
Menace actors have been utilizing a number of web sites promoted by Google adverts to distribute a convincing PDF modifying app that delivers an info-stealing malware known as TamperedChef.
The marketing campaign is an element of a bigger operation with a number of apps that may obtain one another, a few of them tricking customers into enrolling their system into residential proxies.
Greater than 50 domains have been recognized to host deceiving apps signed with fraudulent certificates issued by not less than 4 completely different corporations.
The marketing campaign seems to be widespread and well-orchestrated because the operators waited for the adverts to run their course earlier than activating the malicious parts within the purposes, researchers say.
Full replace delivers infostealer
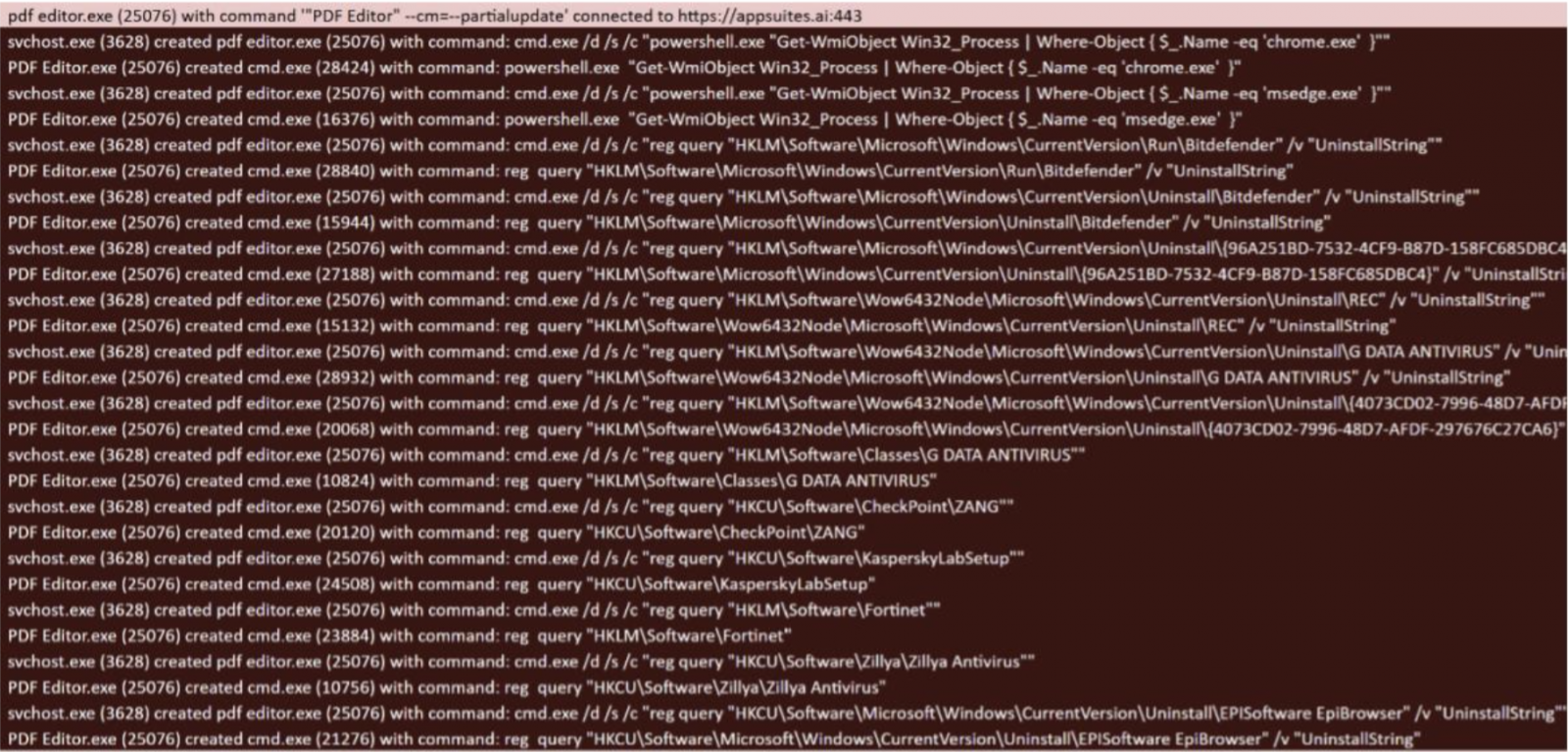
A technical evaluation from cybersecurity providers firm Truesec describes the method of TamperedChef infostealer being delivered to a consumer’s system.
The researchers found that the malware was delivered by a number of web sites that promoted a free instrument known as AppSuite PDF Editor.
Primarily based on web data, the investigators decided that the marketing campaign began on June 26, when most of the web sites concerned had been both registered or began to promote AppSuite PDF Editor.
Nevertheless, the researchers discovered that the malicious app had been verified by the VirusTotal malware scanning providers on Might fifteenth.
It seems that this system behaved usually till August twenty first, when it obtained an replace that activated malicious capabilities constructed to gather delicate information like credentials and net cookies.
Based on Truesec, TamperedChef infostealer is delivered with the “-fullupdate” argument for the PDF editor’s executable.
The malware checks for numerous safety brokers on the host. It additionally queries the databases of put in net browsers utilizing the DPAPI (Knowledge Safety Software Programming Interface) – a part in Home windows that encrypts delicate information.
supply: Truesec
Digging deeper for the distribution technique, Truesec researchers discovered proof suggesting that the menace actor spreading TamperedChef inside AppSuites PDF Editor relied on Google promoting to advertise the bug.
“Truesec has noticed not less than 5 completely different google marketing campaign IDs which suggests a widespread marketing campaign” – Truesec
The menace actor doubtless had a method to maximise the variety of downloads earlier than activating the malicious part in AppSuites PDF Editor, as they delivered the infostealer simply 4 days earlier than the standard expiration interval of 60 days for a Google advert marketing campaign.
Trying additional into AppSuites PDF Editor, the researchers discovered that completely different variations of this system had been signed by certificates “from not less than 4 corporations,” amongst them ECHO Infini SDN BHD, GLINT By J SDN. BHD, and SUMMIT NEXUS Holdings LLC, BHD.
Becoming a member of a residential proxy
Truesec discovered that the operator of this marketing campaign has been lively since not less than August 2024 and promoted different instruments, together with OneStart and Epibrowser browsers.
It’s price noting that OneStart is often flagged as a doubtlessly undesirable program (PUP), which is often the time period for adware.
Nevertheless, researchers at managed detection and response firm Expel additionally investigated incidents involving AppSuites PDF Editor, ManualFinder, and OneStart, all “dropping extremely suspicious information, executing surprising instructions, and turning hosts into residential proxies,” which is nearer to malware-like habits.
They discovered that OneStart can obtain AppSuite-PDF (signed by an ECHO INFINI SDN. BHD certificates), which might fetch PDF Editor.
“The preliminary downloads for OneStart, AppSuite-PDF, and PDF Editor are being distributed by a big advert marketing campaign promoting PDFs and PDF editors. These adverts direct customers to considered one of many web sites providing downloads of AppSuite-PDF, PDF Editor, and OneStart,” Expel.
The code-signing certificates used on this marketing campaign have already been revoked, however the danger continues to be current for present installations.
In some cases of PDF Editor, the app would present customers a message asking for permission to make use of their gadget as a residential proxy in return for utilizing the instrument at no cost.
The researchers word that the proxy community supplier could also be a legit entity not concerned within the marketing campaign and that the operator of PDF Editor is capitalizing as associates.
It seems that whoever is behind PDF Editor is attempting to maximise their revenue on the expense of customers worldwide.
Even when the packages on this marketing campaign are thought-about PUPs, their capabilities are typical of malware and needs to be handled as such.
The researchers warn that the operation they uncovered entails extra apps, a few of them not but weaponized, able to distributing malware or suspicious information, or executing instructions surreptitiously on the system.
Each experiences from Truesec and Expel [1, 2] embrace a big set of indicators of compromise (IoCs) that might assist defenders shield customers and belongings from getting contaminated.


