

The design features sleek, aerodynamic lines and vibrant tricolor accents, crafting a swift and agile visual identity. The telephone’s distinctive wallpaper and user interface are inspired by the high-octane world of motorsport, featuring dynamic graphics and racing-themed elements that capture the essence of speed and adrenaline.

The company reiterated its commitment to a long-standing collaboration with BMW Group Designworks, showcasing the perfect blend of adrenaline-fueled design elements and innovative technology expertise.
, renowned for its collaborative effort with high-performance design, successfully propelling the boundaries of speed and athletic flair.
The Note 40 Sequence Racing Edition encompasses the entire Note 40 series, inclusive of the, , , , and styles. On the performance aspect, the device comes with the MediaTek Helio P99 processor, whereas the other is powered by the Qualcomm Snapdragon 888.
The innovative smartphones boast a cutting-edge chip that enables All-Spherical FastCharge 2.0 technology, allowing for up to 100W Multi-Speed FastCharge capabilities and seamless 20W Wireless MagCharge functionality. Does the Infinix MagKit revolutionize charging experiences with its innovative magnetic design?
The cutting-edge smartphone boasts a stunning 3D-curved 120Hz AMOLED display, coupled with a powerful 108MP camera system featuring optical image stabilization, energetic Halo AI-driven lighting, and immersive JBL audio capabilities. The smartphone operates on Infinix XOS 14, which is primarily based on Android 14, allowing it to receive upgrades up to Android 16, alongside a three-year guarantee for security patches.
The NOTE 40 Sequence Racing Version will be available worldwide starting June 6th, 2024, with varying prices and distribution dependent on region. This launch marks a significant partnership aimed at bringing cutting-edge performance and sleek, motorsport-influenced aesthetics to the next generation of tech enthusiasts globally.
Filed in . Discover in-depth insights on , , , and , exploring their intricacies and applications.

Oura has dominated the wearables market in the good ring sport for quite some time, but following the success of the Oura Ring Gen 3, numerous smaller companies are attempting to capitalize on the trend and enter the fray. Ringing in on the trend of popular ring wear, RingConn appears poised to capitalize on the growing demand for this unique accessory.
While the RingConn Good Ring may lack visual flair, its impressive feature set more than compensates for any aesthetic shortcomings, offering a range of wellness tracking capabilities, an engaging and user-friendly app, and remarkable battery life that matches or surpasses that of the Oura Ring Gen 3. Here’s a revised version: While it may not represent the pinnacle of excellence, the RingConn Good Ring has the potential to become your go-to (or initial) reliable choice for all your connection needs.

The RingConn Good Ring is priced at $279, a more affordable option compared to the Oura Ring Gen 3. With its competitive pricing, users of RingConn’s innovative Good Ring solution also enjoy the added advantage of no subscription fees required to access their health insights.
The ring is offered in a range of sizes, spanning from 6 to 14, making it likely that a suitable size can be found for most people. Available in a trio of distinct hues, this item can be had in Moonlit Silver, Midnight Black, or radiant Pale Gold.
At the time of writing, RingConnect offers a limited-time discount on its premium services, effective until July 10, reducing the price tag significantly. Can be purchased directly from the website or through Amazon.com.
| Class | RingConn Good Ring |
|---|---|
| Supplies | Titanium, PVD coating |
| Safety | IP68 water and dirt resistance |
| Sensors | PPG, temperature, 3D accelerometer |
| Battery | For an additional $18, you’ll receive a USB-C charging cradle that can keep your device charged for up to 7 days. |
| Connectivity | Bluetooth 5.2 |
| Platform assist | iOS (Apple Health), Android (Google Fit) |
| Dimensions | Width: 7.8mm, thickness: 2.6mm |
| Weight | 3-5g (relying on measurement) |
| Sizes | 6-14 |
| Colours | Mysterious Hues: Moonlit Silver, Midnight Black, and Pale Gold |

If you’ve been following recent good ring recommendations, you’ll likely notice that the RingConn Good Ring stands out with its unique design. Here is the improved text in a different style: With its unique squircle design and remarkably matte finish, this ring presents a fresh yet understated aesthetic. While this ring may not possess the same level of opulence as others, its unique design is what truly sets it apart, making it a standout in a world where circular designs are ubiquitous. The ring’s slim profile is notable, measuring a mere 2.6 millimeters in thickness and weighing between three to five grams, depending on the scale used.
The ring sits comfortably on my index finger, unaffected by its rounded interior, except where a flat back accommodates the sensors. While that’s one way to determine the correct orientation of a ring, it’s not always reliable as different rings may feature unique designs or markers that serve as indicators. I don’t seem to experience any issues with the ring slipping around excessively on my finger.

The ring’s setup process requires little to no time investment, boasting a straightforward user interface divided into three intuitive sections: Insights, Developments, and a Me tab that enables users to manage their profile and customize ring settings. Although the UI may appear somewhat cluttered to some users, particularly on the Insights tab, the information is presented in an organized manner, allowing for easy comprehension of what’s being displayed. The Wellness Stability feature stands out as an intriguing aspect of the app, with its beta functionality condensing user data into a visually engaging graph. While using this tool provides a visually appealing way to identify gaps, it also enables analysis of data compared to yesterday’s graph, allowing for insight into your progress over time?
Beneath the graph, you can access swift guidance on how to optimize your well-being, or tap the tile for comprehensive explorations of each metric: Sleep, Exercise, Stress Management, and Vital Signs. To gain a more comprehensive understanding, consider exploring in-depth views that provide personalized insights into aspects such as sleep patterns, with each metric boasting its own dedicated tile within the Insights tab. With this innovative device, you gain access to a wealth of personal data, including sleep patterns, skin health, vital signs, stress levels, physical activity, and overall energy dynamics – all neatly organized across various tiles for easy exploration. You can reorganize the layout within each tile as needed, concealing certain details if desired – such as hiding your Standing time, should that be crucial.
The Insights tab features a useful Health Timeline that provides a comprehensive overview of your daily activity throughout the day. The app offers a quick snapshot of your sleep patterns, allowing you to monitor progress towards established calorie goals once specific actions are taken.
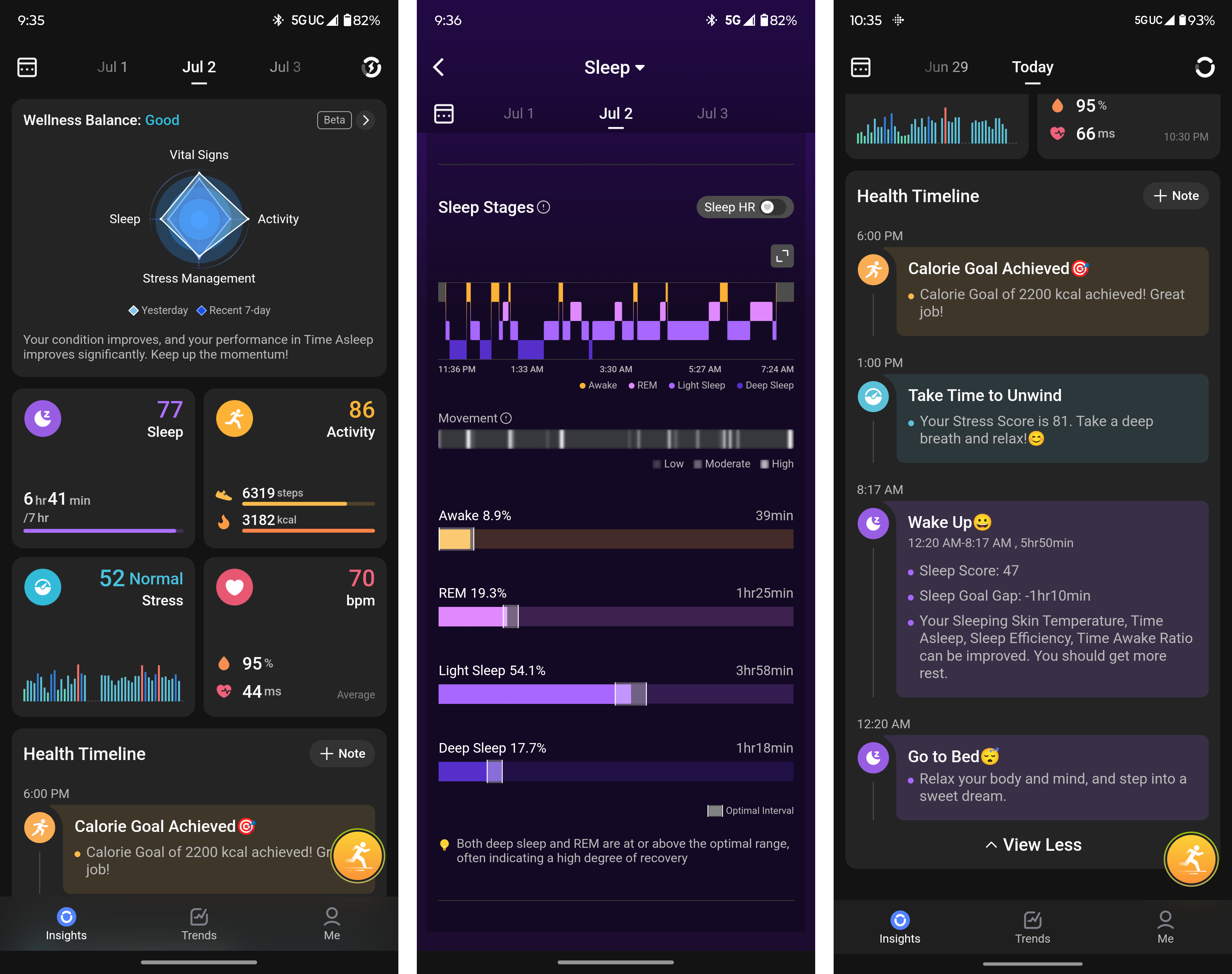
On the current tab, users have access to a convenient Fast Action Button (FAB) that enables rapid transition into exercise tracking. With this feature, individuals can seamlessly select from a variety of training modes, streamlining their workout experience. RingConn Good Ring is poised to meticulously track progress for working and biking enthusiasts, with additional features on the horizon.
While the step counter may occasionally exhibit slight inaccuracies, this is a common characteristic of high-quality fitness trackers, not necessarily limited to smart rings. On certain days, my fitness tracker tends to overestimate the number of steps I’ve taken significantly, especially when compared to my actual route, while on other days it falls short. While it’s expected that devices will exhibit varying degrees of sensitivity, pinpointing a wearable that achieves 100% accuracy is a challenging prospect.
Coronary heart rate readings seem consistent with those from my other devices, including my smartwatch and sleep monitoring device, which have accurately tracked my sleep patterns, duration, and vital signs.
Although the step counter may not be entirely accurate, the RingConn Good Ring excels at tracking sleep metrics.
The RingConne’s good feature set stands out, including menstrual prediction functionality that leverages temperature readings and other data to help determine the date of your next period – a valuable tool for those seeking greater insight into their reproductive cycles, albeit not something I personally would verify.
The RingConn app for Android offers a streamlined interface featuring a series of customizable widgets that provide instant access to vital information, including health scores, battery levels, and more, directly on the home screen.
The RingConn app rewards users with badges, primarily driven by specific performance metrics achieved or milestones reached, such as sustaining ring usage over a set duration. While playing with a valuable ring can be an entertaining experience, allowing you to earn badges and level it up adds a new layer of engagement and challenge.

The process of charging the ring stands out significantly from that of other rings. The smart ring includes a convenient charging cradle that allows for seamless portability, enabling users to charge their device on-the-go while keeping it powered and ready to use whenever needed. With its exceptional battery life, you may not need to worry about recharging your RingConnect Good Ring, as it rivals the performance of the renowned Oura Ring in this regard. Having enjoyed a remarkable 7-day stretch free from competition, I’ve managed to maintain an impressive level of consistency. I didn’t bother to pack my phone’s charging cradle before setting off on my short trip. After weeks of carrying the burden, I had become accustomed to embarking on journeys without concern that my companion would perish during my absence.
One of the greatest aspects of this experience is that the relevant data is freely available to me without the need for a paid subscription. Oura’s offering provides valuable insights alongside numerous options; however, users must commit to a $6.99 monthly fee for its most useful features, posing a relatively substantial additional cost above the device’s initial $299 value.

Despite its impressive features, the RingConn Good Ring is far from perfect. While serving as a wellbeing monitoring system, the ring’s health tracking abilities are somewhat limited due to its primary function being a device rather than a dedicated health wearable. The train monitoring function currently exists in beta mode, with limited functionality available until further development is completed. Manually track outdoor or indoor exercises, including jogging, cycling, and walking, with the goal of expanding to additional sport modes in development.
While RingCon’s offerings meet expectations for reliable rings, it would be beneficial to integrate digital monitoring capabilities to proactively detect potential concerns such as walking or working anomalies. The most notable drawbacks of the Oura Ring include: the app automatically logs a recorded exercise from a vast list, or prompts you to confirm whether you’ve engaged in specific activities such as walking, running, or dancing following physical activity.

One significant drawback is that, despite tracking numerous vital signs, RingConn only facilitates synchronization with Google Fit, without any support for alternative platforms. While the Match app seamlessly integrates with Wellbeing Join, it would be advantageous to have more precise control over data synchronization across devices, as well as enhanced syncing capabilities between my watch and Ring models.
While the Ring Conn Good Ring’s Bluetooth connectivity can be temperamental, it is crucial to await a stable connection before retrieving data.
The timing of the ring’s synchronization remains uncertain until it chooses to align its frequency. It seems that the ring app may experience delays in syncing data in the background, resulting in metrics only being updated when the app is opened. Although it may take a decent amount of time initially, the ring tends to sync effectively with my cellphone in due course. One may need to toggle Bluetooth functionality on and off twice to prompt the device’s successful pairing process.
Then there are notifications. While it’s not a major issue, I’d still find the RingConn’s irregularities quite bothersome. While positive for inactive alerts, I’d like to see notifications for bedtime reminders, badge notifications, and updates to my Health Timeline, such as new exercises or entries. Without a display screen to clutter my experience, I appreciate the simplicity of a wise ring over a smartwatch; yet, this very advantage can also be a drawback if I’m left wondering what’s happening on the device or what data it’s collecting.
While there isn’t an in-app feature to locate misplaced rings, it’s an intuitive function that several users might appreciate, considering the frequency of misplacing jewelry.

The primary and most prominent competitor is a 2021-launched product that has remained the top choice among customers. While Oura’s functions boast lightweight designs, the brand offers additional types of features and a leading role in terms of customization options. While the Oura’s subscription may be a deterrent for some, it actually makes the RingConnect GoodRing stand out more, offering an abundance of wellness monitoring insights without the additional cost.
When considering a good ring’s price, one important factor to contemplate is the. That’s another ring that offers a wealth of useful information and valuable insights, particularly surrounding the topic of sleep. Without any subscription fees being a significant advantage, the smart ring boasts remarkable battery longevity. Although lacking a necessary subscription, the premium pricing for the smart ring significantly exceeds those of the RingConnect and Oura Ring models, making it an unappealing option due to its high upfront cost, which may prompt you to explore alternative solutions instead.

As I delved into the world of wearable technology, I became aware of RingConn as a prominent rival to the popular Oura Ring, and I was intrigued by the potential of its innovative device to track various biometric signals. Wouldn’t it merely amount to a budget-friendly imitation of the pioneering system that sparked the original hype surrounding The Lord of the Rings franchise? Here’s an attempt to improve the text in a different style:
While, absolutely, implying it in one of the most excellent methods feasible.
The Ring Connec Good Ring is a thoughtfully designed wearable device boasting numerous advantages. While comparable to Oura’s wellbeing monitoring, the Fitbit app’s user-friendly layout offers extensive insights into overall health and wellness without requiring additional fees for access to this valuable data. It’s a stunning ring, boasting an impressive battery life that’s simply phenomenal.
While acknowledging some limitations, it’s clear that the Oura Ring Gen 3 fell short of expectations initially, with many features delayed from its launch. While the current state of the RingConn Good Ring appears satisfactory, its true potential remains untapped, with promising developments on the horizon to eagerly anticipate.
If you’re looking for an affordable alternative to the Oura Ring, this may be your best bet.
The RingConn Good Ring is an excellent wearable option for individuals passionate about monitoring and optimizing their overall health and wellbeing, offering intuitive visualizations of vital signs and actionable insights to facilitate self-improvement. There’s no subscription fee, which is always a significant advantage.

Scams
Fraudsters often use deceitful tactics to target unsuspecting travelers looking to book a well-deserved getaway, from sending sophisticated phishing emails to creating fake property listings.

Since its inception, Booking.com has emerged as a primary destination for travelers seeking lodging options, as well as a platform for businesses offering car rentals and airfare bookings. Globally, the total amount has more than doubled since 2016, reaching a staggering figure that surpasses the previous record by a considerable margin.
As its popularity has grown, so too have the attention of cybercriminals, who are naturally drawn to online platforms with high traffic volumes. Online travel booking platforms have become a lucrative hunting ground for scammers.
Booking.com acknowledges the significant scale of the challenge, having witnessed a remarkable “500-900% surge” over the past 18 months, primarily driven by developments since November 2022.
As peak travel season unfolds, it’s essential to scrutinize common scams targeting Booking.com users, as well as develop keen instincts for spotting suspicious activity while using the platform?
constant threat to your online security. In fraudulent schemes, scammers often pose as representatives of reputable platforms or organizations to deceive victims into thinking they are communicating directly with an official representative.
Scammers are relentless in their pursuit of unsuspecting victims on Reserving.com, crafting elaborate schemes where they impersonate the platform itself or representatives of a hotel or other services that users have booked via the site.
Scammers typically spin a convincing narrative, creating a sense of panic and prompting victims to click on a link that supposedly resolves an alleged issue or risks canceling their booking.
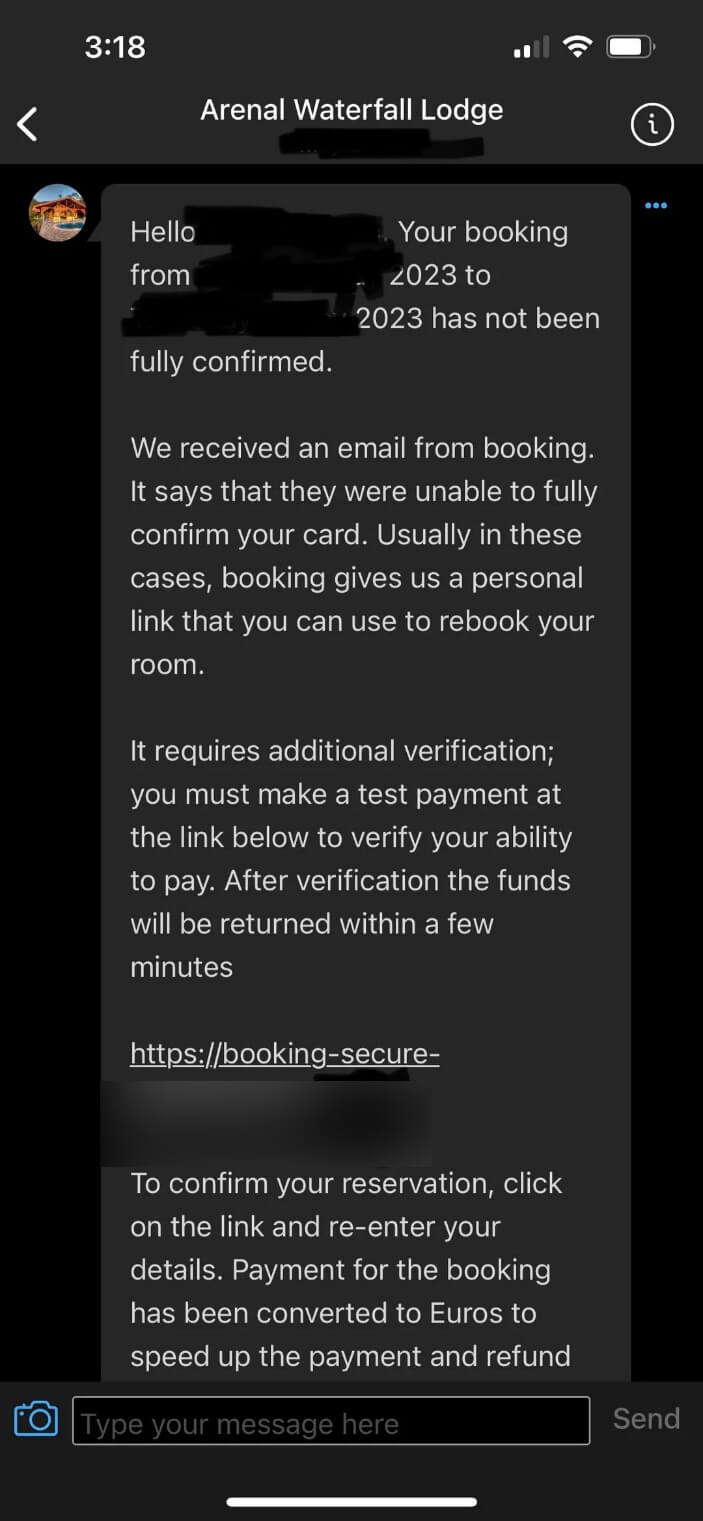
 As the accessibility of generative AI tools increases, scammers are now able to craft increasingly sophisticated and effective fraud schemes, leaving victims vulnerable to financial losses. Phishing attacks can deceive victims by crafting emails that are linguistically sound, contextually relevant, and devoid of obvious red flags, ultimately persuading individuals and organizations to surrender sensitive information or transfer funds.
As the accessibility of generative AI tools increases, scammers are now able to craft increasingly sophisticated and effective fraud schemes, leaving victims vulnerable to financial losses. Phishing attacks can deceive victims by crafting emails that are linguistically sound, contextually relevant, and devoid of obvious red flags, ultimately persuading individuals and organizations to surrender sensitive information or transfer funds.
Scammers may take their tactics to a whole new level by crafting personalized and sophisticated attacks. Cybercriminals have successfully exploited a vulnerability that allows them to deceive unsuspecting victims.
Following their discovery of inn reservation methods, holidaymakers promptly reached out to numerous individuals via in-app chat, requesting immediate payment verification for confirmed bookings.
The scheme revolved around a purported mistake in the initial payment, prompting a demand for an additional charge and necessitating their withdrawal. In various iterations of this scam, perpetrators seek sensitive information such as bank account details or personal identification data under false pretenses to authenticate or verify reservations.
If the issue was not caused by a backend program or infrastructure breach, it is crucial to be vigilant and scrutinize any requests for personal or financial information, as these can potentially compromise your security.
Some vacation properties appear to have leapt from the pages of a whimsical fairy tale, their lush surroundings and ornate details evoking a sense of enchantment. Some of these tales are so fantastical that they border on being utterly impossible? Over the years, numerous tourists have become victims of fraudulent rental listings where cybercriminals advertise luxurious vacation homes at unrealistically low prices, duping individuals into paying for bookings made through platforms like Booking.com. Upon arrival, you’ll find that the supposedly available accommodation either never existed in the first place or has been mislisted as a rental property.
As the platform’s safeguards swiftly take effect, false listings are promptly identified and removed. Despite this, consider the possibility that your trip may still be compromised; therefore, it’s wiser to conduct thorough research before making reservations.
Analyzing online reviews and ratings for the location, I compare its value to similar homes in the area, and conduct a reverse image search to verify whether the photo is original or potentially plagiarized from another website. If something appears too good to be true, it usually is.
“We’re seeking someone to evaluate and review resort bookings.” We typically spend anywhere from $200 to $1,000. The message, purporting to be from a reputable travel company, starts with a misleading claim: “All it’s good to do is fee or just like the resort on [a faux Reserving.com hyperlink].” This is an innovative spin on traditional practices.
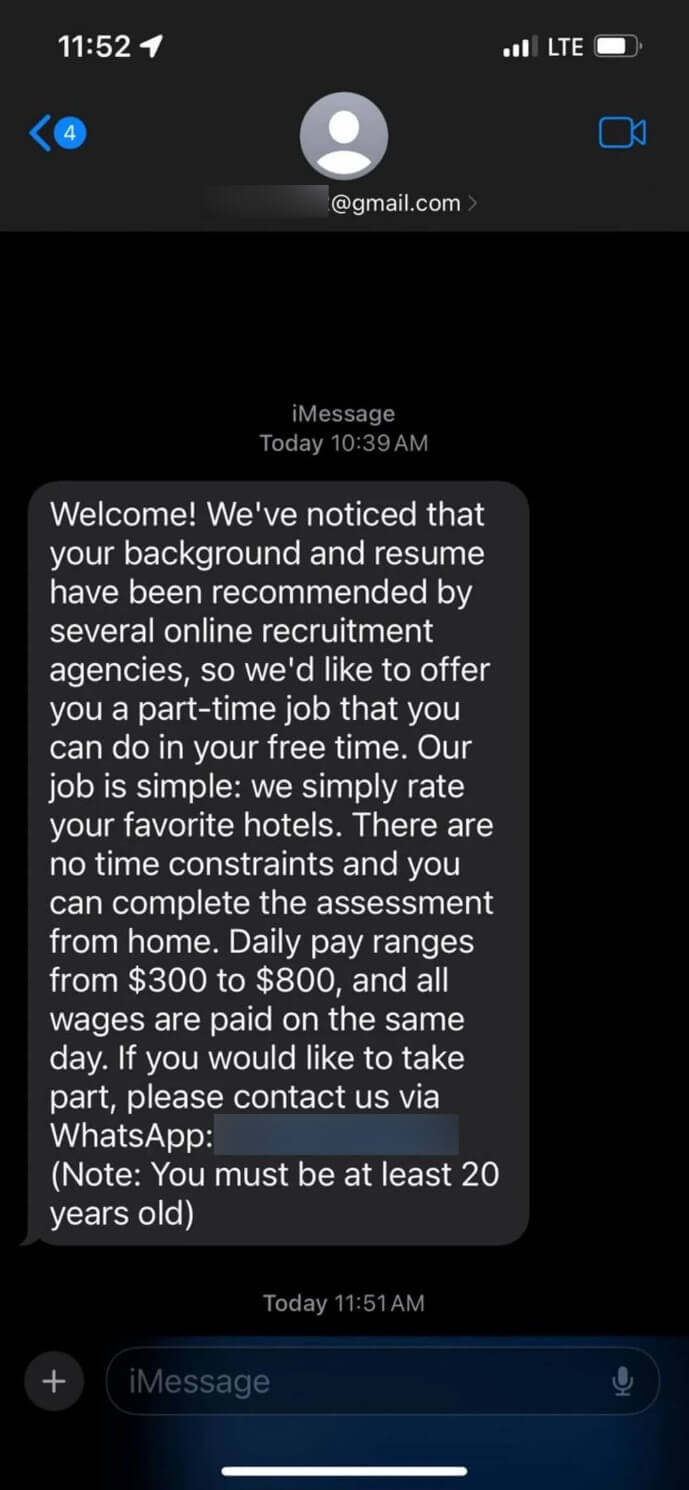
You’re subsequently asked to make an upfront payment to preserve their employment status and protect sensitive information such as social security numbers or other identifiable details that could be exploited for identity theft purposes? The scammers could also be online or offline, and their modus operandi may differ significantly.
How you can keep protected? Booking.com doesn’t typically rent out individuals to assess hotels, nor do they often engage with people via unsolicited text messages. Hiring occurs seamlessly through Reserved Careers, eliminating the need for users to search for vacant positions or evaluate hotel options.
Be wary of suspicious emails or messages that promise incredible deals or discounts on unbooked accommodations or travel packages?
Verify the authenticity of websites by checking their domain names, reviews, and contact information before making any transactions?
Research, research, research: read up on destinations, activities, and local customs to avoid cultural faux pas or misunderstandings?
Be cautious when using public Wi-Fi networks or unsecured connections for sensitive transactions like online bookings or money transfers?
Don’t click on suspicious links or download attachments from unknown sources, as they may contain malware or phishing scams?
Keep personal and financial information private by using secure passwords, two-factor authentication, and keeping data up to date?
Don’t send money to strangers or unfamiliar entities without verifying their legitimacy through trusted sources or authorities?
Report any suspicious activity or potential scams to relevant authorities, such as the Federal Trade Commission (FTC)?
Use reputable travel agencies, tour operators, or accommodation providers that have a strong reputation and physical presence?
Be wary of overly aggressive sales tactics or high-pressure offers that seem too good to be true?
Don’t book with companies that ask for upfront payments or deposits without providing clear refund policies or guarantees?
Keep copies of all booking confirmations, receipts, and correspondence in case of disputes or issues?
When utilising Booking.com, these guidelines will significantly contribute to your online safety:
Bon voyage!

DALL·E 3 has revolutionized the field of synthetic intelligence (AI) with its groundbreaking advancements in picture-generation technology, marking a significant milestone in this rapidly evolving domain. This latest iteration of the technology, engineered by OpenAI, surpasses its predecessors in generating increasingly sophisticated, refined, and context-specific images that accurately reflect the essence of provided textual descriptions. As the latest milestone in the DALL-E series, this third iteration represents a substantial leap forward in AI’s capacity to comprehend and render human language in vivid visual form? DALL-E 3 showcases unprecedented prowess in crafting remarkably intricate and imaginative visuals that meticulously align with complex linguistic cues, boldly expanding the boundaries of AI-driven visual content creation.
The novel system leverages cutting-edge deep learning techniques and an expansive repository of paired images and text data to accurately capture and represent visual concepts with remarkable nuance and creative flair. The AI’s capacity to comprehend summary concepts, unique genres, and nuanced specifics has unleashed a plethora of opportunities across diverse fields, including digital art, advertising, product design, and entertainment. DALL-E 3’s advancements in decision-making, stylistic versatility, and swift execution make it a valuable tool for both professionals and creatives, poised to transform the way visual content is conceived and produced.
api_key = “YOUR_API_KEY”
model = “dall-e-3″
def generate_image(prompt):
url = f”https://api.dalle-mini.com/alpha/generate?prompt={prompt}&num_results=1&size=1024×1024&model={model}”
headers = {“Authorization”: f”Bearer {api_key}”}
response = requests.get(url, headers=headers)
data = json.loads(response.text)
if len(data[“results”]) > 0:
image_url = data[“results”][0][“image”]
return image_url
else:
return None
prompt = “A futuristic cityscape with flying cars and towering skyscrapers”
image_url = generate_image(prompt)
print(image_url)
Launched in 2023, DALL-E is a cutting-edge artificial intelligence model that enables the creation of stunning visuals from written descriptions. This AI’s latest iteration boasts significant enhancements over its predecessor, DALL-E 2, featuring enhanced image quality, significantly expanded prompt comprehension, and a more meticulous commitment to adhering to user directives. The “DALL-E” identity combines the surrealist genius of Salvador Dalí with the resourceful spirit of WALL-E, Pixar’s robotic protagonist, highlighting its capacity to create art through AI-powered capabilities.
Additionally learn:
DALL-E 3’s core architecture is underpinned by a transformer-based framework, akin to those employed in generative pre-trained transformers for natural language processing applications. Trained on a vast dataset of image-text pairs, the model learns to associate verbal descriptions with specific visual locations.
While the full capabilities of DALL-E 3 are not intended for public use, OpenAI has made its API available for communication with this powerful model. Here is the improved text in a different style as a professional editor:
Python Code Illustrating DALL-E 3 API Usage
import openai import requests from PIL import Image import io OPENAI_API_KEY = 'your_api_key_here' def generate_image(description, num_images=1, size="1024x1024"): """ Generate an image using DALL-E 3 :param description: Textual description of the image :param num_images: Number of images to generate :param size: Size of the image :return: List of image URLs """ try: response = openai.Image.create(prompt=description, n=num_images, size=size) urls = [image.url for image in response] print(f"Generated URLs: {urls}") return urls except Exception as e: print(f"An error occurred in generate_image: {e}") return [] def save_image(url, filename): """ Save an image from a URL to a file :param url: URL of the image :param filename: Name of the file to save the image """ try: print(f"Attempting to save image from URL: {url}") response = requests.get(url) response.raise_for_status() img = Image.open(io.BytesIO(response.content)) img.save(filename) print(f"Image saved successfully as {filename}") except requests.exceptions.RequestException as e: print(f"Error fetching the image: {e}") except Exception as e: print(f"Error saving the image: {e}" description = "A futuristic city with flying cars and holographic billboards, in the style of cyberpunk anime" image_urls = generate_image(description) if image_urls: for i, url in enumerate(image_urls): if url: save_image(url, f"dalle3_image_{i+1}.png") else: print(f"Empty URL for image {i+1}") else: print("No images have been generated.")
Discover how to utilize DALL-E 3 and the OpenAI API to create and store an image locally. To utilize this service, you’ll require an OpenAI API key.
The primary objectives of this knowledge are:







Additionally learn:
While DALL-E 3’s advancements in AI capabilities are significant, they also pose fundamental ethical dilemmas.
OpenAI has implemented various safeguards, including content filters and usage policies, to address some of these concerns.
The emergence of DALL-E 3 signals a groundbreaking turning point in the realm of artificial intelligence and its potential to revolutionize creative industries.
DALL-E 3 represents a landmark innovation within the realm of. The technology’s ability to produce plausible, contextually accurate images from written input offers a wealth of opportunities across various industries and applications. Despite one’s robust knowledge base, responsibilities and ethical implications always accompany it.
As scientists continue to drive innovation in AI, cutting-edge tools like DALL-E 3 underscore the pressing need to balance technological advancements with ethical considerations? The future of AI-generated photography looks bright, marking just the beginning of a revolutionary technology that promises to transform the creative and visual arts landscape.
Ans. OpenAI introduced DALL-E 3, a cutting-edge AI model that brings text-based descriptions to life with photorealistic visuals. This cutting-edge model surpasses its predecessors, boasting enhanced image resolution and seamless comprehension capabilities, eclipsing the earlier DALL-E models in terms of sheer superiority.
Ans. It enhances decision-making, optimizes essential elements, clarifies textual interpretations, streamlines stylistic choices, and ensures moral safeguards and consistency across multiple eras.
Ans. With a wide range of applications across industries including marketing, sports development, architecture, education, recreation, fashion design, and product design.
Ans. While the full model is not available for public use, OpenAI offers an API that enables developers to interact with DALL-E 3 through which they can integrate its capabilities into their applications. The article provides an instance of a Python code that illustrates how to leverage this API effectively.

| |
We’re announcing the general availability of Amazon GuardDuty Malware Detection, which expands GuardDuty’s capabilities to detect malicious file uploads to selected S3 buckets. Prior to this, Amazon GuardDuty’s Malware Detection feature provided agentless scanning capabilities to identify and detect malicious files on volumes attached to and containerized workloads.
As a result, you’ll have the ability to continuously scan newly uploaded objects in S3 buckets for potential malware threats, swiftly initiating measures to quarantine or delete any malicious content identified. Amazon GuardDuty’s Malware Protection leverages multiple industry-leading, third-party malware scanning engines to provide effective malware detection without compromising the scalability, latency, or resilience of Amazon S3.
To enhance the security of your Amazon S3 data, utilize GuardDuty’s built-in malware and antivirus capabilities within your designated S3 buckets, thereby simplifying and streamlining malicious file analysis at scale. Unlike many existing instruments employed in malware assessment, this managed solution from GuardDuty eliminates the need for you to manage remote data pipelines or compute infrastructure across every AWS account and region where malware evaluation is required.
Your growth and safety teams can collaborate to design and manage a comprehensive malware security strategy across your organization, mandating that newly uploaded data from unverified sources undergo rigorous scanning for potential threats within specific designated buckets. You can configure post-scan motion in GuardDuty to enable object tagging, which allows for downstream processing and implementation of isolation strategies based on scan results, providing real-time visibility into malicious uploaded objects.
To begin, make a selection from within the options.

Identify and select an S3 bucket from a list of available buckets associated with the currently chosen region. Would you like to enable automatic scanning for new objects in your selected S3 bucket using AWS GuardDuty? While scanning the newly uploaded objects, you may also opt for selecting specific prefixes.

After analyzing an uploaded S3 object, GuardDuty can append a predetermined label for the primary consideration that GuardDutyMalwareScanStatus Why is the worth so negligible when the scan stands?
NO_THREATS_FOUND No malicious content detected during the scan of the object.THREATS_FOUND A potential threat has been identified during our comprehensive scanning process.UNSUPPORTED The object cannot be scanned by GuardDuty due to a measurement issue.ACCESS_DENIED – GuardDuty can’t entry object. Verify permissions.FAILED Guard Duty failed to scan the article.To integrate GuardDuty with Amazon S3 and apply tags to your scanned objects. When using tags, you’ll be able to create insurance policies that prevent objects from being accessed before the malware scan completes, thereby preventing your application from accessing potentially malicious objects.
Establish a secure position that satisfies all necessary authorization protocols.
To incorporate these permissions, replicate the coverage template and believe relationship template for subsequent integration. These templates contain placeholder values that should be replaced with relevant data specific to your bucket and AWS account. You must also substitute the **$AWS_KMS_KEY_ID** for the AWS KMS key ID.

Selecting this button will open the AWS Identity and Access Management (IAM) console in a brand-new tab. You can choose to either create a new IAM role or update an existing IAM role by mapping its permissions using the copied templates. To create or replace an IAM position upfront, navigate to the relevant section within the AWS documentation.
Select the GuardDuty browser tab with the IAM console open, then choose your recently created or updated IAM role.
Within the designated safety column, you will note the details for this secured container.

Here are the GuardDuty findings related to your S3 bucket: Upon identifying the discovery of a suspicious type, namely Object:S3/MaliciousFile, AWS GuardDuty has identified the specified S3 object as malicious. Observe the really useful remediation steps within the selected particulars panel. To learn more, refer to the comprehensive resources available within the Amazon Web Services (AWS) documentation.

 You can enable GuardDuty Malware Protection for S3 buckets without GuardDuty being enabled on your AWS account. Despite allowing GuardDuty access in your account, it is essential to enable comprehensive monitoring by utilizing key logging mechanisms, including administrative event logs, Flow Logs, and DNS query logs, in conjunction with malware detection capabilities. Safety findings can be dispatched to designated personnel for further investigation.
You can enable GuardDuty Malware Protection for S3 buckets without GuardDuty being enabled on your AWS account. Despite allowing GuardDuty access in your account, it is essential to enable comprehensive monitoring by utilizing key logging mechanisms, including administrative event logs, Flow Logs, and DNS query logs, in conjunction with malware detection capabilities. Safety findings can be dispatched to designated personnel for further investigation.
GuardDuty can scan records data belonging to the following synchronized storage options: S3 Standard, S3 Intelligent-Tiering, S3 Standard-Infrequent Access, S3 One Zone-Infrequent Access, and Amazon S3 Glacier Instant Retrieval. The software can scan files to detect and identify file codecs that may potentially harbour or contain malware, allowing for swift and effective mitigation of potential threats. At launch, our technology enables file sizes up to 5 gigabytes, while archived data can accommodate up to five tiers and a staggering 1,000 files per tier upon decompression.
GuardDuty will automatically send scanning metrics to your Amazon EventBridge for each protected S3 bucket, providing real-time insights into potential security threats and allowing for swift incident response. You can configure alarms and define subsequent scan actions, such as labeling the file or moving it to a quarantine repository. To learn more about various monitoring options, such as metrics and S3 object tagging, refer to the AWS documentation for additional information.
Amazon GuardDuty’s malware detection capabilities are currently available globally, with the exception of China regions and US GovCloud areas.
Pricing is based on the volume of gigabytes (GB) processed and the number of unique objects evaluated within a 30-day period.
This characteristic comes with a restricted AWS Free Tier, which includes 1,000 requests and 1 GB per month, subject to terms, applicable for the first 12 months of account creation for new AWS accounts, or until June 11, 2025, for existing AWS accounts. Wanting to learn more? Visit our website for additional guidance!
Amazon S3 provides advanced security features, including GuardDuty malware protection, to safeguard sensitive data stored in buckets.
To ensure the integrity of your S3 bucket, implement the following measures:
1. Enable GuardDuty: In the AWS Management Console, navigate to the GuardDuty dashboard and toggle the switch to “Enabled”. This will activate real-time threat detection and alerts for potential malware infections.
2. Configure S3 Bucket Policies: Set restrictive policies on your S3 buckets using Amazon S3 bucket-level permissions. Limit access to specific users or roles by specifying IP addresses, geolocation, or time ranges.
3. Utilize Amazon S3 Block Public Access: By default, public access is disabled for new buckets. Ensure that this setting remains in place by configuring the “Block Public Access” feature to prevent unintended exposure of your data.
4. Monitor Bucket Activity: Keep a close eye on bucket activity and logs using Amazon CloudWatch. This will allow you to identify unusual patterns or potential security threats, enabling swift action to mitigate any issues.
5. Implement Encryption: Ensure that all sensitive data stored in S3 buckets is encrypted at rest using Amazon S3 encryption. This can be done by configuring the “Server-Side Encryption” feature during bucket creation.
6. Utilize IAM Role-Based Access Control (RBAC): Define and manage role-based access control for your AWS users and roles to ensure that only authorized personnel can interact with your S3 buckets.
7. Limit Bucket Permissions: Restrict permissions on your S3 buckets by limiting the actions that users or roles can perform, such as listing, reading, writing, or deleting bucket contents.
8. Utilize Amazon S3 Versioning: Enable versioning for critical buckets to maintain a history of changes and prevent accidental overwrite or deletion of important data.
9. Conduct Regular Security Audits: Periodically review and audit your S3 bucket configurations, access controls, and security settings to identify potential vulnerabilities and strengthen your overall security posture.
By following these best practices, you can significantly reduce the risk of malware infections and ensure the safety and integrity of your Amazon S3 buckets. For additional information, visit the website and submit your shipping suggestions through the portal or contact your standard Amazon Web Services (AWS) support channels directly.
—
We updated the screenshot to ensure malware safety for S3 buckets and added hyperlinks to relevant AWS documentation.
Establish a Framework for Self-Supervised Learning: Step-by-Step Approach. While refining recurrent SSL models, we observe that the performance degradation follows a step-wise pattern on the left axis, while the learned feature representations progressively increase in complexity along the bottom axis. The direct visualisation of embeddings, substantiated by three fundamental PCA directives, reveals that initialisations collapse partially before expanding into a one-dimensional manifold, a two-dimensional manifold, and subsequently unfolding in tandem with iterative steps within the loss function.
Deep learning’s remarkable efficacy can largely be attributed to its ability to identify and distill meaningful abstractions from intricate data. Self-supervised learning (SSL) has emerged as a leading framework for extracting visual features directly from unlabeled images, analogous to how large language models (LLMs) learn linguistic representations from web-scraped text. Despite SSL’s prominent role in cutting-edge fashion trends, fundamental queries persist: What do self-supervised image programs ultimately study? How does this process unfold?
We present a novel approach to learning from our proposed simplified theoretical model, which we rigorously develop, by processing information through a series of distinct and well-defined stages. As we unveil this behavior’s far-reaching implications, it becomes evident that its consequences will resonate across a wide spectrum of cutting-edge applications currently in use.
This breakthrough unlocks fresh opportunities to refine SSL tactics, while prompting a wide range of innovative research queries that, once resolved, will offer a powerful framework for grasping the intricacies of cutting-edge deep learning applications.