
Ransomware operators behind RansomHub are now exploiting vulnerabilities in Bring Your Own Vulnerable Driver (BYOVD) attacks, deploying novel malware to cripple Endpoint Detection and Response (EDR) security software, rendering it ineffective in detecting potential threats.
Researchers at Sophos identified the malicious software, dubbed EDRKillShifter, during a May 2024 ransomware investigation, which employs a legitimate, yet vulnerable driver on targeted devices to elevate privileges, disable security features, and seize control of the system.
This sophisticated system has the potential to appeal to a wide range of malicious actors, including those driven by financial motives and others.
“During the recent attack in Could, threat actors, believed to be using this malware, attempted to exploit EDRKillShifter to shut down Sophos security on targeted machines, but the effort ultimately failed,” said Andreas Klopsch, a Sophos threat researcher.
When the attackers attempted to execute the ransomware file on the system under their control, the CryptoGuard feature within the endpoint agent successfully blocked the malicious activity.
Researchers at Sophos discovered two distinct malware variants, both accompanied by publicly available proof-of-concept exploit code on GitHub; the first exploits a vulnerable driver dubbed _, while the second targets _, a component from an outdated system monitoring package.
Sophos has found that EDRKillShifter can deliver multiple driver payloads tailored to an attacker’s specific requirements, and its language settings suggest it was built on a computer with Russian localization.
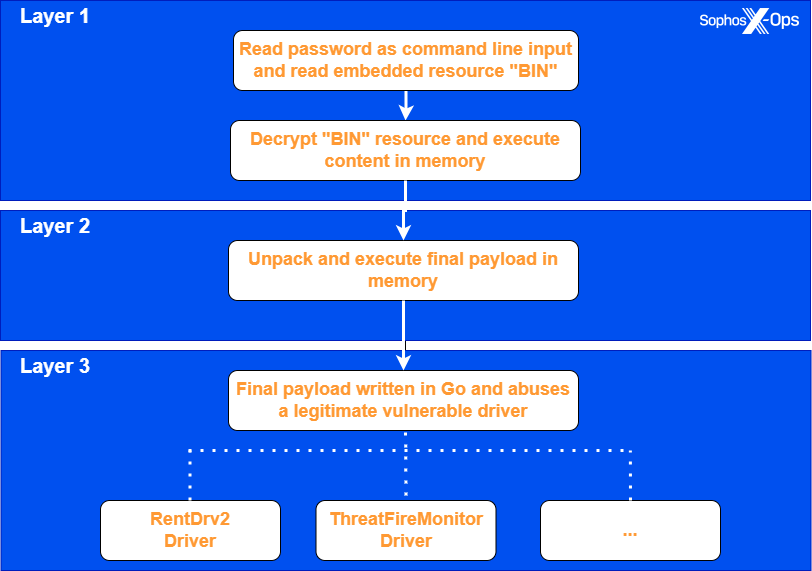
Upon receipt of the password string, the attacker’s loader executes a decryption process to unlock and deploy the embedded Binary (BIN) resource into memory, thereby initiating its execution. The code subsequently decompresses and executes the primary payload, which injects and leverages a genuine driver vulnerability to gain elevated privileges and terminate active endpoint detection and response processes and mechanisms.
“After infecting the system by creating a fresh service for the malicious driver, starting the service, and loading the driver, the malware initiates an endless cycle that methodically scans the running processes, terminating any process whose name matches a predetermined list of targeted applications.”
Notably, these vulnerabilities leverage legitimate drivers with known weaknesses, employing proof-of-concept exploits readily available on the GitHub platform. It appears that threat actors are believed to have taken fragments of proof-of-concept code, adapted them, and then transplanted the programming into the Go language.
To mitigate potential attacks, Sophos advises configuring tamper-evidence settings in endpoint security products, implementing a separation of duties between user and administrator privileges to prevent malicious actors from installing vulnerable drivers, and maintaining software updates to ensure compatibility with Microsoft’s regular de-certification of signed drivers known to have been exploited in previous incidents.
Last year, Sophos discovered another EDR-bypassing malware, known as, which exploited a vulnerable Course of Explorer driver in Medusa Locker and LockBit ransomware attacks. AuKill is akin to an open-source software, dubbed, that leverages vulnerabilities in Windows Explorer drivers and has been linked to at least one observed attack by Sophos X-Ops.

