
Many people have moved past passwords alone for on-line safety, and it’s not laborious to see why. Our new Specops Breached Password Report discovered that of 1 billion stolen credentials, nearly 1 / 4 met customary complexity necessities – and nonetheless the criminals broke by.
These stolen passwords – 230 million of them – met all the necessities of their group, together with greater than eight characters, one capital letter, a particular character and a quantity.
And there’s a lot extra proof of password vulnerabilities: Verizon’s Knowledge Breach Investigations Report (DBIR) 2024 discovered that stolen credentials have been the high motion resulting in a breach.
Alternate options to passwords
So it’s little marvel that new and evolving authentication strategies have gained traction lately. However may they substitute passwords altogether? We predict the reply is a possible ‘no’. Passwords will stay a key safety ingredient for many orgniazations, with further authentication strategies used to reinforce defenses.
First, let’s take a look at among the growing alternate options and applied sciences that would remodel conventional approaches to passwords.
Verizon’s Knowledge Breach Investigation Report discovered stolen credentials are concerned in 44.7% of breaches.
Effortlessly safe Lively Listing with compliant password insurance policies, blocking 4+ billion compromised passwords, boosting safety, and slashing assist hassles!
Biometric authentication
Biometric authentication makes use of an individual’s bodily attributes to substantiate their identification: for instance, fingerprints, facial recognition, iris scans and so on. There are apparent benefits: fingerprints, as an example, are distinctive to a person, to allow them to’t simply be mimicked or replicated.
The expertise can be easy to make use of, avoiding the necessity to enter knowledge that may very well be simply forgotten.
However biometric authentication isn’t invulnerable. For instance, biometric spoofing may exploit pretend variations of a face or different biometric knowledge to try to idiot a system. Authentication techniques that haven’t any liveness checks might be notably weak to deepfake assaults.
And if the system is compromised, you possibly can’t simply reset biometric knowledge, such as you would a password.
Behavioral biometrics
Like biometric authentication, behavioral biometrics depends on traits which can be distinctive to a person. Besides this time, it’s the way in which you work together with the applying or web site in query: as an example, how you progress your mouse or sort on the keyboard.
There are apparent advantages – the person doesn’t need to do something particular, so it’s handy to make use of. It additionally mitigates the hazard of credential sharing, as you possibly can’t simply share your typing rhythm.
However once more, it may be expensive to arrange and there are potential issues round knowledge privateness within the occasion of a breach.
Blockchain for safe password storage
Blockchain may present a extremely safe methodology to safe knowledge. As utilized in cryptocurrency, it supplies an incorruptible methodology of distributing knowledge throughout a decentralized community. Nevertheless, there stay questions across the doable value of storing passwords on blockchain ledgers like Bitcoin.
Zero-knowledge proof expertise
ZKP proves the truthfulness of a mathematical assertion, with out revealing further info ‘that will have been helpful find stated truthfulness’, as famous by NIST.
In passwords, this supplies a safe method to let customers show that they know their very own password, with none must transmit their precise credentials – it’s a cryptographic methodology that proves you realize your password while not having to really submit your credentials.
In different phrases, you possibly can show who you’re with out risking your knowledge.
Nevertheless, challenges may embrace the processing energy required for ZKP and potential points round complexity.
Passphrases
One other various to conventional passwords is using passphrases. Not like customary passwords, which are sometimes brief and complicated, passphrases include a number of phrases strung collectively, creating an extended however extra memorable authentication methodology.
For instance, a passphrase like “PurpleBananaSunsetDancer!” is simpler to recollect than a random string of letters and numbers, whereas nonetheless offering robust safety as a result of its size.
Passphrases are notably efficient in opposition to brute-force assaults, as their prolonged size exponentially will increase the variety of doable mixtures.
Nevertheless, they nonetheless depend on user-generated enter, which means they are often weak if frequent phrases or predictable phrase patterns are used. You could find a full information on transferring to passphrases right here.
Passkeys
Passkeys are phishing-resistant alternate options to passwords which have been rising in recognition during the last couple of years. Based mostly on FIDO2, passkeys use public key cryptography to authenticate customers and log them into web sites and apps. A passkey is usually tied to a tool, resembling a telephone or laptop, and might be unlocked utilizing biometrics or a PIN.
Passkeys are proof against credential stuffing and phishing assaults as a result of the personal key used for authentication is securely saved on customers’ gadgets and by no means shared with web sites or transmitted over the web. Because of this, there aren’t any credentials that may be stolen in phishing assaults or knowledge breaches.
Passkeys at the moment are broadly supported on all main platforms, together with Google, Apple, and Microsoft.
Safety keys
Safety keys are bodily gadgets, normally USB, NFC, or Bluetooth, which can be mostly used for multi-factor authentication (MFA). After getting into a password, customers faucet the safety key or enter a PIN to confirm their identification, which permits the person to log in to the location or utility.
Nevertheless, some platforms now use them for password-less logins the place the proprietor makes use of a PIN or biometrics to show that they’re the proprietor and to permit logins. Help for password-less logins utilizing safety keys is presently out there in Home windows,
Safety keys are proof against assaults as they not solely require entry to the bodily machine but additionally the biometrics and PIN required to authenticate the login.
The enduring benefits of passwords
Many of those methods have been out there for a while, but passwords stay the muse of on-line safety, used day by day by customers and companies throughout the globe. Why is that this?
- Easy and common: the idea has been established for many years and is straightforward for everybody to know.
- Flexibility: you possibly can simply reset your password. You may’t say the identical factor for a facial scan or fingerprints.
- Effectiveness: passwords are both proper or unsuitable. Even when biometric scanners fail or safety tokens go lacking, passwords stay a dependable backup authentication methodology.
One of the best of each worlds
The optimum strategy isn’t to decide on between passwords and another type of safety. As an alternative, we should always embrace some great benefits of new applied sciences, whereas retaining the comfort and safety of passwords.
The answer is to go for the perfect of each worlds by constructing multi-factor authentication, going past two-factor authentication to construct in as many layers of safety as doable. This might contain using a code texted to your telephone alongside a facial scan and using a password.
Even right here, vulnerabilities stay. MFA might be focused by strategies like immediate bombing or adversary-in-the-middle assaults, usually based mostly on exploiting a weak password.
They secret’s subsequently to make sure your passwords are as strong as doable, it doesn’t matter what expertise you employ to reinforce your safety.

Specops Safe Entry: Safe password reset with built-in multi-factor authentication, decreasing the chance of unauthorized entry
Scan your Lively Listing for compromised passwords
Authentication applied sciences will proceed to advance, however you’ll all the time want to remain on high of your passwords.
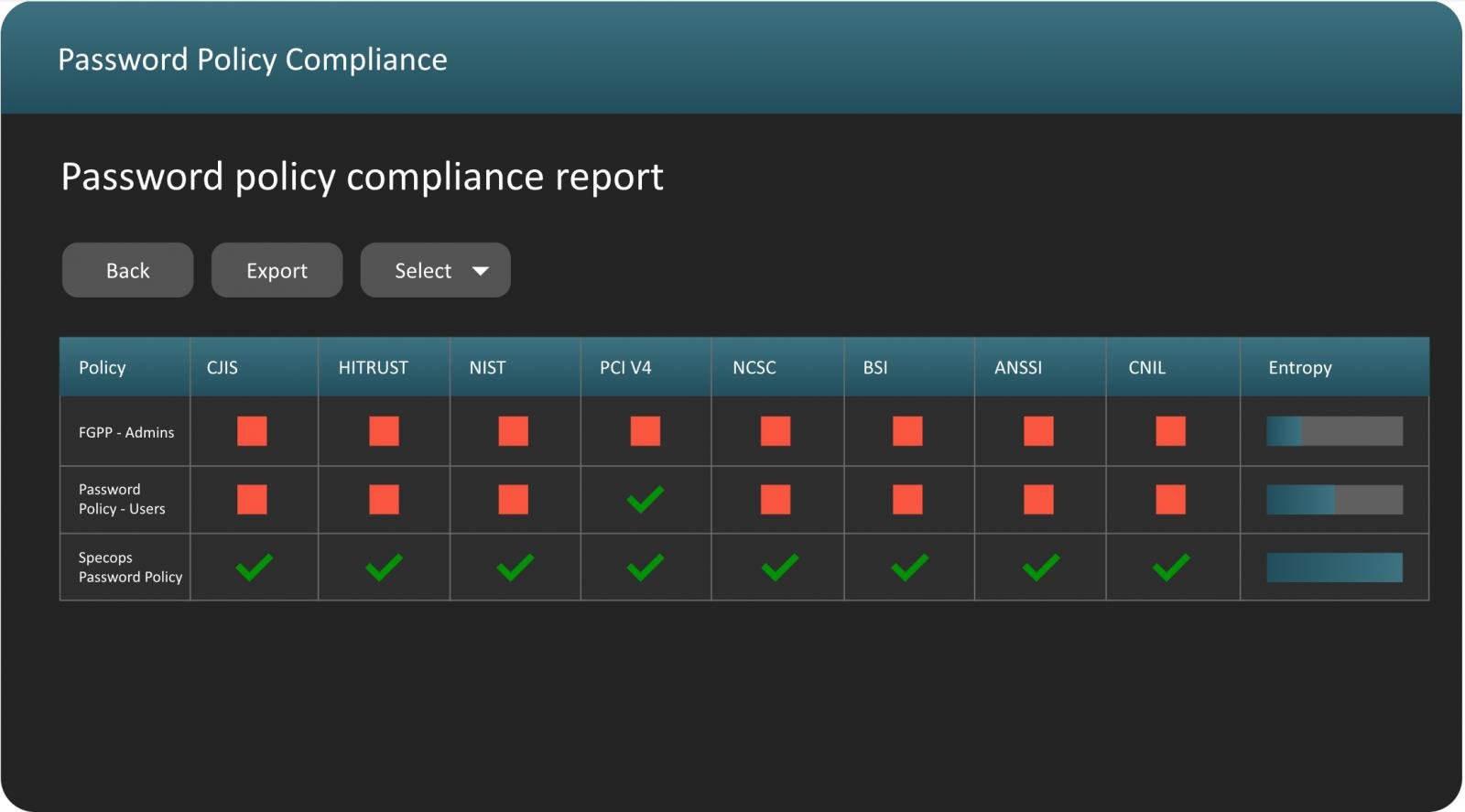
Implementing robust password insurance policies by figuring out and blocking compromised credentials to reinforce safety posture
Specops Password Coverage integrates along with your Lively Listing to repeatedly block a rising database of greater than 4 billion compromised passwords, whereas stopping customers from creating weak passwords and scanning for passwords which have been compromised or breached.
Contact us immediately in your free trial.
Sponsored and written by Specops Software program.

