
Scattered Spider hackers have been aggressively focusing on virtualized environments by attacking VMware ESXi hypervisors at U.S. firms within the retail, airline, transportation, and insurance coverage sectors.
In response to the Google Menace Intelligence Group (GITG), the attackers preserve using their common ways that don’t embody vulnerability exploits however depend on completely executed social engineering “to bypass even mature safety packages.”
A Scattered Spider assault
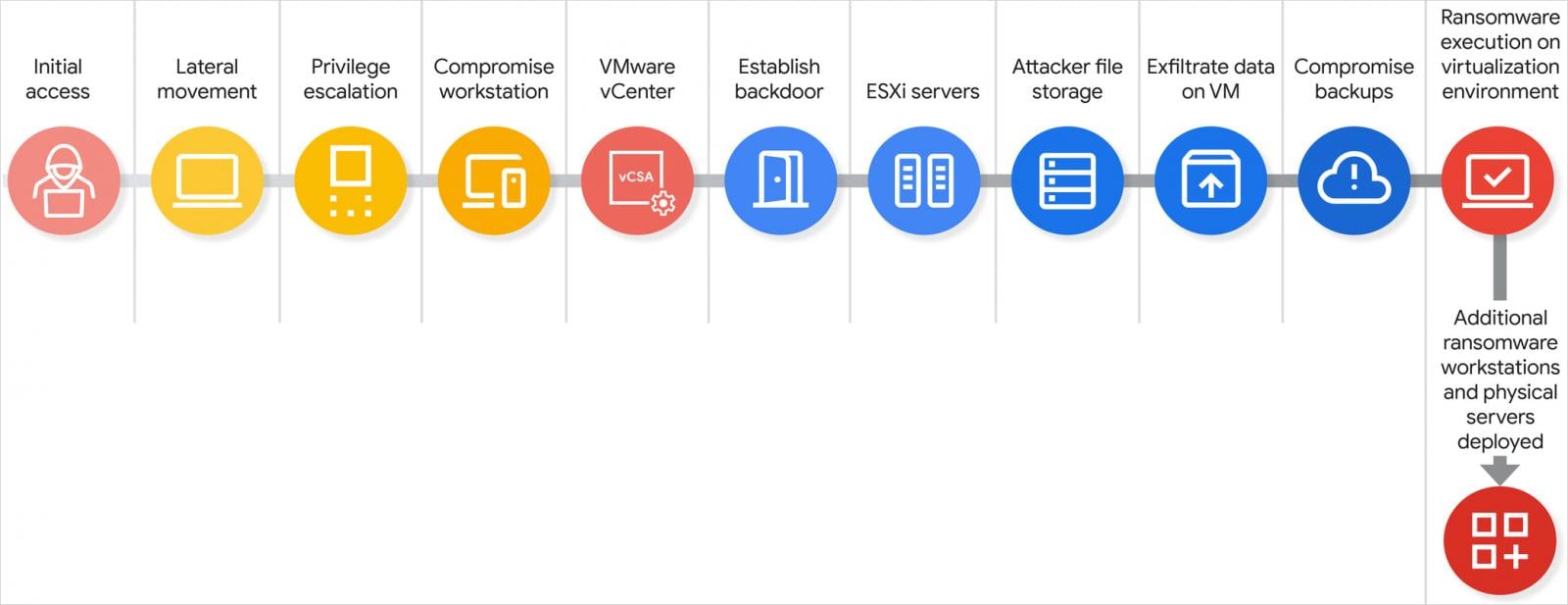
The researchers say that the gang begins an assault by impersonating an worker in a name to the IT assist desk. The risk actor’s function is to persuade the agent to vary the worker’s Lively Listing password and thus get hold of preliminary entry.
This enables Scattered Spider to scan the community gadgets for IT documentation that would supply high-value targets, just like the names of area or VMware vSphere directors, and safety teams that may present administrative permissions over the digital setting.
On the identical time, they scan for privileged entry administration (PAM) options that might maintain delicate information helpful for shifting to precious community belongings.
“Armed with the title of a selected, high-value administrator, they make extra calls to the assistance desk. This time, they impersonate the privileged person and request a password reset, permitting them to grab management of a privileged account” – Google Menace Intelligence Group
The hackers then work their technique to get hold of entry to the corporate’s VMware vCenter Server Equipment (vCSA) – a digital machine that enables managing VMware vSphere environments, which incorporates the ESXi hypervisor for managing all of the digital machines on a bodily server.
This stage of entry permits them to allow SSH connections on ESXi hosts and reset the foundation passwords. Additional, they execute a so-called “disk-swap” assault to extract the essential NTDS.dit database for the Lively Listing.
A disk-swap assault happens when the risk actors powers off a Area Controller digital machine (VM) and dettaches its digital disk solely to connect it to a different, unmonitored VM they management. After copying the delicate information (e.g NTDS.dit file), they revert the method and energy on the area controller machine.
You will need to be aware that the extent of management Scattered Spider obtains on the digital infrastructure permits them to handle each belongings out there, together with the backup machines, that are wiped of backup jobs, snaphots, and repositories.
Within the final part of the assault Scattered Spider leverages their SSH entry to ship and deploy ransomware binaries to encrypt all VM recordsdata detected within the datastores.
Primarily based on their observations, GTIG researchers say {that a} Scattered Spider assault has 5 distinct phases that permit hackers to maneuver from low-level entry to taking full management over the hypervisor.
Supply: Google
A Scattered Spider assault chain, full from preliminary entry to information exfiltration and ransomware deployment, might occur in only a few hours.
Even with out exploiting any software program vulnerabilities, the risk actor manages to acquire “an unprecedented stage of management over a complete virtualized setting, permitting them to bypass many conventional in-guest safety controls,” a Google consultant informed BleepingComputer.
Whereas focusing on ESXi hypervisors is just not new (seen in Scattered Spider high-profile breaches just like the 2023 MGM Resorts assault) GTIG notes that they’re seeing extra ransomware teams adopting this tactic and anticipate the issue to develop.
One purpose behind this might be that adversaries have observed that VMware infrastructure is usually poorly understood by organizations and, consequently, not as robustly defended.
To assist organizations shield towards these assaults, Google printed a technical submit describing the phases of a Scattered Spider assault, explaining why it’s environment friendly, and offering actions that an organization can take to detect the breach at an earlier part.
The proposed measures could be summarized in three primary pillars:
- Lock down vSphere with execInstalledOnly, VM encryption, and disabled SSH. Keep away from direct AD joins on ESXi, delete orphaned VMs, and implement strict MFA and entry insurance policies. Constantly monitor for config drift.
- Use phishing-resistant MFA throughout VPN, AD, and vCenter. Isolate Tier 0 belongings (DCs, backups, PAM) and keep away from internet hosting them on the identical infrastructure they safe. Contemplate separate cloud IdPs to interrupt AD dependency.
- Centralize logs in a SIEM and alert on key behaviors, resembling admin group modifications, vCenter logins, and SSH enablement. Use immutable, air-gapped backups and check restoration towards hypervisor-layer assaults.
Scattered Spider (also called UNC3944, Octo Tempest, 0ktapus) is a financially motivated risk group specialised in social engineering to a stage that it could possibly impersonate firm staff utilizing the suitable vocabulary and accent.
It has not too long ago upped its exercise with assaults on massive UK retail corporations, airline and transportation entities, and insurance coverage firms.
Though the UK’s Nationwide Crime Company arrested 4 suspected members of the group, the malicious exercise, originating from different clusters, has not subsided.
CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud safety drives enterprise worth.
This free, editable board report deck helps safety leaders current threat, influence, and priorities in clear enterprise phrases. Flip safety updates into significant conversations and sooner decision-making within the boardroom.


