Cybercriminals’ recent advancements have made it increasingly easier for scammers to capitalize on your forthcoming travel arrangements. The present phishing scam unfolds as a case study following the theft of a California resort’s login credentials. Cybercriminals are also offering a range of services specifically designed for phishing attacks targeting hotels and travel establishments heavily reliant on the world’s most popular online travel booking platform.
According to market share website data, Expedia.com holds the top spot as the Web’s most trafficked travel service, boasting a staggering 550 million visits in September alone. In the final days of KrebsOnSecurity, we received word from a concerned reader whose close friend fell victim to a targeted phishing scam shortly after making a reservation through the Reserve app in California.
The email, labeled with the resort’s name, cited specific information from the couple’s reservation, insisting that reserve.com’s fraud prevention protocol necessitated supplementary client data before the booking could be confirmed.

After acquiring a booking confirmation from reserving.com in late October, their acquaintance obtained the following phishing message.
Reservations.com has acknowledged a security breach involving one of its partners, which compromised customer booking information and enabled unauthorized access.
“Our safety teams are currently investigating the incident you brought up and may confirm that it was indeed a phishing attack targeting one of our accommodation partners, which unfortunately is not a new phenomenon and rather commonplace across industries.” “Crucially, we want to emphasize that Reserving.com’s internal systems and processes were not compromised in any way.”
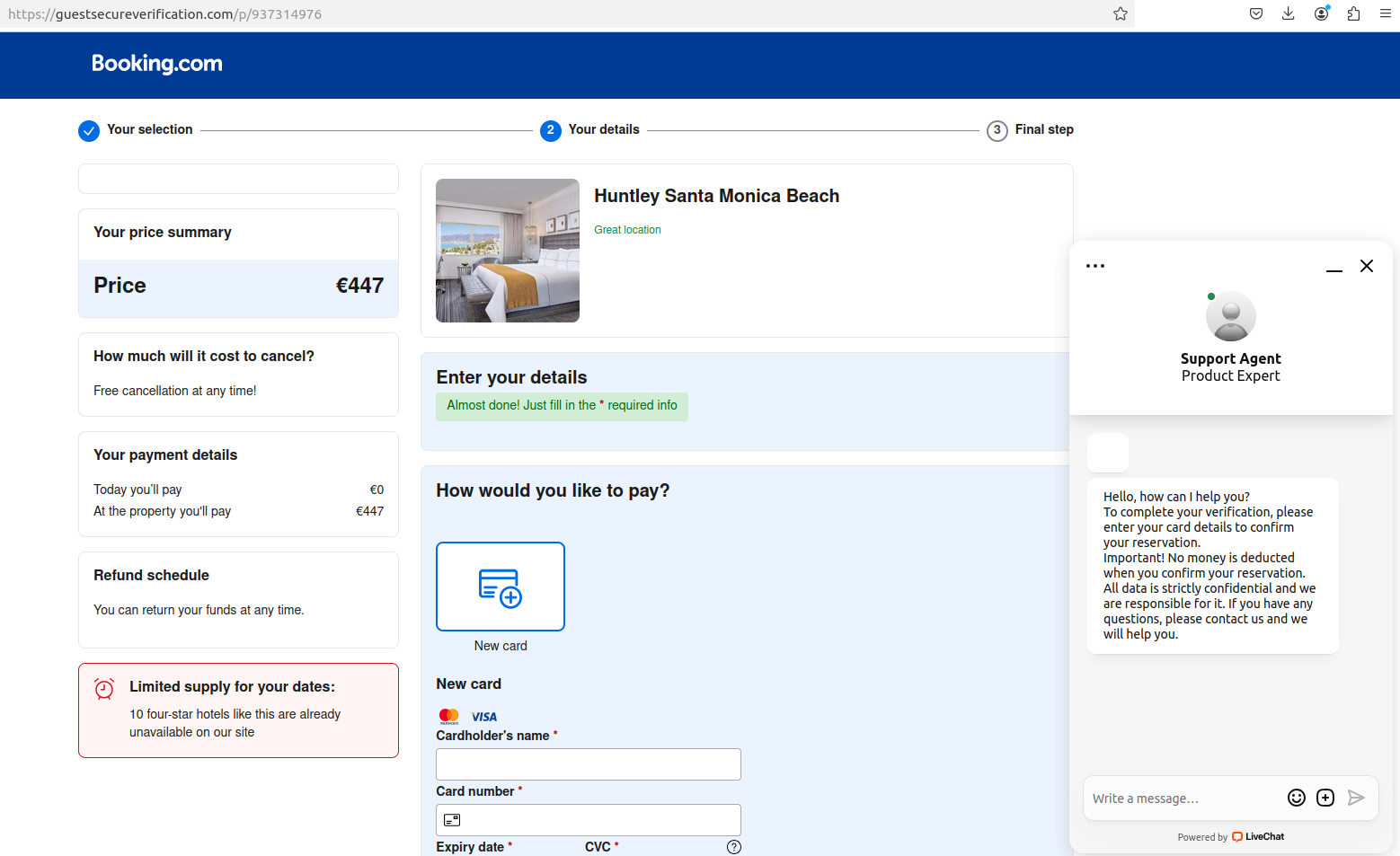
A suspicious website was generated when clicking on a link in an unsolicited text message.
Reserving.com has recently implemented new security measures, requiring guests to provide a one-time passcode generated through their mobile device’s authenticator app, in addition to their standard login credentials of username and password.
A reservation.com spokesperson stated that two-factor authentication is mandatory and rigorously enforced, in conjunction with the secure capture of booking details from customers. Because cybercriminals subsequently send messages to convince potential victims to transfer funds outside their trusted platform.
The phishing attacks originate from compromised devices belonging to users’ friends, allowing hackers to gain access not only to their machines but also to send malicious messages, as reported by your reader.
Although it’s unclear whether the corporation’s two-factor authentication (2FA) requirement applies to all partners or just newer ones? Reserved.com failed to respond to queries about this issue, and currently encourages users to enable two-factor authentication (2FA).
A social media scan revealed that this is just one instance in a long string of scams.
The Federal Trade Commission (FTC) announced in November 2023 that scammers had targeted hotel booking website Expedia.com, using data-stealing malware to compromise users’ personal information. Since at least March 2023, SecureWorks has reported that these attacks have been occurring.
The lack of multi-factor authentication on Reserving.com’s login process allowed an attacker to easily gain access to a compromised account, according to an investigation by SecureWorks.
By mid-2024, reports indicated a staggering 900% surge in phishing attacks targeting travelers on reservation platforms like Booking.com, with AI-powered fraudsters identified as the primary catalyst behind this alarming trend?
Reservation.com informed the Better Business Bureau that it has started leveraging artificial intelligence to combat AI-driven phishing attacks. According to Reserving.com, its investments in the environment have successfully blocked over 85 million fraudulent reservations and thwarted more than 1.5 million phishing attempts in 2023 alone.
The domain name in the fake reservation.com website sent to our readers’ friend — was registered to the email address. Accordingly, our email surveillance system successfully detected over 700 unique phishing domains in the past month alone.
Many of the over 700 gTLDs appear to concentrate on hospitality companies, including platforms such as booking.com. Scammers have created sophisticated schemes to deceive users of various online services, including financial institutions, leading to significant financial losses. A comprehensive, unobstructed list of domains is accessible.
According to an analysis of online forums monitored by the agency’s cybersecurity unit, there is a significant market demand for compromised Airbnb accounts owned by hosts and their associates.
Last month, a post was published on a Russian-language hacking forum offering up to $5,000 for each hacked hotel account. The vendor allegedly facilitates the exploitation of compromised Reserving.com accounts, reportedly using pilfered login information to create fictitious listings for illegitimate purposes.
Here is the rewritten text:
The online marketplace for illicit activities offered a service in October, targeting scammers who required support with specific aspects of their phishing schemes focused on Reserving.com users. The email addresses in question amount to more than two million, and the malicious providers are engineered to facilitate massive volumes of compromised data, enabling phishers to wreak havoc on a grand scale. Clients can collaborate seamlessly with our service through a convenient and intuitive automatic Telegram bot.
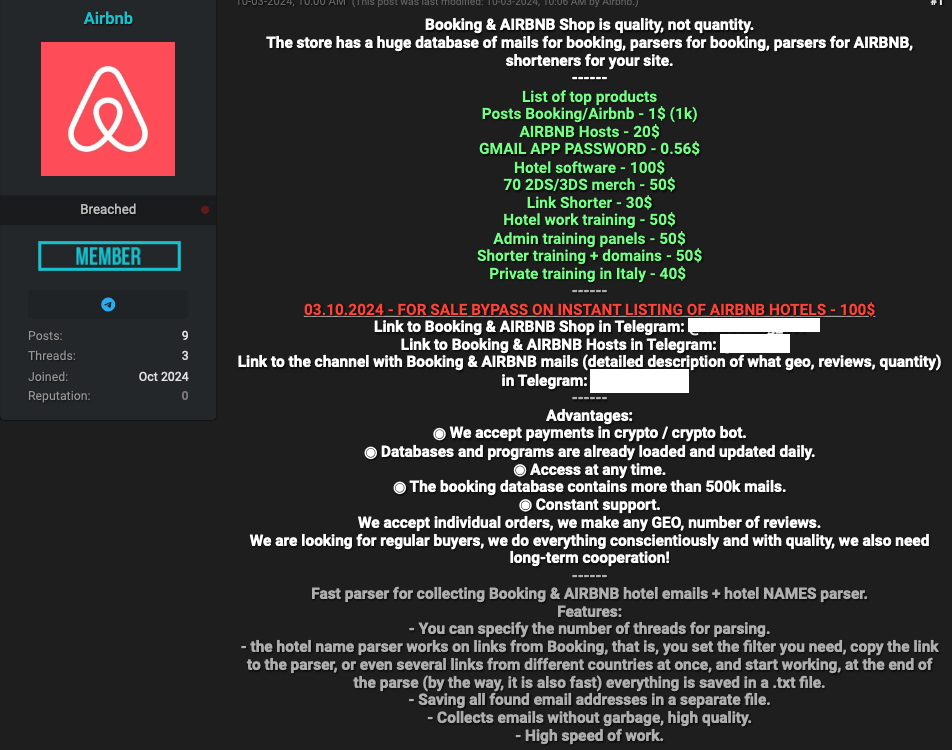
Cybercriminals allegedly leveraged compromised booking.com accounts to fuel the growth of their own travel agencies, targeting fellow fraudsters with up to 50% discounts on hotel bookings through booking.com. Thieves are exploiting easily accessible “config” files that facilitate unauthorized attempts to breach reserved.com administrator accounts, making automation of malicious login attempts a disturbingly straightforward process.
Cybersecurity firm SecureWorks has identified a phishing scheme targeting users of reservation website Expedia.com, where attackers employ malicious software to pilfer login credentials. Thieves can currently acquire stolen credentials for cloud providers that fail to enforce two-factor authentication (2FA) for all accounts by visiting online crime markets, a situation that allows them to gain unauthorized access with relative ease.
Over the past year, Dropbox has seen significant growth in its customer base, attracting numerous shoppers. By the end of 2023, hackers discovered that numerous companies had amassed massive amounts of customer data on Snowflake, with many of these accounts lacking two-factor authentication (2FA) protection.
Snowflake recently implemented a security measure to protect its user base, mandating two-factor authentication (2FA) for all newly registered users. However, a massive data breach occurred when hackers utilized compromised login credentials to exfiltrate sensitive information from a staggering 160 businesses, including major global companies such as and.

