Scammers are bombarding the internet with fraudulent teams claiming to offer live video streaming services from funeral homes for recently departed individuals. Family members and friends watching the streaming services’ hyperlinks are subsequently asked to provide their credit card information. Recently, fraudulent entities have diversified their tactics by offering fake streaming services for various events, often promoted through Facebook.
A comprehensive analysis of the scheme’s dimensions reveals several key aspects, with findings that implicate specific parties in its operation.
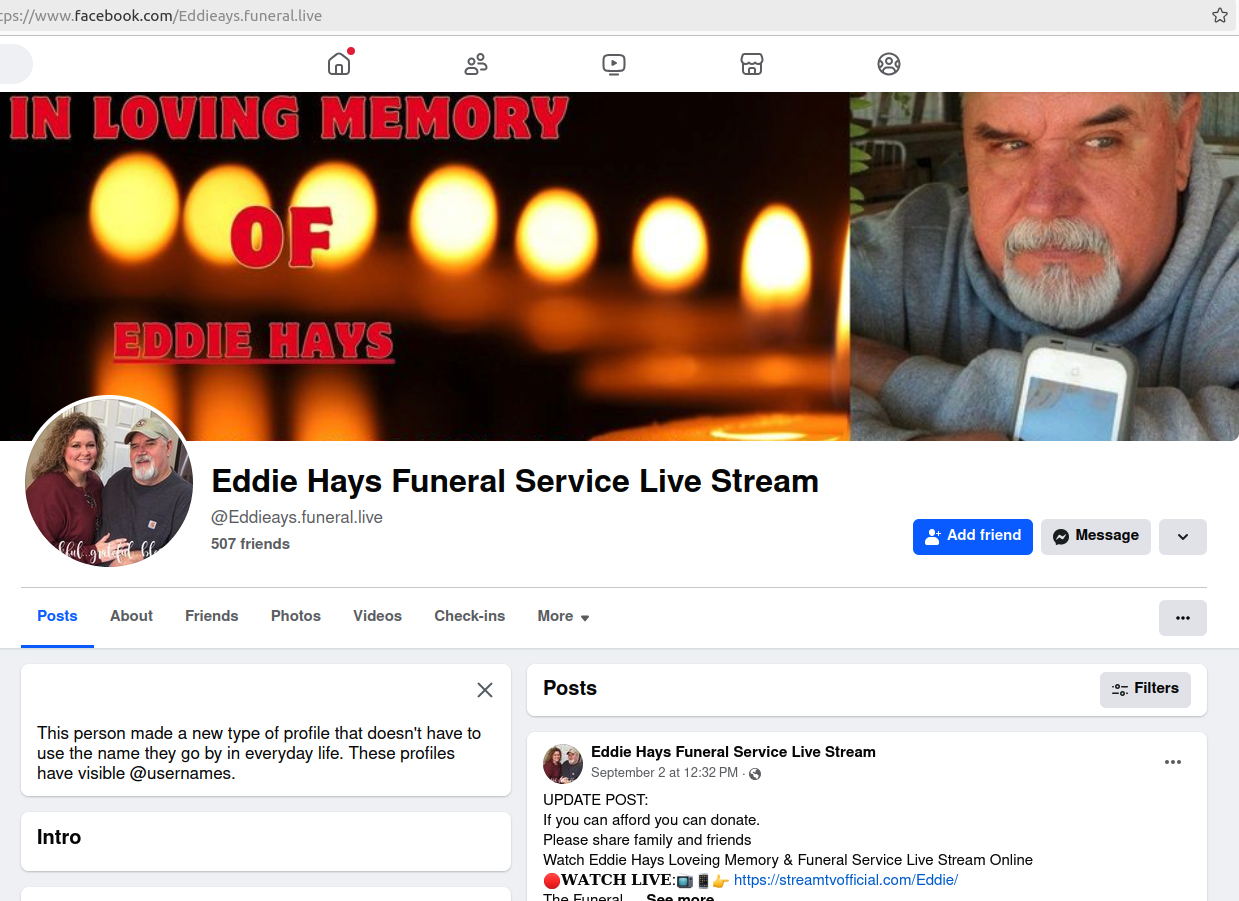
A plethora of deceitful funeral-related groups on Facebook. Upon clicking to access the “dwell stream” of the funeral, users are directed to a recently created website that demands sensitive financial information, including bank card details.
Recently, KrebsOnSecurity received an email from a reader named George, who reported that his friend had passed away, and he noticed the creation of a Facebook group in memory of that friend. The web page accurately provided the timing and date of the funeral service, stating that it might also be accessible online via a link leading to a webpage requiring credit card information for streaming purposes.
“When discussing the website’s peculiarities, George shared that his friend had experienced a similar incident, having lost a close acquaintance just two weeks prior.”
Upon conducting a search for key phrases “funeral” and “stream” on Facebook/Meta, several funeral-related group pages emerge, comprising both businesses and temporary pages established in anticipation of an upcoming funeral.
The majority of these entities utilise mugshots of deceased individuals as their profile pictures, while simultaneously attempting to redirect users to a limited number of recently launched video streaming platforms that demand credit card information before permitting access? More egregious still, some of these memorials brazenly solicit donations in the name of the very individuals they seek to honor.
Although the exact number of Facebook users duped by this scam remains unclear, it’s worth noting that many fake funeral groups target subscribers from a minimum of several of the deceased’s followers, implying these customers had already subscribed to the groups in expectation of the service being live-streamed. Without fail, numerous people are left feeling bereft after missing a loved one’s funeral due to the mistaken assumption that it would be livestreamed.
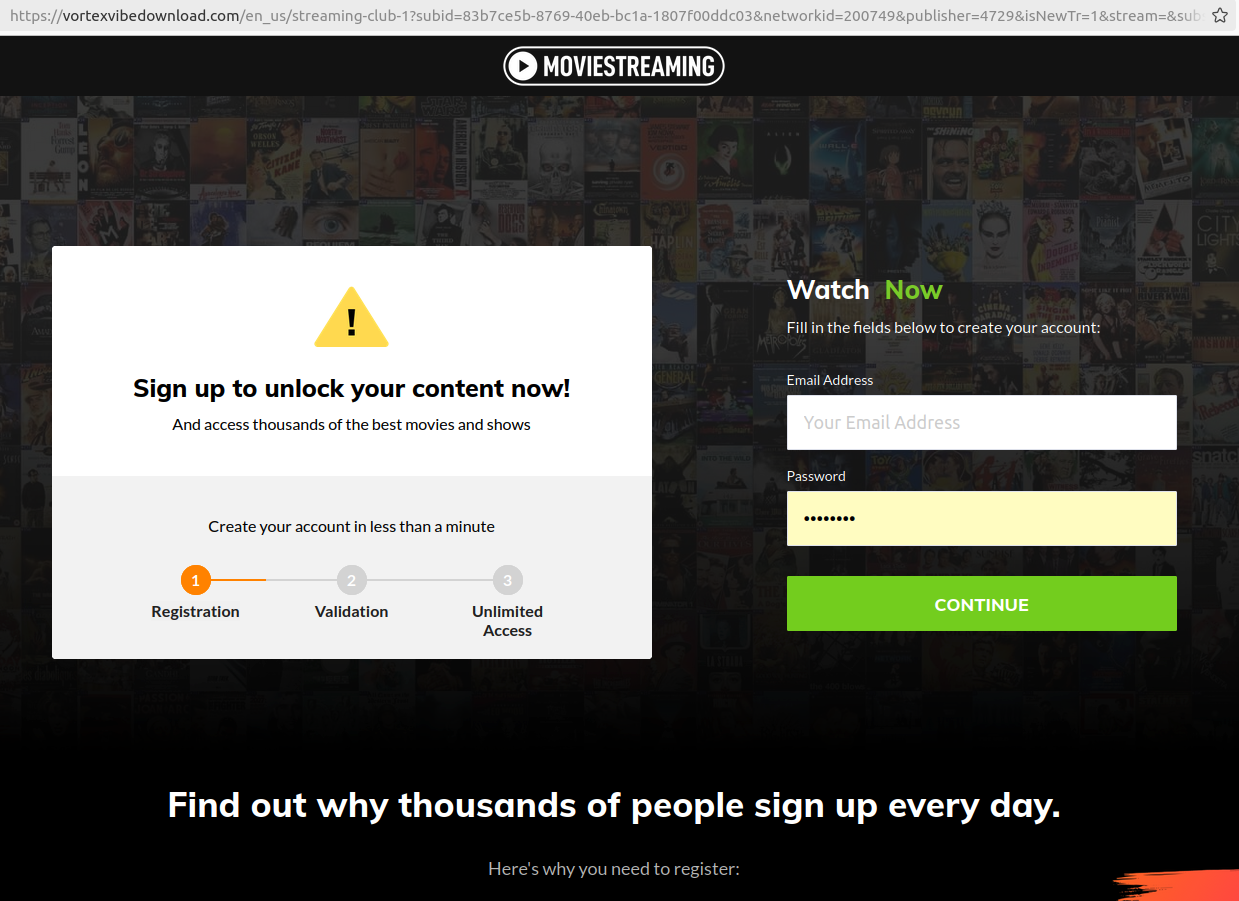
Among numerous seemingly identical touchdown pages linked to fraudulent Facebook groups, one stands out as a potential gateway to illegal activities.
George shared a Facebook post about their friend’s funeral service webpage, which featured a link to the live-streamed ceremony at [website URL], a domain registered as recently as November 2023.
Accordingly, the group responsible for registering this domain is called “that” relies on servers based in Rajshahi, Bangladesh, utilizing the Domain Name System (DNS) services provided by a hosting company named “Hosting Company”.
Upon conducting a search on “apkdownloadweb” in DomainTools, three domains registered to this entity are revealed: apkdownloadweb.com, apkdownloadweb.net, and apkdownloadweb.io. The four domains, namely [A], [B], [C] and [D], further employed the DNS service provided by webhostbd.internet. Apk Download Web features a wealth of “dwell video” teasers showcasing sports events that have already taken place, and claims its domain is the go-to destination.
The livestreaming platform, currently hosted by a Bangladeshi internet service provider, has historically utilized DNS servers provided by webhostbd.internet in addition to those of its primary host.
The web infrastructure for livestreamnow.xyz is hosted by Hetzner, a German-based Internet services company. DomainTools uncovers a similar web presence hosting numerous files, including a.csv file alongside several others referencing video streaming-related terms, such as and.
Thousands of domains reside at this IP address, comprising or ending with the country-code top-level domain for Bangladesh, denoted by “bd”. While numerous domains serve as websites for electronics retailers or blogs focused on IT topics, an equally significant number consist primarily of placeholder content, akin to the familiar “lorem ipsum” text often found on a website’s “contact” page. While some websites may initially appear official, a closer examination reveals they are actually dormant or inactive domains.
The passive DNS data for 148.251.54.196 reveals a diverse range of findings primarily comprising two domains combined in a single entity. There may be instances where hyperlinks are displayed, linking to numerous funeral service streaming teams available on Facebook.
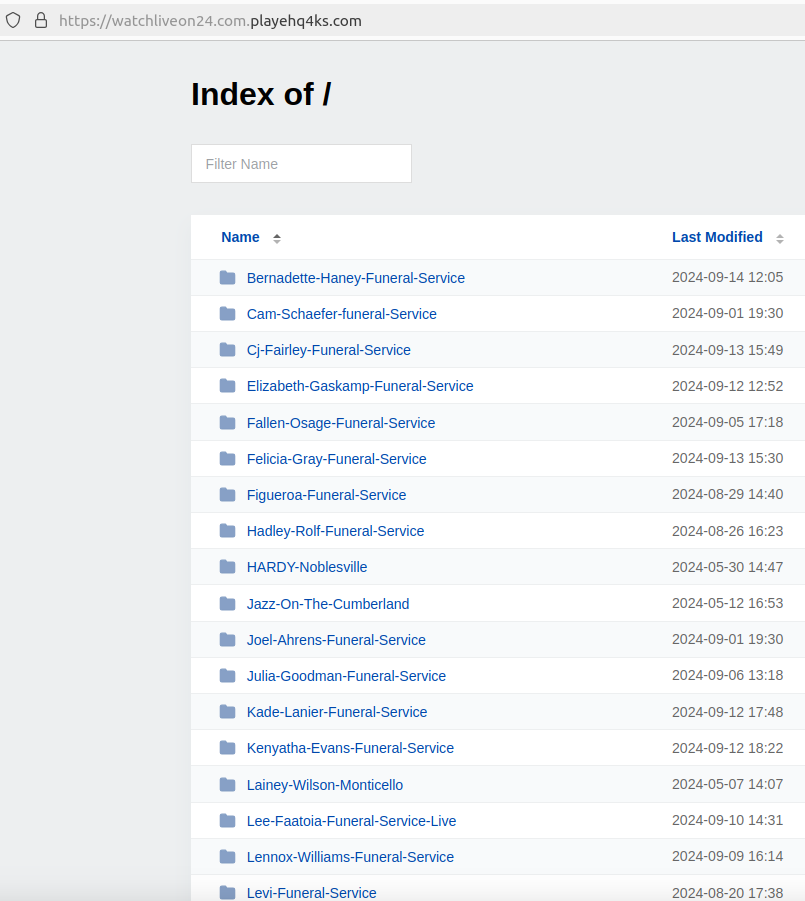
The mixed area on the same web tackle – livestreaming24[.]xyz.allsportslivenow[.]com – features a vast array of links to Facebook groups dedicated to various occasions, including funerals, as well as those for more lighthearted events such as graduations, concerts, award ceremonies, weddings, and rodeos.
Even social media events organized by state and local law enforcement agencies on Facebook have become a prime hunting ground for these scammers. The official Facebook page of the Plympton Police Department, Massachusetts. As anticipation built for this summer’s city social occasion, dubbed [], Facebook quickly spawned not one but two groups exclusively dedicated to the event. These digital hubs notified attendees that they could live-stream the festivities on either [] or [].
WHO’S BEHIND THE FAKEBOOK FUNERALS?
The registrant of livestreamnow[.]xyz, linked within the Facebook group for George’s late friend, was Apkdownloadweb, a corporation. Its domain is registered to an entity in Rajshahi, Bangladesh, utilizing Webhostbd[.]internet DNS servers.
According to Mazidul Islam’s LinkedIn profile, he served as the organizer for the now-discontinued IT blog, gadgetsbiz.com, which DomainTools reveals was registered by an entity based in Rajshahi, Bangladesh.
To deliver this service in full circle, DomainTools identifies the area title for the DNS provider on all aforementioned websites – webhostbd.internet – which was initially registered to an individual, with the email address “MD” (a common abbreviation for Muhammad/Mohammed/Muhammod).
During a search on that email address at Constella, we discover a compromised report from information vendor Apollo.io indicating that the owner’s full name is sadly not particularly unique in that region of the world.
Fortunately, last year the administrator of apkdownloadweb.com suffered a stroke of bad luck when they inadvertently infected their Windows PC with password-stealing malware. As revealed by a breach monitoring service, the unprocessed logs of stolen data from an administrator’s PC were compiled after the incident.
Notably, these self-proclaimed “stealer logs” are primarily fueled by insidious infections stemming from information-gleaning trojans readily available on illicit cybercriminal marketplaces. Typically, compromised PCs generate log files that reveal sensitive data, including stored usernames and passwords across all browsers on the device, as well as detailed records of recently accessed URLs and downloaded content.
Malware peddlers often distribute infostealers by disguising them as cracked or pirated software, hoping to ensnare unsuspecting users who seek free alternatives. Following the discovery of compromised administrator logs on apkdownloadweb.com, it appears that the individual’s personal computer became infected immediately upon downloading a tainted mobile software update package.
The stolen credentials suggest that Apkdownloadweb.com is operated by a young individual from Dhaka, Bangladesh.
According to the administrator of Apkdownloadweb, a “browser history” folder was accessed by Khondokar, who recently commented on the Facebook page of an individual, with their profiles indicating that they are acquaintances.
Despite multiple requests, neither MD Hasan nor MD Abdullah Khondokar provided a comment. A request for comment was also made to Meta by KrebsOnSecurity.

