The previous phrase “we’re solely human, in spite of everything” is what cyber-adversaries are relying upon to achieve entry to mental property, knowledge, and credentials. Adversaries prey on the humanity in us to learn an unsolicited electronic mail, act out of a way of urgency, or succumb to their scare techniques.
We’re bombarded with social engineering scams every day. Why do a few of us fall sufferer whereas others see via veiled makes an attempt at getting us to relinquish one thing of worth? At LevelBlue, we set about researching social engineering and the human component and got here away with some telling knowledge in addition to the gaps the place attackers thrive.
Listed below are a couple of highlights from the analysis. How is your group coping with social engineering? Do you could have a plan for worker training? Do you could have a tradition of cybersecurity?
Obtain this new analysis now and use it as a place to begin in your dialogue on social engineering.
1. Construct a tradition of cybersecurity from the highest. Solely 43% of organizations have a robust cybersecurity tradition. Management because it pertains to cybersecurity implies that all leaders have accountability for cybersecurity together with KPIs and metrics.
2. Spend money on training. Deepfakes are problematic; 59% of organizations say their staff are unable to discern actual from faux. And, solely 26% of organizations make workforce coaching a main space of focus. New varieties of assaults name for brand new varieties of coaching. With out consciousness of social engineering techniques, well-meaning staff might fall to a cyber adversary.
3. Put together and perceive rising assault varieties. Adversaries wish to keep one step forward of us, and so they do that by evolving their assault varieties. A majority of organizations, 56%, really feel ready for enterprise electronic mail compromise (BEC) assaults. Nonetheless, preparedness for deepfake (32%) and AI-driven (29%) drops sharply, regardless of these assault varieties seen as prone to happen.
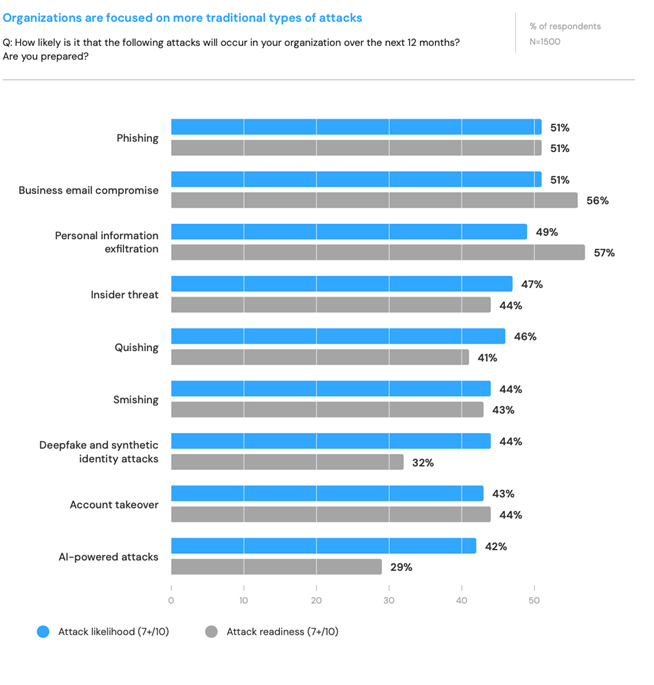
Constructing a tradition of cybersecurity, investing in workforce training, and getting ready for rising assault varieties focused at people show that cybersecurity shouldn’t be a technical difficulty – it’s a enterprise requirement.
The content material offered herein is for common informational functions solely and shouldn’t be construed as authorized, regulatory, compliance, or cybersecurity recommendation. Organizations ought to seek the advice of their very own authorized, compliance, or cybersecurity professionals concerning particular obligations and threat administration methods. Whereas LevelBlue’s Managed Risk Detection and Response options are designed to help menace detection and response on the endpoint degree, they aren’t an alternative choice to complete community monitoring, vulnerability administration, or a full cybersecurity program.

