A recently disclosed Microsoft SharePoint remote code execution (RCE) vulnerability, identified as CVE-2024-38094, has been actively exploited to gain initial access to corporate networks.
CVE-2024-38094 is a high-severity vulnerability (CVSS v3.1 rating: 7.2) in Microsoft SharePoint, a widely deployed web-based platform serving as an intranet, document administration, and collaboration tool that integrates seamlessly with Microsoft 365 applications.
Microsoft publicly disclosed and patched the vulnerability on July 9, 2024, categorizing it as “essential” within its regular software update.
In the final week of the reporting period, the Cybersecurity and Infrastructure Security Agency (CISA) has added a newly identified vulnerability to its catalog, albeit without providing details on how it was exploited in observed attacks.
According to a newly released report by cybersecurity firm Rapid7, the SharePoint vulnerability has been leveraged in a real-world attack scenario, as revealed through an investigation into a recently disclosed data breach.
Our analysis revealed that an unauthorized actor infiltrated a server, leveraging this foothold to perpetuate malicious activity across the entire network.
The attacker evaded detection for a remarkable two weeks. Rapid7 identified the initial attack vector as the exploitation of a previously unknown vulnerability, designated as CVE-2024-38094, within an organization’s on-premise SharePoint server.
Utilizing AVs to impair safety
As reported by Rapid7, hackers exploited the vulnerability CVE-2024-38094 to breach an insecure SharePoint server, ultimately deploying a web shell for illicit access. The probe discovered that the server had been compromised by exploiting a publicly known vulnerability in SharePoint.
The attackers’ initial foothold was quickly exploited as they successfully breached a Microsoft Alternate service account, acquiring domain administrator-level access and significantly elevating their privileges.
As a result, the attacker installed the Horoung Antivirus, thereby compromising the security defenses and hindering detection capabilities, ultimately enabling the deployment of Impacket for lateral movement purposes.
The attacker employed a batch script, ‘hrword set up.bat’, to deploy Huorong Antivirus on the system, establish a customized service (‘sysdiag’), execute a driver (‘sysdiag_win10.sys’), and initiate ‘HRSword.exe’ via a VBS script.
The flawed setup triggered a series of issues with resource allocation, driver functionality, and energy consumption, ultimately rendering the company’s antivirus software ineffective and powerless.
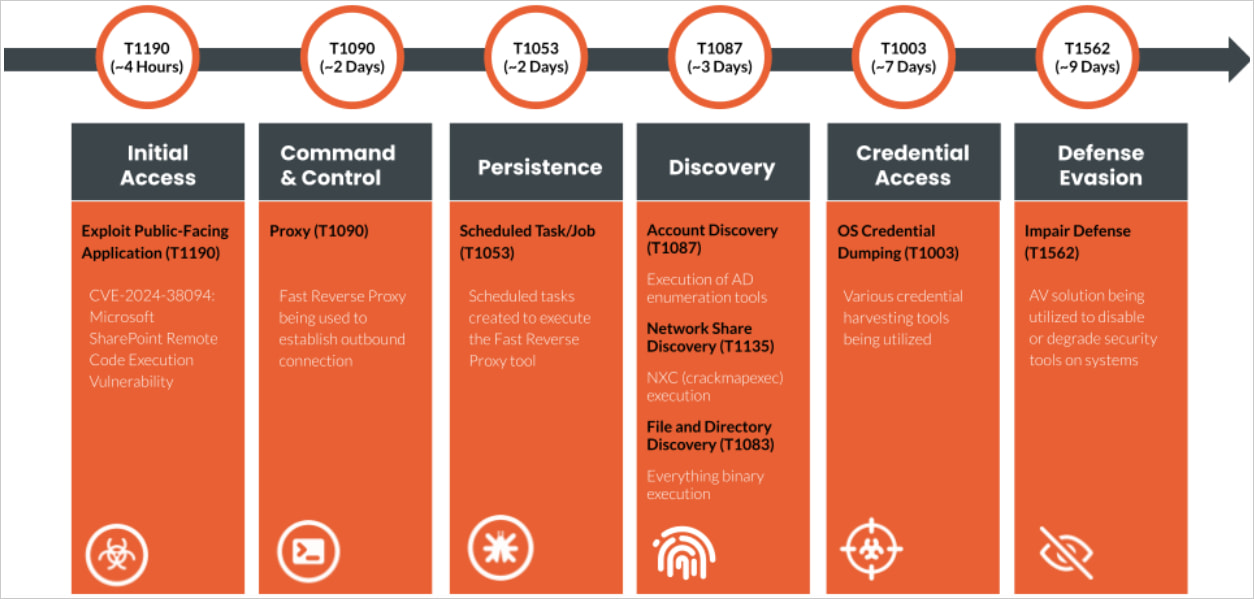
During this phase of the attack, the adversary leveraged Mimikatz to harvest credentials, exploited a vulnerability using FRP to gain remote access, and established persistent access by scheduling recurring tasks.
To evade discovery, attackers had disabled Windows Defender, modified event logs, and tampered with system logging on the infected devices.
The malicious actor leveraged a range of tools, including those similar to Extra instruments, Certify, and Kerbrute, to conduct reconnaissance through network scanning, exploit Active Directory Federation Services (ADFS) certificates, and bruteforce Active Directory service principal names (SPNs).
Despite efforts to destroy third-party backups, the attackers’ attempts to compromise them were unsuccessful.
Although attempting to erase backups is a common tactic employed by ransomware attackers to prevent easy recovery, Rapid7’s failure to detect information encryption means the type of attack remains uncertain.
As energy-intensive exploitation accelerates, system administrators who have yet to implement SharePoint updates since June 2024 must take swift action to do so without delay.