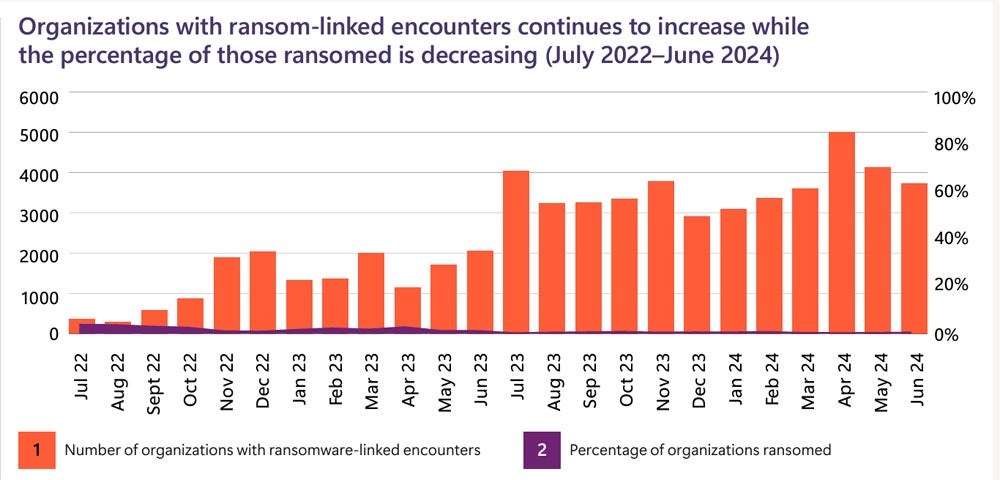
Global ransomware attacks targeting Microsoft customers have skyrocketed over the past year, according to a recent report by Microsoft’s Digital Defense team, published in October. 15. Despite this, advancements in automated attack disruption technologies have resulted in a significant decrease in the number of attacks that successfully breach encryption levels.
Cybercriminals and nation-states perpetrate attacks on Microsoft’s systems daily, highlighting the relentless nature of modern cybersecurity threats. While ransomware attacks have increased by 275%, successful incidents of data encryption and ransom demands have decreased by a significant threefold.
Criminal organisations are exploiting deepfakes and online shopping platforms to launch sophisticated assaults on unsuspecting victims.
Microsoft tracks over 1,500 distinct threat actors, comprising more than 600 nation-state groups, 300 cybercrime organizations, 200 APT teams, and numerous others. The top five ransomware families – Akira, Lockbit, Play, Blackcat, and Basta – collectively accounted for 51% of reported attacks.
Attackers primarily target organisations through social engineering tactics, exploiting identification breaches and publicly accessible vulnerabilities in unpatched systems. Once inside, these individuals usually deploy remote surveillance equipment or compromise security devices. Significantly, 70% of successful attacks were linked to distant encryption, while a staggering 92% targeted unpatched systems.
Types of assault encompassed by law include, but are not limited to:
- Infrastructure assaults.
- Cyber-enabled monetary fraud.
- Cyber attacks on digital payment systems, where online transactions involving credit cards can be conducted without physical proximity.
- Impersonation.
- .
- Account takeover.
- Cyber attacks via identity and social engineering tactics, with a staggering 99% of these incidents being password theft exploits.
- SIM swapping.
- Assistance desk social engineering involves attackers posing as customers to reset passwords or access new systems.
- Credentials, particularly compromised through phishing-as-a-service operations. Typically, these notifications arise from HTML or PDF files with harmful URLs embedded within them.
- DDoS attacks, which have occurred earlier this year?
In the past year, a significant threat emerged: over 176,000 instances of antivirus tampering were detected by Microsoft Defender XDR in 2024, primarily involving unauthorized modifications to security settings.
Global cybercriminals collaborate to evade detection
Financially motivated cybercriminals and nation-state attackers increasingly rely on the same data-stealing tools and command-and-control infrastructure, according to Microsoft’s findings. Unexpectedly, financially driven actors are now exploiting vulnerabilities in cloud services, adopting tactics previously associated with nation-state hackers.
Over the past year, state-sponsored threat actors have increasingly leveraged legal means and methods, while criminals themselves also adapted, erasing the distinction between nation-state-backed malicious activity and cybercriminal tactics.
Microsoft tracks primary risk actor teams from Russia, Iran, and North Korea. Both nations may potentially utilise monetary risk actors as a means of generating revenue, or turn a blind eye to their activities within their territorial boundaries.
According to Tom Burt, Microsoft’s Vice President of Customer Safety and Trust, the ransomware threat underscores the nexus between nation-state activities and financially driven cybercrime. The lack of effective regulation is further compounded by countries that either profit from these schemes or turn a blind eye to cybercrime within their jurisdictions, thereby enabling its proliferation.
As a seasoned expert in national security and cybersecurity, Evan Dornbush shares his insights on this pressing issue:
According to a Microsoft report, a significant pattern has been overlooked and is more likely to outline the way forward for cyber security: the amount of money criminals can earn, said an industry expert in an email to TechRepublic. “Per the Microsoft report, authorities, as a sector, only make up 12% of the attackers’ targeting units,” he stated. While the vast majority of those affected operate outside the public sphere.
The sectors that nation-state risk actors primarily targeted over the past 12 months were:
- IT.
- Schooling .
- Authorities.
- Assume tanks and NGOs.
- Transportation.
As the battlefields of tomorrow unfold, cyber warfare will take center stage. With generative AI on both sides, attackers and defenders alike will wield unparalleled power to shape the digital landscape.
Introduces a fresh array of inquiries. Microsoft advises restricting access to sensitive data for generative AI applications and ensuring the implementation of robust information governance policies to govern their utilization. Artificial intelligence’s transformative influence on cybersecurity is multifaceted and far-reaching.
- As cyber warfare evolves, both attackers and defenders increasingly leverage Artificial Intelligence instruments to gain a strategic edge.
- Nation-state actors can now utilize artificial intelligence to create convincingly false audio and video content, posing significant risks to global stability and international relations?
- Artificial intelligence-powered spear phishing attacks, relentless résumé flooding efforts, and sophisticated deepfake manipulations are currently prevalent.
- Traditional methods for managing global impact initiatives may prove ineffective.
- Artificial intelligence (AI) insurance policies and rules can effectively mitigate some of the dangers associated with the use of AI systems.
- While governments broadly concur on the imperative need for ensuring safety as a critical aspect of artificial intelligence development, they differ significantly in their approaches to achieve this goal.
“The stark reality is that the sheer volume of assaults necessitates a reduction via effective deterrence,” Burt explained, “while industry should take proactive steps to undermine attackers’ efforts by bolstering cybersecurity, this must be complemented with government action to impose penalties that more substantially discourage the most egregious cyberattacks.”
Organizations can proactively counter frequent cyberattacks by implementing a multi-layered approach that combines robust security measures with employee awareness and training.
Microsoft’s report outlines concrete steps that organizations can take to proactively prevent specific types of attacks. By analyzing trends across various industries, TechRepublic has uncovered key takeaways with far-reaching implications.
- Prevent attacks on the methodology layer by enacting measures such as implementing policies for multi-factor authentication and reducing attack surfaces?
- Consequently, configure systems to adopt “secure-by-default” settings, thereby mandating the use of multi-factor authentication for added security.
- Use sturdy password safety.
- Verify preconfigured safety settings, akin to default safety options or managed conditional entry insurance policies, in report-only mode to gauge their potential impact prior to deployment.
- Classify and securely label sensitive data to prevent unauthorized access, and implement robust Data Loss Prevention (DLP) measures to surround high-risk information and high-risk customers with a multi-layered defense. This includes developing an Information Lifecycle Management strategy to ensure the secure handling of confidential data throughout its entire existence, as well as Conditional Entry insurance policies to mitigate potential risks associated with sensitive customer profiles?
Microsoft implemented additional security measures last year following a Chinese-language based intrusion into its email accounts in July 2023.

