Overview
As AI increasingly becomes an integral part of Windows, Microsoft is pushing the boundaries of what’s possible by harnessing the power of a 40+ TOPS Neural Processing Unit on Copilot+ PCs. This allows for decreased latency, extended battery life for demanding AI tasks, seamless AI experiences offline, and enhanced privacy through local data storage.
As the integration of fashion and AI-related data processing on PCs introduces novel cybersecurity risks, it is crucial to consider these vulnerabilities during product development. The following text provides an overview of the security and privacy models, architecture, and technical controls implemented in Recall, a cutting-edge technology premiering on Copilot+ PCs, designed to ensure seamless user experiences while safeguarding sensitive information. Instantly and securely recall past experiences on your computer with this intuitive tool’s immediate assistance.
Safety and privateness design ideas
- Recall’s design prioritizes safety and privacy, built upon four core principles that align with the updates:
The individual remains consistently engaged in a leadership capacity throughout.- Recall is an opt-in expertise. With Copilot+ PC setup, customers are presented with a clear choice to opt-in and enable Recall’s snapshot-saving feature, offering transparency in their decision-making process. If the option isn’t explicitly enabled, the feature will remain inactive, precluding both snapshot capture and storage. Customers can entirely disable Recall by configuring optional settings within Windows.
- Sensitive data stored in Recall remains consistently encrypted, with keys safeguarded accordingly.
- Providers that operate on snapshot data and associated information are remotely managed.
- Within Recall, providers conducting screenshot analysis and decryption activities operate within a secure Virtualized-Based-Security (VBS) enclave. One piece of data that exits the VBS Enclave is the information specifically requested by the user while actively utilizing the Recall feature.
- Customers are deliberately mindful of their Recall utilization.
- Recall utilizes Windows Hello’s Enhanced Sign-in Security to authenticate Recall-related activities. Recall settings are modified and runtime authorizations for accessing the Recall person interface (UI) are implemented. Recall’s advanced security features include real-time monitoring and rate-limiting, as well as anti-hammering measures to safeguard against malicious attacks. When Recall is properly set up, PIN serves as a backup solution exclusively, ensuring data preservation in the unlikely event of a faulty safety sensor malfunction.
Recall safety mannequin
Snapshots and associated information are safeguarded within secure Virtual Secure Enclaves, utilizing an identical hypervisor as Azure to partition the computer’s memory into a dedicated, protected space where data can be processed. With zero-trust principles applied, the enclave’s code leverages cryptographic attestation protocols to verify the environment’s security before executing sensitive operations such as snapshot processing. This space functions as a secure field, accessible only upon receiving permission from the user via Windows Hello. VBS (Virtual Blade Server) enclaves are established from each kernel and administrative customer.
Snapshots of your Windows system can only be accessed after successful authentication using your Windows Hello biometric credentials.
Especially in Home Windows, the enhanced sign-in safety feature uses advanced biometric credentials to safeguard your privacy while actively verifying your identity to access and explore relevant data and associated images.
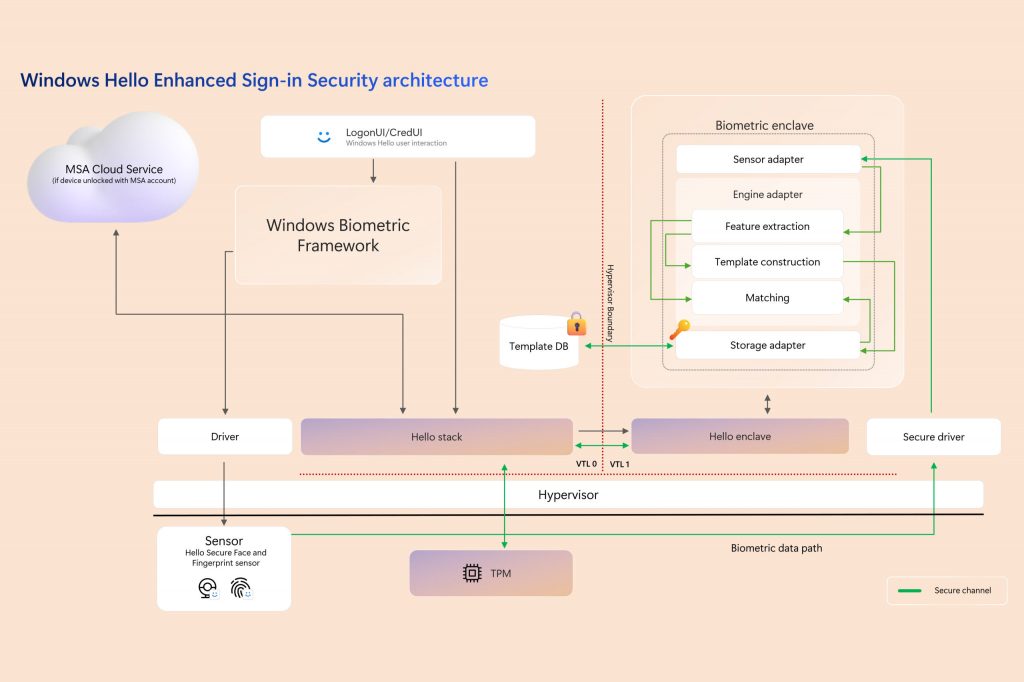
To access recall content, biometric credentials must be enrolled first. Using Windows Hello Enhanced Sign-in Security, encrypted data is temporarily decrypted when employing the Recall feature to access. If authorization is not confirmed within a specified timeframe, future class access may be temporarily suspended, prompting the individual to re-authorize their participation. The restricts in place aim to thwart attempts by latent malware that seek to ‘piggyback’ alongside user authentication and steal sensitive information.
Recall privateness controls
Recall remains an entirely voluntary process at every juncture. Unless you opt to utilize Recall, snapshots typically aren’t captured or stored. Snapshots and associated data are stored locally on the device. Recall doesn’t share any user data, including snapshots and related information, with Microsoft or external entities. Additionally, this data remains private to each individual Windows user on a device and isn’t accessible to others, even if they use the same machine. Prior to saving screenshots, Home Windows will prompt you for permission. As a manager, you have the authority to control and adjust snapshot settings at any moment, allowing for instant deletion, pausing, or disabling of snapshots as needed. Future sharing of information will necessitate explicit and informed consent from the individual in question.
Windows offers a comprehensive suite of tools to help you manage your privacy and customize what gets stored, making it easy to recall and access information when needed.
- Rarely is an in-private look preserved.
- Customers can filter out specific applications or websites displayed in supported browsers.
- Customers can manage the length of time recall content is retained and allocate as much disk space as needed for snapshots.
- By default, Recollect features a robust password filter that discreetly shields sensitive data like login credentials, national identification numbers, and credit card information to prevent their storage within the app. deployed globally across various enterprises.
- The one thing I didn’t intend to sacrifice was my sense of purpose. You may potentially delete a time-based data range from an application, website, or platform, along with everything present in the recall search results.
- A system tray icon provides a visual indication of snapshot-saving activity, allowing for easy identification and rapid pausing of the process as needed.
The Recall controls allow individuals to customize their shopping experience by choosing to retain as much or as little information as desired, thereby maintaining control over their online activity. Notice: Diagnostic information for some Windows features may be available depending on the user’s privacy settings.
Recall structure
The fundamental components of the Recall framework comprise:
Safe Settings
The VBS Enclave’s proprietary Protected Information Retailer safeguards sensitive recall configuration data. Before making any adjustments to sensitive security configurations within the secure environment, users must explicitly approve and authenticate all changes to prevent unauthorized or malicious manipulation. While settings are secure by design and automatically default to a safe state in the event of any detected tampering.
Semantic Index
The semantic index transforms visual and textual data into dimensional representations for efficient querying. The vectors in question potentially point to personally identifiable information gleaned from snapshots, which are then safeguarded through encryption facilitated by keys securely stored within the VBS Enclave’s confines. The VBS Enclave performs all question-related operations internally.
Snapshot Retailer
The dataset consists of preserved screenshots, accompanied by relevant metadata, including URI links provided by applications that integrate with the Recall Consumer Exercise Application Programming Interface (API), as well as additional details such as timestamp, title bar text, application dwell times, and other pertinent information. Snapshots are encrypted using unique person-specific keys, which themselves are safeguarded within the secure confines of the Virtualized-Based Services (VBS) Enclave.
Recall Consumer Expertise
Customers leverage the UI expertise to resolve issues they’ve encountered on their PC, featuring a comprehensive timeline, advanced search capabilities, and seamless snapshot viewing.
Snapshot Service
The background course of this process allows for runtime optimization when creating new snapshots, while also streamlining queries and efficiently processing information provided by the VBS Enclave.
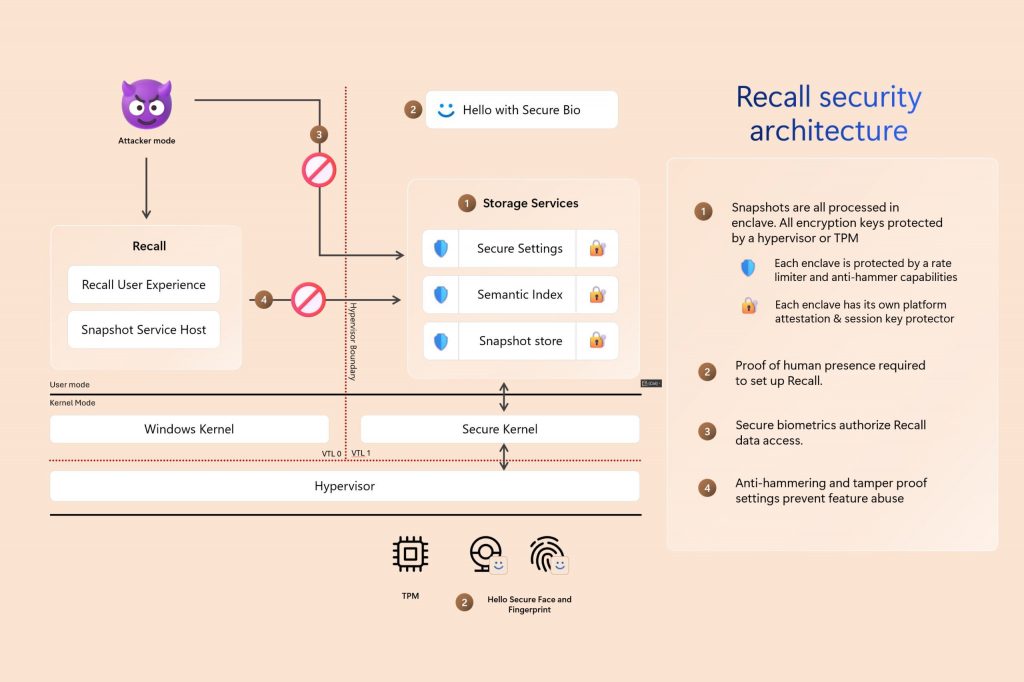
Recall’s storage providers are housed within a secure Virtualized-Based System (VBS) Enclave, safeguarding sensitive data, encryption keys, and ensuring protection against malicious software and potential attacks on the machine. Elements recalled from outside the VBS Enclaves and deemed untrusted on this system.
To safeguard data integrity, the Snapshot Service is engineered to promptly deliver user-requested information while implementing measures to curtail unauthorized knowledge extractions beyond the standard Recall system functionality.
Processes operating outside of VBS Enclaves never instantaneously gain access to snapshots or encryption keys, and instead only receive information returned from the enclave following authorization. The authorization interval features a timeout mechanism and an anti-hammering safeguard to mitigate the impact of malicious query attempts. What snapshot services capture and store data within the confines of the Virtualization-Based Security (VBS) environment, securely preserving sensitive information from external threats. Protected processes are a key technology used to safeguard anti-malware and the Windows Local Security Authority (LSA) host from malicious attacks, thereby ensuring the integrity of the system’s security infrastructure.
The Recall VBS Enclave employs concurrency safeguards and monotonic counter mechanisms to prevent malicious users from overwhelming the system through excessive request submissions.
The recall of structural integrity depends crucially on several architectural features that guarantee safety.
Certain and verified VBS Enclaves
- Encryption keys employed by Recall are irrevocably tied to the identity of the primary individual, securely bound by a key generated from the Trusted Platform Module (TPM) of the hardware platform, and executed exclusively within the trusted confines of Digital Trust Level 1 (DTL1).
-
Virtualization-based security (VBS) primarily relies on the hypervisor to create a secure enclave environment, wherein trusted and verified code is encapsulated within a confidential and isolated Trusted Execution Environment (TEE).
The recall feature operates exclusively on computers equipped with Copilot technology.
Recall exclusively functions on Copilot+-enabled PCs that meet specific criteria and have been validated by Recall’s verification process.
Recall safety opinions
With the design and architecture of Recall incorporating safety, privacy, and accountability considerations for AI, we have also conducted rigorous security audits to ensure the feature’s robustness. These efforts aim to establish a considerate and safe approach:
- The Microsoft Offensive Analysis & Safety Engineering workforce (MORSE) has carried out months of design opinions and penetration testing on the Recall.
- An independent third-party safety vendor was contracted to conduct an objective safety design review and penetration test.
- A Accountable AI Affect Evaluation (RAI) was accomplished, which lined dangers, harms and mitigations evaluation throughout our six RAI ideas (Equity, Reliability & Security, Privateness & Safety, Inclusiveness, Transparency, Accountability). To foster internal awareness and external collaboration, a comprehensive RAI Study and Help documentation was created, effectively driving trust and openness in our client relationships.
Conclusion
Recall’s safe design and implementation presents a robust suite of controls against acknowledged threats. Microsoft is committed to making artificial intelligence accessible to everyone while prioritizing both safety and privacy against even the most sophisticated attacks.
Ensuring safety requires a collaborative effort from every single member of our workforce. Through collaborative efforts with original equipment manufacturers, application developers, and other stakeholders in the ecosystem, we are creating a Windows experience that is inherently designed for security and safely defaults to protecting users. Are there various resources out there that can help educate customers on how to stay secure while using Windows, making it easy for them to understand and implement best practices?
To learn more about Microsoft’s safety features and settings, visit our website at [insert URL]. To stay ahead of the curve and ensure your safety, bookmark our expert insights on the latest security concerns. Comply with us on LinkedIn () and X (X) for the latest information and updates on cybersecurity.

