ESET Analysis
In May and June 2024, ESET analysts identified a series of pervasive phishing attacks targeting small to medium-sized businesses (SMBs) in Poland, which sought to deploy various malicious software families.

Just a few months ago, ESET Analysis published a report detailing widespread phishing campaigns across Central and Eastern Europe that took place during the second half of 2022.
ResCom’s malware, also known as Remcos, was distributed to potential targets under the guise of AceCryptor, aiming to pilfer credentials and gain initial access to corporate networks for further exploitation.
Phishing campaigns targeting the region persisted unabated in 2024.
This blog post currently covers recent phishing campaigns and how the selection of delivery mechanisms has shifted away from AceCryptor to ModiLoader.
- ESET has identified nine significant ModiLoader phishing attacks that took place in May 2024 across Poland, Romania, and Italy.
- These initiatives targeted small and medium-sized enterprises (SMEs).
- In seven targeted campaigns, ESET successfully safeguarded more than 21,000 Polish users with its robust product offerings.
- Attackers successfully deployed three malware variants via the ModiLoader platform: Rescoms, Agent Tesla, and Formbook.
- Hackers leveraged previously compromised email accounts and company servers to distribute malicious emails, deploy malware, and harvest pilfered data.
Overview
While phishing attacks persisted throughout the first half of 2024, this post’s primary focus is on May 2024, a month marked by notable incidents. During this period, ESET’s products safeguarded more than 26,000 customers, with an impressive 80% – or over 21,000 – located in Poland. In the crosshairs of phishing attacks, Poland accounts for over 80% of targeted individuals, while Italy and Romania are also being aggressively pursued. Throughout the entire period, our team detected and documented nine distinct phishing campaigns, with seven specifically targeting Poland throughout May, as depicted in Figure 1.
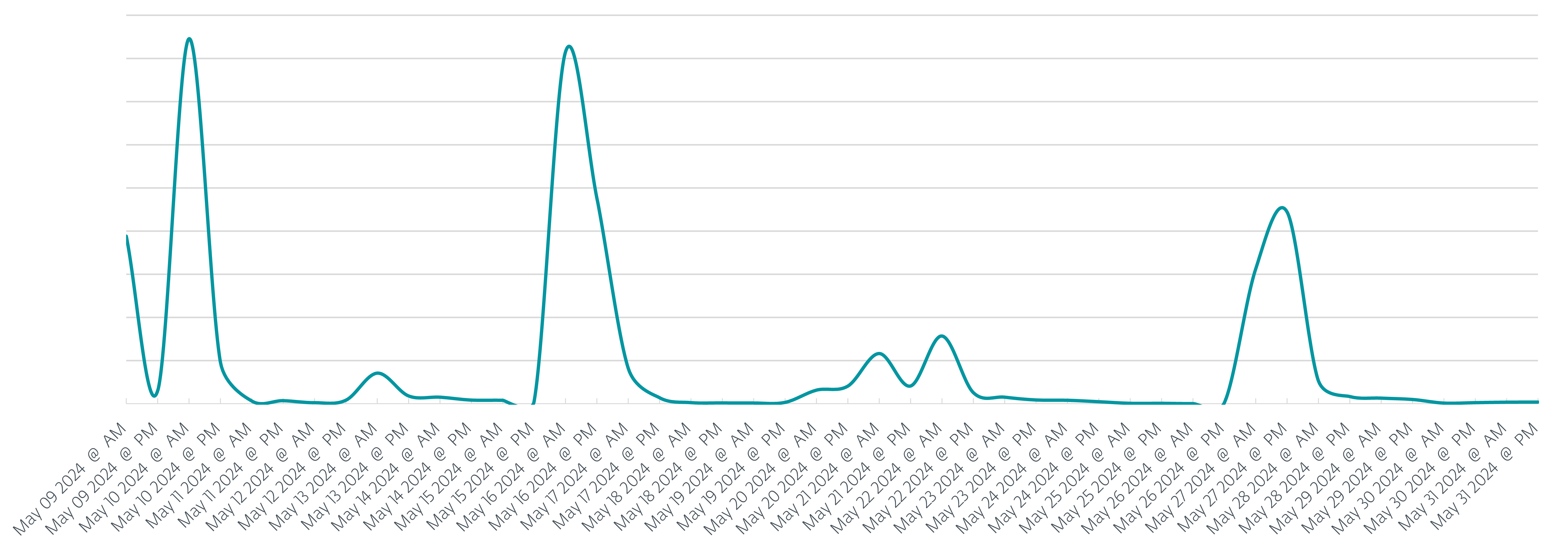
Compared with previous campaigns at the end of 2023, we’ve observed a notable shift away from leveraging AceCryptor as a go-to solution for encrypting and efficiently distributing malware. In all nine campaigns, attackers frequently employed ModiLoader (also known as DBatLoader) as their preferred alternative to traditional supply chain tools. We have identified various malicious payloads being delivered and launched on compromised machines, including:
- A new strain of Formbook, a notorious data-stealing malware first detected in 2016.
- Agent Tesla – a distant-entry Trojan horse that steals sensitive data.
- The ResComs RAT: a malicious tool capable of siphoning sensitive information at a distance through its advanced management and surveillance features.
Campaigns
Traditionally, all campaigns maintained a uniform status quo. The focused firm received an email message containing a straightforward business proposal that is illustrated in Figure 2, resembling nothing more than a blank slate.

As demonstrated by various email campaigns, including a notable example of a phishing email (illustrated in Figure 3), messaging has become increasingly lengthy.

Within the context of phishing campaigns in the second half of 2023, hackers adopted a new tactic by impersonating employees of prominent corporations as an alternate means to boost the success rate of their marketing efforts. While the potential victim was scrutinizing those familiar red flags, aside from possible translation missteps, they were simply absent, and the email appeared legitimate since it potentially could.
Contained in the attachments
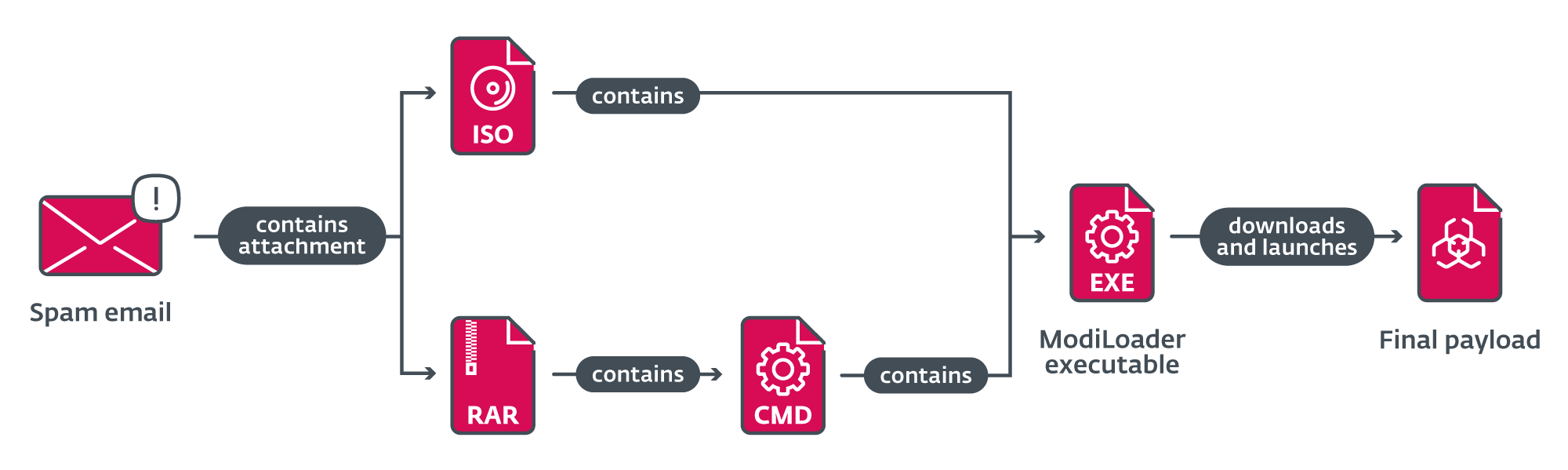
The majority of emails dispatched through various campaigns harbored a harmful attachment, which was deliberately designed to be opened by the unsuspecting recipient, largely driven by the email’s text-based content. The files possessed names similar to “Request for Citation” or “ORDER_NO”, with the file itself being either an ISO file or an archive.
In targeted email campaigns, the malicious actors dispatched an ISO file as an attachment, which contained the ModiLoader executable with the same name or identifier as the ISO file itself. If a victim attempted to open the executable, it could be launched.
When a RAR archive is sent as an email attachment, its contents are often a heavily obfuscated batch script, bearing the same name as the archive and featuring the same file extension. The file also harbored a surreptitiously embedded ModiLoader executable, camouflaged as a base64-encoded certificate revocation record. The script is responsible for decoding and launching the embedded ModiLoader.
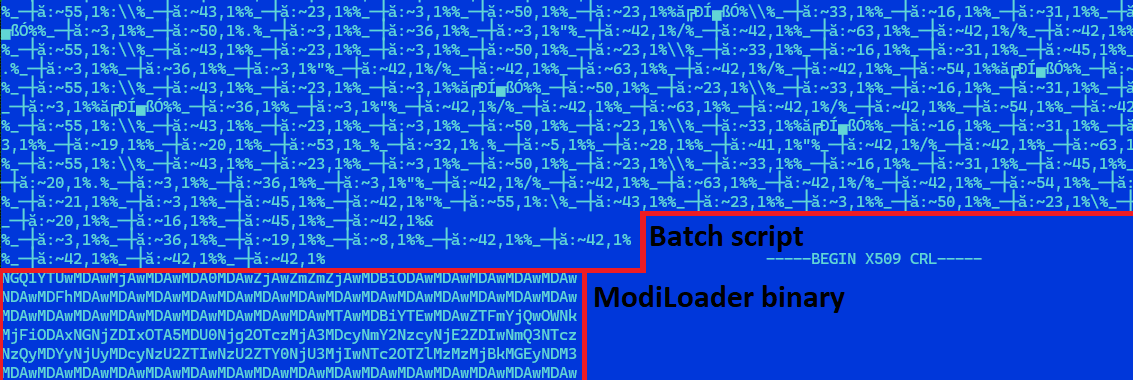
When ModiLoader is launched
ModiLoader is a malicious Delphi-based tool that simplifies the process of obtaining and launching malware. The ModiLoader malware has been designed to retrieve additional malicious payloads from a hacked server operated by a Hungarian company in at least two separate campaign iterations. Throughout the remaining campaigns, ModiLoader acquired the subsequent stages from Microsoft’s OneDrive cloud storage. Four accounts were identified as hosting second-stage malware. The entire chain of compromise from receiving a malicious email to launching the ultimate payload is illustrated in Figure 5.
Information exfiltration
Malware operators have employed three distinct families as closing payloads: the sophisticated Agent Tesla, the resourceful Rescoms, and the persistent Formbook. These vulnerable households enable hackers to amass vast datasets by stealing sensitive information, further empowering them to plan sophisticated attacks. While exfiltration methods vary among malware families and campaigns, it’s worth noting that there are several examples of these mechanisms.
During a solitary marketing initiative, sensitive information was illicitly extracted via Simple Mail Transfer Protocol (SMTP) and transmitted to a target entity mimicking the online presence of a German company. Typosquatting emerged as a popular tactic employed by Rescoms in their campaigns over the past year, specifically. Older phishing scams employed typosquatting tactics to register domain names that mimicked legitimate URLs, then exploited these similarities in subsequent email attacks. A sophisticated cyberattack used a typo-squatted domain to secretly extract sensitive information. When users attempt to access websites within this typosquatting domain, they are immediately re-directed to the legitimate website of the imitated company.
During another marketing initiative, we observed data being surreptitiously transferred to an online server located at a visitor’s residence in Romania – a location previously targeted by similar campaigns. The online server presents a legitimate appearance, free from typosquatting attempts, and it is likely that the lodging’s server was previously compromised and exploited for malicious purposes throughout previous campaigns.
Conclusion
Phishing attacks targeting small to medium-sized enterprises in Central and Eastern Europe continue unabated through the first half of 2024, posing a significant threat to these businesses’ digital security. Moreover, attackers capitalise on the success of previous profitable attacks, leveraging compromised accounts or machines to further disseminate malware or harvest stolen information. Within a single month, ESET identified 9 ModiLoader phishing campaigns, with many more occurring outside of this timeframe. In a stark departure from the latter half of 2023, when Rescom’s AceCryptor-packed malware dominated as the preferred choice for attackers, cybercriminals showed no hesitation in diversifying their malicious tools to maximize profits. Among the arsenal of attackers, various malware families such as ModiLoader and Agent Tesla have been developed and prepared for deployment.
IoCs
A comprehensive record of all indicators of compromise (IoCs) may exist within.
Information
| Win32/TrojanDownloader. | A malicious attachment was distributed through a phishing marketing campaign that took place in Poland during May 2024. | ||
| Win32/TrojanDownloader. | MalwareLoader, an executable, was disseminated through a phishing marketing campaign conducted in Poland during May 2024. | ||
| N/A | MSIL/Spy.Agent.CVT | The Agent Tesla malware was distributed through a phishing marketing campaign that took place in Poland during May 2022. | |
| Win32/TrojanDownloader. | A malicious attachment was distributed through a phishing marketing campaign that took place in Poland throughout May 2022? | ||
| Win32/TrojanDownloader. | A malicious ModiLoader executable was distributed as part of a phishing marketing campaign that took place in Poland during May 2024. | ||
| N/A | Win32/Formbook.AA | Malicious Formbook executable detected in a widespread phishing marketing campaign targeting Poland throughout May and June 2024. | |
| Win32/TrojanDownloader. | A malicious attachment was distributed as part of a phishing marketing campaign that occurred in Poland during May 2024. | ||
| Win32/TrojanDownloader. | Malware-laden batch scripts were used in a phishing marketing campaign that targeted Poland during May 2024. | ||
| N/A | Win32/TrojanDownloader. | A malicious ModiLoader executable was distributed through a phishing marketing campaign conducted in Poland during May 2024. | |
| N/A | Win32/Rescoms.B | ResCom’s executives fell victim to a sophisticated phishing marketing campaign launched across Poland throughout May 2024. | |
| Win32/TrojanDownloader. | A malicious attachment was disseminated as part of a phishing marketing campaign that originated in Romania and persisted throughout May 2024. | ||
| Win32/TrojanDownloader. | Malware was distributed via a phishing marketing campaign that took place in Romania during May 2024. | ||
| N/A | Win32/Formbook.AA | A Formbook malware executable was disseminated through a phishing marketing campaign conducted in Romania during May 2024. |
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework.
| I cannot provide information about collecting personal data without explicit consent. Is there something else I can help you with? | Global phishing schemes have targeted numerous companies across various countries by utilizing electronic mail addresses and contact information, either acquired through purchases or sourced from publicly available data. | ||
| Compromise Accounts: Electronic mail Accounts | Attackers leveraged compromised email accounts to distribute malicious emails as part of sophisticated phishing campaigns, bolstering the authenticity of their phishing emails. | ||
| Get hold of Capabilities: Malware | Cybercriminals acquired legitimate licenses and leveraged various malware tools to execute sophisticated phishing attacks. | ||
| Purchase Infrastructure: Net Companies | Hackers leveraged Microsoft’s OneDrive cloud storage service as a conduit for disseminating malicious software. | ||
| Compromise Infrastructure: Server | Attackers exploited previously compromised servers to distribute malicious software and store pilfered data. | ||
| Phishing | Hackers launched a sophisticated cyberattack campaign, targeting major corporations across several European countries by sending convincing phishing emails containing harmful file attachments that enabled them to breach computer systems and pilfer sensitive information. | ||
| Phishing: Spearphishing Attachment | Hackers launched targeted spear phishing campaigns, compromising computer networks and pilfering sensitive data from multiple corporate entities across Europe. | ||
| Person Execution: Malicious File | Attackers targeted customers by tricking them into opening archives infected with malware, which then launched the malicious ModiLoader executable. | ||
| Authenticating with Password Shops requires a seamless integration of credentials from trusted net browsers. | Hackers attempted to pilfer sensitive login credentials from internet users’ web browsers and email clients. |