At Sophos, your safety is our top priority. With our investment, Sophos Firewall has become the industry’s most secure option, and we continuously strive to render it an unyielding barrier against hacking attempts.
To enhance your organization’s overall security stance, we highly recommend that you conduct regular assessments and integrate best practices across all your community infrastructure, regardless of the vendor – whether Sophos or others.
Obtain the necessary information and learn on from there.
Maintain firmware updated
Each Sophos Firewall OS release comprises critical security enhancements, including our latest iteration.
Make sure you maintain your firmware updated underneath Backup & Firmware > Firmware. Regularly verify and update firmware within at least a one-month interval via Sophos Central or the on-box console to ensure optimal system functionality. You’ll easily schedule updates in Sophos Central to minimize downtime and ensure seamless deployments over a specified period.
On-line guides:
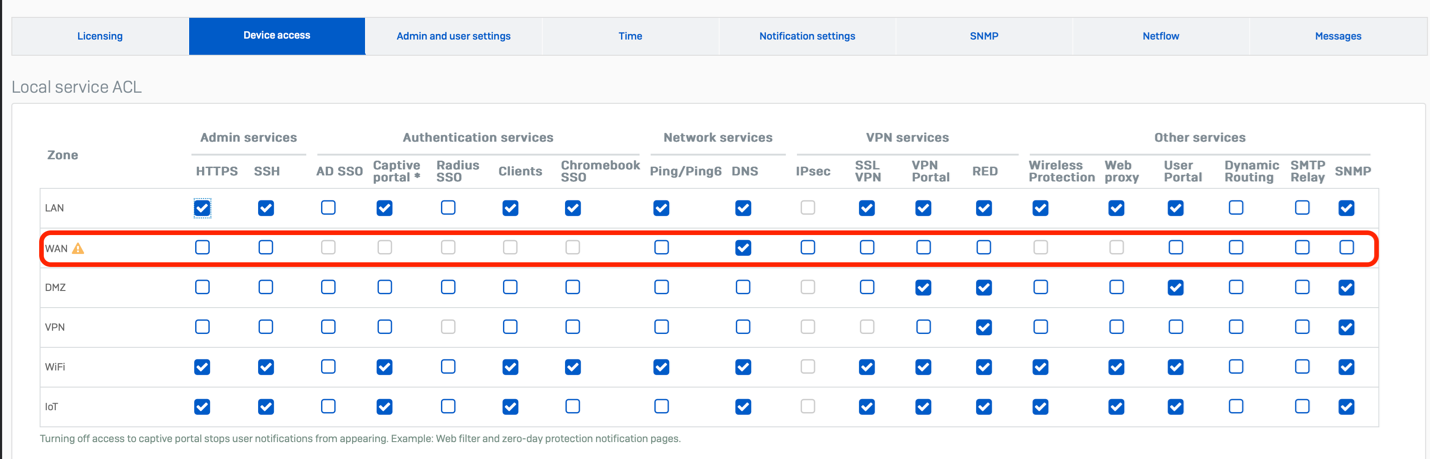
Restrict gadget service entry
It’s imperative to disable all unnecessary services on your WAN interface to ensure optimal network performance and security. Companies offering HTTPS and SSH administration?
Sophos Central offers a safer alternative to handling your firewall remotely by enabling a WAN administrator entry. Alternatively, consider remote management of your community devices.
Verify your native companies entry management underneath Administration > System Entry and guarantee no gadgets are checked for the WAN Zone except completely crucial:
On-line guides:
Utilize robust password management, implement multi-factor authentication protocols, and configure role-based access control to safeguard digital assets.
Implement robust passwords and consider enabling multi-factor authentication or one-time passwords to safeguard against unauthorized access to your firewall, effectively shielding it from stolen credentials and brute-force hacking attempts.
Ensure that your sign-in security settings are configured to prevent repetitive failed login attempts and utilize robust passwords in conjunction with CAPTCHA verification. Furthermore, implement role-based entry controls to ensure limited access and maintain confidentiality.
On-line guides:
Reduce entry to inside techniques
Any device exposed to the WAN via a NAT rule is potentially vulnerable. IoT devices should not require discovery through NAT or inbound connections, ideally.
Regularly scrutinize and reassess all NAT and firewall configurations to guarantee that no unauthorized WAN-to-LAN or remote access has been inadvertently enabled. Implement secure remote access controls by utilizing Zero Trust Network Access (ZTNA) and Virtual Private Networks (VPNs) when connecting to internal systems from a distance, ensuring that sensitive technologies remain inaccessible to the public internet and minimizing exposure of vulnerable services like distant desktop connections.
To mitigate potential security threats, disable or decommission any Internet of Things (IoT) devices that lack robust cloud proxy services and necessitate manual configuration via Network Address Translation (NAT), as these devices are inherently vulnerable to exploitation by malicious actors.
On-line guides:
Allow applicable safety
Protect your community from potential threats by leveraging the combined power of Transport Layer Security (TLS) and Intrusion Prevention System (IPS) inspection, carefully configuring relevant firewall rules to scrutinize incoming traffic from unknown or untrusted sources. Optimize your TLS and IPS inspections by harnessing the power of trusted utility FastPath offloading, thereby achieving optimal safety and efficiency in your specific environment. Avoid establishing sweeping firewall configurations that authorize unrestricted communication between arbitrary entities.
Additionally shield your community from each DoS and DDoS assaults by setting and enabling safety underneath Intrusion Prevention > DoS & spoof safety. Enhance spoofing resistance and implement flags for all types of Denial-of-Service (DoS) assaults.
Block unwanted visitors from regions not engaged in enterprise transactions by implementing a firewall rule that restricts access from suspect countries or geographic areas.
Sophos X-Ops ensures that all risk feeds are properly configured to log and block malicious activity beneath the scope of Advanced Threat Protection.
On-line guides:
Allow alerts and notifications
Can Sophos Firewall be configured to notify directors of system-generated occurrences? Directors should ensure that systems are in place to assess the list of incidents, verifying that system and safety occurrences are effectively monitored to facilitate timely action on issues and events.
Notifications are dispatched via both email and SNMP traps. To configure Notifications, navigate to Configure > System companies and choose the Notifications listing tab.
On-line guides:
Extra information
Consider leveraging Sophos Firewall’s capabilities and consult with experts to fully utilize its features.

