According to Intel471’s latest findings, malicious actors are increasingly targeting macOS with tailored malware or exploiting cross-platform vulnerabilities to achieve their goals on Apple computers.
The discovery of additional macOS vulnerabilities has led to their exploitation in the wild. Cybercriminals frequently employ vulnerabilities to carry out various types of cybercrime and espionage.
As macOS’s security reputation has grown, so too have the attempts to compromise its defenses. According to a recent report, malicious software is more prevalent on Apple devices than ever before, with over 90% of companies experiencing at least one malware incident in the past year alone. This alarming trend is attributed largely to the proliferation of ransomware, which has seen a staggering 1500% increase since last quarter, as well as the emergence of new, highly sophisticated strains designed specifically to evade Apple’s built-in security features.
Between January 2023 and July 2024, researchers observed more than 40 threat actors targeting macOS vulnerabilities with diverse malware types, including a majority of infostealers and trojans.
Infostealers
Malware known as info stealers, or infostealers, continue to evolve and spread across various platforms, including workstations and macOS systems.
According to cloud security company Uptycs, the number of incidents involving infostealers nearly doubled during the first quarter of 2023 compared to the same period in 2022. Cybersecurity firm Group-IB reports a staggering fivefold increase in illegal online market demand for macOS-targeted malware.
Cybercriminals leverage such software programs to pilfer login credentials, session cookies granting unauthorized access without the need for authenticating credentials, as well as sensitive data like bank card details or cryptocurrency wallet information. The software programme can also be widely utilised by individuals who obtain legitimate credentials, typically sourced from companies rather than individuals, and resell them to other cybercriminals.
Atomic Stealer, also referred to as Atomic macOS Stealer (AMOS), has emerged as a dominant force in the realm of macOS infostealers since its inception in 2023. Malware is engineered to pilfer login credentials and digital wallet data from Apple computers and web browsers.
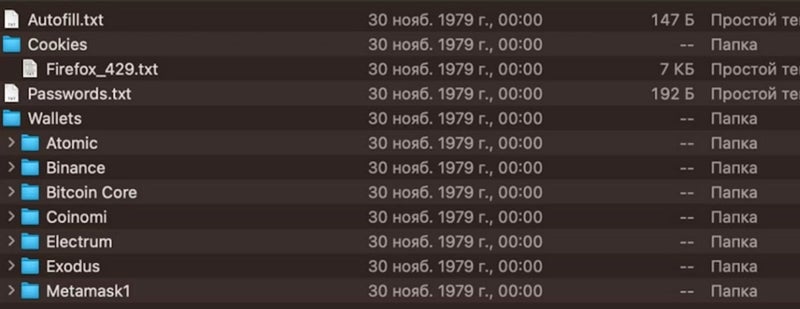
However, a significant proportion of cybercriminals are currently involved in promoting and operating various infostealers that specifically target macOS systems? A notorious threat actor, known by the moniker “codehex,” has been actively marketing a sophisticated macOS malware tool called ShadowVault, which is capable of exfiltrating sensitive data from compromised computer systems, including information stored in Chrome-based browsers, saved files, and even cryptocurrency wallets.
The malicious actors behind these threats may also disguise their creations by affixing an Apple developer signature, thereby complicating the job of security programs to detect them effectively. The malicious software was marketed as a monthly subscription service, priced at $500 per month under a Malware-as-a-Service (MaaS) business model.
Trojans
Distant-entry Trojans are another increasingly prevalent type of malware targeting macOS systems.
A macOS malware, allegedly created in the Rust programming language and potentially linked to a ransomware threat actor, provides its operator with several features.
- Executes distant instructions.
- Manipulates information on compromised techniques.
- Provides extra payloads.
- Collects system data.
This innovation creates a unique solution to counter each type of cyberespionage and cybercrime threat actor. The Rust programming language has gained popularity among malware developers due to its ability to create cross-platform software that can easily be ported to any operating system.
Ransomware
“The discovery of macOS ransomware strains a sense of unease as threat actors increasingly seek innovative ways to target Apple users.”
In April 2023, researchers unveiled a novel encryptor targeting the notorious ransomware strain, which specifically attacks macOS systems, including those running on Apple’s latest silicon-based architectures.
In late 2023, another relatively unsophisticated ransomware strain emerged, dubbed Turtle, which was built using the cross-platform programming language Golang, also known as Go. The malware was initially unsigned, a rare occurrence, but never received official notarization, rendering it detectable by Gatekeeper, according to safety researcher Patrick Wardle’s expertise.
Vulnerabilities exploited
The number of macOS vulnerabilities exploited in 2023 surged by more than 30% according to Action1, a leading provider of patch administration software.
Notwithstanding the significant findings by Intel471, it is crucial to note that the cybersecurity firm identified an alarming 69 vulnerabilities in various iterations of macOS between March 2020 and July 2024, with more than 10 classified as high-risk. Some of these vulnerabilities have already been exploited by malicious cyberactors involved in espionage activities.
A sophisticated malware campaign has been discovered, targeting numerous state-sponsored entities globally with a variant of the Cytrox’s Predator adware, specifically affecting various versions of macOS due to an unspecified vulnerability (CVE-2023-41993).
Threat actors have exploited CVE-2023-41064, a serious buffer-overflow vulnerability. The notorious cyberespionage group extended its nefarious services to state-backed entities, peddling its malicious adware offerings.
A notorious cybercriminal, known by their handle oDmC3oJrrSuZLhp, has reportedly listed a critical exploit for sale on an underground forum, with the vulnerability priced at $2.7 million. The CVE-2022-32893 flaw enables attackers to execute arbitrary code on targeted systems.
State-sponsored menace actors
While some adware vendors cater to state-sponsored malicious actors, it’s notable that several threat actors also produce malware and tools specifically designed for macOS platforms.
The notorious North Korean threat actor, known for their nefarious activities, has created a sophisticated malware component dubbed, specifically designed for macOS and targeting financial institutions involved in cryptocurrency transactions.
The group specifically targets individuals holding cryptocurrency assets, with the ultimate goal of pilfering all associated crypto funds from compromised wallets.
Russian menace actors, reportedly affiliated with both the Russian Main Intelligence Directorate (GRU), a component of the Russian Ministry of Defence, and Russia’s foreign intelligence agency SVR, have also employed macOS malware in their arsenal.
The XAgent modular backdoor, employed by APT28, has been in operation for several years, featuring a module that enables the exfiltration of sensitive data from compromised macOS devices, including iOS backups containing confidential information such as messages, contacts, voicemail records, call histories, notes, and calendars. APT29 leveraged a now-unsupported, cross-platform distant administration and post-exploitation framework to concentrate its efforts on compromising macOS systems.
Vietnamese threat actor APT32 has expanded its scope by deploying a macOS variant focused on targeting various organizations, in addition to its existing Linux and Windows malware arsenal.
guard towards this menace
Regular updates and patches for macOS are crucial to prevent exploitation of widespread vulnerabilities and ensure ongoing security.
The safety of our systems requires that we deploy a robust software program that detects and responds to malware and suspicious activity in real-time? Email safety options, including robust filtering and authentication protocols, are crucial for preventing initial compromises, as many preliminary breaches occur through phishing emails targeting unsuspecting users.
Ultimately, all workers must possess the skills to identify and mitigate potential social engineering tactics employed through emails or instant messaging platforms.

