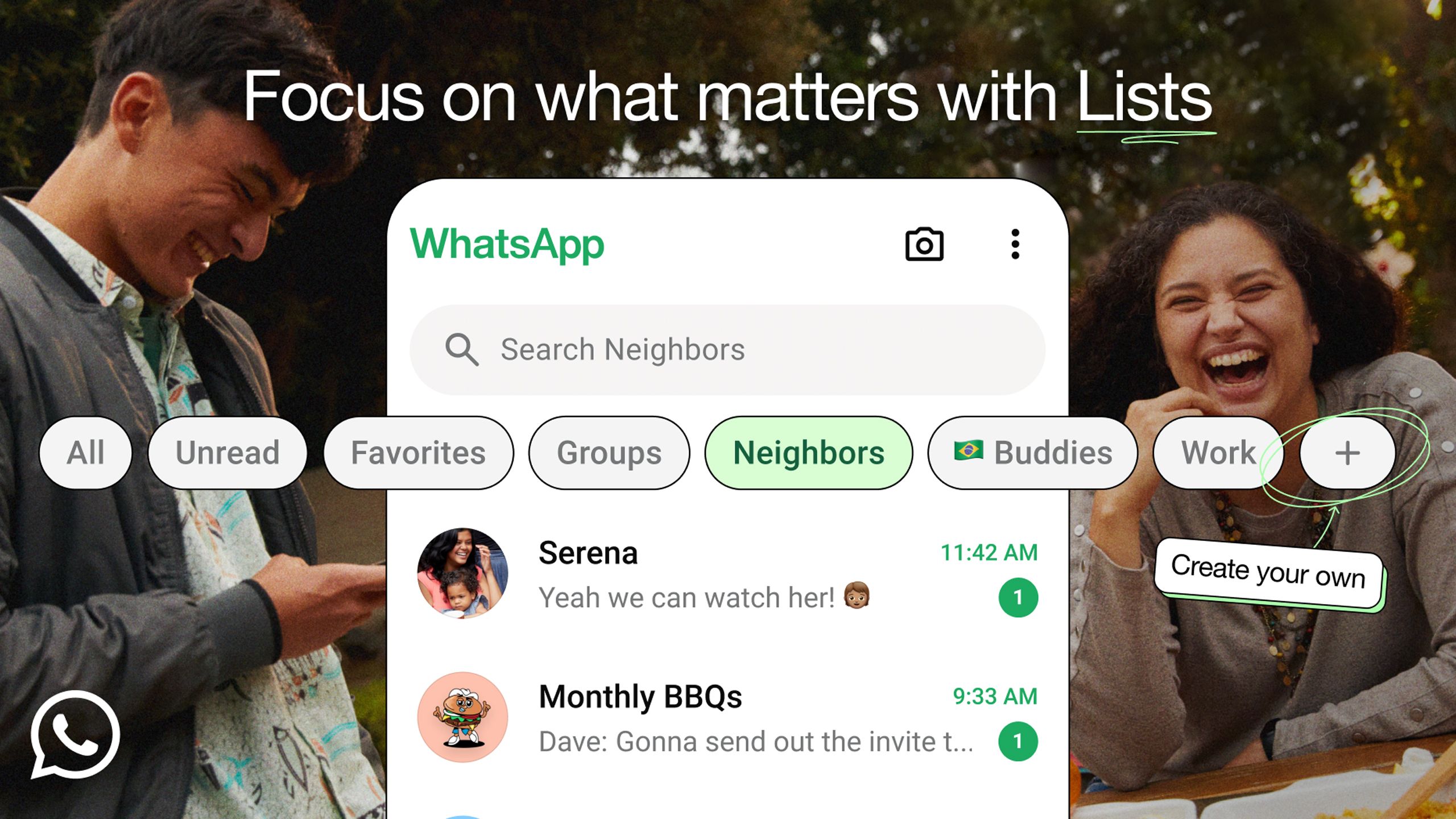
Faded sunsets dripped with melancholy’s heavy hue, as wispy beach umbrellas seemed to whisper secrets to the wind. Sweat-drenched tourists morphed into tormented figures, their smiles distorted into anguished grimaces. The turquoise sea churned with an undercurrent of despair, while seagulls wheeled above like harbingers of doom. In this desolate landscape, even the ice cream cones withered like forgotten dreams. It may well be better not to know.
What soothing tranquility might unfold if Hokusai’s brush danced across the canvas to capture the serenity of a scenic river panorama?
While model switching on photographs may not be a novel concept, its application received a significant boost with the work of Gatys, Ecker, and Bethge, who demonstrated an efficient approach utilizing deep learning.
Here’s the improved text:
The primary concept is straightforward: develop a hybrid that strikes a balance between what we want to manipulate and what we want to emulate, optimising for maximum similarity in both instances?
If you’ve read the chapter on neural fashion switching, you may recognize some of the code snippets presented.
Despite this, a pivotal differentiation exists: The deployment of TensorFlow enables a vital approach to coding, facilitating seamless mapping of concepts to code.
Here is the rewritten text:
Please provide the original text, and I will improve it in a different style as a professional editor. Amongst the many snippets, you won’t find yourself repeating any.
Stipulations
The compatibility of the code posted will hinge on the most recent iterations of several TensorFlow R packages. You can install these packages by following this setup procedure:
To ensure seamless integration with the latest advancements in machine learning, it is crucial to utilize the most recent version of TensorFlow – namely v1.10 – which can be effortlessly installed via the following configuration:
To effectively utilize TensorFlow’s eager execution, First, we have to name tfe_enable_eager_execution() proper originally of this system. We need to leverage the Keras implementation that comes with TensorFlow rather than employing a lower-level Keras implementation.
Let’s get started!
Here is our content landscape – contrasted by a canvas of your own.

Here: And behold this iconic fashion mannequin, inspired by Katsushika Hokusai’s works, available for acquisition at:

We develop a utility wrapper that efficiently aggregates and pre-processes all input images in one step.
As we plan to leverage VGG19’s expertise gained from training on ImageNet, we must preprocess our input images in the same manner employed during its development. Before showing the mixture picture, we will first apply the inverse transformation to it.
Setting the scene
We’re planning to utilize a neural network, but we won’t be training it. While neural fashion switching diverges from conventional optimization methods by not adjusting the community’s weights, it does successfully propagate the loss through the entire network, thereby enabling the transmission of information along the intended pathway.
We expect to be captivated by two types of contributions from the community, aligned with our dual goals.
We aim to maintain the mixture’s visual integrity at an exceptionally high level, mirroring the original content’s aesthetic quality. Within a convolutional network, higher-level layers abstractly represent more comprehensive concepts, suggesting that we select a layer situated further up in the architecture to compare outputs from the input data and the combined model.
The generated image should closely resemble the style of a professional fashion photograph. To align with the design template’s decrease stage options such as textures, shapes, strokes, a set of decreasing level convolutional block is selected for comparison and mixed results are obtained.
Losses
While optimizing the entire picture, we will consider three types of losses. How significantly does the blend diverge from the standard? Here, we are employing the sum of squared errors for purposes of comparison.
Our second concern is ensuring that all types are matched as accurately as possible. Models are typically operationalized due to the presence of flattened function mappings within a layer? What’s the relationship between map layers and fashion trends?
Subsequently, we calculate the Gram matrices of the layers that interest us, as previously outlined, for both the original image and the optimization candidate, and then analyze these matrices using the sum of squared errors.
Furthermore, ensuring the mixture image does not appear excessively pixelated requires incorporating a regularization component that accounts for the entire scope of variations within the picture.
What’s the optimal approach to combining these setbacks? We have achieved satisfactory results with the revised weightings; feel free to experiment and adjust them as needed.
The fashion industry’s demand for high-quality images has led to an increase in the use of mannequins as models. To create captivating photographs that showcase clothing and accessories, photographers are now incorporating these realistic figures into their work.
What drives this shift towards using mannequins? One key factor is the need for greater efficiency in fashion photography. Traditional photo shoots can be time-consuming and costly, requiring multiple models to be hired and dressed for each outfit.
We’re satisfied with the mannequin’s output for the content material and elegance photos, but it’s sufficient to achieve this just once.
We concatenate each photograph along the batch dimension, feed it into the model, and retrieve a list of outputs, where each item on the list is a 4D tensor. For the fashion image, we require the fashion output at batch position 1, while for the content image, we need the content output at batch position 2.
When uploading images, note that dimensions two and three may have varying sizes depending on the file size.
Computing the losses
On each iteration, we need to translate the mixture picture using the mannequin, acquire fashion and content outputs, and calculate the losses. Although the provided code features extensive comments with tensor sizes for easy validation, it’s worth noting that the specific numbers assume a workflow involving 128×128 images.
Computing the gradients
As rapidly as losses accumulate, calculating the gradients of the overall loss with respect to each parameter becomes simply a matter of calling tape$gradient on the GradientTape. Who coined the term “nested name”? compute_lossWhether the judgment of the mannequin regarding our mixed photograph is embedded within GradientTape context.
Coaching part
Now it’s time to coach! While maintaining the original’s informal tone, the revised text reads: Whereas we’d normally conclude with “…the mannequin,” our subject isn’t actually VGG19 – that model serves solely as a tool. Instead, we’re working with a basic setup comprising just:.
- a
Variable that holds our to-be-optimized picture - The losses in capabilities that we previously discussed.
- An optimiser that can apply the calculated gradients to the picture variable?
tf$prepare$AdamOptimizer)
Below, we display the fashion options from the fashion picture and the content material functionality from the content material picture simultaneously, followed by iterating through the optimization process, storing the output every 100 iterations.
Unlike the standalone tutorial and guide, yet aligning with Google’s best practices as outlined in their style guide, we’re deliberately opting out of using L-BFGS for optimization purposes, instead favoring Adam for the concise introduction to eager execution required here.
Despite this, another optimisation method could potentially be plugged in should you desire, thereby altering
optimizer$apply_gradients(checklist(tuple(grads, init_image)))
by an algorithm of choice, utilizing its inherent logic and naturally, assigning the optimized outcomes Variable holding the picture).
Able to run
Now that we’re prepared to begin the process:
By iteration 1000, we observed minimal variations in outcomes, which is the point at which our river panorama began to take shape.
…more eerily captivating than anything Edvard Munch might have conjured on canvas.
Conclusion
With the neural fashion switch, a certain amount of experimentation may be necessary to achieve the desired outcome. As our example illustrates, simplicity isn’t necessarily compromised by ease of implementation. To ensure transparency in understanding, effective implementation also enables adding debug output and step-wise examination of code line-by-line to scrutinize tensor shapes.
Until we meet again in our next execution phase.
Gatys, Leon A., Alexander S. Ecker, and Matthias Bethge. 2015. abs/1508.06576. .
Get pleasure from this weblog? Stay Informed – Receive Latest Posts Directly to Your Inbox:
Posts additionally obtainable at