
APT-C-60, a South Korea-allied cyberespionage group, has exploited a previously unknown Windows-based WPS Office zero-day flaw to implant the SpyGlace backdoor on East Asian targets.
WPS Workplace is a productivity suite developed by China-based software company Kingsoft, widely used across Asia. According to reports, the platform boasts a staggering number of more than 500 million active users globally.
The zero-day flaw, identified as CVE-2024-7262, has been exploited in the wild since at least late February 2024, affecting versions from 12.2.0.13110 (August 2023) to 12.1.0.16412 (March 2024).
Without warning, Kingsoft quietly remedied the flaw in March, failing to notify customers that hackers were actively exploiting it; this prompted cybersecurity firm ESET, which initially discovered the campaign and vulnerability, to release a detailed report.
With the revelation of CVE-2024-7262, cybersecurity experts were further alarmed by the discovery of a second critical vulnerability, identified as CVE-2024-7263, which was swiftly addressed by Kingsoft in late May 2024 through the release of model 12.2.0.17119.
APT-C-60 exploitation
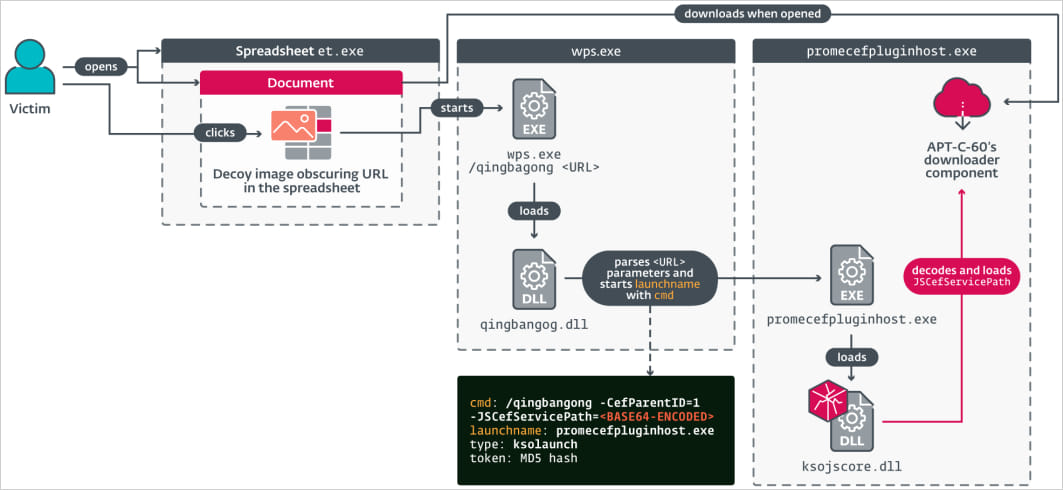
A vulnerability (CVE-2024-7262) exists in the handling of customised protocol handlers within software, specifically with ‘ksoqing://’ which enables the execution of external programs via specially crafted URLs embedded within documents.
Due to inadequate URL validation and sanitization, a vulnerability allows attackers to create malicious links that can lead to arbitrary code execution.
The APT-C-60 group crafted a deceitful spreadsheet containing malicious MHTML content, concealing harmful links beneath seemingly innocuous images designed to deceive victims into activating the exploit by clicking on them.
When processing URL parameters, a base64-encoded command is concealed, intending to execute a designated plugin (promecefpluginhost.exe), which then endeavours to load a malicious Dynamic Link Library (DLL) named ksojscore.dll, harbouring the adversary’s code.
The DLL is a component of the APT-C-60 malware, specifically responsible for downloading and installing the primary payload, TaskController.dll, which enables the SpyGlace backdoor.
SpyGlace is a notorious backdoor that gained notoriety after being employed by APT-C-60 in targeted attacks against human rights organizations and entities involved in international trade.
Unhealthy patch leaves hole
Researchers at ESET uncovered the vulnerabilities in APT-C-60’s attacks, specifically identifying CVE-2024-7263, a previously unknown arbitrary code execution flaw affecting WPS Workplace. This newly discovered issue was found to be an incomplete patch of CVE-2024-7262.
Kingsoft initially attempted to address the problem by implementing parameter-specific validation. Despite efforts to secure certain components, such as ‘CefPluginPathU8’, vulnerabilities remain, allowing attackers to successfully inject malicious DLL paths via the promecefpluginhost.exe process once again?
The cybersecurity firm ESET warns that the newly discovered vulnerability is likely to be exploited within domestic networks or through community-sharing platforms, potentially hosting the malicious DLL.
Despite this opportunity, no exploitation of the vulnerability was observed in the wild by the researchers or actors such as APT-C-60. Despite the urgency, it’s plausible that they would have discovered the security vulnerability created by Kingsoft’s hazardous update with sufficient time and effort.
Customers using WPS Workplace are recommended to upgrade to the latest release as soon as possible, specifically version 12.2.0.17119, to mitigate all code execution vulnerabilities.
“With its misleading appearance, this exploit poses a significant threat to unsuspecting consumers who may click on what appears to be a harmless spreadsheet, underscoring the importance of caution in today’s digital landscape.”
The use of MHTML files enabled attackers to exploit a remote code execution vulnerability.
Analyzing a comprehensive catalog of indicators of compromise (IoCs) linked to the APT-C-60 drill is crucial for identifying and mitigating potential threats.

