Russian-speaking cybercrime collective “Doppelganger”, notorious for its phishing and malware operations that have allegedly cost victim organizations a staggering $3 billion since 2013, was officially dismantled last year by US authorities. authorities. Despite claims from consultants, Fin7 appears to have revived in 2024, spawning thousands of websites impersonating various media and expert organizations, allegedly leveraging the services of a prominent internet hosting provider notorious for facilitating cyberattacks targeting Russia’s adversaries.
In Could 2023, the U.S. Following a successful prosecution, Washington state law enforcement secured convictions and incarceration for three individuals identified as key players within the notorious cybercrime collective Fin7. This bold statement was a defiant challenge to a coalition of countries by the U.S. The Department of Justice has characterized a criminal organization comprising over 70 people, structured into various enterprise models and cells.
In April 2024, telltale signs of Fin7’s resurgence emerged, as we reported on a significant automotive company being breached through targeted attacks against users seeking a popular free network scanning tool.
Researchers at a safety agency have developed an approach to track the evolution of Fin7’s dynamic cybercrime infrastructure, comprising more than 4,000 hosts that employ a diverse range of exploitation tactics, including typosquatting, booby-trapped advertisements, malicious browser extensions, and spearphishing domains.
According to Silent Push, the organization has identified Fin7 domains targeting or mimicking those of well-known manufacturers such as, among others: ASUSTek, Canon, Dell, HP, Intel, Lenovo, Microsoft, Nikon, Oracle, Samsung, Sony, Toshiba, Western Digital, and Xerox.
As reported by a senior menace analyst at Silent Push, many Fin7 domains appear as innocuous-looking websites for generic companies, featuring default website templates that often contain irrelevant textual content bearing no relation to the entity’s stated business or purpose.
According to Edwards, Fin7 utilizes this tactic to artificially age the domains, thereby creating a veneer of legitimacy and benign popularity before reassigning them for use in phishing attacks targeting specific hosting brands.
“It took them approximately six to nine months to scale up,” Edwards noted of the cybercriminal outfit, “but since January, they’ve been thriving, building an extensive phishing infrastructure and acquiring aged domains.”
In Fin7’s typosquatting attacks, the group registers domains that mimic those of popular, free software tools. Fake domain names are subsequently advertised on Google, ensuring that paid links to these sites appear prominently in search results, typically above the authentic source of the software being sought.
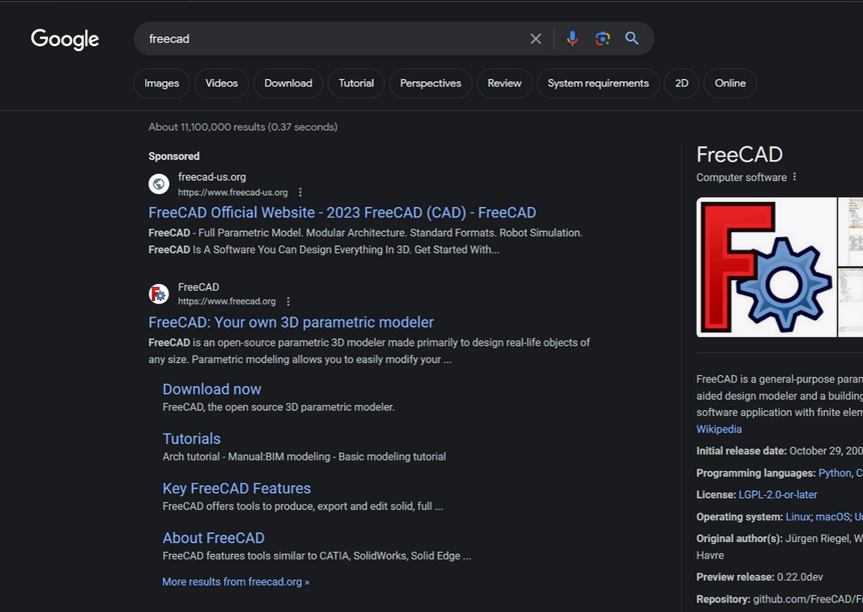
A malicious website posing as FreeCAD emerged prominently as a sponsored result in Google search outcomes earlier this year.
The Fin7 group is currently concentrating on a software application, Silent Push, which comprises tools for malware propagation, command-and-control functionality, lateral movement, privilege escalation, data exfiltration, network reconnaissance, and remote access.
By May 2024, cybersecurity experts discovered that the notorious cybercrime group Fin7 had been exploiting Google’s advertising platform to distribute malicious pop-ups, luring victims into installing fake browser extensions that installed malware on their devices. In April, the exercise was undertaken without attributing it to a particular group.
At our Thomson Reuters typosquatting area, we kindly request that you consider installing a reliable browser extension to access the rich information content.
Following a tip-off from a company previously targeted by Fin7, Edwards announced that Silent Push had discovered newly registered Fin7 domains, indicating the gang’s potential resurgence. After conducting a search for hosts matching Fin7’s identified profile, we found only one promising website exhibiting high energy levels. According to Edwards, one website linked numerous Fin7 assets to Stark Industries Options, a relatively new internet hosting provider that emerged just two weeks prior to Russia’s invasion of Ukraine.
Stark Industries’ options have been exploited as a launching pad for successive waves of cyberattacks targeting Ukraine, with ties to the Russian military and intelligence agencies.
“According to Edwards, FIN7 has rented a substantial quantity of dedicated IP from Stark Industries.” “Our analysis has uncovered several Stark Industries IP addresses that can be dedicated exclusively to supporting FIN7’s online infrastructure.”
FIN7, infamous for its sophisticated tactics, concealed its operations behind a veil of authenticity by creating fake cybersecurity firms, such as and , to provide cover for its malicious activities, ultimately facilitating devastating ransomware attacks. One of several newly identified Fin7 domains, recognized by Silent Push, is a website that purports to “help develop your online business with our IT, cybersecurity, and cloud solutions.”
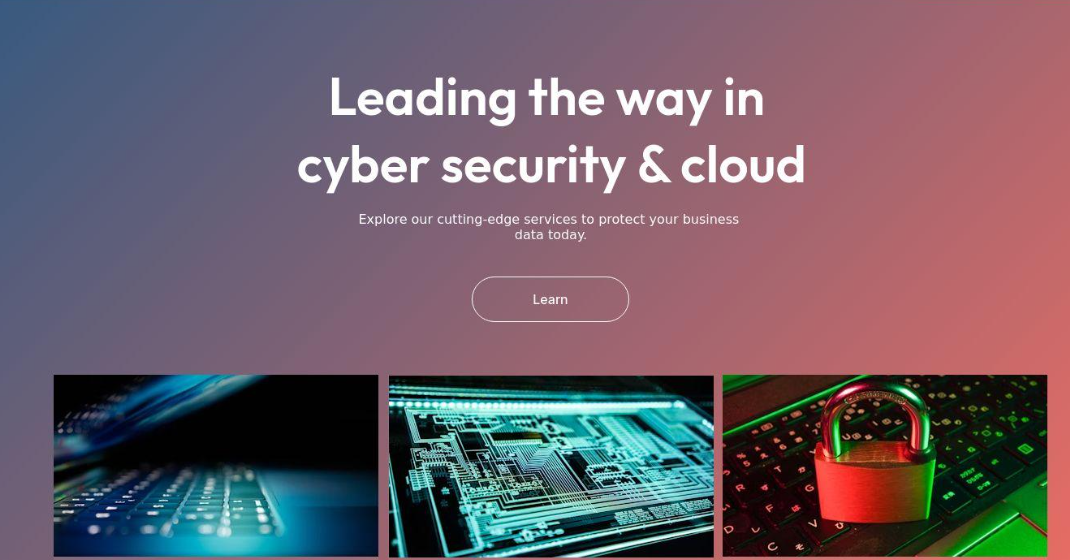
The Pretend Fin7 Safety Agency: Cybercloudsec?
Like various phishing groups, Fin7 exploits current events, simultaneously targeting travelers visiting France for the upcoming Summer Olympics. Among the numerous newly identified Fin7 domains, Silent Push uncovered a multitude of websites engaged in phishing schemes targeting individuals seeking tickets.
“We believe our findings unequivocally demonstrate that the notorious Fin7 group is once more accelerating its malicious activities at an alarming rate.” “We anticipate that law enforcement authorities will take note of this development and prioritize Fin7 as a target for intensified enforcement efforts. Furthermore, we hope that several of our adversaries will draw inspiration from this pool and significantly invest in building their own infrastructure.”
Additional studying:
.
(PDF).

