The China-based domain administrator has been granted until mid-August 2024 to demonstrate compliance with measures for identifying and suspending malicious domains, including those engaging in phishing activities, failing which it risks losing its license to manage top-level domains. Amidst the release of recent findings, a warning has been issued that “.high” is now the most prevalent suffix in phishing websites, trailing only behind those ending in “.com”.

Picture: Shutterstock.
On July 16, ICANN dispatched a letter to the registrants of the .high domain registry. ICANN has historically pursued numerous enforcement actions against registries and registrars, but in this instance, it took a unique approach by targeting a site responsible for managing an entire top-level domain (TLD).
The missive criticized the registry for its inability to respond to inquiries regarding phishing attacks linked to .high domain names.
According to findings compiled over several weeks, it is evident that .TOP Registry lacks a systematic process for timely, thorough, and impartial consideration and response to studies of DNS abuse.
Although ICANN’s caution concealed the recipient’s identity, records indicate that the .high registry is managed by a Chinese entity called . Corporate representatives have thus far failed to respond to inquiries for comment.
The Phishing Information Exchange (PIE) domains, ending in .high, are currently prominent in their launched state, leveraging phishing intel gathered from multiple sources, including APWG, M3AAWG, and WASC.
According to Interisle’s latest research, a staggering two million phishing attacks were recorded over the past year, with a significant proportion – exceeding 4% – attributed to phishing websites leveraging newly registered .high domains between May 2023 and April 2024? According to Interisle, the .high domain registry currently hosts approximately 2.76 million domains, with a staggering 117,000 of those being identified as phishing websites over the past year alone?
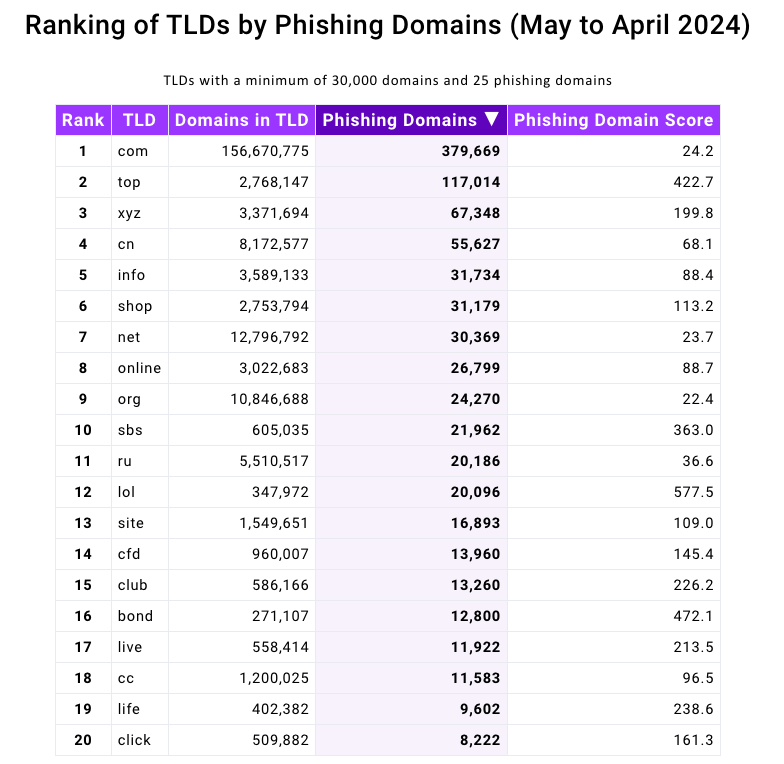
Supply: Interisle Consulting Group.
ICANN evaluated its application for .high domains, primarily based on information gathered and analyzed over the preceding weeks. However the truth that excessive volumes of phishing websites are being registered via Jiangsu Bangning Science & Expertise Co Ltd. The notion that innovation is hardly a brand new concept is hardly a startling revelation.
In excess of a decade ago, the Chinese registrar emerged as the fourth most prevalent source of phishing websites, according to data compiled by the Anti-Phishing Working Group (APWG). Keep in mind that the APWG report excerpted beneath was revealed
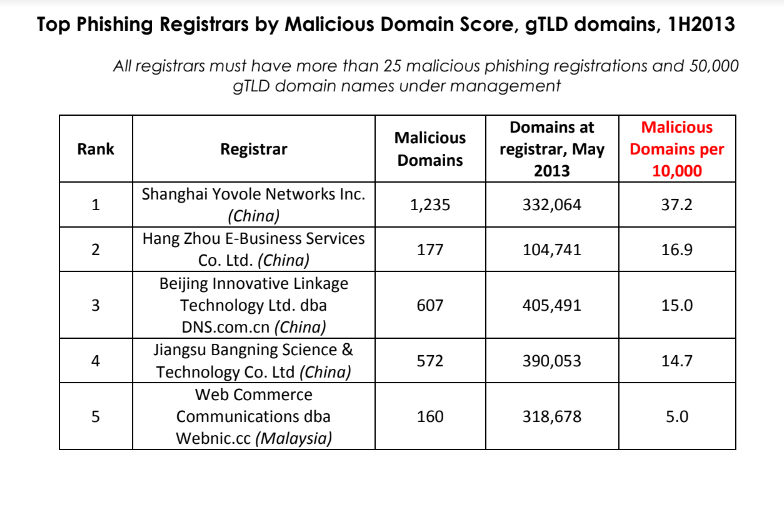
The 2011 APWG Phishing Report.
The IPFS has given rise to an intriguing development in the phishing landscape, as criminals increasingly exploit its decentralized infrastructure to host malicious websites, taking advantage of the network’s anonymity and lack of centralized control. The alarming surge in phony online portals utilizing IPFS as a conduit for launching sophisticated phishing attacks has resulted in a precipitous increase of approximately 1,300 percent, with a staggering 19,000 fraudulent sites detected throughout the past year alone?
According to a report released by Interisle last year, domains concluding with “.us”, the top-level domain reserved specifically for the United States, Although .us domains fell short of the top 20 in this year’s study, the “com” domain retained its longstanding position as the largest source of phishing domains overall?
About a year ago, the most notorious area registrar at the time was a defunct entity that dispensed free domains across several country-code top-level domains (ccTLDs), including .tk, .ml, .ga, and .cf. Following a scandal that led to its downfall, Freenom ceased operations, allegedly ignoring numerous abuse complaints while profiting from advertising revenue generated by malicious websites hosted on its platform.
Phishers soon transitioned to alternative, cost-effective top-level domains (TLDs) and leveraged companies offering anonymous, complimentary domain registration opportunities – specifically subdomain providers. Phishing attacks on websites built using Google’s platform surged more than 230% in the past year, according to Interisle. Several prominent subdomain companies have observed a significant surge in domain registrations linked to phishing schemes, according to recent reports. The companies in question include Xfinity, GoDaddy, and Namecheap.
Supply: Interisle Consulting.
Interisle Consulting suggests ICANN may issue warning letters to at least six top-level domain registries, highlighting that spammers and phishers frequently rotate through the same TLDs, including .gdn, .ml, .ga, and .tk, all of which experienced a significant surge in phishing activity following Freenom’s collapse.
By proactively flagging registrants who seek to register excessive domain volumes, Piscitello suggested that area registrars and registries could significantly curb the proliferation of phishing websites registered through their services. Researchers found that at least 27% of phishing domains were registered en masse, suggesting The registrant simultaneously acquired a large quantity of domain names in rapid succession.
A phishing operation was tracked as it registered 17,562 domains within an eight-hour span, an astonishing rate of approximately 38 domains per minute, with the majority using randomly generated .lol domain names.
ICANN typically attempts to address contract disputes through private negotiations with affected registry and registrar stakeholders, but experts note that the organization frequently only makes public enforcement letters when a recipient fails to respond to prior notifications. ICANN’s letter highlights that Jiangsu Bangning failed to acknowledge receipt of the emailed notifications, leaving their status uncertain. The registry was cited as having fallen behind in paying its ICANN membership fees, with a specific reference to this oversight in the relevant documentation.
According to an evaluation, two prevailing trends emerge: one being the stark decline in public compliance and enforcement actions, even as the number of new top-level domains has surged significantly, whereas…
In most instances, the primary reason for issuing a warning letter to a registry or registrar was their inability to pay the annual ICANN membership fees on time, thereby rendering their continued participation uncertain. Since 2022, an evaluation of around two dozen enforcement letters sent by ICANN to domain registrars has disclosed that non-payment of dues was identified as a primary or contributing factor in at least 75% of cases.
According to Piscitello, a former ICANN vice chairman for safety, nearly every breach notice sent during his tenure was triggered by a registrar’s outstanding debt.
“I think it’s just window dressing for ICANN to claim they’re on top of DNS abuse,” Piscitello said.
KrebsOnSecurity has reached out to ICANN seeking comment, and will update this story if a response is received.
ICANN has stated that most investigations are resolved and closed at the preliminary stage, resulting in a significant number of enforcement circumstances initiated against contracted parties requiring compliance, correction or implementation of remedial measures to prevent future occurrences.
“Before issuing any notice of breach to a registrar or registry operator, ICANN Compliance performs a thorough contractual compliance verification of the relevant contracted party,” ICANN stated in its written response to inquiries. Throughout this verification process, ICANN Compliance proactively evaluates the contracted party’s compliance with obligations outlined in the agreements and policies. Any additional contractual violations detected during these audits will be appended to the Discovery of Breach documentation. It’s not uncommon for registrants failing to adhere to their contractual commitments – regardless of whether these relate to DNS abuse, registry data escrow services, or other issues – to find themselves behind on ICANN fee payments.
Added assertion from ICANN. Elucidated Piscitello’s previous role at ICANN.

