Building Diverse Knowledge-Driven Organizations: Leadership Strategies for the Modern Workplace?

As underlying semantics are established, a common semantic layer should be built, integrating customer-facing platforms such as business intelligence (BI), spreadsheets, and embedded analytics, enabling seamless modeling and deployment of data across the enterprise through prebuilt integrations and a robust API suite. This text also offers a range of developer tools that facilitate collaboration by enabling the creation of data models, management of caching and pre-aggregations, and enforcement of data entry controls.
When implemented correctly, a shared semantic layer enables information groups to operate under additional governance and management, ultimately delivering more value to end-users by reducing misunderstandings between teams. This ensures uniformity and accuracy across all information consumption points, thereby enhancing effectiveness. Regardless of whether the information is being leveraged by an individual, a dashboard, or something providing answers to questions, the information remains consistent.
The ease with which information groups are able to quickly disseminate data to both internal and external stakeholders simplifies their communication processes. Organizations can effortlessly substitute outdated metrics, conceptualize novel perspectives on knowledge, and seamlessly integrate fresh sources of unprocessed data. Additionally, they can implement governance insurance policies, along with entry-level management, clear definitions, and operational efficiencies.
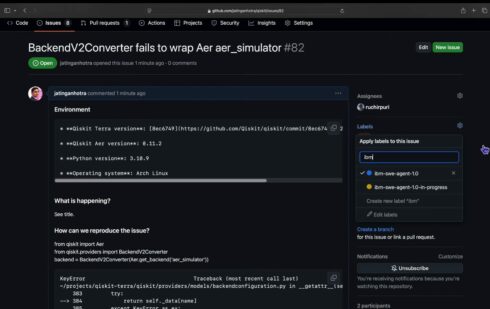
IBM is releasing a household of AI brokers (IBM SWE-Agent 1.0) which can be powered by open LLMs and might resolve GitHub points mechanically, releasing up builders to work on different issues quite than getting slowed down by their backlog of bugs that want fixing.
“For many software program builders, day-after-day begins with the place the final one left off. Trawling by means of the backlog of points on GitHub you didn’t cope with the day earlier than, you’re triaging which of them you’ll be able to repair shortly, which is able to take extra time, and which of them you actually don’t know what to do with but. You might need 30 points in your backlog and know you solely have time to deal with 10,” IBM wrote in a weblog submit. This new household of brokers goals to alleviate this burden and shorten the time builders are spending on these duties.
One of many brokers is a localization agent that may discover the file and line of code that’s inflicting an error. In response to IBM, the method of discovering the proper line of code associated to a bug report generally is a time-consuming course of for builders, and now they’ll have the ability to tag the bug report they’re engaged on in GitHub with “ibm-swe-agent-1.0” and the agent will work to search out the code.
As soon as discovered, the agent suggests a repair that the developer may implement. At that time the developer may both repair the problem themselves or enlist the assistance of different SWE brokers for additional assistants.
Different brokers within the SWE household embrace one which edits traces of code primarily based on developer requests and one which can be utilized to develop and execute exams. All the SWE brokers could be invoked instantly from inside GitHub.
In response to IBM’s early testing, these brokers can localize and repair issues in lower than 5 minutes and have a 23.7% success price on SWE-bench exams, a benchmark that exams an AI system’s capability to unravel GitHub points.
IBM defined that it got down to create SWE brokers as an alternative choice to different rivals who use giant frontier fashions, which are inclined to value extra. “Our purpose was to construct IBM SWE-Agent for enterprises who desire a value environment friendly SWE agent to run wherever their code resides — even behind your firewall — whereas nonetheless being performant,” stated Ruchir Puri, chief scientist at IBM Analysis.
At The Hospital for Sick Children (SickKids), a cutting-edge robotic system is revolutionizing the approach physicians and researchers take to treating cardiovascular disease.
Arrhythmogenic cardiomyopathy (ACM) is the leading cause of sudden cardiac death in younger adults. With no other recourse, a cardiac transplant remains the sole lifesaving option for individuals afflicted with this hereditary condition.
Now, an analysis workforce, led by Dr. Jason Mayne, a renowned researcher at Toronto’s Hospital for Sick Children (SickKids), has collaborated with several esteemed doctors to advance the field of pediatric medicine. Researchers at the University of Toronto’s Robotics Institute have created a groundbreaking robotic technology allowing scientists to simultaneously test multiple potential therapeutics for the first time.
“This capability allows us to deliver the most effective medication to the individual who needs it most at the precise moment,” asserts Dr. Maynes, Chief of the Division of Anesthesia and Pain Medicine, Associate Chief of Research for Perioperative Services, and Senior Scientist in the Molecular Medicine program.
Recent technological advancements have enabled the proliferation of high-throughput screening, facilitating the simultaneous evaluation of multiple potential therapeutics across a range of health conditions, including oncology. In stark contrast to cancerous cell dynamics, researchers studying cardiovascular disease encounter a unique challenge: capturing the complex, three-dimensional movements of cardiac cells in their natural state. The challenge lies in developing conventional drug-screening technologies that can swiftly and accurately deliver molecules into beating cardiomyocyte tissue without causing harm, rendering it difficult.
Confronted with this complex problem, the analysis workforce crafted an innovative solution – a diminutive robotic arm equipped with a versatile z-shaped micropipette and advanced 3D imaging technology that enables insertion of fluorescent molecules into drug-treated, beating cardiomyocytes at unprecedented speed and precision, thereby facilitating rigorous research on the efficacy of novel drug candidates.
The study’s outcomes are unveiled in , highlighting the significant advancements made by the team and underscoring the groundbreaking potential of their discovery to transform treatment options for cardiovascular disease patients.
“‘Through the application of this innovative approach, we were able to identify five promising therapeutic options for treating Acquired Cystic Macula.’ notes lead researcher Dr.” WenKun Dou, a postdoctoral fellow at the Hospital for Sick Children (SickKids) and the University of Toronto (U of T). “When interdisciplinary teams collaborate, novel breakthroughs can emerge.”
Researchers at the Centro Nacional de Investigaciones Cardiovasculares (CNIC) in Spain have collaborated on a drug candidate that has been shown to effectively reduce irregular heartbeats in a preclinical model developed by the Association for Computing Machinery (ACM).
The findings from this study have significant implications for individuals living with asbestos-related cardiovascular disease (ACM), as they may expedite the development of innovative treatments, ultimately eliminating the need for invasive cardiac surgery. As a result of implementing a personalized approach to high-throughput screening, the analytical team envisions that the far-reaching effects will transcend ACM and resonate within the broader context of SickKids’ Precision Child Health vision, a mission to deliver tailored care to every patient.
“With the capability to quickly model specific patient scenarios and test treatments at scale, therapy can be precisely tailored to meet the unique needs of each individual patient,” says Maynes.
The examination was supported by funding from the Canadian Institutes of Health Research (CIHR), Natural Sciences and Engineering Research Council of Canada (NSERC), the Ontario Research Fund – Research Excellence program, Montgomery County Intermediate Unit (MCIU), and the SickKids Foundation.

Innovative industries seeking reliable and eco-friendly inspection solutions for challenging environments now possess a game-changing alternative. The latest addition to our lineup, the T Model 5, seamlessly integrates cutting-edge hardware and software innovations to meet the growing need for precise, agile, and robust inspection solutions that exceed customer expectations. Developed in partnership with experts in non-destructive testing, the innovative model brings cutting-edge technologies to bear on inspection workflows across multiple industries, including wind farms, petrochemical facilities, and isolated industrial sites.
The Voliro T Model 5 boasts a cutting-edge 5G module that facilitates seamless, real-time data transfer, empowering remote monitoring and effortless software updates to ensure optimal performance and minimize downtime. The corporate emphasizes the benefits of this characteristic, noting it enables proactive wellbeing monitoring, maintenance, and seamless software upgrades, thereby streamlining inspection data management. This enhancement holds significant value for industries reliant on swift, accurate information for inspections, fostering improved upkeep, productivity, and adaptability, particularly in remote or hard-to-access locations – allowing them to respond quickly to changing circumstances?
Real-time information switching and monitoring facilitate proactive maintenance. Real-time wellbeing monitoring allows for swift detection of potential issues, enabling early intervention that minimizes costly downtime and prevents equipment anomalies from escalating. The enhanced connectivity also enables operators to make informed decisions in real-time, further streamlining processes through reduced response times. Will downtime be minimized?
The Voliro T Model 5’s robust security features integrate advanced motor monitoring capabilities, leveraging the insights from Digital Velocity Controllers (ESCs) to promptly detect potential motor anomalies. The innovative system empowers pilot operators to proactively address potential motor anomalies before they impact operations, thereby introducing an additional layer of safety during inspections.
The latest Voliro T Model 5 boasts a revamped flight controller equipped with a triple-redundant, thermally regulated inertial measurement unit (IMU). This method, when coupled with a sophisticated vibration isolation system, ensures remarkable flight steadiness even in challenging circumstances, including GPS-denied areas or locations with strong winds. The introduction of a cutting-edge Ethernet interface enables seamless, high-speed data transfer, allowing controllers to oversee complex inspections in real-time and streamline operational efficiency.
The tail motor and propeller have been upgraded to further improve responsiveness and stability, particularly in high-wind conditions. The enhanced controller tuning now provides precise control and stability, enabling more accurate maneuvers during challenging inspections. They urge us to “Experience the difference by taking flight!”
The internal electronics of the Voliro T Model 5 have undergone a comprehensive overhaul to enhance its overall reliability. Newly designed PCBs and precision-engineered antennas ensure a significant boost in efficiency, especially for First-Person View (FPV) cameras, thereby reducing the risk of video stream disruptions during critical inspection periods?
The Voliro T Model 5 features a range of design elements specifically engineered to withstand the challenging conditions typically found during aerial inspections. The shell and structural components utilise premium materials to enhance robustness and reliability in harsh settings. This robust development aims to address the complexities of assessing aging infrastructure, delivering high-temperature services, and optimizing performance at high altitudes.
Extra design enhancements embrace:
To address the demands of extended reconnaissance operations, the Voliro T Model 5 boasts a reduced weight of 250 grams, resulting in enhanced aerodynamics and increased flight duration. These enhancements boost efficiency, enabling operators to cover larger areas without requiring frequent recharging.
The latest design iteration boasts enhanced meeting mechanisms, coupled with reinforced locking systems for the bumpers and tail, allowing operators to effortlessly assemble and disassemble the device according to their needs.
As Voliro further refines its market leadership in non-destructive testing (NDT), the Voliro T Model 5 represents a pivotal milestone in its ongoing quest for excellence. With significant advancements in security, durability, and data management, the Voliro T Model 5 is poised to support industries in tackling the complexities of inspecting critical infrastructure effectively.
As Voliro observes, the pressing need for time-efficient, safe, and reliable inspection solutions will continue to grow, underscoring the importance of our latest model’s release, designed specifically to meet these evolving demands.
Learn extra:
Palletizing plays a crucial role globally, as goods are efficiently stacked and stabilized on pallets for transportation or warehousing purposes. As automation becomes increasingly prevalent, manual palletizing remains a staple in warehousing and manufacturing sectors, where human workers continue to perform these tasks with precision and efficiency.
Despite its prevalence, widespread use of smartphones raises significant health and security concerns that cannot be overlooked?
This article will explore the risks associated with manual palletizing and discuss strategies for minimizing those hazards, ultimately ensuring a safer workplace.
Palletizing activities can lead to elevated levels of stress, fatigue, and anxiety, increasing the risk of developing musculoskeletal disorders.
These MSDs result in a significantly reduced quality of life, persistent disability, and profound psychological distress for employees, ultimately leading to increased absenteeism, turnover, and insurance premiums for employers.
In the United States, supply chain management and logistics are key priorities, particularly when it comes to handling and palletizing materials. In line with the U.S. The Bureau of Labor Statistics (BLS) and the Occupational Safety and Health Administration (OSHA) have found that industries heavily reliant on handbooks for reporting purposes are more likely to experience higher rates of employee accidents.
By the end of 2022, an astonishing 266,530 workplace incidents related to musculoskeletal problems had necessitated time off from duties, underscoring their significant impact on office safety and employee well-being in the year 2023.
Developing an effective plan to minimize hazards associated with palletizing handbooks necessitates a comprehensive approach that transcends traditional load capacities for lifting.
By leveraging instruments such as the Human Capital Index (HCI) and the Composite Lifting Index (CLI), organizations can effectively assess the aggregate physical demands placed on their workforce. These instruments enable industrial and security engineers to devise effective prevention strategies.
By engaging engineering teams early in the threat assessment and mitigation process, you can guarantee the implementation of the most effective and practical security measures. This proactive approach not only boosts employee security but also fosters a healthier and more productive work environment.
By incorporating both semi-automated and fully automated palletizing solutions, businesses can significantly minimize the risks associated with manual palletizing, leveraging technology to efficiently handle repetitive and physically demanding tasks.
While semi-automated palletizing methods rely on a degree of human involvement for tasks such as monitoring and controlling the machinery, the physical labor is primarily handled by the equipment itself.
By adopting this approach, organizations experience increased productivity compared to traditional methods, allowing staff to focus on more complex tasks and reducing the risk of repetitive strain injuries. While semi-automated systems often employ robotic arms or automated conveyors to facilitate stacking and palletizing processes, they still require human involvement to a certain extent.
Automated palletizing solutions significantly reduce human intervention by leveraging advanced robotics to efficiently manage the entire palletizing process independently. These robotic palletizers exhibit a wide range of capabilities.
With advancements in technology, automation is no longer limited to massive industrial manufacturers alone. With advancements in technology, automated palletizing has become a feasible option for companies of all sizes, thanks to the affordability and versatility of collaborative robots. Collaborative robotic palletizers, characterized by their agility, simplicity, and compact footprint, have become increasingly prevalent among small to medium-sized manufacturers, where they facilitate efficient production processes.
By replacing traditional labor-intensive manual handling with advanced robotic palletizers, organizations can significantly enhance office safety while also boosting operational efficiency, thereby minimizing the risk of human error and workplace incidents.
By automating palletizing processes, employees are able to focus on more strategic tasks and drive growth within the organization. A robotic palletizer minimizes reliance on scarce skilled labor, freeing workers from tedious tasks that few are eager to perform.
While handbook palletizing is crucial in numerous industries, its labor-intensive nature and propensity for posing significant health and safety risks to employees make it a pressing concern that requires urgent attention. By acknowledging the risks of accidents and adopting comprehensive strategies to mitigate them, organizations can safeguard their personnel and optimize operational efficiency.
Collaborate closely with your engineering teams to uncover the full potential of automation technologies and leverage them to create a safer work environment for all personnel. As we prioritize security in our daily operations, we can already start reaping the benefits of a healthier work environment tomorrow.
Disney is expanding its artificial intelligence and augmented reality capabilities with an additional layer. According to initial reports, the corporation has recently established a dedicated emerging technologies division. The newly christened Office of Knowledge Enablement will spearhead the corporation’s integration, deployment, and utilization of artificial intelligence, augmented reality, and virtual reality technologies.
The company has brought on board the CTO of its Studios Knowledge division to oversee the issue. Prior to joining Disney in 2010, Voris served as the Chief Technology Officer for the National Football League. Recently, he spearheaded the organization’s most significant event. Voris will provide a report to Alan Bergman, co-Chairman of Disney’s Leisure division. The company ultimately plans to expand its team to approximately 100 employees.
“The pace and scale of AI and XR breakthroughs are revolutionary, poised to transform customer interactions, creative industries, and the corporate landscape for decades to come – emphasizing the need for Disney to seize the exciting opportunities while mitigating potential risks.” “The establishment of this new entity demonstrates our unwavering commitment to fostering responsible usage and promoting best practices as a positive force for change.”
According to a statement from Disney, its Office of Technology Enablement will not absorb existing AI and XR projects currently underway at the company, a spokesperson for the entertainment giant told Engadget. By doing so, it will enable various Disney teams, many of which are currently working on merchandise incorporating such technologies, to align their efforts with the company’s overarching strategic goals.
The organization seeks to intensify its impact by emphasizing coordination, synchronization, and momentum in initiatives, while reiterating its commitment to fostering responsible and exemplary practices that promote accountable usage.
It is safe to say that Disney has likely navigated the last 20 years of technological change more successfully than most of Hollywood, leveraging its early adoption of new platforms and innovative storytelling approaches to maintain its market lead. By leveraging the versatility of their on-set virtual production infrastructure, the company has successfully optimized the creation of visually stunning productions such as sci-fi epics. As technological advancements with AI and prolonged actuality continue to reshape the landscape of work and leisure, it is prudent to implement additional safeguards to ensure responsible deployment of these technologies within the organization.
If you decide to acquire something via a hyperlink in this article, we may receive a commission.
Pixelmator, a company that creates stylish image editing software for both macOS and iOS platforms. While initial reservations lingered about the acquisition, I’m now optimistic that Apple will leverage Pixelmator’s expertise to revive and enhance Aperture.
For those unfamiliar, Aperture was a professional-grade photo editing and management application developed by Apple.
The app competed favourably with industry leaders like Adobe Lightroom by offering a range of features that went beyond mere photo management. Its superior capabilities included the ability to edit images with nuanced control, providing users with a comprehensive toolset for enhancing their visual content. With the launch of Apple’s revamped Images app in 2014, users gained access to a refreshed visual storytelling experience.
Until that point, Apple had shown little to no interest in developing an alternative to Aperture. The company has enhanced its Images app by adding more features and controls, enabling users to quickly adjust parameters such as brightness, shadows, contrast, and sharpness in their photographs for improved visual effects.
The reason I was intrigued by Apple’s acquisition of Pixelmator is that it underscores the company’s commitment to empowering creators. Currently, Pixelmator features a Photo Editor app called Photomator, focusing specifically on photo editing capabilities that directly compete with Adobe Lightroom’s offerings. While I prefer using Photomator extensively, my go-to application is often on the iPad. The app seamlessly integrates with contacts and Apple Pencil capabilities.
I’m not enthused about the revamped Images app in iOS 18; instead, I still prefer editing photos within a dedicated application rather than relying on Apple’s Images. Apple’s acquisition of Pixelmator and Photomator provides an opportunity to revive intelligent image editing software rather than further complicating the Photos app by leveraging their creative expertise.
Pixelmator’s impressive software programme boasts several features that could seamlessly integrate into Apple’s Images app, enhancing its functionality. Apple may introduce AI-powered features similar to Pixelmator’s highly-regarded upscaling capabilities for photographs, a cutting-edge technology that leverages machine learning algorithms. I still hope to see a dedicated app, akin to Aperture in its heyday or Photomator today, that prioritizes photo management and editing with the same level of focus and care.

Pixelmator’s software program remains unchanged for now, pending regulatory approval to seal the deal. The corporation may well discontinue the app, gradually incorporating its technologies into their own proprietary applications.
As Apple continues to drive innovation in mobile computing, Pixelmator’s future under their umbrella likely hinges on strategic refinements to its image editing software. To stay ahead of the curve, consider these potential resolutions: Please provide the text you’d like me to improve. I’ll respond with the revised text in a different style as a professional editor.