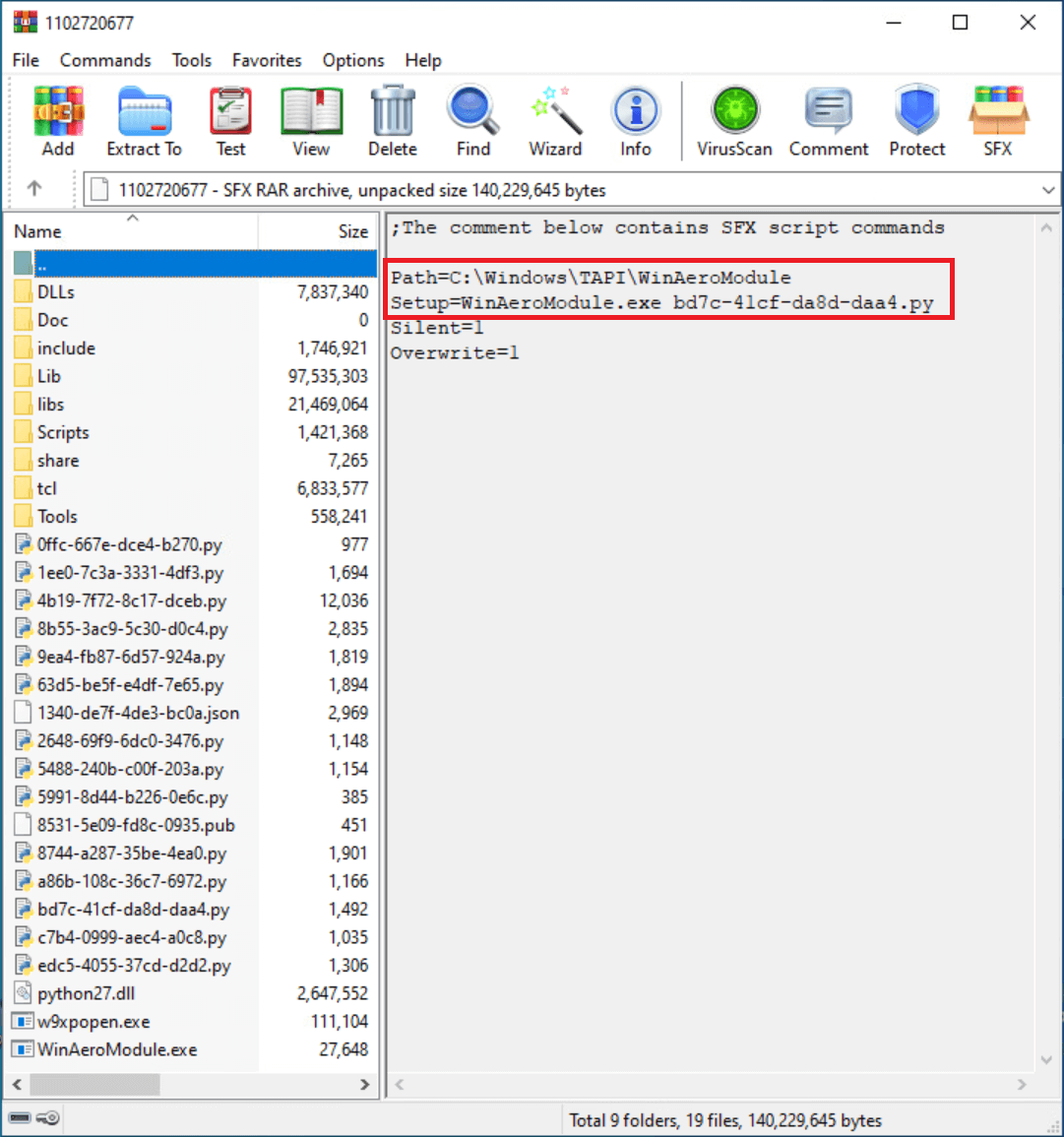
Within the malware’s configuration file, the preliminary script in GoldenHowl performs the following actions:
- obtains and extracts the malware’s settings from a JSON-formatted file.
- Creates directories that are exploited by the malware, effectively establishing a foothold for its malicious operations.
- Creates separate threads for each module.
The malware’s configuration is decrypted using a custom algorithm and a pre-defined, hardcoded key. The decryption process yields partial insight into the configuration.
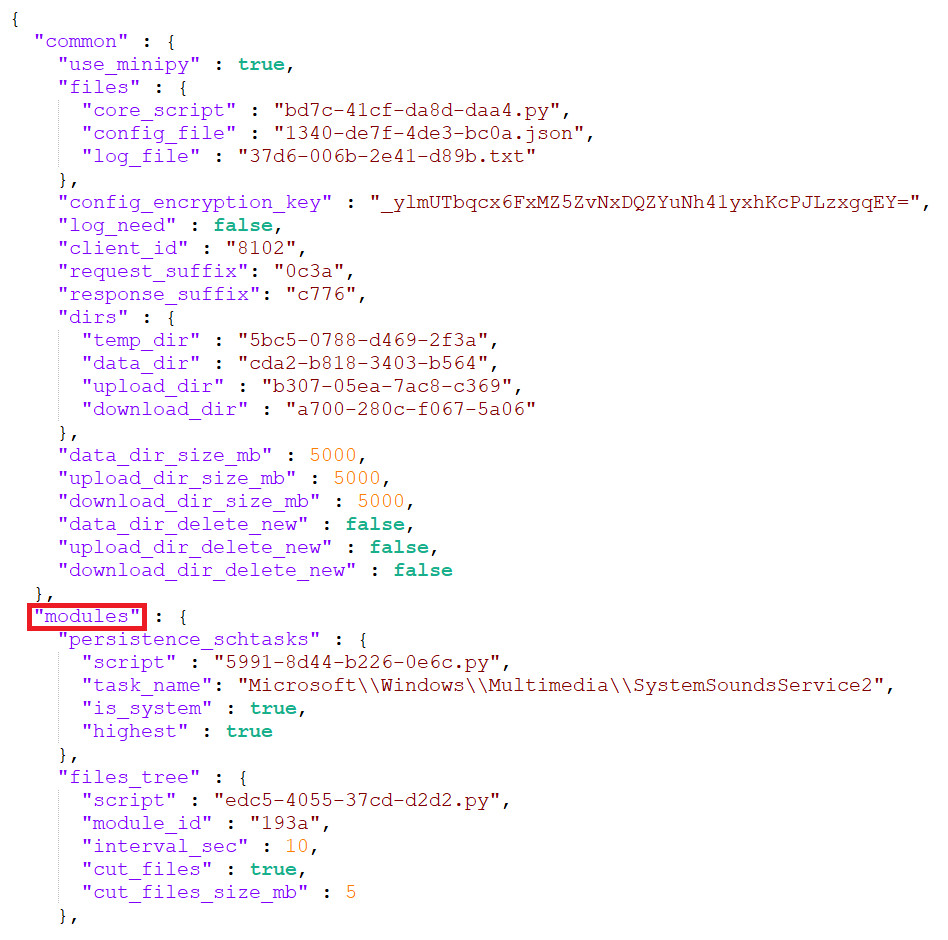
The Desk 2 documentation highlights the Python modules in the order they appear in the configuration file, providing a summary of each module’s functions and capabilities. Modules run indefinitely, except for the startup module, which executes immediately upon start-up.
Desk 2. Malicious modules in GoldenHowl
| Schedules the persistence of core_script’s execution through a recurring process. | ||
| Generates an inventory of information and directories by calling Home windows’ tree command, for a path laid out in a request despatched by the C&C. | ||
| Exfiltrates a single file to the C&C server. The file path is laid out in a request despatched by the C&C. | ||
| Utility module that takes incoming requests from the C&C server and decrypts them, and takes responses from different modules that must be despatched to the C&C and encrypts them. The encryption algorithm used is Fernet; a specific peculiarity of this module lies in its handling. | ||
| Utility module that uploads and downloads information from the C&C server. No changes were made to this input as there was no provided text. Please provide the text you would like me to improve in a different style as a professional editor. Observe that the phrase transport is usually utilized by and to seek advice from a kind of C&C protocol. While this information may be intended for dissemination among Russian-speaking construction professionals, its reliability in terms of authorship is uncertain. | ||
| Utility module that receives a ZIP archive with up to date modules or configuration from the C&C server, extracts the archive, and runs in a brand new course of, terminating the present course of. | ||
| Connects to an SSH server laid out in a request despatched by the C&C. Acts as a reverse shell, executing instructions acquired from the C&C. | ||
| Generates an inventory with energetic IP addresses in an IP vary, primarily based on an IP masks laid out in a request despatched by the C&C server. The script initiates by broadcasting a message to all IP addresses within the specified subnet, followed by querying the ARP cache tables for all network interfaces using the command. | ||
| Generates an inventory with ports which might be accepting connections, primarily based on an IP handle and a listing of ports laid out in a request despatched by the C&C server. | ||
| Establishes a secure SSH connection with a remote server, redirecting data transmission between two networks: one designated by a local listening port and the other utilizing a forwarding port on the SSH server. A request from the C&C server specifies: the handle and port of the SSH server, username and password for the SSH session, the forwarding port on the SSH server, and the handle and port of the listening host. | ||
| Checks whether or not a bunch, laid out in a request despatched by the C&C server, is susceptible to a Home windows SMB distant code execution vulnerability. The code for this module is akin to that found in both ‘and’ modules from. The vulnerability in this module has yet to be exploited, leaving potential targets unpatched and vulnerable to attack. | ||
| Serves as a proxy server, redirecting network packets from a source IP address (supply handle) to a destination IP address (vacation spot handle). The port to pay attention for incoming connections is laid out in a request despatched by the C&C server. The code in this module bears a striking resemblance to that found in . | ||
| The file writer writes a textual content file to a given path. It takes a string as input and saves it into the specified location on your computer. You can use this method to store any information you want to remember, like notes or reminders. The trail and textual content for writing are laid out in a request despatched by the C&C server. |
C&C communication
In accordance with GoldenHowl’s configuration, something that comes from the C&C server is named a request, and information going to the C&C server characterize a response. It ought to be famous that regardless of this naming conference, GoldenHowl just isn’t a passive implant: it initiates the connections to the C&C server. The module is chargeable for communication with the C&C server, and for writing requests and responses to particular directories. The directories utilized by GoldenHowl are revealed on Desk 3.
Desk 3. Directories in GoldenHowl’s configuration
| Shops encrypted requests coming from the C&C server. | ||
| Shops encrypted responses, with information or output of instructions, to be despatched to the C&C server. | ||
| Shops requests despatched by the C&C server, that are taken from , decrypted, and positioned on this listing for modules to course of. Shops also output the results of executed instructions, which are retrieved from this list and subsequently encrypted before being written to. The module carries out these actions. | ||
| The unused listing remains dormant, devoid of integration into any notable modules. |
Requests and responses have well-defined, structured filenames that facilitate easy identification.
- Request –
- Response –
The fields, ‘fields’, and ” are defined within the configuration and apply universally across all modules; refer to Figure 4 for illustrations. The sector defines which module should handle a request or generate a response, and is specified in the configuration section of each individual module. The sector request_id is generated on the C&C server, and ties collectively requests with responses.
The module sends GET requests periodically to the C&C server to examine for out there requests. Specifically, the parameters that define this module’s settings include:
- – handle of the C&C server (we noticed , the identical handle as GoldenDealer’s server),
- The default port used for communication with the server, typically identified as TCP port 443.
- The protocol indicator – specifies whether HTTP or HTTPS is expected to be employed for data transmission.
- – the minimal wait time earlier than contacting the C&C server, and
- The delay filename specifies a duration in seconds that may range from 0 to 3600, governing the interval between subsequent interactions. The file is not included with GoldenHowl, but it might be embedded by the attackers using the module.
The handle used to contact the C&C server is .
GoldenRobo
The final of the noticed instruments from the 2019 toolset, GoldenRobo, is a straightforward part written in Go that executes the utility to stage information and ship them to its C&C server. The program iterates through all drive letters from A to Z, attempting to access each one in turn. If the operation proves profitable, a meticulously crafted Robocopy command is assembled.
If we dissect the directive:
- information are copied from ,
- to (for instance: ),
- Can you provide the original text for me to work on? I’ll do my best to improve it in a different style.
- together with subdirectories (),
- Not retrying on failed copies?
- excluding information that is more than seven days old,
- excluding specified directories ().
Archived copies of data from all drives are compiled into a single ZIP file, with its contents replicated exactly as they appear while GoldenRobo is operational, timestamped with the current date.
The archive is distributed in a base64-encoded format and saved as a `.`. The final aspect of the URL is identical to the discipline specified in GoldenHowl’s configuration. The hardcoded URL in GoldenRobo suggests a tailored attack, implying that the attackers specifically crafted this variant for the individual victim.
The Identified Toolset: As previously documented by Kaspersky.
Following the initial deployment of their toolset, GoldenJackal started exploiting vulnerabilities on previously compromised machines by employing a diverse array of malicious tools and tactics. In September 2019, our investigation revealed that PowerShell scripts were executed to install a malicious backdoor. This backdoor was utilized to execute various PowerShell scripts, as well as obtain and run reliable tools analogous to Cobalt Strike and Mimikatz.
Between September 2019 and January 2024, a comprehensive analysis revealed that GoldenJackal’s arsenal had expanded to include the following sophisticated tools.
- JackalControl,
- JackalSteal, a sophisticated file collector and exfiltrator,
- The notorious JackalWorm: a malware that once thrived by spreading malicious payloads via compromised USB drives. We detected the JackalControl backdoor spreading its malicious payload.
Since these elements have already been thoroughly documented elsewhere, we’ll focus on exploring their implications and applications in our upcoming discussion. Nevertheless, one fascinating level to say is that in early variations of those instruments, URLs for C&C servers have been hardcoded within the malware binaries. In some unspecified time in the future, GoldenJackal modified JackalControl and JackalSteal to obtain C&C servers as arguments.
What’s driving the latest innovation in community engagement: Staying relevant through meaningful interactions?
In May 2022, our analysts observed GoldenJackal leveraging a novel suite of tools to target a European government entity. The majority of these instruments are developed in Go, providing a multitude of functionalities, such as aggregating data from USB drives, disseminating payloads throughout the network via USB drives, extracting sensitive information, and leveraging certain PCs on the network as servers to transmit diverse data to various applications. As observed, attackers have successfully exploited lateral movement tactics within the network.
As attacks intensified, GoldenJackal adapted an exceedingly flexible approach, leveraging diverse components to execute multiple functions seamlessly. Some hosts have been exploited to exfiltrate sensitive data, while others have been leveraged as native servers to obtain and disseminate pre-staged information or configuration details, and a few have been identified as attractive targets for file collection, potentially facilitating espionage activities. The periodic table is structured into five categories: Metals, Nonmetals, Metalloids, Noble Gases, and Representative Elements.
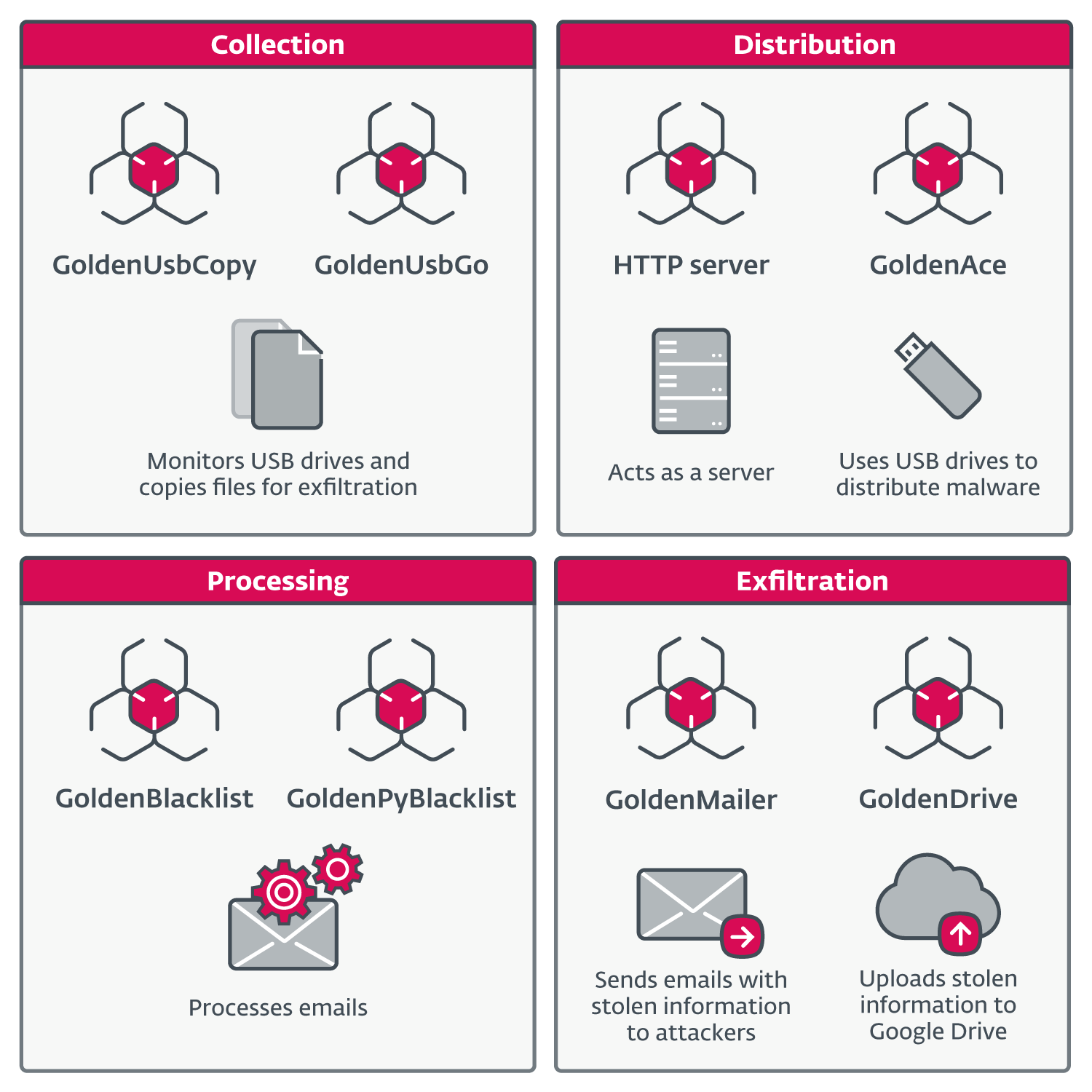
Without observing any exterior IP addresses in the examined components, our analysis did not uncover any community infrastructure features. File exfiltration techniques often leverage publicly available cloud storage services like Google Drive or utilize compromised email infrastructure via protocols such as Outlook’s SMTP servers.
GoldenUsbCopy
The GoldenUsbCopy, classified as a group component, visually indicates the insertion of USB drives, securely copying intriguing data into an encrypted container stored on disk, awaiting exfiltration by various entities. According to the binary analysis, the main package name of the application is unidentified.
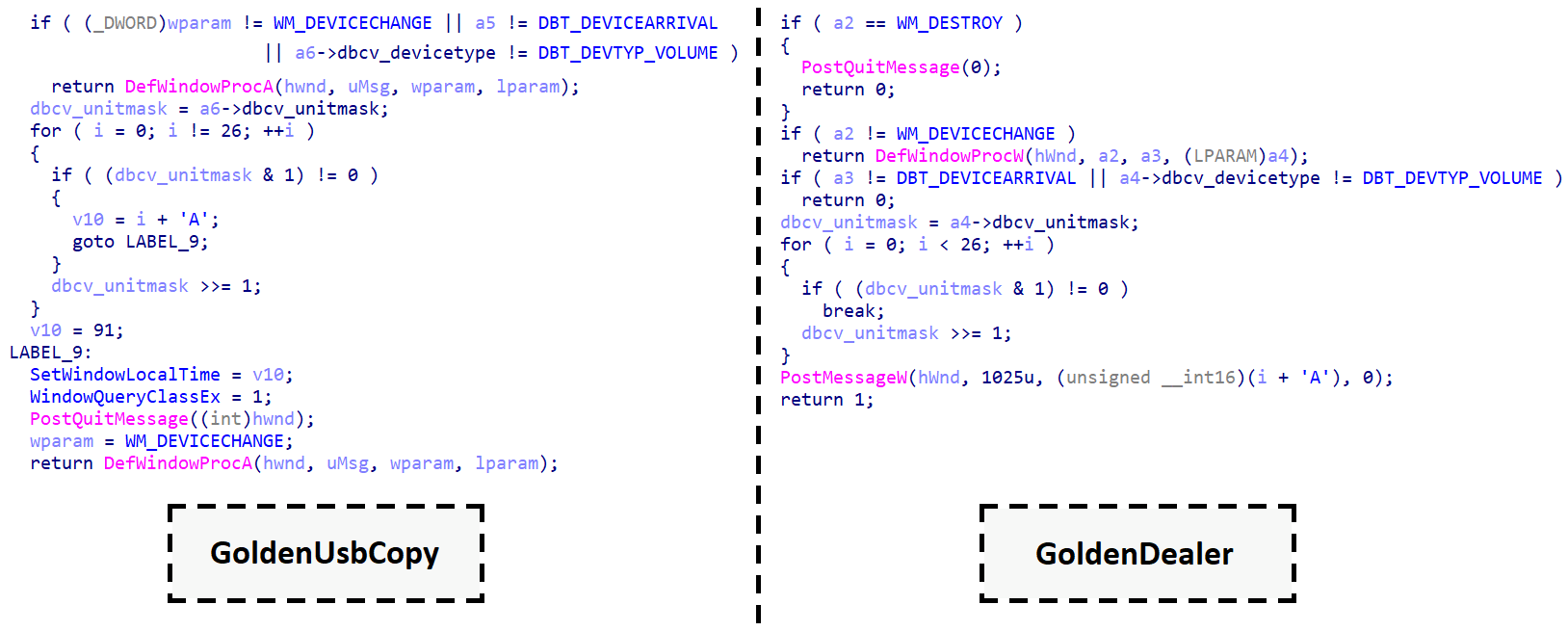
When newly installed drives are detected, a graphical window appears, prompting the user to identify the drive and provide system information. This is achieved through a customized handler that captures the necessary data and provides it for further analysis. When a handler processes a message featuring a specific occasion sort and a corresponding machine sort, it suggests that a fresh drive can now be handled. Determining similarity in 6 lines of code reveals a direct comparison between decompiled code from GoldenUsbCopy and GoldenDealer. Despite being written in a specific programming language, it becomes apparent that the code retrieves the drive’s letter to initiate the process in a similar manner.
The GoldenUSB Copy application identifies which data to extract from a USB drive according to a predefined configuration securely stored in an AES-encrypted file using Cipher Feedback (CFB) mode. The 32-byte key used to decrypt the configuration is embedded directly into the malware’s code. After decryption, the configuration consists of the following fields in JSON format:
- The encrypted archive, denoted by its full path, serves as a secure repository for diverse data, analogous to catalogs of file names from newly installed storage devices, and sensitive intelligence intended for surreptitious extraction.
- A public key to encrypt Advanced Encryption Standard (AES) keys that potentially may be utilized to encrypt data intended for exfiltration.
- Information that has been finalized more than a specified number of days ago is typically not considered for processing.
- A database containing SHA-256 hashes of data potentially extracted for exfiltration purposes.
- The registry stores a catalog of hash values.
- The maximum amount of data that a storage device or computer system can hold is referred to as its total byte capacity.
- Information larger than 1 MB, in bytes, are usually not exfiltrated, and
- A list of file extensions used for data exfiltration: .docx, .xls, .csv, .txt.
Once the configuration has been successfully decrypted, GoldenUsbCopy enters a wait state, anticipating the insertion of a USB drive. The contents of the inserted drive are cataloged and compiled into a text-based document, subsequently packaged within a ZIP archive, whereupon it is secured using Advanced Encryption Standard (AES) technology, ultimately being appended to. The encrypted container is then written to disk, while intermediate steps, which involve textual content information and archives, are retained in memory.
Data that meets the criteria for exfiltration undergoes a comparable procedure: this information is aggregated and preserved in its original hierarchical structure, then securely encrypted using AES, before being consolidated into a single entity. During the process of selecting data for unauthorized transfer, a digital list featuring SHA-256 hash values is obtained from the system’s registry. If the hash of a file matches the one on the checklist, then exfiltration has been prevented. If the hash doesn’t meet the criteria outlined in the checklist, it is added to ensure the file cannot be re-exfiltrated.
In instances where the volume of exfiltrated data exceeds a predetermined threshold, excess information is typically omitted from the archival process for exfiltration purposes. Instead, the corresponding directory paths are recorded in an encrypted text file and stored within the archive.
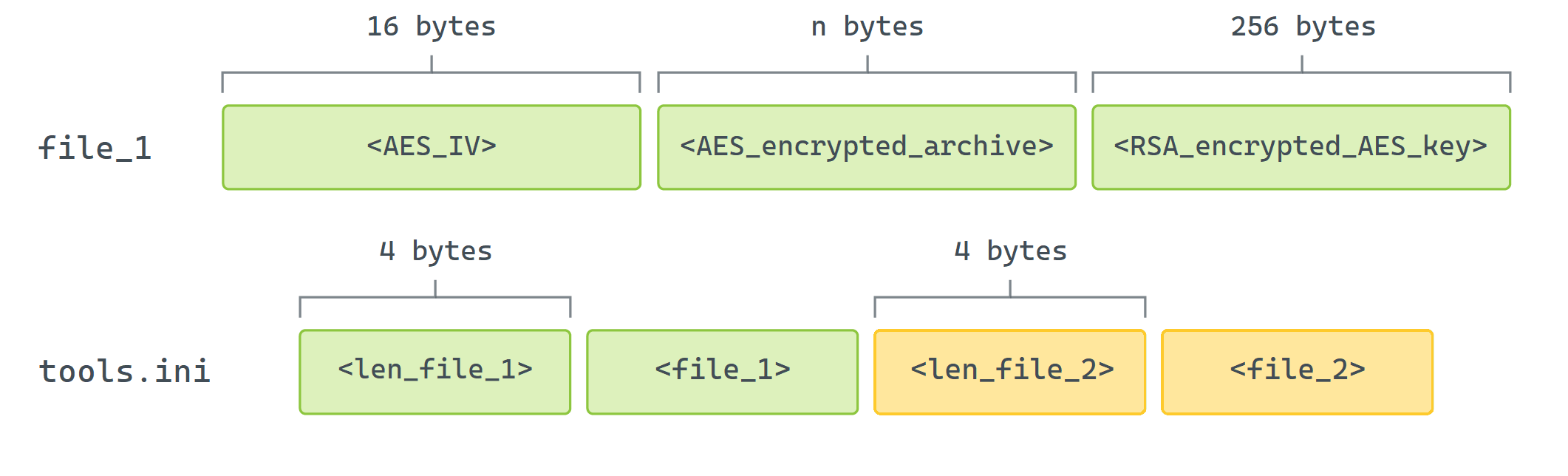
Each individual file archived within the encrypted container is secured through AES-encrypted in CFB mode, utilizing a unique key and initialization vector (IV), which are randomly generated upon addition. The critical components of the project, namely the essential items (IV), require preservation. The determinative step in determining 7 reveals an instance where specific fields are stored securely within a digitally shielded repository.
GoldenUsbGo
Based on telemetry insights and analysis of Go variants employed in compilation, this component shares similarities with the GoldenUsbCopy, likely representing a more advanced iteration, developed subsequent to its observation in our data. Notwithstanding the added complexity, GoldenUsbGo’s straightforward design yields identical performance.
- There isn’t any configuration file. All criteria for file selection are embedded directly within the malicious code.
- When a filename contains a chosen phrase from a list, regardless of other criteria (the list consists of strings like “and” or “or”),
- Else, files with measurements must not exceed 20 megabytes.
- The file’s most recent modification date must be no older than 14 days, and
- The file must have a single extension from among .docx, .pdf, .txt, .jpg, or .xlsx.
- The repeated insertion of detachable drives is often left unmonitored. Does a scheduled scan monitor the pre-defined list of drive letters to detect instances where allocated quantities equal one, two, three, or four?
- The list of hashed data processed thus far is stored exclusively in memory.
- There is no measurement restriction for the encrypted container where information is staged for exfiltration.
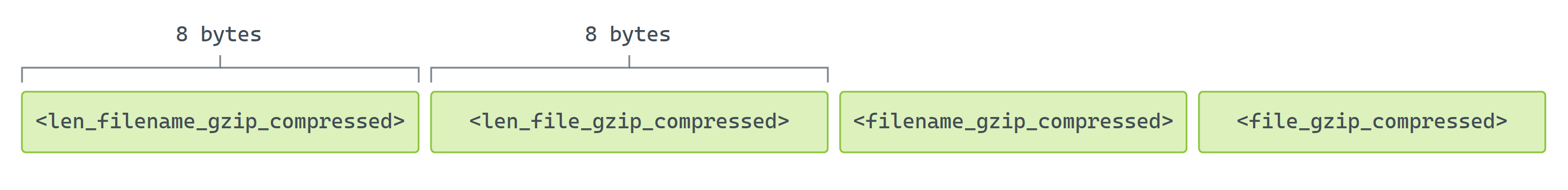
- Data records are typically not archived; instead, they are compressed using gzip. Files containing content are compressed along with their corresponding filenames. Determination of compression techniques precedes encryption methods in organizing data?
The path leading to the encrypted container is irreversibly embedded within the malicious code itself.
The incorporation of a hardcoded username within the path, previously censored, along with a concise list of drives and specific file names, provides conclusive evidence that GoldenUsbGo was custom-built for this individual victim.
Data compressed and encrypted using AES-256 in Cipher Feedback (CFB) mode with a predefined encryption key. Although the construction resembles that of GoldenUsbCopy, proven in Determine 7, this version lacks an AES key. Upon compression, GoldenUsbGo creates a comprehensive inventory of the inserted drive’s contents, mirroring the same procedure used for exfiltrating data. The filename for the itemizing is fashioned from the present date and time, formatted as (e.g., YYYYMMDD_HHMMSS).
GoldenAce
The component, classified as a distribution tool in our assessment, disseminates various malware variants and retrieves pre-positioned data by utilizing USB drives as a vector of propagation. While it may be suitable for focusing on air-gapped programs, its design does not specifically prioritize this capability over that of GoldenDealer. While this combination proves effective, featuring a lightweight framework and an unidentifiable component.
GoldenAce periodically verifies drives against the checklist to identify ones mapped to a specific quantity. The script then verifies whether any trash listings exist at the root level of that particular drive. When a non-existent directory is encountered, it is automatically created in a hidden state, and a file called “replace” is then duplicated into this newly generated listing, sourced from the same location where GoldenAce is functioning.
The primary directory, listed in alphabetical order, that is not hidden is now prepared for hiding. A file named [file name] is copied to the root of the drive and renamed as [new name].
The file, identified as JackalWorm, is an executable that employs a folder icon, designed to repeatedly execute and propagate itself onto another system when a USB drive is inserted. Unlike the notorious Jackal Worm as depicted by Kaspersky, this variant is significantly more limited; it lacks the ability to monitor drive insertions, and its functionality cannot be customized to execute multiple actions. Upon execution on a detachable drive’s base directory, this malware initiates Windows Explorer to access a concealed folder, then generates a batch script to run the payload within. The contents of this study are thoroughly established and verified in Chapter Nine.
@echo off copy "<drive_letter>:trashreplace" "C:Customers%username%AppDataNativereplace.exe" "C:Customers%username%AppDataNativereplace.exe" "<drive_letter>:trash" :check1 @tasklist | findstr /i /b "replace.exe" >nul @if %errorlevel%==0 goto check1 @del /f /q /a h "C:Customers%username%AppDataNativereplace.exe" @del /f /q "C:Customers<username>AppDataNativereplace.bat"Determine 9. Contents of
When executed, the script is automatically run and deleted along with its corresponding batch file once its intended operation is completed. While we did not inspect the component’s contents, it likely accumulates data and organizes it within a directory on a removable storage device, since the path to this directory is passed as an argument to the method.
When GoldenAce detects that a listing already exists on a drive, rather than copying data to the drive, it duplicates the information within the listing to.
HTTP server
When running our application, we’ve observed that it’s bundled with PyInstaller and launched via a dot file. Unfortunately, we did not review the file’s contents, which means we are unaware of the parameters passed during execution, including crucial details like the port number that the server should listen to.
GoldenBlacklist
As a processing component, GoldenBlacklist downloads an encrypted archive from a neighboring server, then processes email messages within it, carefully maintaining only those of interest. As soon as the process concludes, a fresh, dedicated repository is created for further data extraction.
The URL to retrieve the preliminary archive is dynamically configured. The downloaded file is saved with the name , and then AES-decrypts it using a hardcoded key through a dependable executable program.
When the encrypted archive is successfully decrypted, its contents are extracted for analysis. Only data that meets specific quality criteria is then written to a designated subfolder within the directory where the malware is executing. Standards:
- There are no electronic mail addresses listed that would trigger a spam filter’s blocklist. To eliminate electronically delivered mail messages that typically originate from uninteresting senders. While we cannot fully explore the comprehensive list here, it is worth noting that many email addresses are linked to newsletters and press releases. One must acknowledge that crafting such a meticulous list would require a significant amount of time and effort from the perpetrators.
- The file consists of a single character, namely a period. These are electronic mail messages with attachments that mirror the format of PDF files, Microsoft Office documents, and archives, among others.
Upon selecting the desired information, GoldenBlacklist stores the listing in a secure archive, encrypting it with the same cryptographic key used for initial data decryption. The ensuing file is . Upon deletion of the intermediate information and folders, all data including,, and situated within the malware’s directory is also removed. It appears that another component, which we didn’t initially monitor, replicated these trustworthy executables in their original state from the outset.
GoldenPyBlacklist
The GoldenPythonBlacklist: A Pythonic Implementation of GoldenBlacklist. The executable file generated by PyInstaller is packaged with a unique identifier. There exist diverse alternatives to this aspect.
- the preliminary archive is written in a rough outline format
- The crucial aspect for deciphering lies in similarities, with one notable exception being the initial character.
- The decrypted archive is successfully extracted and stored in a temporary folder for processing purposes.
- One additional criterion for file selection is introduced during the processing of exclusively file names ending with (.pst), which are files generated by Microsoft Outlook.
- Information that fails to meet the criteria is eliminated.
- The ultimate archive is produced using the powerful 7-Zip archiving tool.
- .tar
GoldenMailer
GoldenMailer, categorized as an exfiltration module, facilitates the theft of sensitive data by transmitting emails containing attachments to maliciously controlled email accounts. The unique identifier of the script is `.py`. GoldenMailer seamlessly integrates with multiple email service providers – including Gmail and Outlook – to send electronic mail messages using the reliable SMTP protocol on port 587.
The configuration is learned from a file located in the same directory where GoldenMailer is operating. The configuration comprises five sequential traces.
- Electronic mail handles are used to authenticate with the SMTP server, serving both as a sender and destination identifier.
- SMTP authentication credentials are required.
- Path to archived listings for exfiltrating sensitive data.
- base filename (e.g. `archive_`) used for archives to exfiltrate; these archives utilize a sequential naming convention:, thereby facilitating efficient archival organization.
- variety of information to exfiltrate.
We found evidence suggesting that this configuration file originated from another PC within our local network. Given that the configuration file specifies a threshold for identifying potentially exfiltrated archives, we infer that those archives would need to be replicated across the network, distinguishing between tasks such as curation, dissemination, and extraction. The suspected configuration file was likely created by the entity responsible for gathering data and preparing it for unauthorized transfer, but unfortunately, our investigation did not involve examining this component.
The system determines that a specific email sent by GoldenMailer has been successfully delivered and is now accessible for viewing or retrieval. Improve as: The topic has a typo; it reads “it’s”. What does this sentence mean? The hardcoded strings within the malware’s binary are immutable and tightly coupled with its functionality. Multiple attachments are distributed electronically when multiple files need to be exfiltrated, with each email containing a single archive.
The configuration information revealed a list of subsequent electronic mail addresses.
GoldenDrive
Compared to GoldenMailer, this component siphons data by uploading it to Google Drive. The required credentials are embedded in two distinct sections of the malicious code, featuring attributes akin to username/password combinations and API keys/auth tokens. Discovery of references to Google Drive’s API, along with code snippets written in the Go programming language.
Like GoldenMailer, this feature allows for the addition of a single file at a time? The GoldenDrive command is triggered by supplying a full path to the file intended for addition.
Conclusion
In a recent blog post, we exposed two novel toolsets employed by the GoldenJackal Advanced Persistent Threat (APT) group to target air-gapped systems of government agencies, including those in Europe. Malicious actors often exploit the convenience of USB drives to illicitly acquire sensitive documents.
The notorious GoldenJackal group has successfully developed and deployed not one, but two sophisticated toolsets to breach air-gapped networks within an impressive five-year timeframe, showcasing its exceptional adaptability and understanding of its adversaries’ community segmentation strategies?
A comprehensive checklist of indicators of compromise (IoCs) may include.
IoCs
Recordsdata
|
|
|
|
|
| DA9562F5268FA61D19648DFF9C6A57FB8AB7B0D7 |
| Win32/Agent.AGKQ | GoldenDealer. |
| 5F12FFD272AABC0D5D611D18812A196A6EA2FAA9 |
| Python/Agent.ANA Python/HackTool.Agent.W Python/Riskware.LdapDump.A Python/Riskware.Impacket.C | GoldenHowl. |
| 6DE7894F1971FDC1DF8C4E4C2EDCC4F4489353B6 | OfficeAutoComplete.exe | WinGo/Agent.AAO | GoldenRobo. |
| 7CB7C3E98CAB2226F48BA956D3BE79C52AB62140 |
| WinGo/DataStealer.A | GoldenUsbCopy. |
| 8F722EB29221C6EAEA9A96971D7FB78DAB2AD923 |
| WinGo/Spy.Agent.AH | GoldenUsbGo. |
| 24FBCEC23E8B4B40FEA188132B0E4A90C65E3FFB |
| WinGo/DataStealer.C | GoldenAce. |
| A87CEB21EF88350707F278063D7701BDE0F8B6B7 |
| MSIL/Agent.WPJ | JackalWorm – less complicated model. |
| 9CBE8F7079DA75D738302D7DB7E97A92C4DE5B71 |
| WinGo/Spy.Agent.CA | GoldenBlacklist. |
| 9083431A738F031AC6E33F0E9133B3080F641D90 |
| Python/TrojanDownloader.Agent.YO | GoldenPyBlacklist. |
| C830EFD843A233C170285B4844C5960BA8381979 |
| Python/Agent.ALE | GoldenMailer. |
| F7192914E00DD0CE31DF0911C073F522967C6A97 |
| WinGo/Agent.YH | GoldenDrive. |
| B2BAA5898505B32DF7FE0A7209FC0A8673726509 |
| Python/Agent.ALF | Python HTTP server. |
Community
| N/A | Orange Polska Spolka Akcyjna | 2019‑08‑09 | Major C&C server utilized by GoldenJackal in 2019. | |
| N/A | UTANDE | 2019‑08‑09 | Secondary C&C server utilized by GoldenJackal in 2019. | |
| N/A | N/A | 2019‑09‑25 | A compromised website was allegedly utilized to spread malicious software. | |
| N/A | N/A | 2019‑09‑25 | Compromised web site used as a C&C server. | |
| N/A | N/A | 2019‑09‑25 | Compromised web site used as a C&C server. |
E-mail Addresses
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework
| Purchase Infrastructure: Digital Personal Server | GoldenJackal in all probability acquired a VPS server to make use of as a secondary C&C server for the GoldenDealer malware. | ||
| Purchase Infrastructure: Server | GoldenJackal probably acquired a server to make use of as a major C&C server for the GoldenDealer malware. | ||
| Compromise Infrastructure: Net Companies | GoldenJackal has used compromised WordPress websites for C&C infrastructure, utilized by the JackalControl and JackalSteal malware. | ||
| Develop Capabilities: Malware | The notorious hacker GoldenJackal crafts a bespoke malware to wreak havoc. | ||
| Set up Accounts: Cloud Accounts | Golden Jackal has utilized Google Drive to store both exfiltrated data and authentic instruments. | ||
| Acquire Capabilities: Software | Utilizing trusted tools akin to Plink and PsExec, GoldenJackal leverages these robust instruments for executing post-compromise operations with precision. | ||
| Command and Scripting Interpreter: PowerShell | The notorious GoldenJackal actor allegedly leveraged PowerShell scripting to procure the malicious JackalControl malware from a previously compromised WordPress website, showcasing their advanced capabilities in digital forensics and threat intelligence. | ||
| Command and Scripting Language: Windows PowerShell | The GoldenAce malware utilizes its capabilities to execute a batch script that carries out various malicious operations. | ||
| Command and Scripting Interpreter: Python | The GoldenHowl malware suite encompasses a multitude of nefarious modules, potentially comprising Python-based scripts. | ||
| Native API | Using the GoldenDealer API, a developer can execute a binary file programmatically without manual intervention. | ||
| System Companies: Service Execution | GoldenDealer can be configured to operate as a Windows service, allowing it to automatically start and manage transactions without user intervention. | ||
| Consumer Execution: Malicious File | The JackalWorm malware uses a deceitful folder icon as bait, enticing unsuspecting victims to unwittingly launch the malicious program. | ||
| The Windows Service system course has been designed to provide a comprehensive overview of the essential elements and best practices for creating and modifying Windows services. This course is tailored to meet the needs of IT professionals, developers, and system administrators who are responsible for managing and maintaining Windows-based systems. **Course Objectives:** * Understand the fundamental concepts of Windows services **Course Outline:** 1. Introduction to Windows Services **Course Format:** This course is delivered in a hands-on, instructor-led format, with interactive exercises and real-world scenarios to reinforce learning. Students will have the opportunity to work on practical projects and exercises that demonstrate their understanding of Windows services. **Prerequisites:** Basic knowledge of Windows operating systems and programming concepts (such as C#) are recommended but not required. | GoldenDealer establishes a foothold on a compromised system, perpetuating its malicious presence. | ||
| When a user boots up their Windows machine, various programs and processes initiate automatically. These autostart entries are stored in the registry under two keys: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run and HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. Additionally, users can also add startup items to the Startup folder located at C:\Users\ | If GoldenDealer is unable to generate a service for persistence, a new entry is added to the Run registry key as a fallback solution. | ||
| Scheduled Process/Job: Scheduled Process | GoldenHowl orchestrates a meticulously planned process to ensure persistence is achieved on schedule. | ||
| Concealing Artifacts: Hidden Files and Folders | GoldenDealer adjusts Windows Registry settings to conceal hidden files and folders from being displayed in Windows Explorer. Malicious malware such as GoldenDealer, GoldenAce, and Jackal Worm have the ability to conceal folders on USB drives. | ||
| Indicator Removing: File Deletion | GoldenAce eliminates payloads once they have been executed. After deleting intermediate information, GoldenBlacklist and GoldenPyBlacklist remove all remaining data related to the ultimate archives. | ||
| What secrets do we uncover when we wear a mask? In today’s world of endless possibilities and infinite connections, it is crucial to understand the art of deception. | GoldenUsbCopy leverages a trusted Firefox browser listing to facilitate data staging. | ||
| Masquerading: Masquerade File Sort | The Jackalworm malware uses a folder icon to masquerade as a harmless, non-executable file, thereby evading detection and potentially compromising system security. | ||
| Modify Registry | To prevent hidden files and directories from being displayed in Windows Explorer, GoldenDealer tweaks the registry settings. | ||
| Encrypted or encoded files: Obscured Records | Utilising a diverse range of encryption algorithms, including XOR, Fernet, and Advanced Encryption Standard (AES), GoldenJackal’s comprehensive toolkit safeguards sensitive configuration data and exfiltrated information with robust cryptographic protection. | ||
| Unsecured Credentials: Credentials In Recordsdata | Files bearing seemingly innocuous names may actually contain sensitive credential data, potentially vulnerable to the GoldenUsbGo threat. | ||
| Unsecured Credentials: Personal Keys | GoldenUsbGo appears for information which will include personal keys, analogous to those with filenames that contain .pem or .key? | ||
| Account Discovery: Native Account | The GoldenDealer malware collects sensitive information from all compromised user accounts on an affected system. | ||
| File and Listing Discovery | GoldenHowl boasts a module for generating a comprehensive inventory of system data and directories, providing valuable insights into a compromised system’s infrastructure. GoldenUsbCopy and GoldenUsbGo produce comprehensive listings of files and folders on a USB drive. | ||
| Community Service Discovery | GoldenHowl enables remote systems scanning, identifying open ports, and assessing susceptibility to EternalBlue attacks. | ||
| Peripheral Machine Discovery | Two software utilities, GoldenDealer and GoldenUsbCopy, track the installation of removable storage devices. GoldenUSBGo and GoldenAce scrutinize multiple drive letters to identify attached removable drives. | ||
| Course of Discovery | A forensic investigator gathers crucial information regarding the functioning procedures of a system that has been breached. | ||
| Distant System Discovery | GoldenHowl can utilize its scanning capabilities to identify a wide range of IP-based programs? | ||
| Software program Discovery | GoldenDealer acquires sensitive information regarding submitted applications from a previously breached computer system. | ||
| System Info Discovery | GoldenDealer extracts exhaustive information regarding the operational framework and user profiles from a breached computer infrastructure. | ||
| What community configuration discovery tools are used for web connection discovery? | The GoldenDealer software allows users to toggle internet connectivity for a computer, permitting control over online access. | ||
| Community Share Discovery | GoldenAce inspects a directory of potential drive letters that could potentially include shared community resources. | ||
| Exploitation of Distant Companies | GoldenHowl can utilize Windows SMB protocol to detect and exploit remote code execution vulnerabilities allowing potential lateral movement opportunities. | ||
| Replication via detachable media: A Novel Approach to Data Transfer. | The GoldenDealer tool efficiently transfers executable files between USB drives, thereby allowing users to concentrate on executing air-gapped software applications. Malware authors leverage detachable drives to distribute and propagate GoldenAce’s harmful executables. | ||
| The archive process of collected information has been successfully executed via library protocols. | Golden Robo and Golden USB Copy archives information to be exfiltrated using the ZIP library. | ||
| Automated Assortment | When a newly connected external drive comes into view, GoldenUsbCopy and GoldenUsbGo automatically prepare the data for future extraction. | ||
| Information from Native System | Instruments within GoldenJackal’s toolkit gather data and insights from their native environment. | ||
| Information from Detachable Media | GoldenUsbCopy and GoldenUsbGo efficiently aggregate captivating data from removable storage devices. GoldenAce enables users to effortlessly recover stored data from a removable storage device, specifically targeting files staged for retrieval on a chosen directory list. GoldenDealer enables users to extract sensitive data from compromised software, conveniently stored on a removable storage device for quick analysis. | ||
| Information Staged: Native Information Staging | The majority of instruments within GoldenJackal’s toolset are designed to process and manage various data elements domestically, facilitating both ingestion and extraction operations seamlessly. | ||
| E-mail Assortment: Native E-mail Assortment | A comprehensive blacklist, comprised of malicious email addresses and patterns, gathered through the GoldenJackal toolkit, facilitates enhanced filtering and detection capabilities. | ||
| Utility Layer Protocol: Net Protocols | GoldenDealer and GoldenHowl utilize secure HTTPS protocols to facilitate secure communication between their systems. | ||
| Effective communication relies heavily on the ability to convey complex information in a clear and concise manner. | A GoldenDealer leverages removable media to transfer executable files between isolated systems, including air-gapped networks, and subsequently extracts relevant information from these systems for transmission to connected networks. | ||
| Information Encoding: Normal Encoding | Executable information despatched from the C&C server to GoldenDealer are base64 encoded. | ||
| Protocol Tunneling | GoldenHowl can transmit ahead messages securely via a secure shell (SSH) tunnel. | ||
| Proxy: Inside Proxy | Here is the rewritten text in a professional style: Golden Howl acts as a proxy, seamlessly forwarding packets with precision and reliability. | ||
| Exfiltration Over C2 Channel | GoldenHowl exfiltrates information through the identical channel used as its C&C. | ||
| USB-based data exfiltration schemes have emerged as a significant threat to organizations, allowing attackers to siphon sensitive information from compromised devices. | GoldenJackal’s sophisticated toolkit empowers operators to covertly extract sensitive data from air-gapped systems by repeatedly transmitting information via removable media, ultimately facilitating clandestine exfiltration processes. | ||
| Exfiltration over Net Service (EoNS): Securely transmitting sensitive data to cloud storage. | GoldenDrive potentially transfers sensitive data to a maliciously controlled Google Drive location. | ||
| Unidentified Communication Method: Data Transfer Utilizing Insecure, Unencrypted Network Path | The GoldenMailer malware leverages the Simple Mail Transfer Protocol (SMTP), relying on STARTTLS encryption on port 587 to exfiltrate sensitive data. |

