As smartphones have become an integral part of our daily lives, malicious apps have evolved into increasingly sophisticated and deceptive entities. Recently, our team discovered an app called “BMI Calculation Vsn” masquerading as a simple health tool on the Amazon App Store, yet it has a sinister intention: to surreptitiously collect the package titles of installed apps and incoming SMS messages. Amazon promptly took action in response to McAfee’s report, subsequently removing the offending app from its Appstore, ensuring users’ security.

Determine 1. Software printed on Amazon Appstore
The application appears to be a straightforward tool, providing a solitary webpage where users can input their height and weight to compute their Body Mass Index (BMI). The application’s user interface appears to be consistently aligned with conventional wellness software. Beneath its seemingly innocuous facade, a tangled web of malevolent deeds unfolds.
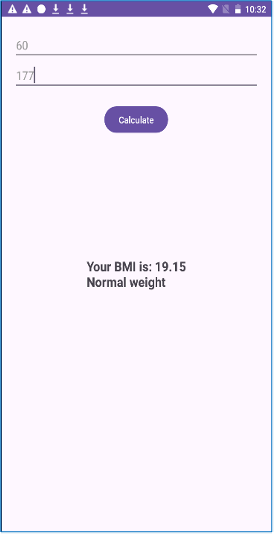
Determine 2. Software MainActivity
Upon further examination, our findings reveal that this application exhibits several hazardous behaviors.
- When the application is launched, it starts a background service to capture the display screen. Upon clicking the “Calculate” button, the app prompts the user with a system-generated notification seeking permission to record the display screen, following which the recording begins. Can this AI-powered tool effectively capture gesture passwords and sensitive information from various applications? During the assessment of fresh data sets, it became apparent that the developer lacked preparedness to tackle this task. When the code failed to upload the recorded MP4 file to the C2 server, the initial approach in the startRecording() method was flawed, simply returning without executing the subsequent code as intended.
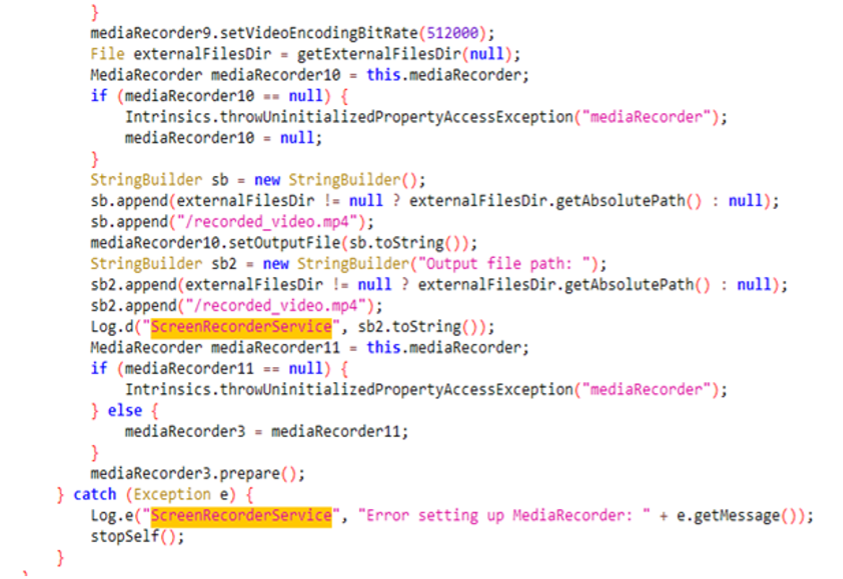
Determine 3. Display screen Recorder Service Code
The recording initiates, potentially triggering a permissions request dialogue to appear.
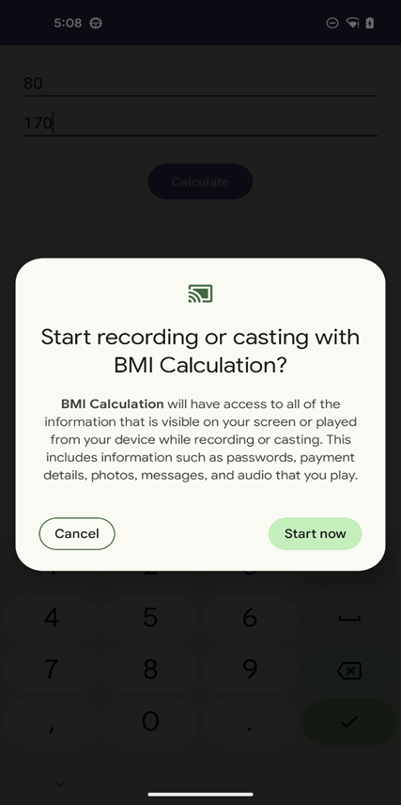
Determine 4. Begin Recording Request.
- The application conducts a thorough scan of the system to generate a comprehensive inventory of all installed functions. This knowledge may potentially be employed to identify target audiences or devise sophisticated strategies.
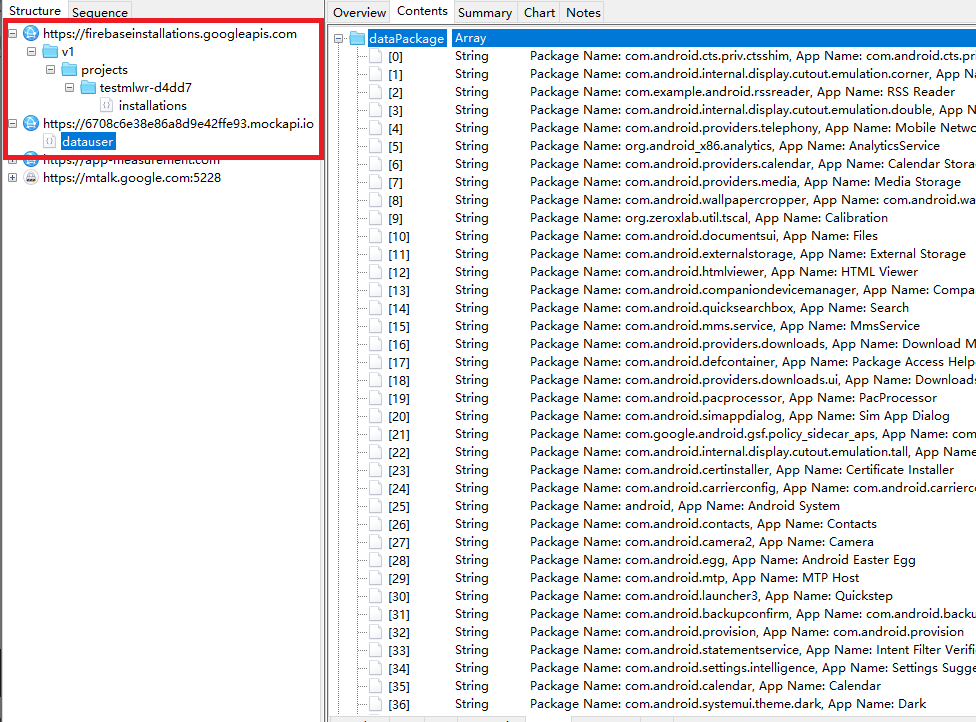
Determine 5. Add Consumer Information
- The software intercepts and gathers all SMS messages transmitted on the system, likely targeting sensitive data such as one-time passwords (OTPs) and verification codes. The intercepted textual content messages may be uploaded to a Firebase storage bucket designated as testmlwr-d4dd7.appspot.com.
According to our assessment of historical data, the malicious application remains in a developmental phase, failing to reach a stable or fully functional state. The text’s growth history was uncovered by searching for related samples on VirusTotal, utilizing the malware’s bundle title (com.zeeee.recordingappz). Developed in October 2024, an initial version of this malware emerged as a seemingly innocuous display screen recording application. But midway through its development cycle, the app’s icon was surreptitiously modified to masquerade as a BMI calculator, while the payload quietly evolved to steal unsuspecting users’ SMS messages in the latest iteration.
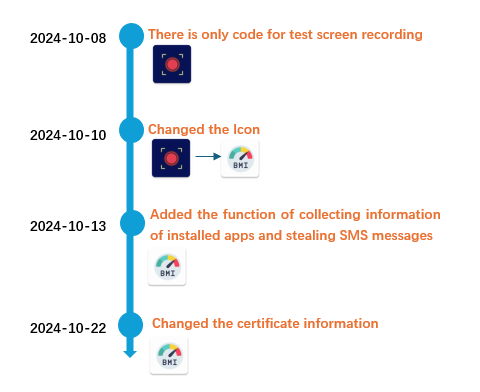
Determine 6. The Timeline of Software Growth
The Firebase setup API used by this app employs the character “testmlwr”, signifying that the application remains in its testing phase.
The developer’s title is: “Developer” Visionet Information Internasional”. Hackers exploited the reputation of a prominent Indonesian IT management company by masquerading as them on Amazon Appstore, duping users into downloading malicious software. This truth implies that the malware writer may even possess knowledge about Indonesia.
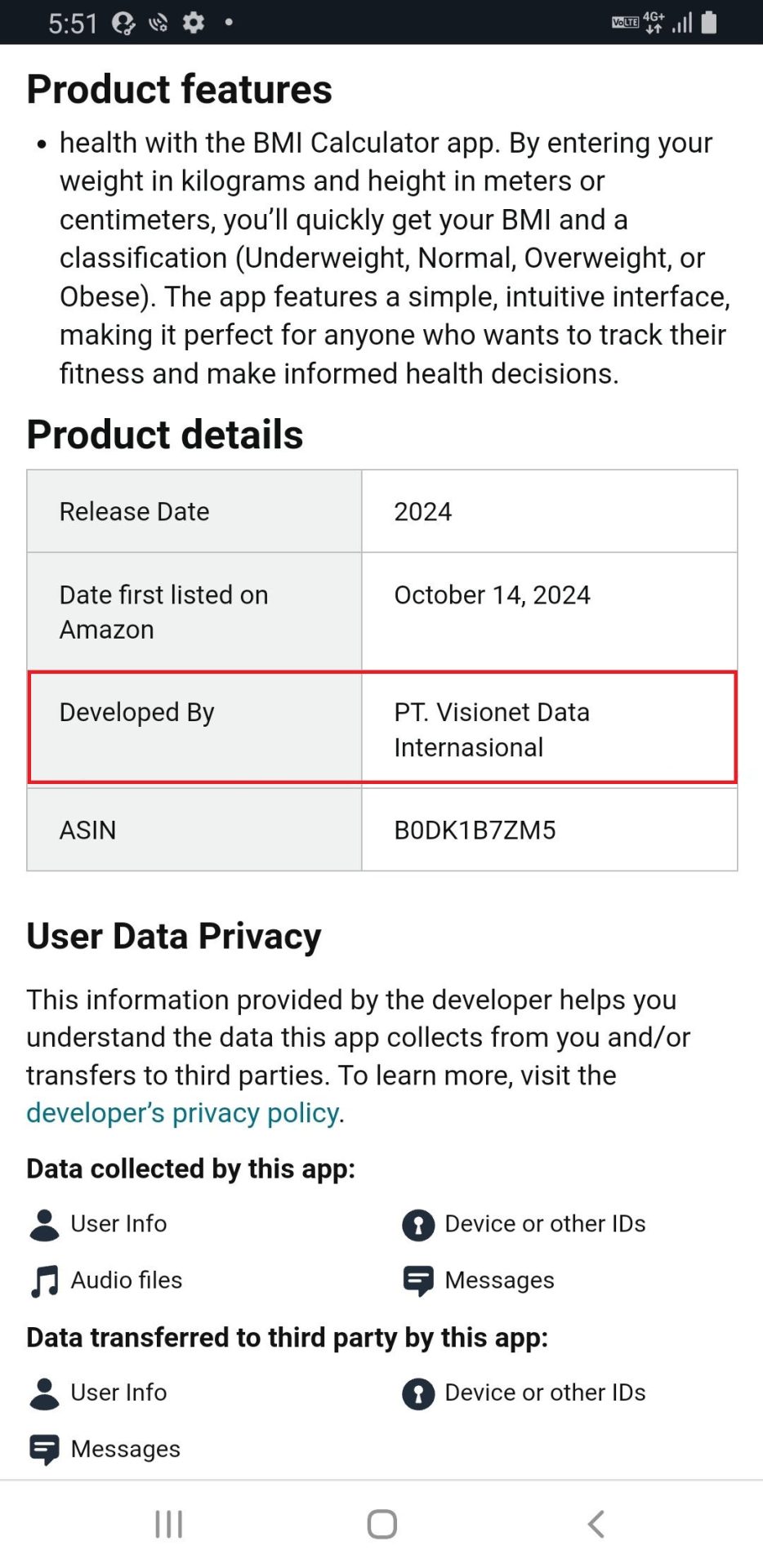
Determine 7. Developer Info
To avoid falling victim to such malicious apps, heed the following precautions:
- Establish Secure Antivirus Protections: Implement tried-and-tested antivirus applications to promptly identify and neutralize harmful programs before they can cause damage.
- When installing a mobile application, thoroughly scrutinize the permission requests before proceeding. Disallow any permissions that seem unconnected to the advertised functionality. A BMI calculator lacks any valid reason to require access to SMS or display screen recording capabilities.
- Monitor vigilantly for anomalous application behavior, indicative of diminished system performance, rapid battery depletion, and/or elevated data usage, potentially signifying clandestine operations running in the background.
With cybercrime’s relentless evolution, it is crucial that we remain perpetually proactive in protecting our digital existence. Despite their utility, apps like BMI Calculation VSN serve as a cautionary tale, highlighting how seemingly innocuous tools can conceal unforeseen dangers. While remaining vigilant and implementing robust security protocols, we can effectively protect our privacy and data.
Distribution web site:
- hxxps://www.amazon.com/PT-Visionet-Information-Internasional-CalculationVsn/dp/B0DK1B7ZM5/
C2 servers/Storage buckets:
- hxxps://firebaseinstallations.googleapis.com/v1/initiatives/testmlwr-d4dd7
- hxxps://6708c6e38e86a8d9e42ffe93.mockapi.io/
- testmlwr-d4dd7.appspot.com
Pattern Hash:
- 8477891c4631358c9f3ab57b0e795e1dcf468d94a9c6b6621f8e94a5f91a3b6a

Introducing McAfee+
Protecting Your Digital Life: Safeguarding Identity and Privacy

