Malware analysis involves identifying the tactics, techniques, and procedures (TTPs) employed by risk actors, mapping out infrastructure, and analyzing innovative methodologies, often building upon existing research to uncover novel strategies. However, most investigations typically commence with a hunch, an idea that seems almost too straightforward. At the close of 2023, our team discovered an installer dubbed “that” which enables the deployment of a driver capable of injecting code into remote processes, as well as two libraries designed to intercept and manipulate browser traffic on community sites? The malware can manipulate web content by modifying or replacing it, re-route users to alternative websites, or launch new tabs with distinct URLs based on specific conditions.
While the installer was flagged as adware by various security tools, a more intriguing discovery was the presence of an embedded driver bearing Microsoft’s digital signature, raising questions about its purpose and potential implications. Developed in response to its signature by Chinese language firm 湖北盾网网络科技有限公司, or Hubei Dunwang Community Know-how Co., Ltd – a company whose anonymity sparked curiosity due to a lack of information about it. Despite lingering uncertainty regarding the distribution method, this software was touted as a “Web café security solution” specifically targeting Chinese-language speakers. While claiming to elevate online browsing proficiency by blocking ads and harmful websites, the reality is starkly at odds – instead, it exploits browser traffic interception and filtering capabilities to display game-themed advertisements. The software also transmits certain PC-related information to the company’s server, likely for purposes of compiling setup data.
Furthermore, this seemingly playful behavior unwittingly provides an opening for other malicious entities to execute code at the most privileged level accessible in the Windows operating system, namely the NT AUTHORITY\SYSTEM account. Due to lax entry controls, this kernel component is vulnerable to malicious interactions, permitting unauthorized access to exploit its code injection capabilities and potentially compromise sensitive processes.
We promptly notified Microsoft of this issue on March 18.thIn April 2024, the organization opted to adopt a standardized coordinated vulnerability disclosure program, thereby streamlining their response to security threats and fostering a culture of transparency and accountability within their ranks. Microsoft’s Safety Response Center (MSRC) concluded that this wasn’t a vulnerability, as the offending driver had been removed from the Windows Server Catalog on May 1.st, 2024. ESET’s security experts identify this threat as potentially malicious and possibly dangerous.
Who’s 湖北盾网网络科技有限公司 ?
Prior to dissecting the intricacies of the HotPage malware’s internal mechanics, it was essential to gain insight into the code-signing signature of the installed driver. What initially drew our attention was the proprietor of the signing certificates, as depicted in Figure 1.
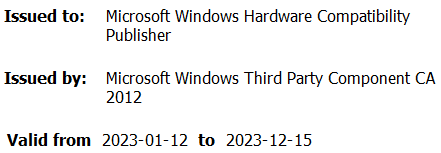
Due to the fact that the 64-bit variant of Windows 7 necessitates kernel-mode drivers to be digitally signed in order for them to be successfully loaded by the operating system. The signing process, previously outlined by, , and , is founded on trust; however, there have been instances where this was exploited. The Chinese-language company successfully underwent the process and acquired a Extended Validation (EV) certificate, as depicted in Figure 2.
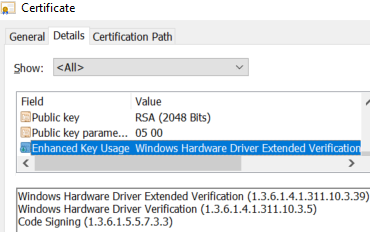
To uncover the corporate identity linked to this signature, extracting the signer’s characteristics was pivotal. The three exhibits that demonstrate the attribute recognized by the thing ID are as follows:
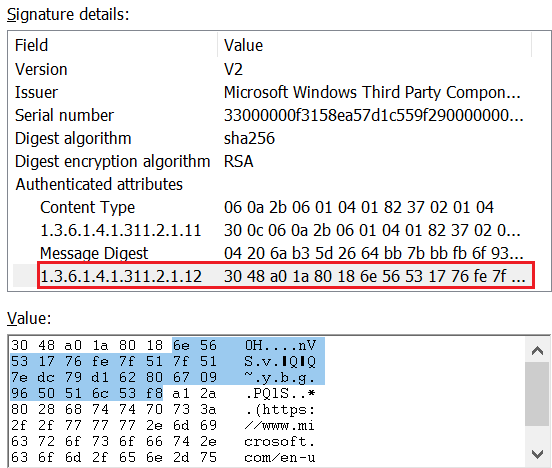
Using advanced algorithms, we successfully extracted the corporate entity identifier from the signature in Figure 4, revealing the underlying company responsible for this construction member.
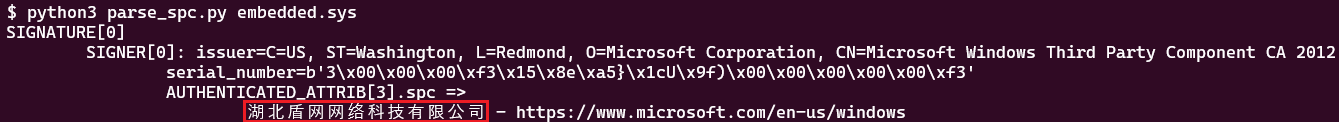
As evidenced in Figure 5, we found a mention of this company within the document. The corporation employed a diverse array of product categories during the driver submission process for certification purposes. The corporation appears to have developed two community filtering applications: an “element” driver referred to internally as “or”, with a notable typographical error (“Tt” instead of “To”).
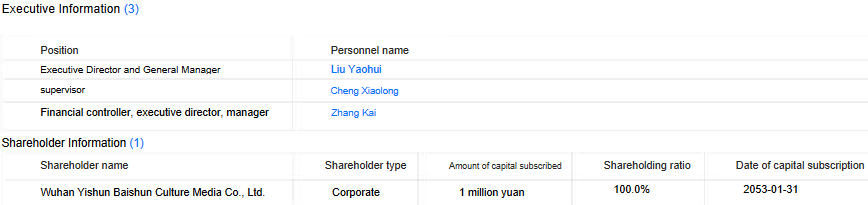
The investigation into the corporation via search engine results did not generate significant findings. The corporation was established on January 6.thIn January 2022, a comprehensive report was published and an email address was provided. The enterprise scope encompasses technology-driven initiatives focused on growth, as well as promotional efforts and collaborations with companies and consulting firms. According to previous translations, specifically Document 6, the principal shareholder has been re-designated as Wuhan Yishun Baishun Tradition Media Co., Ltd, a relatively obscure entity that primarily focuses on promotional activities.
According to the Mental Property tab, we found that in April and May 2022, the company applied for a business name and registered its website on February 22.nd, 2022. The area currently resolves to localhost () and is therefore inaccessible. Despite appearances, a screenshot of the website was captured on November 10th.th SKIP
![Figure 7. Screenshot of the dwadsafe[.]com webpage made by zhizhuyinqing.com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-7-screenshot-of-the-dwadsafe-com-webpage-made-by-zhizhuyinqing-com.png)
The SHA-1 hash (:) for the HTTP request’s physical address was also captured by VirusTotal. The supply code enables the development of a robust and secure cloud-based platform for proactive web café cybersecurity. The website presents a licensing agreement that outlines the purpose of the software, though inconsistencies arise. The desk contains a compilation of intriguing aspects from the available data.
| 为一款主动防御系统,自身并不具有任何拦截功能,单独运行本软件不会对现有任何软件或者程序有拦截、破坏、修改等操作,也不会拦截任何病毒程序。用户只有在编写相关过滤规则后,才会开始生效;用户可以根据自己的实际需要,选择是否使用这些规则 | 6. As a proactive and robust security solution, this software operates independently to detect, neutralize, and prevent the spread of malicious code, including viruses, without interfering with legitimate programs or applications. Only once customers establish custom filtering criteria will the filters have a tangible effect; at that point, customers can opt to apply these parameters based on their unique requirements. |
| 应用户的强烈需求而开发的:目前,有部分软件和网站的广告对用户存在较大的骚扰和误导,严重影响用户的上网体验。应广大用户提出要求,本公司开发并提供网吧环境下的安全监视、监控、过滤等功能的软件——过滤规则均由网友提供并共享,通过发布。用户可以根据自己的实际需要,选择是否使用这些功能。 | 7. Customers’ sturdy needs prompted the development of DwAdsafe. In response to customer demands, we are pleased to introduce DwAdsafe. In DwareSafe, trusted software and applications are supplied and shared by a community of netizens. Customers have the flexibility to opt-in or opt-out of utilizing these features according to their individual preferences. |
| 动防御型软件,故包括但不限于拦截、监视、删除、结束等功能。使用对计算机信息系统的部分或全部有对应的控制及处理权限 | 8. DwAdSafe is a robust and proactive security software solution, designed to provide comprehensive protection against various types of malware threats. Utilizing DwAdsafe can have . |
To address concerns over the licensing agreement, the software program is effectively promoted as a solution for web cafes to block advertisements. Despite corporate denials, our research uncovered evidence that DwAdsafe possesses a moderately invasive interception feature, accompanied by non-negotiable protocols.
The entity responsible for this malicious code remains shrouded in mystery.
HotPage evaluation
This section elucidates the mechanisms by which disparate components collaborate to achieve their collective purpose, namely integrating advertisements within a web browser. Although the exact distribution mechanism remains unknown, our preliminary analysis suggests that the malware might have been packaged with another software application or promoted as a security tool due to the elevated privileges required to install the driver. As of 2022, a few promotional references were scattered across certain online forums, with one notable example visible in Figure 8.
![Figure 8. Mention of dwadsafe[.]com in a forum dedicated to Internet café maintenance Figure 8. Mention of dwadsafe[.]com in a forum dedicated to Internet café maintenance](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-8-mention-of-dwadsafe-com-in-a-forum-dedicated-to-internet-cafe-maintenance.png)
The installer transfers the installation package to the system’s storage device and initiates a process to launch its execution. The software decrypts its configuration file, which stores a list of supported Chromium-based browsers and libraries. Upon detection of functioning or loading executable files, the primary motivator attempts to surreptitiously integrate one of various pre-listed libraries into the browser’s execution sequence. Following the hijacking of Windows API capabilities via a network-based mechanism, the injected library scrutinizes the target URL and under specific conditions, redirects the user to an alternative webpage through various methods.
The installer
The installer, with SHA-1 hash , is a compressed file, packaged using UPX, which was uploaded to VirusTotal on August 26, 2023. Determining the Nine: A High-Level Overview of the Driving Forces Set Up.
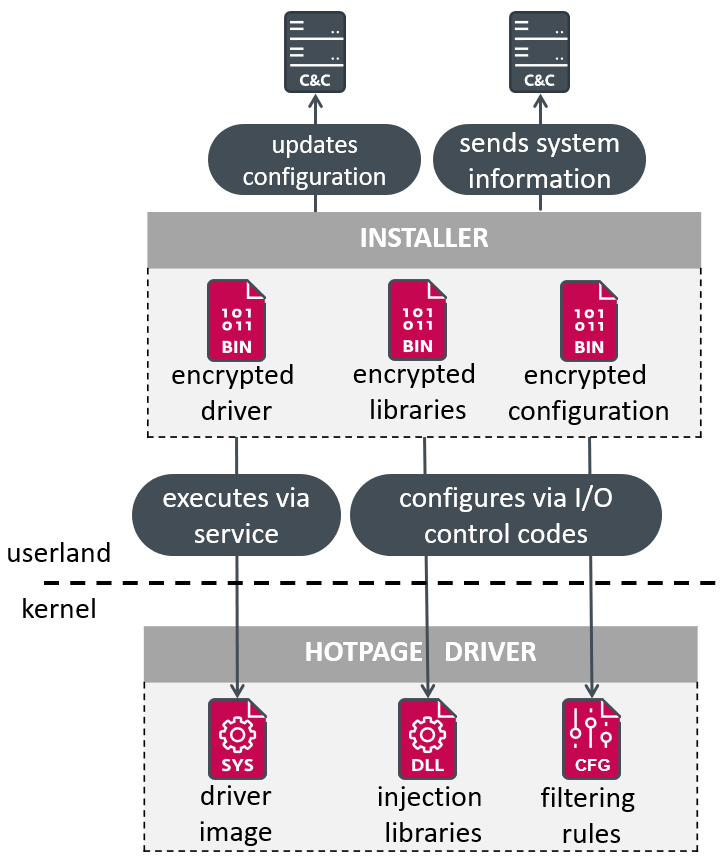
The installer seamlessly integrates with various iterations of the driver component, incorporating single-byte XOR encryption with the primary key. It also injects necessary libraries into web browser processes, while simultaneously processing three JSON-formatted configuration files.
- Provides compatibility with specific browser libraries and offers examples of how to integrate them through hooking.
- The application allows users to configure settings for focused browsing, including records of frequently accessed websites, specific command-line parameters, and designated homepages.
- The system accommodates filtering guidelines, featuring a dedicated API endpoint for shipping primary details regarding the compromised laptop, as well as another crucial endpoint for managing configuration updates.
The malware commences by executing an instruction that checks whether it is running within a virtualized environment to validate its operation. If the machine filename of the driving force exists, then the program decrypts the driving force and saves it to a file. The randomly generated identifier is a 7-character string assigned by the extension. A unique identifier is generated from a randomly selected string to distinguish the newly created service tied to the file path of the saved driver. Since the start of the engine type is prepared, the service needs to be initiated deliberately to harness its momentum. Although this adware appears to lack persistence mechanisms in its current iteration, further analysis may uncover alternative methods for maintaining its presence.
During the installation process, the installer engages in a dialogue with the driver, specifying the machine file name via I/O management protocols in the sequence:
- Ship the 32-bit hooking library to be injected into Goal Net Browser processes.
- Ship a 64-bit library for injecting hooks into Goal Net browser processes seamlessly.
- – ship the configuration.
The installer retrieves the registry key associated with the newly created service, then verifies whether its corresponding values remain up-to-date. These values appear to be arbitrary and are likely determined by another component in the system? Without delving into the minutiae of the community protocol, the remote server should provide an updated version of the configuration. The communication is encrypted using RC4, leveraging a key generated from the given string through Windows’ built-in function. Determines the contents of the configuration file in exhibit 10.
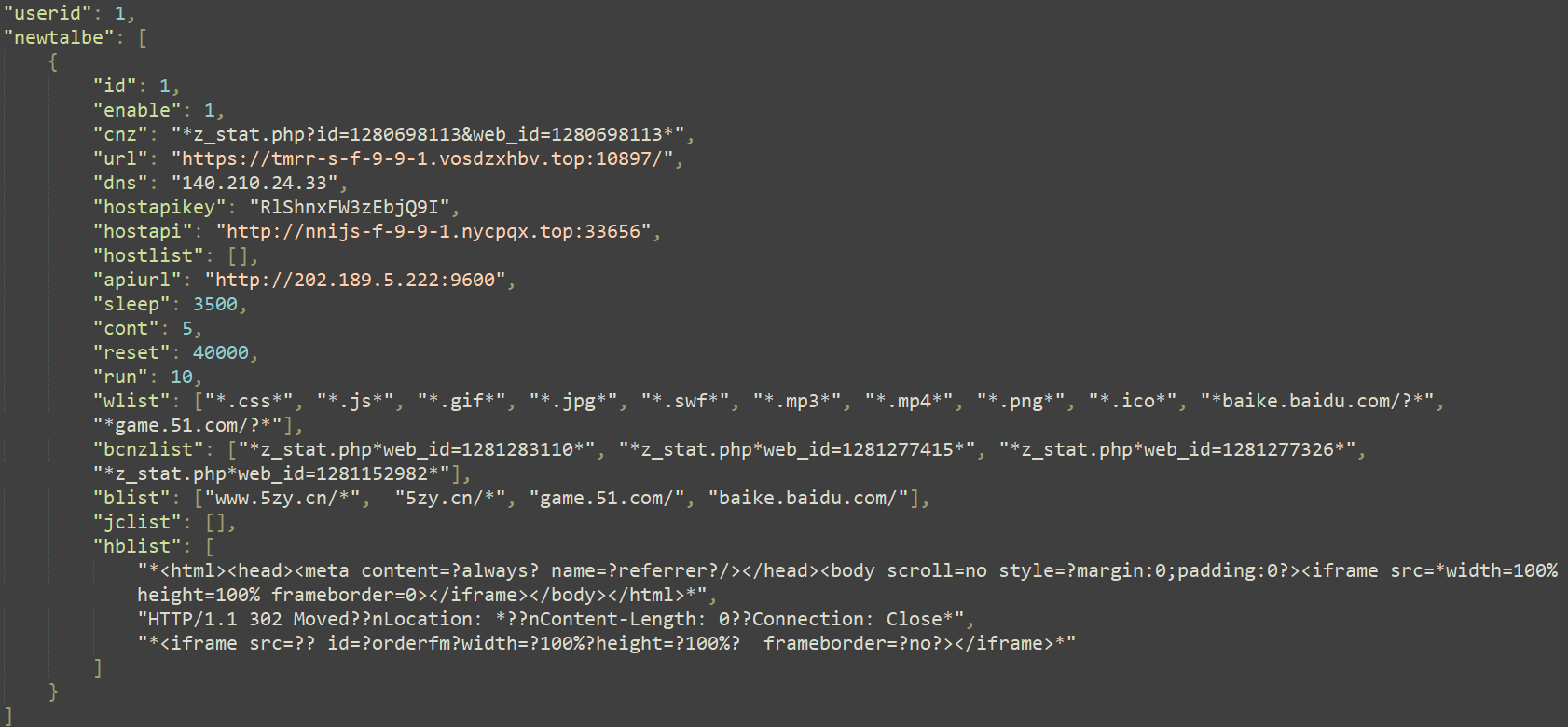
The required values from this file are outlined in Desk 2, presented in the order in which they appear in the configuration file (as per Determine 10).
| The URI sample matching URLs used to gather statistics when visiting a website as specified by its worth. | |
| and | When accessing any URL from a list, a fresh tab will automatically open and direct you to the specified value. What value lies in the intellectual property tackling of this area? |
| The URL’s worth lies in its ability to replace the traditional DNS system, a comprehensive dictionary comprising game-related domains alongside their respective IP addresses. The is the decryption key. | |
| List of authorized recipients for shipment of information regarding compromised laptops: | |
| Patterns for redirection: URI templates, domain name patterns, file extension filters, HTML code snippets, and HTTP response header matches. |
The URL’s value is leveraged to revamp an HTTP GET request, incorporating TLS and a standard Person-Agent header. The acquired data is decrypted using RC4 encryption, containing a dictionary of gaming-related hostnames mapped to their respective resolved IP addresses.
Upon completing the updates, the installer dispatches a command to the driver using an I/O request with a management code.
As malware spreads across compromised laptops, it methodically processes each endpoint supplied by the JSON feed. For every device, it generates a formatted JSON string encapsulating vital details about the infected machine, encrypts the package using RC4 encryption with a key derived from Windows API calls, and transmits the aggregated data to the remote server via an HTTP POST request. The aggregated dataset comprises information on PC identification, community network interface Media Access Control (MAC) address, operating system model, and display screen resolution.
Injector driver
The primary purpose of a motive force is to dynamically inject libraries into browser functions, thereby modifying the execution flow to redirect users to alternative URLs or open new tabs. Two threads are spawned to handle requests for opening a fresh new tab and injecting libraries using publicly available challenges. Moreover, advanced notification routines are designed to monitor newly created processes and executable images as they are loaded. The underlying driving force is simplistically depicted in Figure 11.
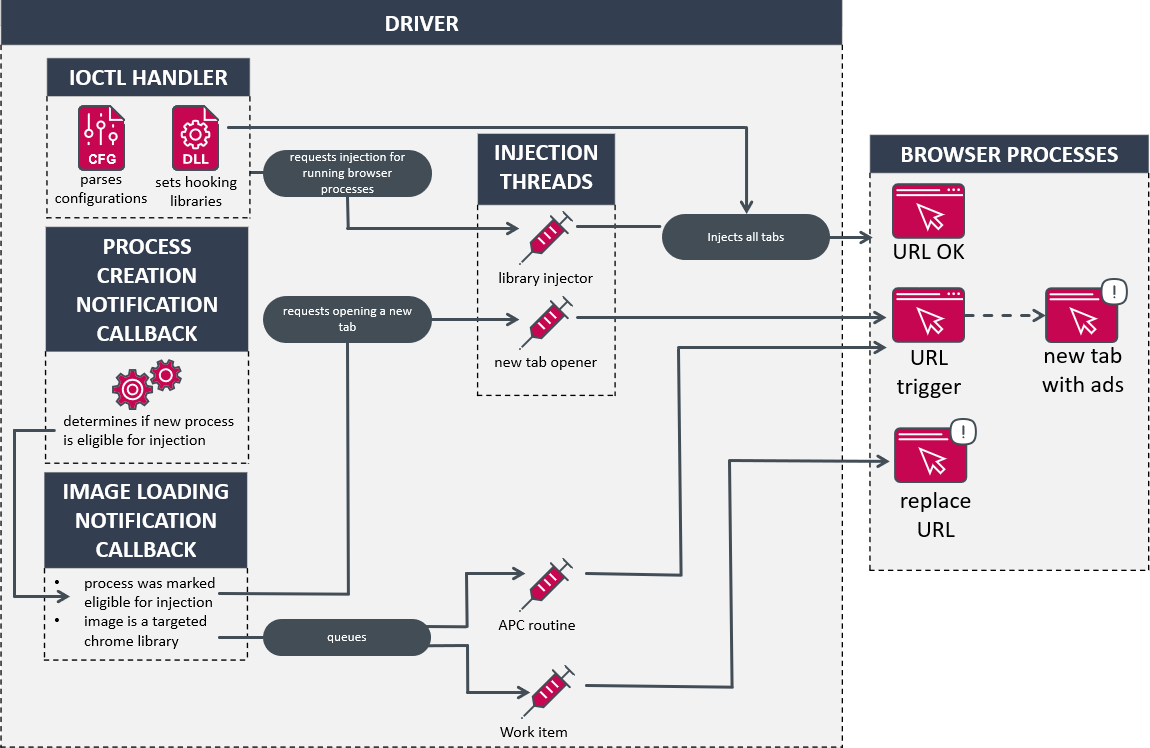
Mysterious forces beyond our understanding initiate a peculiar sequence of events by erasing the driving force’s digital representation from the storage device. Subsequently, a tool object is instantiated, dubbed, and configured to manage diverse I/O demands outlined in Table 3. The management codes (IOCTLs) governing the configuration of injected libraries are only accessible once, thereby precluding the ability to update settings in a timely manner. These specific management codes are safeguarded by verifying that the caller’s file path conforms to a well-defined pattern.
| Determines the configuration settings based on the input provided. | |
| Utilize the 64-bit library for injection purposes. | |
| Reintegrate the 32-bit library for seamless injection. | |
| Examines the provided configuration settings to ensure their validity and efficacy. | |
| Receives a list of browser tabs processes to terminate. | |
| Returns the configuration. | |
| Returns the dimensions of the configuration, providing a precise breakdown of the settings’ spatial characteristics. | |
| Returns the configuration. | |
| The method returns the dimension of the given configuration in a specific format which depends on the type of the configuration object. | |
| Parses the configuration provided as input. |
As the management code executes, the driving force iterates through each loaded module governing the workflow of all operational processes. When a specific module from the configuration is identified, a request to integrate a library into that module’s workflow is enqueued.
The driving force concludes its setup process by spawning two threads and configuring the notification handlers discussed earlier.
It is crucial to ensure that the configuration is not set. This document’s sole purpose is to illustrate potential applications within the management framework of the driving force, clarifying its utility and relevance. The configuration enables consumers to be redirected to a specific webpage, typically their homepage, that is rich in advertisements whenever they launch a browser with a focus on advertising.
The software program’s model was built entirely around ad configurations, relying solely on these to facilitate effective ad injection.
Library injection thread
This thread checks the queued injection requests and, for each one, attaches itself to the targeted process, allocates memory blocks, and copies its shellcode.
Using the Blackbone library, the driving force executes the shellcode, which incorporates its own PE loader and subsequently invokes the entry point of the injected library.
New tab thread
Despite sharing a common logical foundation, the second thread employs distinct reasoning, accompanied by dissimilar shellcode injection. The Windows API is invoked utilizing a command-line parameter comprising the technique title of the focused process merged with the URL requiring opening. The latter is fabricated from variables derived from a configured setting’s cumulative total. As an illustration, the configuration depicted in Figure 12 would produce the string. Since Chromium-based browsers spawn a fresh process for each new tab, creating a process from the browser’s current process effectively opens a new tab.
Determines the content of the configuration file, exhibiting a total of 12.
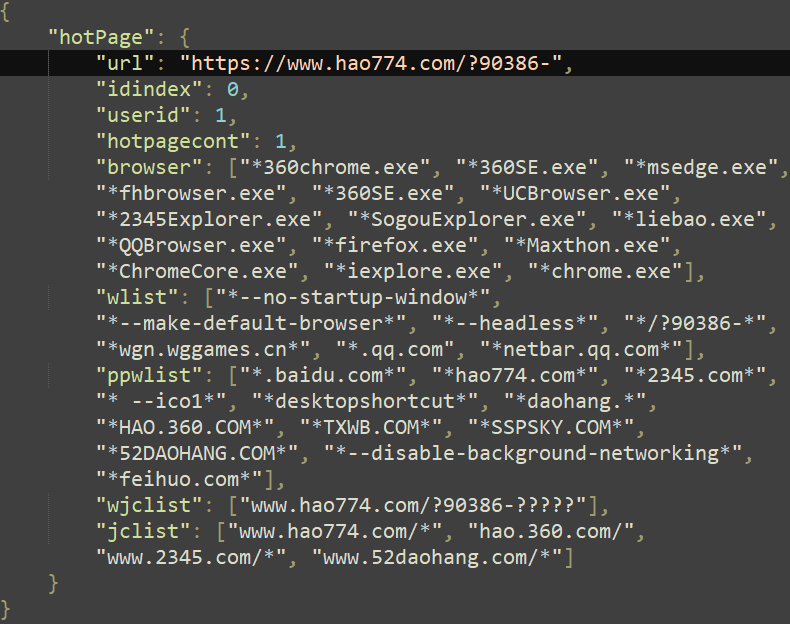
This configuration file governs the tracking of preferred web browsers and command-line directives that determine when the injection mechanism is necessary. The domains are both closely tied to gaming-related content and online gaming community maintenance.
Course of creation notification routine
Upon initiation, the homepage of the brand-new net browser instance is redirected to a specific URL defined within its configuration settings. Even in instances where the driving force is unused, its implementation of this characteristic remains unaffected, as the installer’s model does not transmit this configuration to the driving force?
Under specified conditions, the online browser program will be deemed qualified to access URLs according to the predefined settings.
- That is typically the primary occurrence of the browser, as opposed to opening a brand-new tab.
- The method’s file path conforms to one of several well-known patterns specified in the configuration record.
- The command line of this method does not conform to any established pattern as recorded in the configuration file.
- If a method’s command line comprises its unique file path, it must not conform to any prevailing patterns recorded in the configuration log.
When the browser process initiates the loading of its primary executable images, a request to open a new tab is placed in a queue for processing. The distinction between the professional net listings, such as Determine 13 and Determine 14, is starkly evident when comparing these to the ad-riddled webpage presented to consumers.
![Figure 13. Legitimate main page of the web directory 2345[.]com Figure 13. Legitimate main page of the web directory 2345[.]com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-13-legitimate-main-page-of-the-web-directory-2345-com.png)
![Figure 14. Ad-riddled page mimicking the homepage of 2345[.]com Figure 14. Ad-riddled page mimicking the homepage of 2345[.]com](https://web-assets.esetstatic.com/wls/2024/7-2024/hotpage/figure-14-ad-riddled-page-mimicking-the-homepage-of-2345-com.png)
Picture loading notification routine
The routine primarily focuses on addressing two distinct types of scenarios. When a picture is successfully loaded from a record, a queue is triggered that enables the loading of various hooking libraries via their personalized PE loader.
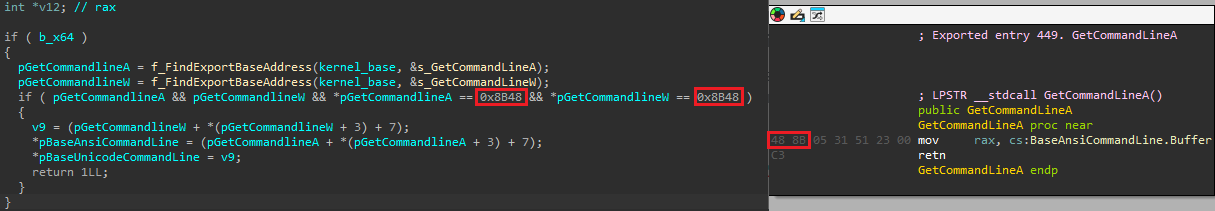
When flagged as eligible to open a novel webpage, the malware successfully accomplishes this either by launching the link in a fresh tab or within the existing one. When the filename matches a common expression recorded in the configuration, a request to open a new tab is enqueued for processing by the corresponding thread. In this new scenario, when opening the webpage, it is essential to create a tab by queuing a piece of merchandise through, which can dynamically modify the command-line parameters for the method being created. The attachment connects itself to the method, locates the export mechanism within the library, and adjusts the Unicode string stored in it. The command line is modified by combining the path of the method’s executable file with the relevant URL, as specified in the configuration. Determines the side-by-side comparison of code responsible for finding the command-line buffer and disassembling the performance, showcasing Exhibit 15.
Injected library
The injected library’s primary action is to acquire and configurations by interrogating the driving force. When the injected browser filename is 360Chrome, the system deletes the relevant registry key and modifies the Preferences file, situated beneath the browser’s default directory, to set the homepage equal to the URL value specified in the configuration.
To prevent exploitation by malicious users, the pattern employs hooks that return 1 when matched, effectively blocking the execution of safety insurance policies and allowing for code injection. The DNS (Domain Name System) is then employed to direct the browser, ensuring that domain names are resolved to specific IP addresses, thereby guaranteeing a correct server redirect when domains no longer exist.
Hooking SSL_read and SSL_write
The malware exploits the browser’s TLS decryption mechanisms by hooking into the and capabilities, enabling manipulation of decrypted website traffic. It achieves this by searching for specific patterns within loaded modules, as these capabilities are not typically exported. The dictionary contained within the configuration, illustrated in Figure 16, accommodates two distinct pattern formats. These two terms are employed to identify more recent and earlier iterations of a software application. We verified that the patterns align with the established Microsoft Edge library model.
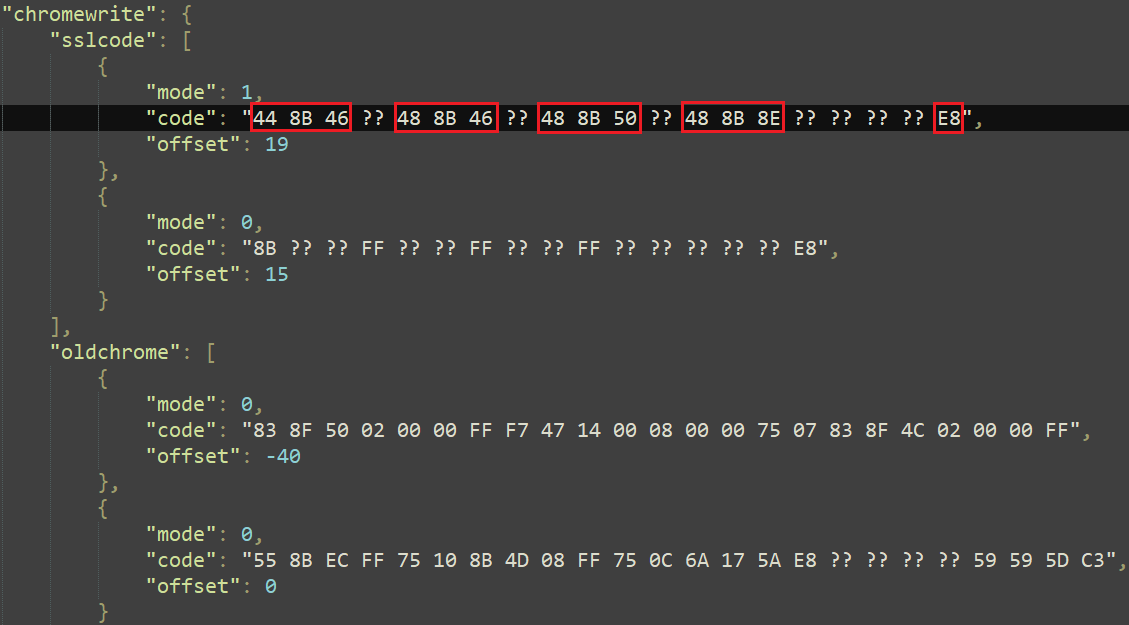
The worth indicates whether a sample is 32-bit or 64-bit in size; it represents the precise byte offset into the sample. The distance is the space from the start of the sample to the pointer that performs the operation, as described in Determine 17.
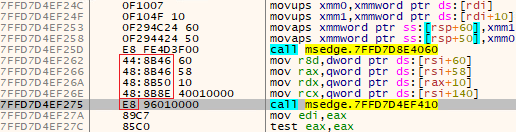
As soon as APIs are discovered, they’re immediately utilized via the Detours library. The malware inspects the gathered information, subsequently triggering a distinct function that encrypts and transmits the data. As for the latter, the injected library effectively manipulates decrypted data with a deliberate intent to alter its content. During inspection of each capability, the relevant code scrutinizes the information regarding its and management codes within the perform hooking mechanism.
As a low-level Windows API function, Hooking NtDeviceIoControlFile allows developers to intercept and analyze file system operations. The following code snippet demonstrates how to hook the NtDeviceIoControlFile function and examine both input and output parameters.
“`c
#include
#include
// Function pointer for the hooked NtDeviceIoControlFile.
NTFYPROC NtDeviceIoControlFileHook;
void InitializeHook()
{
// Get the original NtDeviceIoControlFile function address.
NtDeviceIoControlFileHook = (NTFYPROC)GetProcAddress(GetModuleHandle(_TEXT(“ntoskrnl.ex”)), “NtDeviceIoControlFile”);
}
NTSTATUS HookedNtDeviceIoControlFile(PFILE_OBJECT FileObject, EVENT_TRACKING_DATA_TRACKINGFORMATION TrackingForm)
{
// Perform any desired actions here.
printf(“Hooked NtDeviceIoControlFile called\n”);
// Call the original function with the hooked parameters.
return NtDeviceIoControlFileHook(FileObject, TrackingForm);
}
“`
The malicious library appears to hook the system’s performance management mechanism to handle specific IOCTL (Input/Output Control) codes, as observed in Figure 18.
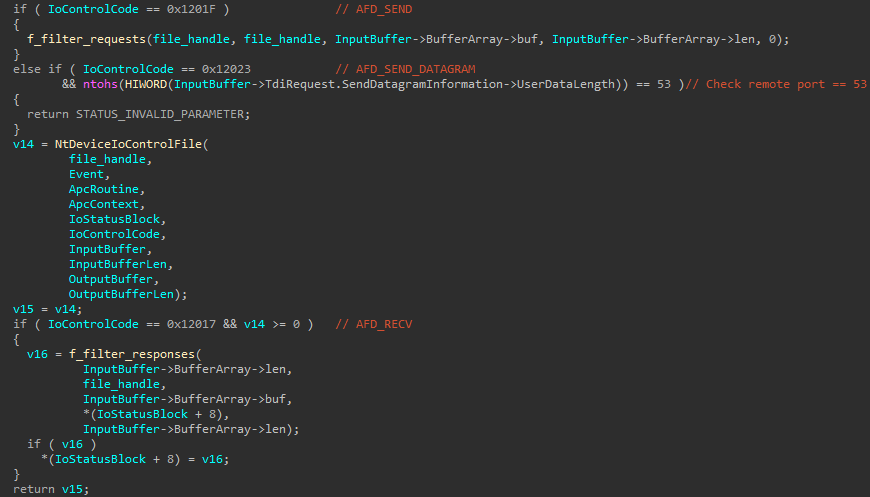
When implementing the management code for UDP packet transmission, the malicious software circumvents DNS queries by returning an error response whenever the destination port number equals 53. This effectively restricts the online browser to utilise only the host entries specified within the configuration settings.
The code responsible for managing requests initiates its execution by retrieving the URL and referrer information from the incoming HTTP request. Upon examining the provided URL against specific values within both configuration sets, the malware executes a diverse range of actions, as outlined in Desk 4. Under certain conditions, requests are dispatched although responses are altered within the processing framework according to distinct redirection tactics predetermined later on.
| Reports the details of the compromised laptop to the IT administrator’s notification system. | ||
| Will significantly boost the visibility of our homepage by incrementing the hit counter, thereby providing valuable insights into user engagement and online presence. | ||
| SKIP | ||
| Sends the information with none modifications. | ||
| The company will re-route customer requests for product information to a dedicated webpage featuring FAQs and detailed specifications, thereby streamlining the inquiry process. The response is loaded in a new browser window. | ||
| Redirects the information without any modification to ensure its integrity and authenticity by sending it as is. | ||
| Redirects sensitive information to secured channels and encrypts data before transmission, ensuring secure communication protocols are followed, thereby minimizing potential risks and vulnerabilities. | ||
| Modifies the response utilizing redirection technique to provide more effective communication by conveying essential data while effectively using words and phrases that help people quickly understand the message. |
When the malware executes its malicious intent under management code (), it initially extracts the consumer’s data and verifies whether the response is flagged as eligible for diversion. The four forms of redirection as outlined in Desk 5 include: The string within the modified response is rewritten to accommodate the URL as specified in the configuration file.
|
| The browser is redirected to another webpage; an internal redirect counter is incremented. | |
| Redirect to: https://newurl.com/newcontent | ||
| Redirecting the current webpage using redirect techniques and interfaces? | ||
| The redirection counter does not need to be incremented in this case. |
Determining the effectiveness of 19 is contingent upon its ability to illustrate the utilization of redirection techniques following navigation to a URL that conforms to one or more URL patterns defined within the configuration. Another tab opens, mirroring the existing configuration in exact detail.
Safety points and privilege escalation
Initially, the machine’s object is created without specifying any entry control lists (), which allows anyone to send I/O requests to it freely. Prior to executing specific I/O management codes, the requesting process must adhere to a directory pathway that complies with the specified regular expression pattern.
While that’s a valid concern, it’s crucial to determine whether the speaking course is indeed part of the HotPage elements; otherwise, creating directories beneath a user-writable folder won’t guarantee its inclusion.
Two scenarios exist where a consumer’s system, when equipped with the HotPage driver, might enable running code under the account of the consumer. We developed a Python-based proof-of-concept script that addresses various scenarios.
Privilege escalation achieved through exploiting a vulnerability that allows for arbitrary dynamic-link library (DLL) injection into arbitrary processes.
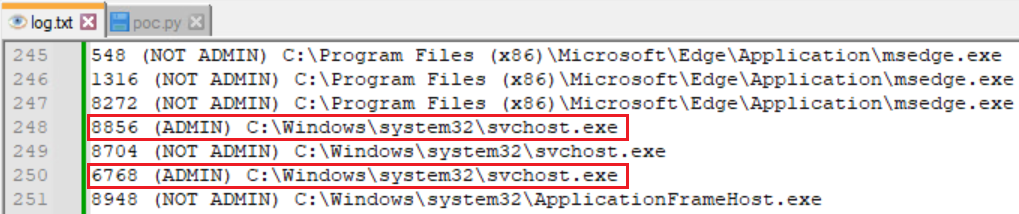
Initially, it is assumed that the driving force was correctly loaded; nonetheless, the necessary configuration and libraries to facilitate its injection were overlooked. It’s theoretically possible to establish a personalized library, thereby allowing for injection. We developed a compact library capable of logging essential information about an injected process: its PID, execution status as an administrator, and file path.
According to a screenshot of the log file taken on Determine 20, multiple processes were successfully loaded with our proprietary library, including those boasting administrator-level access.
However, it must be emphasized that injecting something as renowned as cannot be achieved through this approach alone.
When a new process is created in Windows, the command line used to launch that process is stored in the process’s environment block. This allows an attacker who has already escalated their privileges to create a new process with a modified command line, effectively granting themselves elevated privileges without needing to know the original password or authentication token of the user who launched the process.
During the initial scenario, we relied on the assumption that both injected libraries and the configuration were not set, but as observed in the installer evaluation, they are indeed set as soon as the driver is first loaded. Despite these efforts, the configuration still refuses to take hold. To optimize the workflow based on management evaluations, we developed an innovative approach that harnessed the power of the driving forces’ creation process and picture loading notification logics, allowing us to re-run the same executable with a custom command line?
Under the specified circumstances, defined within the designated sections, the driving force may initiate a new tab, directing it to the URL currently configured. The desired browser behavior is accomplished either by modifying the command line of a new browser instance or by duplicating an existing browser instance, then updating its command line to match the URL specified in the configuration. By identifying which courses can be duplicated and introducing a novel command-line feature, we can achieve privilege escalation by focusing on a privileged course, for instance?
Conclusion
The assessment of this fairly uninspired instance of malware has again verified that adware developers remain willing to push boundaries to achieve their objectives, underscoring a persistent willingness to circumvent security measures? While they’ve cultivated a core component with a broad suite of tactics to manage processes, they also navigated the requirements imposed by Microsoft to obtain a code-signing certificate for their driver module.
Abuse of prolonged verification certificates remains a persistent concern, the HotPage driver serving as a reminder of this ongoing issue. While many safety trends may ultimately be founded on hearsay, threat actors tend to operate along a grey area between legitimacy and ambiguity. Regardless of whether software is promoted as a safety solution or simply packaged with other programs, its inherent features pose significant risks to users’ security.
Despite its own frustrations, adware’s underlying weaknesses leave a system vulnerable to far more sinister attacks. An unprivileged attacker could exploit the vulnerable driver to gain elevated privileges or inject libraries into remote processes, ultimately triggering further damage, often using a genuine and digitally signed driver.
ESET’s researchers identify this vulnerability, previously removed by Microsoft from its Windows Server Catalog on May 1.stThe future of healthcare: 2024 and beyond?
IoCs
A comprehensive record of indicators of compromise (IoCs) and samples is stored within our database.
Information
| N/A | Win64/HotPage.B | HotPage driver. | |
| N/A | Win32/HotPage.B | 32-bit HotPage hooking library. | |
| N/A | Win64/HotPage.A | 64-bit HotPage hooking library. | |
| Win32/HotPage.A | HotPage installer. |
Community
| CHINATELECOM JiangSu YangZhou IDC. | 2023-10-06 | The server retrieves a comprehensive list of game-related domains along with their respective IP addresses. | ||
| CHINATELECOM JiangSu YangZhou IDC. | 2023-10-06 | Customers who have been compromised by malicious activity are redirected to a separate network server, which serves as a holding page filled with ads. | ||
| N/A | Shandong Eshinton Community Know-How Co., Ltd. | 2023-10-06 | The DwAdsafe area formerly utilized for collecting installation information has been repurposed. |
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework.
| Receive Capabilities: Code Signing Certificates | DwAdsafe’s driver is securely validated by a reputable code-signing authority, verifying its authenticity and integrity. | ||
| Person Execution: Malicious File | The installer element is a standalone executable utility that enables users to install and configure software applications on their devices. | ||
| System Providers: Service Execution | The DwAdsafe’s driver is loaded through the creation of a Windows service. | ||
| Hijack Execution Move: KernelCallbackTable | DwAdsafe’s driver installs kernel-level callbacks to monitor the loading of images and their creation process. | ||
| Course of Injection: An Asynchronous Process – Nomenclature | The DwAdsafe driver leverages APC (Atomic Patching Cache) as a versatile injection technique for its drivers. | ||
| Subvert Belief Controls: Code Signing | DwAdsafe’s drivers are signed with trusted, industry-standard code-signing certificates. | ||
| Deobfuscate/Decode Information or Info | The embedded configuration information are securely encrypted. | ||
| What does this technique accomplish? The injection of a dynamic-link library (DLL) into an application’s process enables the manipulation of the target program’s behavior without modifying its executable code. This approach can be utilized to achieve various objectives, including process memory access and execution control, API hooking, and system calls interception. | DWAdSafe can hijack a network browser’s process management stream by injecting dynamic link libraries (DLLs). | ||
| Hidden in Plain Sight: The Art of Concealing Data | The DwAdsafe’s driver and hooking libraries are included within the installer package. | ||
| Indicator Elimination: File Deletion | The DwAdSafe’s driver automatically uninstalls and erases itself from the computer’s hard drive. | ||
| Is Data Protection a Concern for You? The Mystery of Obfuscated Information. | The DwAdsafe’s installer is heavily packed with UPX compression. | ||
| System Proprietor/Person Discovery | The DwAdsafe’s installer and the hooking libraries collect the victim’s username. | ||
| Browser Session Hijacking | DwAdsafe’s hooking libraries enable the interception and manipulation of community site visitors within browser processes in real-time. | ||
| Software Layer Protocol: Net Protocols | The HTTP protocol is used to ship collected details about the consumer and laptop to the C&C. | ||
| Encrypted Channel: Symmetric Cryptography | The RC4 encryption algorithm is used for encrypting communication with the C&C. | ||
| Information Manipulation: Transmitted Information Manipulation | DwAdsae’s hooking libraries can potentially intercept and manipulate community site visitors within the context of a networked browser process. |

