
Most accomplished cybercriminals opt out of linking their real identities to their hacker pseudonyms. Despite being an old-school breed, some Russian hackers still follow the tradition of concealing their real-life identities by keeping a low profile and avoiding any telltale signs that might give away their true selves. A seminal study examining this enigmatic occurrence is known colloquially as “Sundown”, the pseudonym adopted by a renowned Russian cybercriminal with expertise in providing early access to various ransomware syndicates.
A notorious “entry dealer” named x999xx consistently peddles entry points into hacked corporate networks, typically comprising remote access credentials, as well as compromised databases replete with sensitive personal and financial data.
A cyber intelligence agency revealed in February 2019 that x999xx, a prominent member of a top-tier Russian-language cybercrime forum, frequently touted the sale of compromised databases and network login credentials.
In August 2023, x999xx acquired a stake in a company specializing in software development solutions for the real estate industry. In July 2023, x999xx launched an unauthorized marketing campaign targeting the entire United States population by offering to sell Social Security numbers, names, and birthdates. State properties (unspecified in the public offering).
Approximately a month prior, an anonymous individual posting under the handle ‘x999xx’ published a comprehensive thread detailing gross sales data for 80 databases allegedly sourced from Australia’s largest retail corporation. It’s likely that you’ll utilize this data to exact a ransom payment or employ it for a completely unrelated purpose, as x999xx remarked in the Exploit forum. Unfortunately, the vulnerability was rapidly remedied. As the data lies dormant, its potential unrealized, yet it remains untainted by malicious intent, poised to serve a purpose when circumstances align.
In October 2022, X999XX acquired an administrative foothold in the United States. healthcare supplier.
ALIAS: MAXNM
Here is the rewritten text:
The earliest recorded mention of the malware known as x999xx dates back to 2009, when it was first discussed on a Russian-language online forum under the email address. Ozersk is a city located in the Chelyabinsk region of western central Russia.
According to breach monitoring services, the handle maxnm@ozersk.com had been utilized over a decade ago to establish an account on VKontakte, Russia’s response to Facebook, under the pseudonym “Ozersk”. Mr. Kirtsov’s profile lists his birthdate as September 5, 1991, no quotation marks necessary.

Private photographs shared by Maxim on his Vkontakte account in 2016. Translation of the caption from Russian may have resulted in inaccuracies?
The individual, whose handle was x999xx, joined the Russian-language cybercrime forum in 2014 using the email alias.
According to Constella, this email handle was employed by an individual from Ozersk with Russia’s leading delivery service in 2022.
Prior investigations of contact information uncovered that before 2009, x999xx had a history of dealings with Maxnm on Russian cybercrime forums. A cyber intelligence firm traced the online identity ‘Maxnm’ to a 2006 registration on Zloy, originating from a web handle in Chelyabinsk and linked to an email address.
The same email address was employed to establish multiple user profiles on various criminal forums in 2005, including those on and from Chelyabinsk, as well as another platform in 2006.
A search in Constella for the Russian model of Kirtsov’s full title reveals a multitude of accounts linked to .
A comprehensive analysis of the digital footprint associated with maksya@icloud.com reveals that this handle was utilized approximately a decade ago to establish an active account under the alias x999xx at Apple’s iCloud platform. The account features an array of screenshots, including economic statements from multiple banks, chat logs with various hackers, and compromised websites, providing an extensive collection of digital evidence.
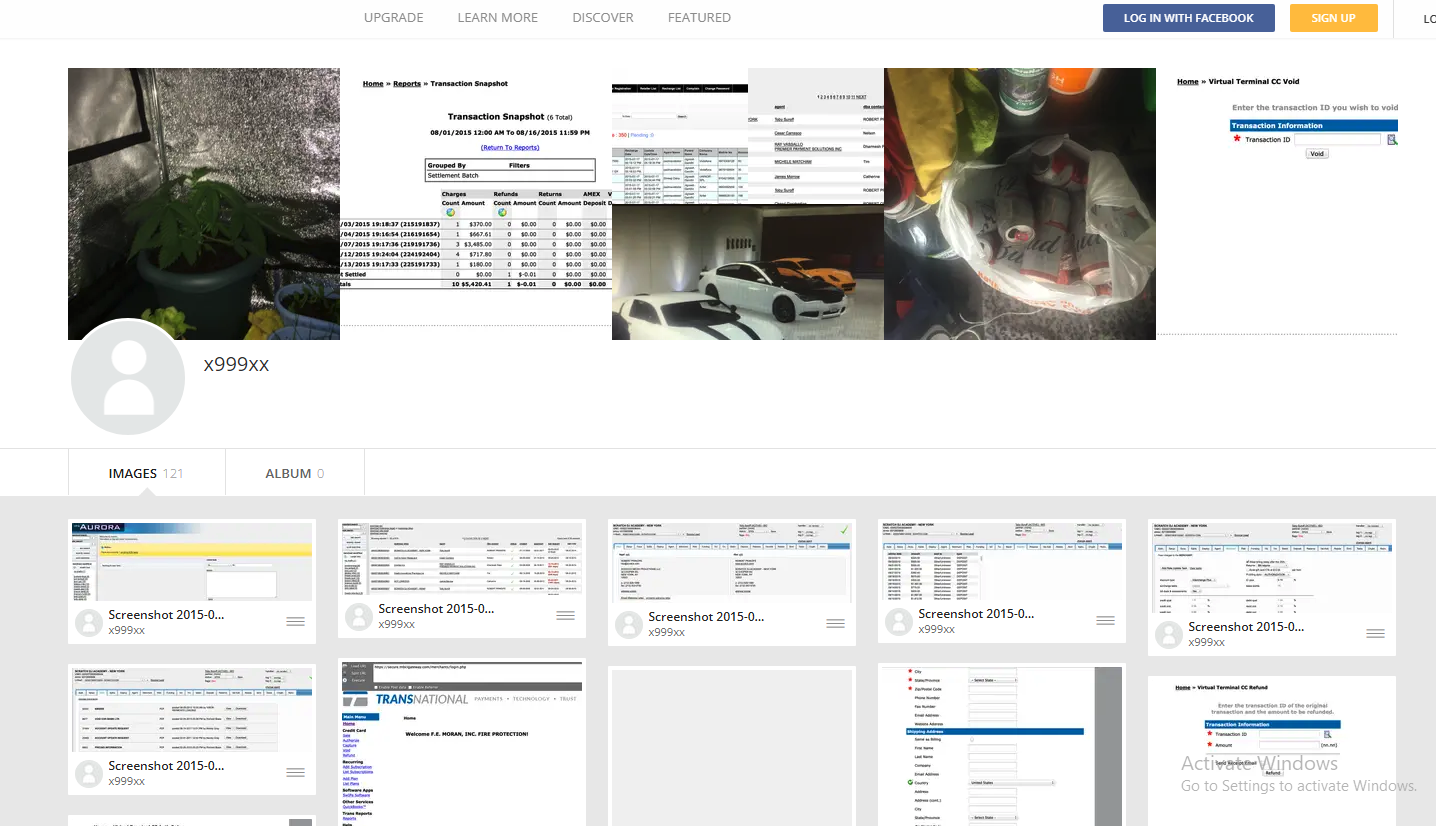
The x999xx’s Imageshack account features a curious assortment of digital artifacts, including snapshots of bank account statements from numerous financial institutions, as well as transcripts of online conversations with various hacking enthusiasts and amateur videography showcasing homemade cannabis cultivation.
A glance at the photographs within Kirtsov’s Imageshack account also reveals additional images appearing on his Vkontakte webpage, alongside photos showcasing his collection of cars and even snapshots of potting marijuana plants. According to Kirtsov’s Vkontakté profile, in 2012, he was a member of his college.
The Vkontakte webpage lists Kirtsov’s occupation as a reference to a website, apparently a blog chronicling life in Ozersk. Despite initial assurances, the safety agency’s 2019 investigation unexpectedly uncovered that this area had been compromised and was unwittingly hosting a malicious server.
Cobalt Strike is a commercial-grade community penetration testing and reconnaissance tool designed exclusively for authorized partners. However, stolen or illicitly obtained Cobalt Strike licenses are consistently exploited by cybercriminal organizations to facilitate the establishment of a foothold for ransomware deployment within compromised networks.
In August 2023, x999xx published a post on the Exploit forum, expressing his enthusiasm for purchasing a legitimate model of Cobalt Strike. About a month prior, x999xx lodged a formal complaint against a fellow forum member, seemingly a former acquaintance who had suddenly and mysteriously vanished from the community, leaving x999xx and other users in a state of uncertainty. Cybercriminals were hired by Cobaltforce, boasting expertise in leveraging Cobalt Strike to facilitate ransomware attacks, with the goal of monetizing access to compromised networks in exchange for a portion of the profits.
On the surface of Lake Ozersk, an email address is currently linked to a domain registration, which has also been utilised to register approximately 24 other domain names, including a . The vast majority of these domain names were registered to Maxim Kirtsov in Ozersk. Beneath lies a thought map used to track the identities discussed in this narrative.
Connections linking x999xx to Max Kirtsov: A visual representation of key relationships and shared attributes.
According to intel 471, x999xx, a prominent contributor on Russia’s “Gofuckbiz” online forum for webmasters, boasts an impressive record of more than 2,000 posts spanning nearly a decade. In a single submission from 2016, x999xx inquired about the whereabouts to acquire a heat lamp mimicking daylight, citing the distressing loss of his pet rabbit due to insufficient light and warmth. Mr. A series of archival footage on Kirtsov’s Vkontakte webpage primarily features caged rabbits from 2015 or earlier, comprising the majority of its visual content.
CONFIRMATION
Reaching out via email, I contacted Mr. Kirtsov acknowledged that he’s x999xx. According to Kirtsov, he and his team are also frequent readers of KrebsOnSecurity.
“We’re delighted to hear from you and take a closer look,” Kirtsov responded.
When questioned about his potential involvement in the authorized and ethical implications of his work, Kirtsov minimised his role in ransomware attacks, claiming a focus on data harvesting rather than malicious activities.
Kirsanov’s letter concluded with a tone of self-assurance: “I consider my commitment to moral principles to be on par with yours.” I’ve also launched into research and am currently mentoring students. As you likely discovered through publicly available information and the review of the innovative device, you may have noticed my contributions to an online forum, where my actions were made accessible to others.
“As I reflect on my previous posts advocating for entry promotion, I must candidly acknowledge that, in hindsight, I realize those mentions were never truly acted upon.” “It’s no surprise that market listings have significantly decreased as the majority of users exploit the discussion board for personal gain.”
Kirtsov claims to have no enthusiasm for compromising healthcare facilities, his sole aim being the illicit acquisition of their data.
According to Kirtsov, he was familiar with successful website owners willing to pay up to $50 per 1,000 health-related emails. As a direct result, my attention was exclusively focused on parsing through countless emails, with little regard for supplementary details like X-ray reports, insurance codes, or individual patient names. As a seasoned expert in SQL, I demonstrate exceptional comfort when handling data types such as IDs and email addresses. I am not in any way engaging in spam or anything like this.
According to Russian crime forums, x999xx claimed to exclusively focus on external targets, never targeting anyone or anything within Russia, and believed his activities posed minimal risk of attracting attention from domestic law enforcement agencies as long as they remained focused on international adversaries.
The lax approach to cybersecurity exhibited by x999xx bears a striking resemblance to that of another prominent Russian ransomware operator, who exploited vulnerabilities in multiple organizations while secretly running his own affiliate programs.
“Don’t sully the community where you live,” said Wazawaka, describing his personal guiding principle. “Travel locally, and don’t venture abroad.” Russia’s mom will help you too. Loving one’s nation often fosters loyalty and dedication, ultimately leading to success.
In January 2022, KrebsOnSecurity revealed the true identity of a 32-year-old individual from Khakassia, Russia. In May 2023, several ransomware groups, as key determinants, collectively extorted hundreds of thousands of dollars from victim organizations. The U.S. State DivisionIs providing information leading to the seizure and/or prosecution of Matveev?
In a bid to counter the perceived impunity enjoyed by many high-profile ransomware criminal groups operating from within Russia’s borders, Western regulatory agencies are shifting their focus towards disrupting the psychological dynamics that drive these individuals. Law enforcement agencies have developed targeted initiatives, codenamed “” , aimed at dismantling ransomware-as-a-service operations by infiltrating these illegal networks, disrupting the primary cybercrime providers, and undermining trust within criminal organizations.
When authorities within the U.S. and U.Ok. Introduced in February 2024, law enforcement agencies took control of the infrastructure previously utilized by the notorious ransomware gang, adopting LockBit’s victim shaming website design to link replacement press releases on the takedown, and featuring a countdown timer eventually replaced with private details of the individual involved.
In May 2024, law enforcement agencies in the USA and Europe launched a coordinated effort against several of the most prominent cybercrime platforms responsible for distributing ransomware and data-thieving malware. The Operation Endgame website featured a captivating countdown timer, subtly hinting at the imminent release of a series of high-energy, fast-paced animated advertisements reminiscent of those often used by cybercriminals to promote their online services in flashy, attention-grabbing ads.

