In case your ESC already comes with AM32, you possibly can configure or flash it utilizing one of many AM32 configuration instruments out there. Nonetheless, in case your ESC has BLHeli_32, changing it to AM32 is a little more advanced. This step-by-step tutorial will information you thru the method.
For extra details about ESCs, try this purchaser’s information: https://oscarliang.com/esc/
Disclaimer: Official directions can be found on the AM32 homepage: https://am32.ca/. This tutorial demonstrates how I personally flash my ESC. Observe these directions at your personal threat; I’m not liable for any damages. I like to recommend familiarizing with the method on a spare ESC that you just don’t want, so if something goes flawed you gained’t be grounded.
Why Flash AM32?
A few explanation why you would possibly wish to swap from BLHeli32 to AM32:
Nonetheless, when you discover it too tough to flash AM32, it’s completely high-quality to remain on BLHeli32 and hold flying for my part. There’s is basically nothing flawed to maintain flying BLHeli32, until there’s a bug or new options you wish to have by upgrading to AM32.
Or simply purchase ESC with AM32 pre-installed to keep away from all of the technicalities:
Course of Abstract
Listed here are the straightforward steps to flash AM32 onto a BLHeli_32 ESC:
- Join ESC to STLink V2 Programmer
- Take away write safety and erase the chip
- Set up AM32 Bootloader on the ESC
- Flash AM32 Firmware
Is Your ESC AM32 Appropriate?
In the intervening time, not each BLHeli_32 ESC is appropriate with AM32. Earlier than continuing, examine in case your ESC is appropriate: https://github.com/AlkaMotors/AM32-MultiRotor-ESC-firmware/wiki/Checklist-of-Supported-{Hardware}
What You Want
ST-Hyperlink V2 Programmer, buy right here (beneath $10):
STM32 ST-Hyperlink Utility: https://www.st.com/en/development-tools/stsw-link004.html
This software program is required for disabling write safety on the BLHeli_32 ESC, permitting you to put in the AM32 bootloader. Alternatively, you should use STM32CubeProgrammer, which can require account registration to obtain.
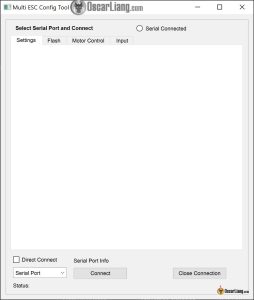
Multi_ESC Config Software: https://github.com/am32-firmware/AM32?tab=readme-ov-file#firmware-release–configuration-tool
This instrument is used to flash AM32 firmware and configure the ESC utilizing Betaflight passthrough, much like BLHeli32Suite.
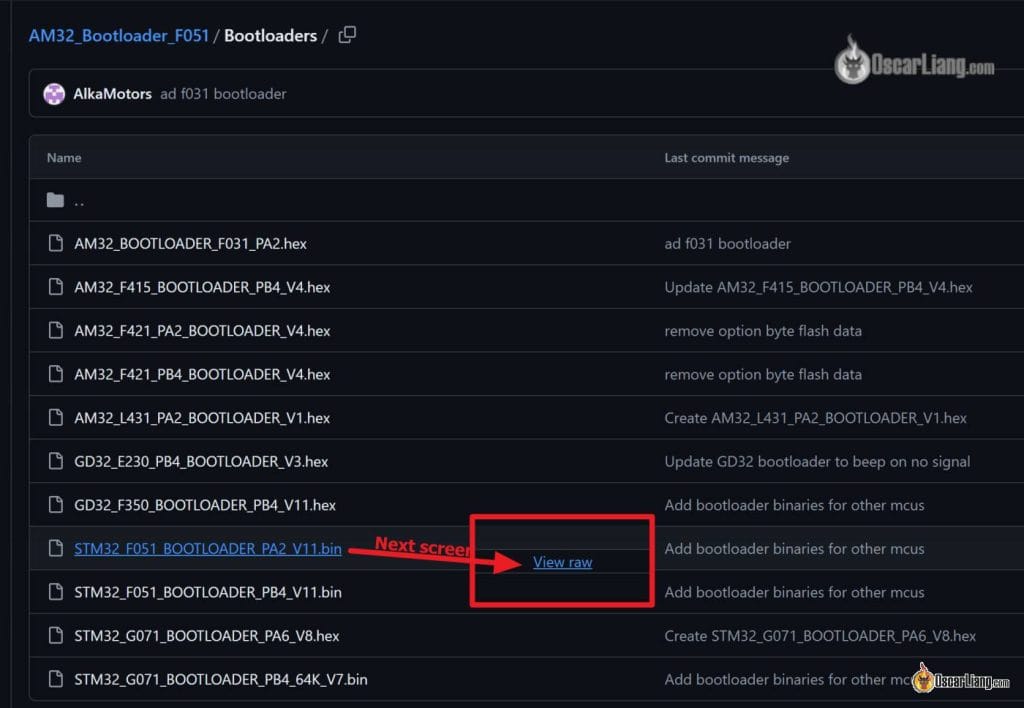
Obtain AM32 Bootloader file right here: https://github.com/AlkaMotors/AM32_Bootloader_F051/tree/important/Bootloaders
To find out which bootloader file is true your ESC, seek advice from the supported {hardware} checklist: https://github.com/AlkaMotors/AM32-MultiRotor-ESC-firmware/wiki/Checklist-of-Supported-{Hardware}
Instance: For the Tekko32 4in1 ESC with the STM32 F051 processor, it’s listed beneath the goal title FD6288, with the bootloader labeled PA2.
Click on on the required bootloader file, then choose “View uncooked” to obtain it.
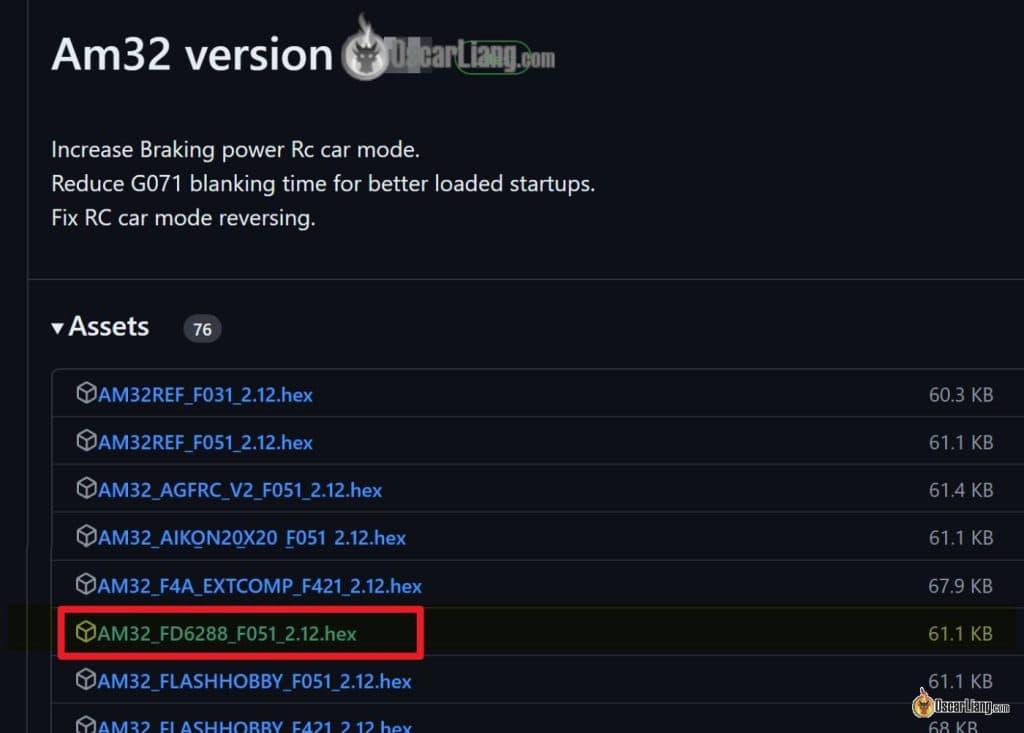
Obtain AM32 Firmware file right here: https://github.com/am32-firmware/AM32/releases
Make sure you get the right firmware file to your ESC primarily based on the goal title and processor sort. Incorrect firmware, the ESC merely gained’t work (e.g., no response and makes three brief beeps repeatedly when powered on). When you flashed the flawed firmware, you possibly can nonetheless flash the right one which ought to resolve these points, no less than that’s my expertise.
Discover the firmware file by goal title and processor, then click on the hyperlink to obtain.
Upon getting downloaded the 2 obligatory information, you might be prepared to start the flashing course of.
The way to Flash AM32 Bootloader
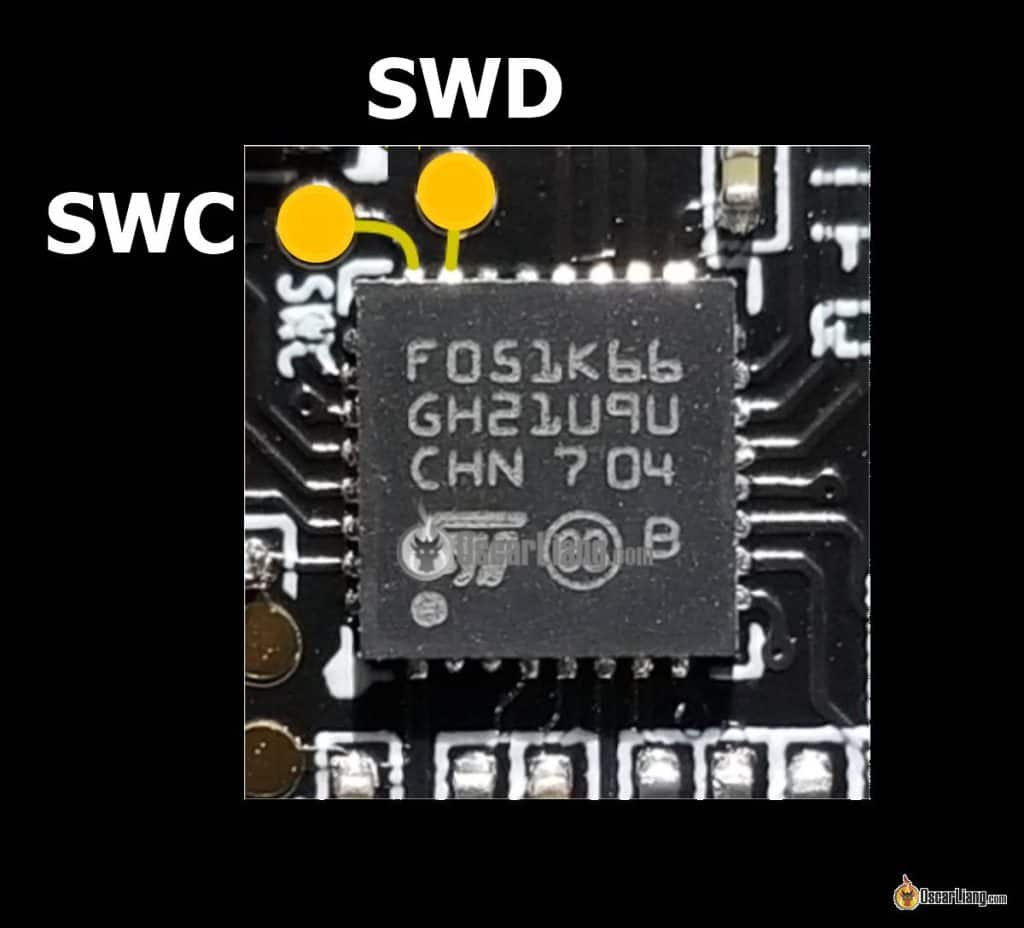
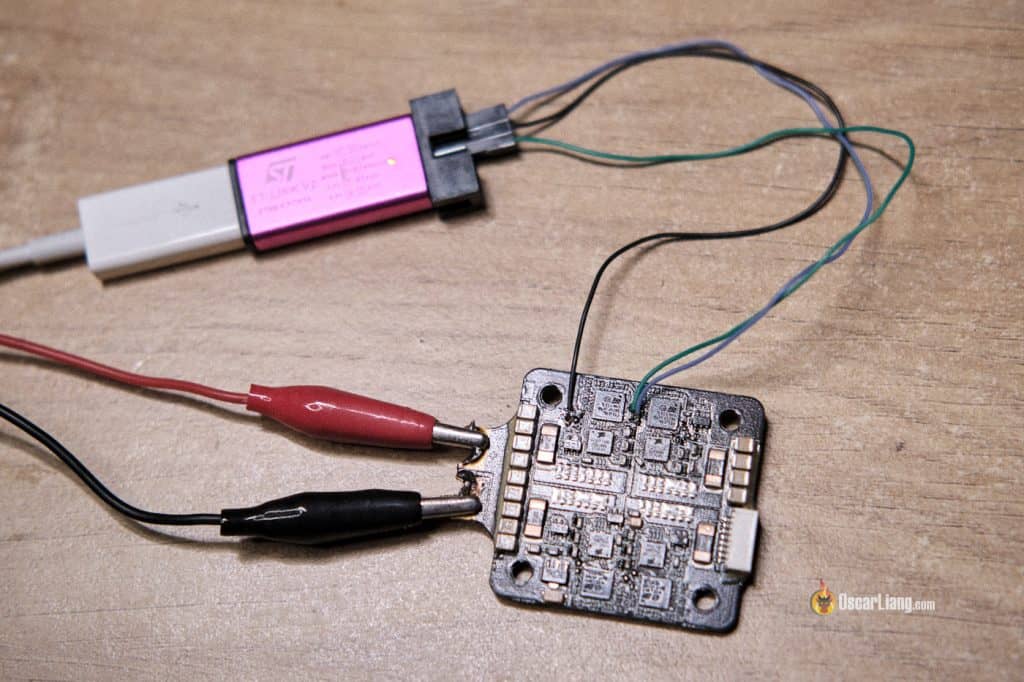
Connecting STLink Programmer to ESC
| ESC Aspect | ST-Hyperlink Software |
| SWC | SWCLK |
| SWD | SWDIO |
| GND | GND |
It’s essential to discover the tiny SWC and SWD pads for every ESC. Generally they’re labelled which is straightforward to identify.
The places of those pads are related throughout totally different ESCs, and you may inform them aside by following the traces.
You additionally want to attach the bottom (GND). You should utilize any GND on the ESC, together with the XT60 GND.
Earlier than connecting the STLink V2 instrument to the ESC, make sure the ESC is powered by a LiPo battery or bench energy provide by way of the XT60 connector.
Within the ST-Hyperlink Utility, click on on “Goal” within the high menu, then “Settings,” and alter Mode to “Scorching Plug.” Go away the remainder at default.
Eradicating Write Safety and Erasing the Chip
Disclaimer: When you erase the chip, you can’t flash BLHeli32 again onto the ESC.
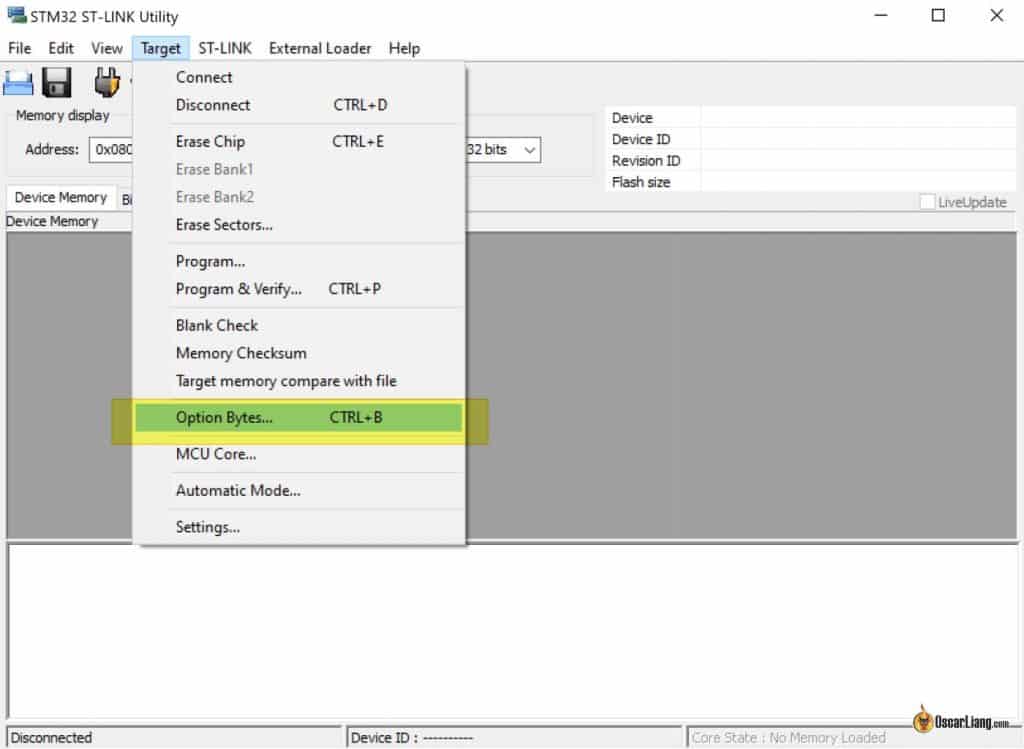
Click on on “Goal” within the high menu, then choose “Choice Bytes.”
Change “Learn Out Safety” to Stage 0, and click on on “Unselect all” beneath Flash sectors safety. Click on “Apply.”
It’s best to see “Choice Bytes Up to date Efficiently” within the console, indicating write protections have been eliminated.
Now, go to “Goal,” then “Erase Chip” to erase BLHeli32 on the ESC. When you encounter an error, strive “Erase Sectors” and choose all as a workaround.
Putting in AM32 Bootloader
Below “Goal”, click on on “Program”.
For F051 processors, make sure the Begin handle is 0x08000000. Choose the bootloader file and examine “Skip Flash Erase.”
Click on “Begin” to flash.
Eradicating SWC/SWD Wires
As soon as the bootloader is flashed, safely disconnect the ST-Hyperlink V2 instrument and desolder the SWC, SWD, and GND wires from the ESC.
Flashing AM32
As soon as your ESC has the AM32 bootloader, it will likely be acknowledged by AM32 Configuration Instruments, together with the Multi_ESC config instrument. There, you possibly can flash the AM32 firmware and cargo the default settings by way of Betaflight passthrough.
Join the ESC to your Betaflight flight controller and energy the ESC.
In Multi ESC Config Software, choose the COM port of your FC and click on “Join”.
Go to the “Flash” tab and click on on one of many ESCs you wish to flash (M1, M2, M3, or M4). It ought to say “Related – No EEprom”.
Load the firmware we downloaded earlier, then click on “Flash Firmware”.
As soon as accomplished, click on on “Ship Default Settings” to jot down the EEPROM.
Now repeat this for the opposite 3 ESC on the board, and you must now have a useful AM32 4in1 ESC!
Testing ESC
You possibly can check the ESC by soldering a motor to it and making an attempt to spin it within the Betaflight Motor tab. If all went properly, the ESC ought to work usually.
Configuring AM32
There are a number of instruments you should use to configure AM32 ESC, together with
- Multi ESC Config Software (standalone instrument)
- am32.ca (AM32 on-line instrument – Chrome primarily based)
- esc-configurator.com (Bluejay on-line instrument – Chrome primarily based)
For freestyle FPV drones, the AM32 builders suggest:
- Activate Variable PWM frequency
- Set Motor KV and Motor poles to match the motor
- Go away the remainder of the settings at default
I’ll present a extra detailed put up on the totally different settings after additional testing.
Conclusion
I hope you discover this tutorial helpful. Let me know when you have any questions. Blissful flying!































 Chandan Rupakheti is a Senior Options Architect at AWS. His most important focus at AWS lies within the intersection of Analytics, Serverless, and AdTech providers. He’s a passionate technical chief, researcher, and mentor with a knack for constructing progressive options within the cloud. Outdoors of his skilled life, he loves spending time along with his household and pals apart from listening and enjoying music.
Chandan Rupakheti is a Senior Options Architect at AWS. His most important focus at AWS lies within the intersection of Analytics, Serverless, and AdTech providers. He’s a passionate technical chief, researcher, and mentor with a knack for constructing progressive options within the cloud. Outdoors of his skilled life, he loves spending time along with his household and pals apart from listening and enjoying music. Parnab Basak is a Senior Options Architect and a Serverless Specialist at AWS. He makes a speciality of creating new options which might be cloud native utilizing fashionable software program growth practices like serverless, DevOps, and analytics. Parnab works carefully within the analytics and integration providers area serving to prospects undertake AWS providers for his or her workflow orchestration wants.
Parnab Basak is a Senior Options Architect and a Serverless Specialist at AWS. He makes a speciality of creating new options which might be cloud native utilizing fashionable software program growth practices like serverless, DevOps, and analytics. Parnab works carefully within the analytics and integration providers area serving to prospects undertake AWS providers for his or her workflow orchestration wants.


