When Nikola Tesla envisioned handheld telephones capable of displaying movies, images, and more, his predictions seemed like a far-fetched fantasy. Nearly a century on, smartphones have become an integral extension of the human body for countless individuals.
Digital fabrication engineers continually strive to enhance the aesthetic appeal of everyday items. To help consumers access crucial information, such as health metrics, and explore novel designs for everyday items like walls, mugs, and shoes, researchers are investigating reprogrammable surfaces that can be digitally altered at will.
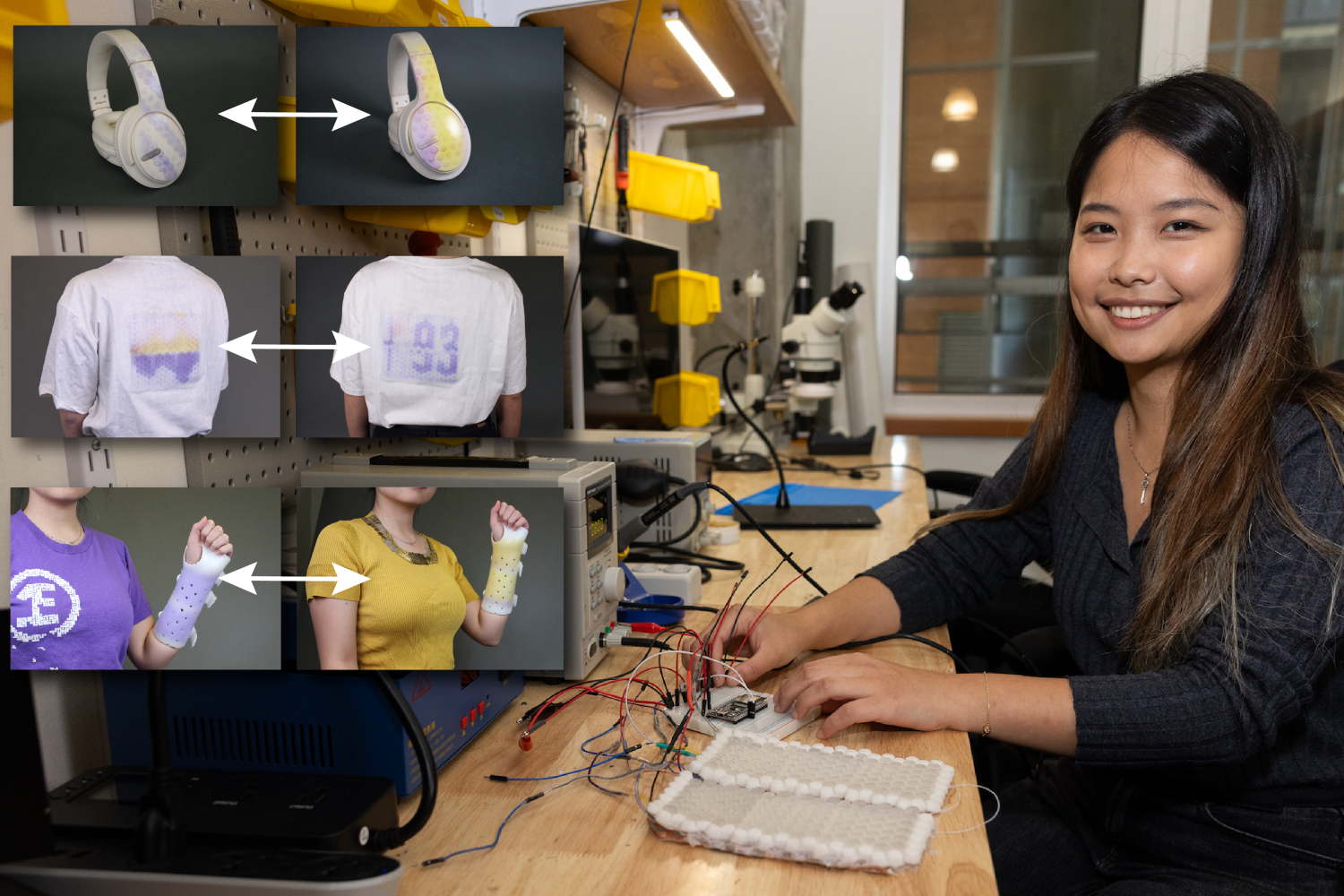
Scientists from MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) in collaboration with the University of California at Berkeley and Aarhus University have made significant progress by developing “SmartSkin,” a portable light system and design tool capable of altering the color and texture of various objects. Equipped with ultraviolet (UV), pink, inexperienced, and blue (RGB) light-emitting diodes (LEDs), this device can be integrated into everyday items such as clothing and accessories like shirts and headphones. Once a customer designs a pattern using their phone or tablet and wirelessly transfers it to a PortaChrome device via Bluetooth connectivity, the floor can be transformed into a vibrant display showcasing personalized health data, entertainment, and fashion designs.
To render a product reprogrammable, it must be treated with photochromic dye, an invisible ink capable of transforming into distinct colors in response to varying light patterns. As soon as coating is complete, users can generate and transmit custom patterns to the product through our graphic design software, or seamlessly integrate with our API to create real-time, data-driven designs directly on the device. Connected to a floor, PortaChrome’s UV lights intensify the dye, while RGB LEDs neutralize it, thereby activating the desired colors and ensuring each pixel is precisely calibrated to match the intended design.
Researchers led by Zhu achieved remarkable speed boosts in colour adjustment, processing objects’ hues in under 4 minutes on average – an unprecedented eightfold acceleration compared to their previous work. This marked velocity increase stems from the adoption of a lightweight sensor that physically interacts with the object to transmit UV and RGB light signals. By employing a projector, Picture-Chromeleon harnessed the power of photochromic dye to unlock its colour-shifting properties, as long as sunlight was cast upon the object’s surface at a shallow angle.
Yunyi Zhu, an MIT Ph.D. student in electrical engineering and computer science, affiliated with the Computer Science and Artificial Intelligence Laboratory (CSAIL), notes that PortaChrome offers a practical technique for reprogramming one’s environment. Unlike our earlier projector-based system, the PortaChrome is a more portable light source that can be placed directly atop the photochromic surface. This feature allows for seamless color changes without requiring consumer involvement, thereby preventing environmental contamination caused by UV exposure. As a result, customers can affix their heart rate charts to their shirts following a workout.
During demonstrations, PortaChrome successfully showcased vital health data on a wide range of unconventional surfaces. As a consumer ventured out on a hike, they carefully secured their PortaChrome to their backpack, positioning it directly against the back of their shirt, which had been treated with photochromic dye? Researchers designed a system in which altitude and coronary heart rate sensors transmitted data to a lighting device, which was subsequently converted into a chart through a reprogramming script they developed. The course enables students to create a wellbeing visualization on the back of the customer’s shirt. Researchers at MIT showcased a cutting-edge visualisation technique, where a user’s cardiovascular progress toward a specific goal was represented through the gradual assembly of a virtual pill, displayed in real-time on a digital platform.
PortaChrome has further validated its ability to tailor wearables to specific requirements. Researchers rebranded existing white headphones by adding distinctive blue patterns that run perpendicular to the ear cups, alongside vibrant horizontal stripes in shades of yellow and purple. The photochromic dye was applied to the headphones, after which the workforce connected the PortaChrome device inside the headphone casing. The scientists successfully transferred their designs onto the object, resulting in a vibrant, watercolor-like aesthetic. Researchers successfully adapted a wrist splint by dyeing it to match various clothing items through this process.
The possibility exists that this project’s outcome could be utilized to digitally catalogue consumers’ personal items. Envision adorning yourself with a cloak that can dramatically alter the overall aesthetic of your attire, much like accessorizing with a scarf that redefines the style of your entire outfit, or consider applying a vinyl wrap to give your vehicle a fresh and modern appearance.
On the hardware front, PortaChrome is comprised of four fundamental components. The product features a textile-based framework serving as a backbone, overlaid with two distinct layers: the first, embedded with UV LEDs, and the second, fitted with RGB LEDs; the assembly is capped by a silicone diffusion layer, optimizing its overall performance. As a delicate mesh of transparent honeycomb, the silicone layer encapsulates the intricate network of UV and RGB LEDs, skillfully redirecting their illumination toward precise pixels on the floor to accurately render a desired design.
The gadget’s flexible design allows for effortless wrapping around objects of diverse shapes. For tables and various flat surfaces, consider placing PortaChrome directly onto the surface like a placemat, ensuring a secure fit. To protect your curved merchandise, such as a thermos, consider wrapping sunshine-colored supplies around it like an espresso cup sleeve, ensuring a snug fit and complete coverage of its surface.
The adaptable and flexible mild system is designed using readily available tools found in maker spaces, such as laser cutters; similarly, the same approach can be replicated with versatile printed circuit board (PCB) materials and other mass production techniques.
While it could potentially rapidly transform our surroundings into interactive displays, researchers including Zhu propose that it could benefit from further acceleration enhancements. To enable rapid reconfiguration of a high-definition floor design, they seek to integrate smaller LEDs, potentially leading to an upgraded visual experience with increased brightness and precision.
Researchers posit that the surfaces we encounter daily are imbued with rich sensory cues – colours and textures – which transmit vital information and influence our interactions with them. PortaChrome is revolutionizing the concept of reprogrammable surfaces by seamlessly integrating UV and RGB LEDs with photochromic pigments into everyday objects, effectively pixelating their surroundings with dynamic shading and pattern capabilities. PortaChrome’s innovative capabilities have the potential to transform our collaboration with the environment, particularly in fields such as bespoke fashion and responsive consumer interactions. This expertise enables real-time personalization that effortlessly merges with daily routines, offering a preview of the future of ubiquitous entertainment.
Zhu is accompanied by nine CSAIL associates on this paper, including MIT PhD student and MIT Media Lab affiliate Cedric Honnet; as well as former visiting undergraduate researchers Yixiao Kang and Angelina J. Zheng and Grace Tang are joined by a distinguished group of experts, including MIT undergraduate student Luca Musk; Junyi Zhu, Assistant Professor at the University of Michigan (SM ’19, PhD ’24); postdoctoral researcher and Aarhus University Assistant Professor Michael Wessely; and senior writer Stefanie Mueller, TIBCO Professional Development Affiliate Professor in MIT’s departments of Electrical Engineering and Computer Science and Mechanical Engineering, as well as Chief of the HCI Engineering Group at CSAIL.
This work was funded by the MIT-GIST Joint Analysis Program and presented at the ACM Symposium on Consumer Interface Software and Technology in October.