Vulnerabilities abound as never before. The industry has seen a staggering 200% surge in the identification and exploitation of vulnerabilities in 2023. During the initial seven months of 2024, stock prices surged by a notable one percent compared to the preceding 12-month period. Currently, no Marvel-themed vulnerability management tools have become a standard fixture in the corporate cybersecurity toolkit.
According to Michelle Abraham, research director for security and trust at IDC, “Vulnerability management is a cornerstone of cybersecurity.” “Organizations remain perpetually vulnerable when they fail to detect and respond to security incidents, as even if a vulnerability is temporarily fixed, malicious actors retain the knowledge and skills gained from exploiting it.”
Prime vulnerability administration instruments comparability
Several vulnerability management tools share similar features. Upon closer examination, I discovered each one has its unique focal point or approach. While some professionals are uniquely specialized in their fields, I contrasted them primarily based on value, as well as four key factors:
- Cloud, on-prem, or each.
- As a comprehensive component within a robust cybersecurity ecosystem.
- Automated discovery.
- Automated remediation.
While attempting to make an apples-to-apples comparison based on value is impossible due to disparate valuation methods among distributors and a lack of transparency regarding pricing, it remains crucial to consider this limitation when analyzing the market.
| Beginning worth | Cloud or on-prem | Cybersecurity suite options | Automated discovery | Automated remediation | |
|---|---|---|---|---|---|
| Approximately $333 per month to manage a portfolio of 100 properties. | Cloud-based. Tenable’s on-premise suite, dubbed Tenable Safety Middle, focuses on vulnerability management. | Information security management, internet service scanning, cloud safety, identity disclosure, operational knowledge safety, network floor management, and risk assessment. | Sure | Sure | |
| Here is the rewritten text: The ESET Defend bundle, featuring ESET Vulnerability and Patch Administration, offers a comprehensive protection solution for $275, covering five devices over a period of 12 months. | Cloud-based. A dedicated on-premise suite provides vulnerability management capabilities. | EDR, server safety, cellular risk protection, encryption, risk protection, cloud safety, vulnerability & patch administration, MFA, and MDR | Some automated discovery tools have limitations in scope, falling short of the comprehensive capabilities found elsewhere. | Some auto-remediation capabilities are included | |
| $9 per gadget monthly or $96 per month for up to 10 gadgets | Two distinct architectures: Cloud-Optimized Infrastructure (COI) for cloud deployment and On-Premises Architecture (OPA) for in-house setup. | What’s the significance of zero trust? | Sure | Sure | |
| For a comprehensive package, you’ll pay approximately $184 every 12 months, while Publicity Administration costs around $40 annually. | Cloud-based | Cybersecurity Solutions: Enhanced Detection and Response, Antivirus Protection, Risk Intelligence Gathering, Public Sector Cybersecurity, Artificial Intelligence-Driven Threat Hunting, Cloud Security Services, Security Information and Event Management, Knowledge Security and Automation. | Sure | Sure | |
| We offer a small business plan for $295 every 12 months, as well as an enterprise model priced at approximately $2,000. | Offering a cloud-based solution with the option to deploy on-premise models. | Asset administration, vulnerability & configuration administration, danger remediation, risk detection & response, EDR, cloud safety, and compliance. | Sure | Sure | |
| For a 500-asset license, we offer $2 monthly per asset, or $6 monthly total. | Cloud and on-prem | Cybersecurity solutions, Extended Detection and Response (XDR), Public Relations Administration, and Incident Floor Management. | Sure | Sure | |
| $4 monthly per person. | Cloud or on-prem | What emerging technologies for endpoint management include: discovery, IT automation, real-time perception, endpoint administration, community and endpoint security, supply chain, and repair and asset administration. | Sure | Sure | |
| For just $200 per month, you’ll have access to up to 50 powerful marketing strategies. | Cloud | No | Sure | Restricted |
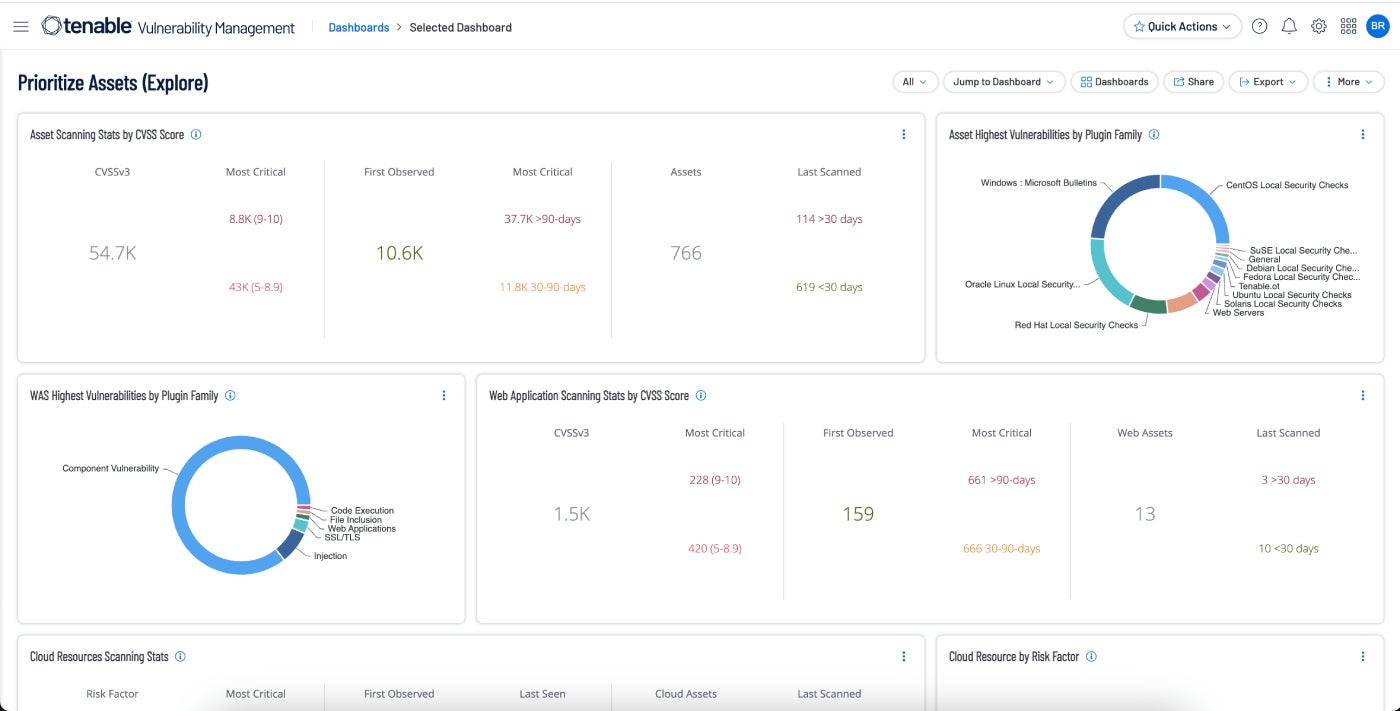
Tenable Vulnerability Administration: Greatest total

Tenable’s Vulnerability Management approach takes a data-driven, risk-based methodology for effective vulnerability administration. The initiative prioritizes community visibility, aiming to forecast potential assaults and rapidly respond when critical vulnerabilities arise. A is accessible.
Why I selected Tenable
I selected Tenable as one of the top total vulnerability management tools for numerous reasons. As the market leader in vulnerability management tools, it holds a commanding 25% market share. This product boasts an impressive array of choices, thoroughly satisfying most users’ requirements. The solution seamlessly integrates with numerous platforms and security tools, streamlining workflow automation and minimizing the number of sources required to safeguard the business.
Pricing
- Tenable’s pricing averages approximately $4,000 annually for a portfolio of 100 properties.
Options
- The Tenable Neighborhood thrives with a vibrant atmosphere, where numerous enthusiastic patrons are eager to assist in resolving any concerns.
- Scanning of on-premise methodologies, digital devices, cloud-based systems, and mobile technologies is performed with equal enthusiasm and passivity.
- Cloud Connectors provide real-time visibility and monitoring into public cloud environments such as Microsoft Azure, Google Cloud Platform, and Amazon Web Services.
- Embedded prioritization, advanced risk intelligence, and instant reporting capabilities empower customers to anticipate threats and preemptively impede malicious activity.
Professionals and cons
| Professionals | Cons |
|---|---|
| Seamlessly integrated within the comprehensive Tenable One ecosystem. | Some customers have reported that assistance could potentially be enhanced. |
| Steady, always-on discovery and evaluation | Actual-time scanning and overall scanning speed can be significantly improved. |
| Menace intelligence | Far from being the cheapest option, this solution falls short in terms of value for money. |
| Automated vulnerability prioritization. | The project requires a strong foundation in programming languages such as Java and Python. |
| Real-time visualizations of potential dangers, coupled with the continuous monitoring of vulnerabilities, assets, and remediation efforts. | |
| Establishing Danger: Vulnerability Scores |
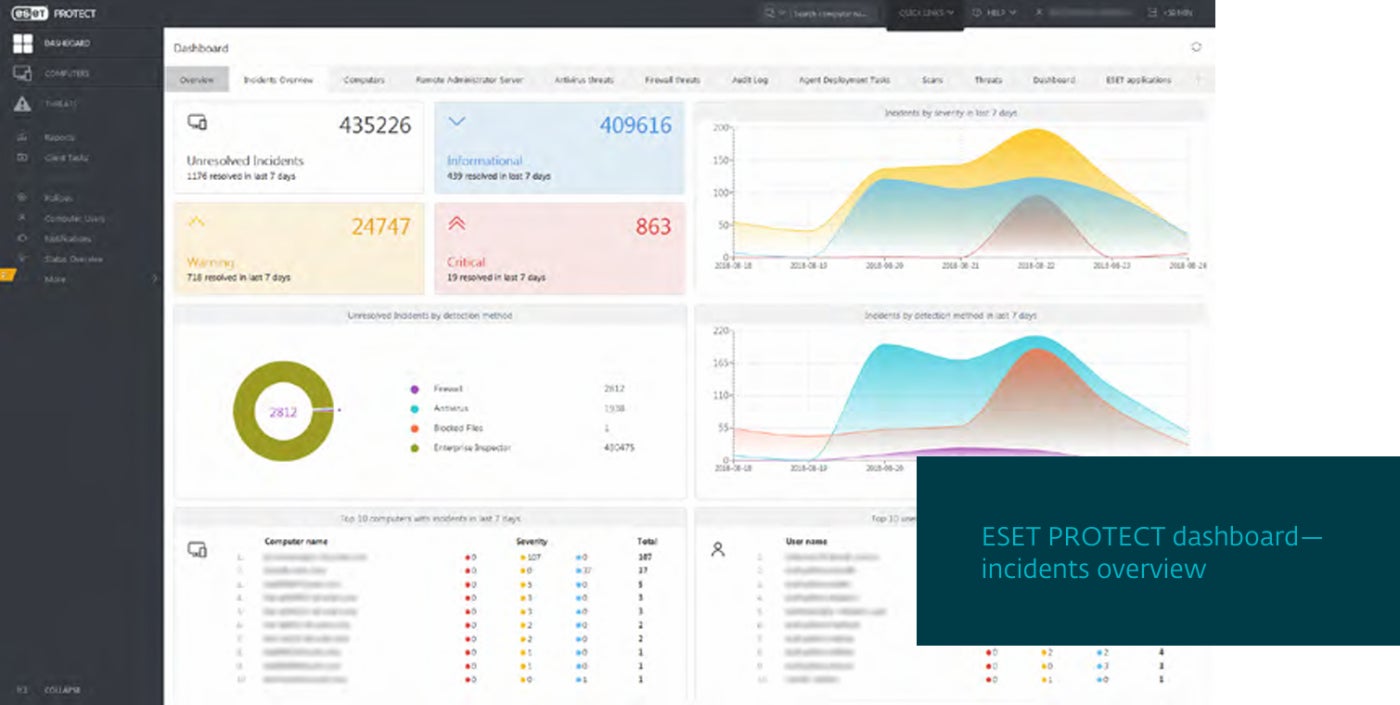
ESET’s Comprehensive Vulnerability and Patch Management Solution: The Ideal Choice for Small to Medium-Sized Enterprises

ESET’s vulnerability and patch administration capabilities enable the routine scanning of hundreds of functions for numerous thousands of prevalent vulnerabilities and exposures. The system can prioritise and filter identified vulnerabilities based on their publicly disclosed rating and severity level.
By leveraging ESET’s Vulnerability and Patch Administration solution, I aimed to streamline our IT infrastructure’s security posture while minimizing the administrative burden on my team. With this tool, we can quickly identify vulnerabilities, prioritize patching efforts, and ensure compliance with regulatory requirements. The solution’s intuitive interface and real-time threat intelligence enable us to make data-driven decisions and respond rapidly to emerging threats.
I was impressed by how effortless it was to install and activate ESET, with a seamless user experience that streamlined the process. This offers a compelling solution for subject matter experts (SMEs) and larger entities struggling to access reliable IT and cybersecurity resources.
Pricing
- For $275, customers receive a 12-month subscription to the ESET Defend bundle, which includes ESET’s innovative Vulnerability and Patch Administration capabilities, providing comprehensive protection for five devices.
Options
- Supports a wide range of operating systems, including multiple versions of Windows, Linux, and macOS.
- Detects over 35,000 CVEs.
- Regularized automated scans with user-defined scheduling options.
- Identifies and categorizes vulnerabilities according to their publicity ranking and severity level for streamlined mitigation efforts.
Professionals and cons
| Professionals | Cons |
|---|---|
| Simplifying patching processes involves prioritizing critical properties and scheduling non-essential updates during off-peak periods. | Automated discovery and remediation capabilities fall short in their scope compared to other available alternatives. |
| Protecting against emerging cyber risks: safeguarding against ransomware and zero-day attacks. | Focused specifically on smaller and mid-sized businesses rather than the corporate market. |
| Effortlessly organized, simple to utilize, and long-lasting. |
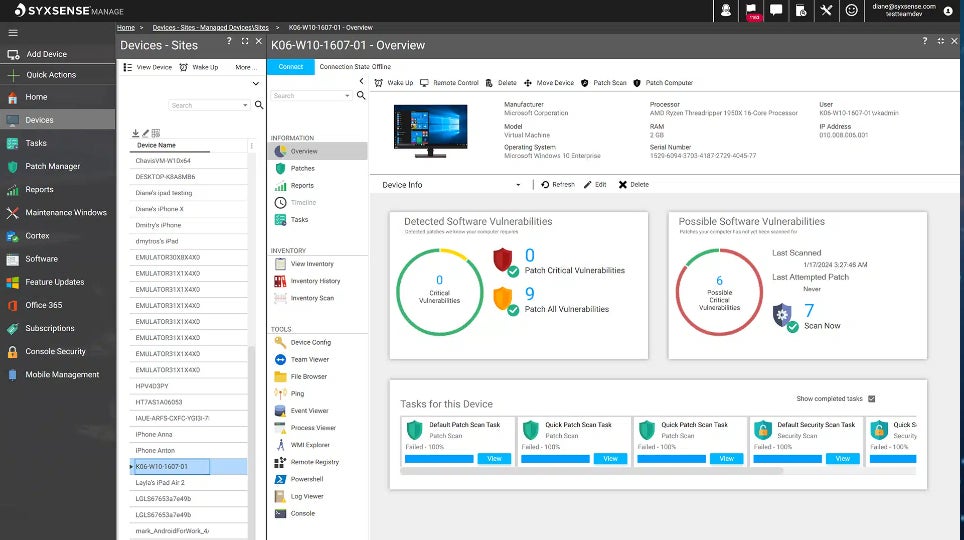
What sets Syxsense Enterprise apart from other patch management solutions is its unparalleled ability to streamline and automate the process of keeping endpoints up-to-date and secure. With Syxsense Enterprise, organizations can confidently rely on a robust platform that prioritizes efficiency and effectiveness in their IT operations.

Syxsense Enterprise integrates patch management, vulnerability scanning, IT administration, and mobile device management within a comprehensive vulnerability management platform. Recently, the system has introduced integrated remediation capabilities alongside its zero-trust approach. The entire inventory is now seamlessly consolidated into a single unified console within the Syxsense Enterprise framework.
Why I selected Syxsense
Originally operating as a patch management expert, Syxsense evolved. Building on that success, the company has consistently grown to become a comprehensive vulnerability management platform. Notwithstanding my observation, the product seemingly lacks a comprehensive suite of safety features characteristic of many other providers in this market. The organization’s cybersecurity posture is currently inadequate, as it lacks essential components such as Security Information and Event Management (SIEM), risk intelligence, and antivirus software. I was pleased with the focused attention on vulnerability management and device control. For organizations already equipped with a safety platform, Syxsense offers a seamless enhancement of patch management and vulnerability administration capabilities.
Pricing
- $9 per gadget monthly or $96 per month for up to 10 gadgets.
Options
- Automated discovery and remediation workflows.
- Patching administration seamlessly integrates patch superseding, rolling back outdated patches, and securing endpoints including cellular devices.
- A Zero Belief Analysis Engine fosters a robust and trustworthy safety stance across endpoint devices.
Professionals and cons
| Professionals | Cons |
|---|---|
| Glorious patch administration performance. | The acquisition of Syxsense by Absolute Software potentially hinders the company’s momentum for sustained innovation, which had previously driven it to leadership in the patch and vulnerability management space. |
| Tightly targeted on vulnerability administration. | The suite is missing crucial components akin to antivirus software, risk assessment tools, and Security Information and Event Management (SIEM) systems. |
| What are the specific security requirements for implementing cloud-based infrastructure? The main concern with cloud-based infrastructure is securing data at rest and in transit. This requires implementing robust encryption protocols to ensure that sensitive information remains confidential. |
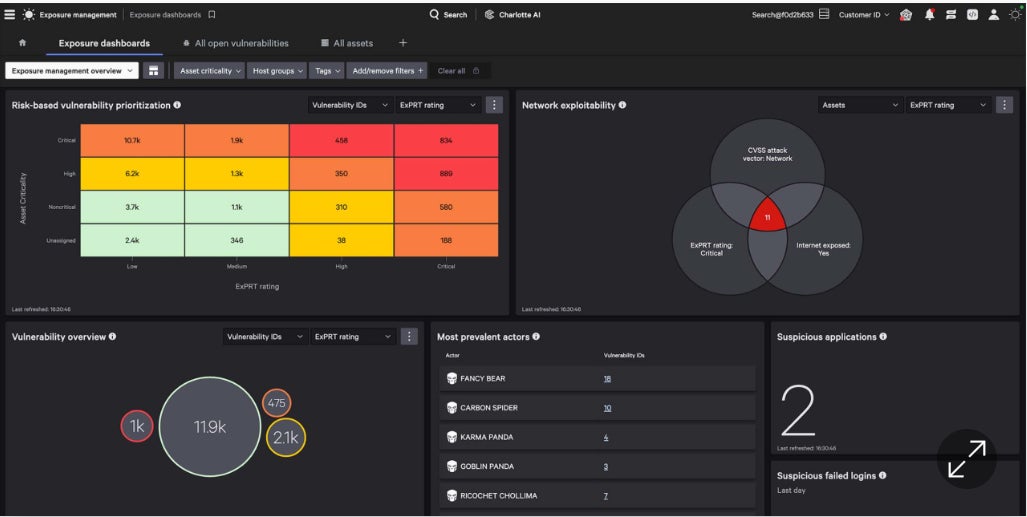
CrowdStrike’s Public Sector Solutions: Comprehensive Cybersecurity Suite for Proactive Vulnerability Management

Originally based on the mature Falcon Spotlight product, CrowdStrike’s Publicity Administration leveraged my existing knowledge and expertise. Here is the rewritten text:
This innovative enhancement significantly expands the capabilities of Falcon Highlight, incorporating an additional risk management strategy and leveraging AI-based technologies to further elevate its performance.
I chose to work with CrowdStrike’s Public Relations department because of their exceptional expertise in cybersecurity and threat intelligence. With years of experience under their belt, they possess a deep understanding of the complexities surrounding digital security, making them an invaluable asset for any organization seeking guidance on how to protect itself from potential cyber threats.
The CrowdStrike public administration is a stable entity within its own right. One component of a comprehensive system featuring a diverse array of safety mechanisms. Patrons are more likely to purchase the entire CrowdStrike platform rather than just the Public Relations Management module. The CrowdStrike Falcon Platform is a comprehensive suite of security tools that combines Endpoint Detection and Response (EDR), antivirus, risk intelligence, public sector management, artificial intelligence, cloud security, Security Information and Event Management (SIEM), knowledge security, automation, and more into a single, integrated agent. For organizations seeking a comprehensive vulnerability management solution and a robust security suite, adopting the entire Falcon Platform is an excellent decision that won’t lead to regret.
Pricing
- For a comprehensive suite, you can expect to pay approximately $184 per 12-month period, while the publicity administration module is available for around $40 per 12 months.
Options
- Vulnerability assessments are conducted using automated tools to identify potential security weaknesses, regardless of whether they are within or outside the community.
- Enhancing response times through real-time insights into emerging vulnerabilities and threats.
- The ability to discern and forecast which vulnerabilities pose the greatest potential risk to the organization?
- The corporation features a unified, lightweight architecture that streamlines its operations.
Professionals and cons
| Professionals | Cons |
|---|---|
| Vulnerability and patching orchestration. | Limited capabilities in detecting misconfigurations of safety-critical features. |
| Integration throughout the CrowdStrike Falcon. | Focus intensely on the entirety of suites rather than just vulnerability management. |
| Artificial intelligence seamlessly integrates risk intelligence with real-time vulnerability assessments to provide a comprehensive security solution. | |
| A unified module controller. |
Qualys VMDR: A Top Choice for Cloud-Committed Organizations

Qualys Vulnerability Management solution detects and responds to threats by taking a comprehensive approach that prioritizes and remediates critical vulnerabilities promptly, leveraging real-time threat intelligence and contextual insights to inform mitigation decisions. I valued the significance of its proprietary automated scoring system, dubbed TruRisk.
Why I selected Qualys VMDR
Qualys VMDR seamlessly consolidates a suite of critical security features, encompassing vulnerability assessment, asset discovery, inventory management, and attack surface management. This innovative, cloud-based suite of safety solutions is comprised of two distinct modules. Given its scalability and robust features, I believe this solution would be an excellent choice for large-scale organizations leveraging the cloud infrastructure.
Pricing
- I was initially underwhelmed by Qualys’s pricing structure, which seemed overly complex and difficult to navigate. Primarily rooted in the realm of cloud computing, this concept revolves around three primary models: digital machines, serverless architectures, and containerized solutions. The value of each unit primarily fluctuates in response to differences in its performance, complexity, and overall value proposition. The enterprise pricing model for our entire suite starts at around $500 per month, scaling upward according to the number of users. The vulnerability administration module is reportedly available to small businesses starting at $250 annually and $2,000 for enterprises.
Options
- While primarily cloud-based, a dedicated on-premise personal cloud solution is available for customers requiring stringent data sovereignty controls.
- A cloud-based service catering primarily to small-to-medium-sized enterprises (SMEs) offers a suite of security tools, including vulnerability management, detection, and response (VMDR), as well as endpoint detection and response capabilities, and automated patch administration instruments.
- Threats to an organization’s security are a constant concern, and developing effective countermeasures requires a nuanced understanding of the risks involved. By employing a combination of danger-based and context-based prioritization techniques, organizations can better identify and mitigate potential threats.
Danger-based prioritization involves evaluating the severity of potential threats based on factors such as their likelihood and potential impact. This approach helps organizations focus on the most critical threats that could cause significant harm if left unchecked.
- Simplified integration with patch administration, stock control, and IT service management processes.
- The Qualys Menace Analysis Unit proactively identifies novel threats by synthesizing insights from its global user community, multiple threat intelligence sources, third-party data, and the dark web.
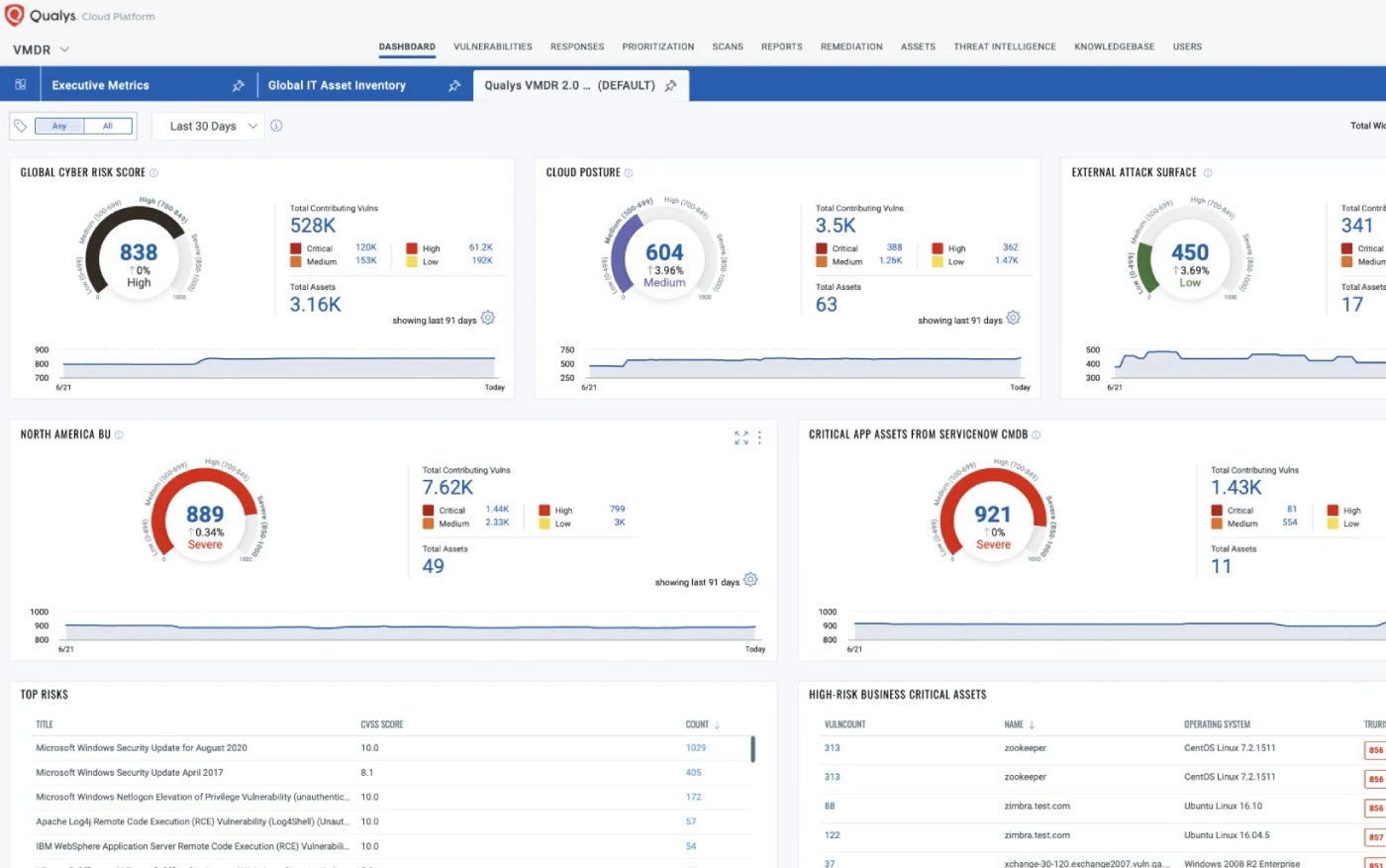
Professionals and cons
| Professionals | Cons |
|---|---|
| Comprehensive range of vulnerability signature databases. | It may be challenging to integrate this technology into the daily operations of younger IT professionals. |
| Real-time vulnerability detection, akin to patching and configuration rectification. | Cloud and hypervisor help may be significantly improved. |
| Automatically identifies and applies the latest available update to vulnerable systems. | |
| As a prominent market leader in vulnerability management, Qualys boasts a significant share of the market. |
Options
- Continuously evaluates and ranks critical vulnerabilities based on risk assessments ranging from 1 to 1000.
- The organization diligently monitors compliance with industry regulations, insurance coverage standards, and relevant laws, juxtaposing its performance against established trade benchmarks.
- Rapid7 Labs enables organisations to detect and respond to internet-facing assets, promptly alerting them to potential vulnerabilities.
- Robust scanning capabilities coupled with a diverse range of devices.
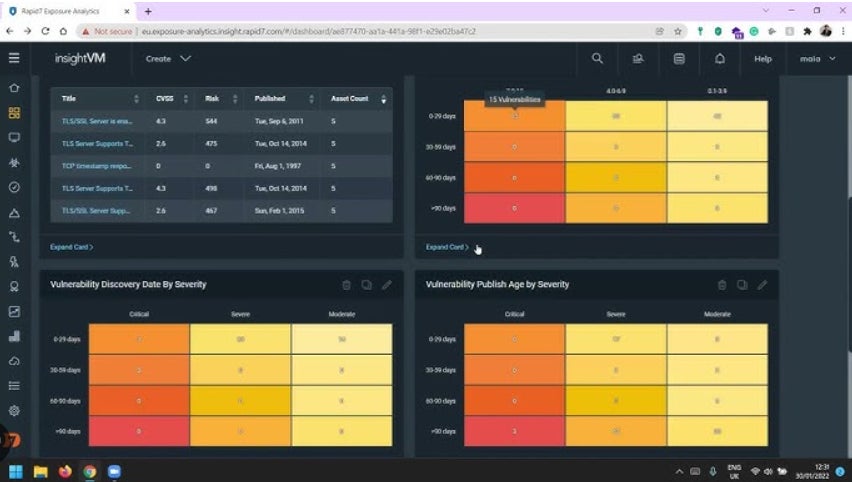
Professionals and cons
| Professionals | Cons |
|---|---|
| Automated remediation. | Designed specifically for well-educated safety teams. |
| Computerized pen-testing. | Proper arrangements can often prove challenging to coordinate. |
| A leading vulnerability management solution provider with significant market share. | Customers are cognizant of integration and deployment touchpoints. |
| Conducts thorough vulnerability scans across a comprehensive scope of cloud, on-premises, and digital infrastructure, while continuously gathering intelligence from every endpoint. | Responsiveness may indeed be significantly enhanced. |
| Vulnerability patching and containment efforts can be greatly enhanced by implementing safety groups that facilitate streamlined remediation actions. | |
| Seamlessly integrates with a diverse range of third-party tools, including ticketing systems, patch management solutions, and Security Information and Event Management (SIEM) platforms. |
What makes Ivanti VMaaS stand out from the rest? Its cloud-based virtual machine (VM) management capabilities are unparalleled.

Ivanti boasts a rich and extensive heritage as a leading provider of high-vulnerability management solutions. The solution offers deployable tools that can be utilized across the organization or as a service.
Why I selected Ivanti VMaaS
Ivanti’s VMaaS solution uniquely combines vulnerability management as-a-service with expert security analysis, scanning tools, and proven processes to help organizations identify vulnerabilities on their networks and within applications. Additionally, the firm offers advanced cloud-based tools like Ivanti Neurons, enabling organizations to proactively manage risk-based vulnerabilities with precision.
Pricing
Options
- Ivanti Neurons for Risk-Based Vulnerability Management (RBVM) can ingest knowledge from multiple third-party scanners to fill gaps and eliminate blind spots.
- It continuously consolidates insights from vulnerability scans and provides valuable information to IT and security teams.
- Findings from scans are consistently correlated and contextualized against a backdrop of risk knowledge and thorough evaluations, driving informed priorities.
- Identifies vulnerabilities in software development, pinpointing specific coding mistakes to optimize performance and ensure reliability.
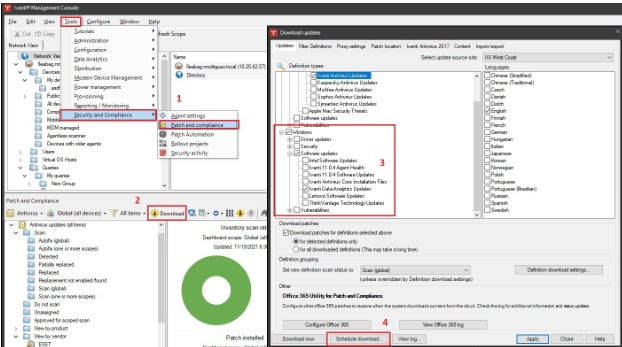
Professionals and cons
| Professionals | Cons |
|---|---|
| With this comprehensive managed service, staff are liberated to focus on innovative projects. | Customers express frustration with insufficient assistance. |
| Straightforward-to-follow remediation plans. | Customization choices are restricted. |
| Effective danger scoring enables targeted remediation recommendations by focusing on the most pressing risks. | Thorough patch administration tools can additionally identify every endpoint functioning on the network with greater precision. |
| Automated workflows. |
StorageGuard: A Leading Solution for Reliable Storage and Backup Capabilities

The StorageGuard solution from Continuity Software proactively identifies, remediates, and prevents safety misconfigurations and vulnerabilities across hundreds of storage, backup, and data protection systems.
Why I selected StorageGuard
While many instruments in this space provide comprehensive security features, encompassing vulnerability management or forming part of extensive security suites that extend far beyond vulnerability assessment capabilities. Given the constraints we chose StorageGuard because it employs an alternative approach. With an unyielding emphasis on a specific aspect of the market, our solution zeroes in on a glaring weakness prevalent across many vulnerability management products – storage and backup vulnerabilities and misconfigurations. By seamlessly filling a specific gap in functionality, StorageGuard is an excellent choice for pairing with other tools on this list.
Pricing
- $200 per month for up to 50 proven methods.
Options
- Straight addressing the vulnerabilities and potential threats identified by NIST in its guidelines.
- Effective safeguards for data storage and backup solutions from leading providers including Dell, NetApp, Hitachi Vantara, Pure Storage, Rubrik, Commvault, Veritas, Hewlett Packard Enterprise, Brocade Communications Systems, Cisco Systems, Veeam Software, Cohesity DataSystems, International Business Machines, Infinidat, VMware, Amazon Web Services, and Microsoft Azure.
- Ability to identify discrepancies from a predetermined reference model.
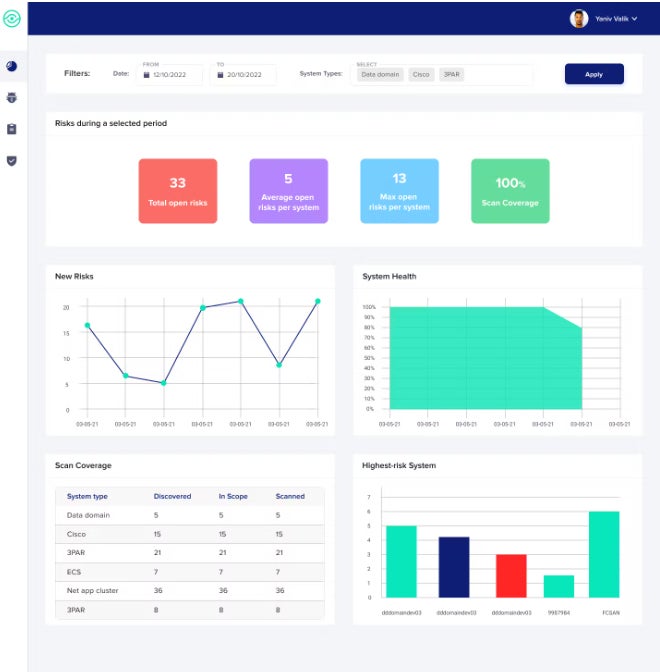
Professionals and cons
| Professionals | Cons |
|---|---|
| Identifies vulnerabilities in data storage and backup systems that other scanning tools may overlook, providing a more comprehensive assessment of potential security threats. | Fails to address traditional weaknesses in external libraries and operating systems. |
| Customers frequently comment on the intuitive nature of our solution’s usability, as well as its comprehensiveness in identifying and rectifying backup and storage misconfigurations. | Focused on distinguishing between exploration of key findings and making definitive choices. |
| Ensures seamless demonstration of audit conformity across various frameworks, including CIS Controls, NIST, ISO, PCI, and NERC CIP standards, thereby guaranteeing regulatory excellence. |
Vulnerability administration: Incessantly requested questions
What are vulnerability administration instruments?
Vulnerability management is a critical capability that detects and catalogues identified vulnerabilities, specifically Common Vulnerabilities and Exposures (CVEs), in devices potentially exploitable by attackers to gain unauthorized access and leverage those compromised systems for further network infiltration.
To further counteract potential vulnerabilities stemming from configurable or codified settings, the scope of this term typically expands to encompass not only mitigating configuration or code points but also patch management, Mobile Device Management (MDM), Information Technology asset administration, and Endpoint Detection and Response (EDR). Vulnerability administration is typically integrated within a comprehensive security suite.
Vulnerability administration instruments orchestrate comprehensive security assessments by scanning networks, systems, and applications to identify and categorize weaknesses. These tools leverage various techniques, including network mapping, port scans, and exploitation attempts, to pinpoint potential entry points for attackers. Once vulnerabilities are detected, the instruments provide detailed information on their severity, remediation steps, and suggested mitigations, empowering administrators to prioritize and address threats effectively.
Vulnerability administration can be broken down into a series of manageable steps, many of which can be seamlessly automated.
- Vulnerability scanning.
- Identifying and reporting vulnerabilities discovered, prioritized according to their potential impact on the organization’s overall security posture.
- What are the critical steps to rectify the situation and prevent future occurrences? A comprehensive plan must be devised to address the root causes of the issue, encompassing both short-term and long-term solutions.
- Verification of implemented solutions to ensure that identified issues are effectively addressed and no longer persisting.
- Vulnerability Reporting: A Comprehensive Overview of Enterprise Risk Assessment?
Vulnerability administration instruments are typically deployed via automated scripts, utilizing APIs and software development kits (SDKs), allowing for seamless integration with existing IT infrastructure. These tools often employ a push or pull methodology to distribute updates, ensuring timely patching and minimizing downtime. Additionally, some vulnerability management solutions offer cloud-based deployment options, simplifying the process for organizations with distributed environments.
They may be deployed as on-premises software programs, offered as Software-as-a-Service (SaaS), or provided as managed services.
Vulnerability administration as a service enables organizations to outsource their vulnerability management and remediation processes, providing ongoing monitoring, assessment, and resolution of vulnerabilities across their IT infrastructure.
Vulnerability management as a managed service is typically provided by a vendor via the cloud, rather than requiring customers to download and operate on-premise software. It relentlessly scans, evaluates, encounters, and governs vulnerabilities across cloud identities, workloads, platform settings, and infrastructure at all times.
When evaluating a high-vulnerability management tool, consider searching for features like real-time threat intelligence, automatic vulnerability detection, and prioritized remediation guidance.
Core capabilities are consistently found in all high-vulnerability management platforms. These embrace:
- Ongoing discovery of every gadget, function, and method, as well as identification of potential vulnerabilities and misconfigurations, is crucial for ensuring security across the entire network, regardless of the device or its connection status.
- A comprehensive database of vulnerabilities and threats that remains perpetually current.
- Effective integration with an array of platforms, leveraging cutting-edge safety protocols, advanced vulnerability scanning capabilities, streamlined ticketing systems, and diverse safety instrumentation.
- A methodology for assessing and ranking risks:
- Computerized remediation or remediation steering.
- Enhanced reporting capabilities that shine a light on key performance indicators and ensure seamless compliance with regulations.
Which vulnerability management solution should you choose for your organisation?
In pursuit of a vulnerability management tool, one should inquire about such things as:
- The device seamlessly integrates with a range of popular platforms, including iOS and Android, as well as Windows and macOS operating systems. Some software is designed specifically for Linux, others for Windows, and a few cover multiple or all operating systems and platforms? Please provide the text you’d like me to improve, and I’ll do my best to revise it in a different style while considering that workers are already educated on certain topics. Avoid introducing Linux tools when working with internally trained staff who specialize in Windows, and similarly refrain from incorporating Windows-specific tools when working with Linux-trained professionals.
- What endpoints are lined? Some deals focus on servers, PCs, and laptops, while others extend to cover smartphones, IoT devices, Wi-Fi, and other various gadgets.
- To enhance security posture by augmenting existing risk management processes, I would like to incorporate and refine elements such as threat intelligence feeds, incident response protocols, employee training programs, cybersecurity governance frameworks, and continuous monitoring tools. When undertaking a comprehensive revamp of your overall safety framework, start by selecting a suite that offers robust vulnerability management capabilities and then customize it to meet your specific needs. When you’ve established a solid safety foundation, focus on vulnerability management tools that provide the level of protection you require.
- Carefully examine the striking visual appeal, scrutinize the subtle nuances in shading, and pay close attention to the potential for additional fees, pricing structures, and related considerations.
- Diversify your reliance to avoid being held hostage by a single provider’s limitations. While Vendor A might align with your safety infrastructure needs, Vendor B could actually excel in vulnerability management.
- The landscape of musical instruments is a vast expanse of creativity, with various types catering to diverse artistic expressions. As we delve into the world of instruments, it’s crucial to recognize their unique strengths, weaknesses, and market shares.
Regardless of the device chosen from the checklist above, the benefits of vulnerability management become evident through reduced breaches, more effectively safeguarded data, earlier detection of attacks, and increased automation.
Methodology
The instruments we’ve selected are informed by analyst reviews, peer evaluations, and user satisfaction, as well as aggregated ratings from reputable technology recommendation websites like TechRepublic. I also offered a diverse range of vulnerability management products, highly specialized tools, and those where vulnerability management was just one module within a larger software suite.

