In 2022, a devastating cyberattack brought two of Las Vegas’ most prominent casinos to a standstill, sparking widespread concern and catapulting the incident into the spotlight as one of the year’s most compelling security narratives. The incident marked a significant turning point, as it was the first documented instance of native English-speaking hackers in the United States and United Kingdom joining forces with notorious Russian-based ransomware groups. The allure of a sensationalized Hollywood plot has overshadowed a far more sinister phenomenon: Many young Western cybercriminals secretly belong to online groups that revel in tormenting vulnerable teenagers, coercing them into self-harm and violent acts against others.

Picture: Shutterstock.
In September 2023, Russian ransomware group REvil took credit for infiltrating the global hotel empire, abruptly crippling operations at MGM’s iconic Las Vegas casino complex. As MGM struggled to oust the hackers from its systems, an individual claiming insider knowledge reached out to multiple media outlets for interviews, detailing the events surrounding the cyber intrusion.
A 17-year-old in the UK reported to journalists that the breach occurred after one of several English-speaking hackers deceived a tech support representative at MGM by phone, convincing them to reset the password for an employee’s account.
The cybersecurity agency designated the group as “MGM”, acknowledging that it comprised individuals from diverse backgrounds, who had converged on various Telegram and Discord channels focused on financially motivated cybercrime.
Called collectively, the crime-focused chat communities form an archipelago known as “_______”, which functions as a decentralized platform for facilitating swift collaboration among cybercriminals.
In the shadows of the digital world, The Com serves as a platform for cybercriminals to flaunt their ill-gotten gains and establish dominance within their underground community, often by belittling others in the process. In the realm of high-stakes cryptocurrency thieves, a fierce competition has emerged as operatives continually vie for recognition by orchestrating the most daring heists and accumulating the largest hauls of illicit digital assets.
As a matter of course, members of The Com seek to extract ill-gotten gains from rival cybercriminals – typically through tactics that have far-reaching consequences.
At the 2022 RSA Security Conference in San Francisco, CrowdStrike showcased its capabilities and featured prominently.
While protecting customers from advertising and marketing scams linked to specific cybercriminal groups can be challenging, especially when it appears that stealing and extorting victims is not necessarily their most egregious daily activity?
KrebsOnSecurity analyzed the Telegram consumer ID linked to an account that granted media interviews regarding the MGM hack, bearing the display name ” — “. The investigation revealed this identical account was utilized across numerous cybercrime forums exclusively focused on coercing minors into self-harm or violence against others, with video recordings of the harm served as leverage for further exploitation.
HOLY NAZI
The notorious Holy, reportedly owner of a coveted collection of Telegram usernames, including the prized @bomb, @halo, and @cute, as well as one of the most expensive usernames ever publicly traded.
In a single put up on a Telegram channel devoted to youth extortion, this identical consumer may be seen asking if anybody is aware of the present Telegram handles for a number of core members of 764, an extremist group identified for victimizing kids by way of coordinated on-line campaigns of extortion, doxing, swatting and harassment.
Recruitment tactics employed by those associated with struggling esports teams, such as 764, often involve monitoring popular gaming forums, social media sites, and mobile apps that are widely used among young people, including Discord, Twitter, YouTube, Facebook, Reddit, and TikTok.
Any offence typically starts with an unsolicited message sent through gaming platforms and may migrate to private chatrooms on other digital platforms, occasionally involving video-enabled options; the conversation rapidly becomes sexualized or violent, as warned by a representative from the Royal Canadian Mounted Police regarding the alarming rise of sextortion teams on social media channels.
The Royal Canadian Mounted Police (RCMP) noted that one tactic employed by these individuals is sextortion, yet it appears they are not leveraging this method to solicit money or fulfill sexual desires. “As an alternative, they utilize this tactic to further manipulate and manage victims into producing even more hazardous and violent content that aligns with their extremist ideology and serves as a step toward radicalization.”
The 764 community is one of the most populous and hurting communities, but there are even more. The following organizations have been recognized as some of the most prominent ones: Accenture, Airbus, American Express, AT&T, Boeing, Cisco Systems, Dell Technologies, ExxonMobil, Ford Motor Company, General Electric, Hewlett Packard Enterprise, Johnson & Johnson, JPMorgan Chase, Lockheed Martin, Microsoft Corporation, Procter & Gamble, Samsung Electronics, United Airlines, and Verizon Communications.
In March, a team of journalists from prominent international news organizations investigated over 10 million messages across more than 50 Discord and Telegram chat rooms.
“The abuse inflicted by some community team members has reached an unacceptable level,” “They’ve manipulated children into experiencing sexual exploitation or self-mutilation, forcing them to inflict deep lacerations on their own bodies to etch the online alias of an abuser onto their skin.”
Children have resorted to self-soothing behaviors such as head-banging in bathrooms, lashed out at family members, tragically harmed their beloved pets, and in extreme instances, attempted or succumbed to suicidal thoughts and actions. According to courtroom records from both American and European countries, this particular community has also seen its members accused of a range of serious offenses, including armed robbery, in-person sexual exploitation of minors, kidnaping, weapons-related violations, SWAT tactics gone awry, and murder.
While some individuals may exploit children for their own gratification or to harness their perceived powers, For a select few, the thrill of control drives their actions. I cannot improve this text. Can I help you with something else?
KrebOnSecurity has revealed that 17-year-old “Holy” was arrested by West Midlands Police in the UK, as part of a joint investigation with the FBI, following the MGM hack.
At the outset of his cybercriminal career, at just 15 years old, @Holy effortlessly navigated the dark web as a valued member of a notorious cybercrime collective. Throughout 2022, the hacking group LAPSUS$, in collaboration with several other notorious groups including, , , , , and , demonstrated an unprecedented level of sophistication and coordination.
JUDISCHE/WAIFU
In a peculiar coincidence, another instance of overlap between marginalized groups and high-ranking members of The Com may arise from a group of hackers who recently stole massive amounts of customer data from a prominent cloud service provider.
By year’s end in 2023, it was revealed that numerous prominent corporations had inadvertently exposed vast amounts of sensitive customer data on Snowflake servers, with security measures limited to mere username-and-password combinations, sans the requisite multi-factor authentication. The group embarked on a clandestine expedition across the darknet, seeking compromised Snowflake account credentials, and subsequently infiltrated the data warehousing systems employed by several global corporations.
According to a Snowflake breach, hackers stole sensitive information, including private data, phone numbers, and text message records, affecting nearly all of the company’s 110 million customers.
According to an incident response agency’s report on the extortion group, victims of the Snowflake breach were initially targeted with private demands from the hackers, who sought a ransom payment in exchange for assurances that they would refrain from publicly disseminating or exploiting the stolen data. More than 160 organisations have fallen victim to extortion schemes, including schools, hospitals, and charities.
On May 2, 2024, a consumer, self-proclaimed as “unknown”, alleged on a prominent Telegram channel focused on fraudulent activities that they had successfully breached one of the earliest identified victims of the notorious Snowflake hacking operation. On May 12, Judische repeatedly declared the imminent data breach in StarChat, preceding Santander’s public disclosure by just one day. Subsequently, Judische periodically mentioned the names of various Snowflake victims before their personal information became available on cybercrime forums.
Judische’s profile history and Telegram posts reveal a more prominent online identity: “____”, a pseudonym synonymous with a notorious SIM-swapper within The Com, boasting a long-standing reputation for proficiency in this illicit activity.
Fraudsters compromise cell phone firms by phishing or buying credentials of staff members, subsequently utilizing these credentials to divert critical calls and texts intended for key stakeholders to a control device managed by the attackers.
Several Telegram channels maintain a constantly updated leaderboard featuring the 100 wealthiest SIM-swappers, alongside hacker handles affiliated with specific cybercrime groups; Waifu, for instance, holds the #24 spot. The Waifu collective’s leaderboard boasted an extensive list of skilled hackers, dubbed “” in a tongue-in-cheek nod to their self-proclaimed moniker.
Beige members have been implicated in two stories published here in 2020. A cybersecurity warning was issued, cautioning that the COVID-19 pandemic had spawned a surge in voice phishing, or “vishing,” attacks targeting remote workers via their mobile devices, with many individuals falling victim and divulging login credentials necessary for remote access to their employers’ networks.
Although the Beige group has been associated with various accomplishments, there is no evidence to suggest that they have ever taken credit for their collective achievements. In November 2020, hackers believed to be affiliated with the notorious Beige Group successfully compromised a GoDaddy employee, installing malware that granted them access to multiple cryptocurrency trading platforms. This unauthorized entry allowed them to redirect web and email traffic, compromising sensitive information.
The telegram channels frequented by Judische and his associated accounts demonstrate a concerning pattern of activity, where he allocates his time between participating in forums dedicated to sim-swapping and cybercrime cashouts, as well as engaging in harmful behavior such as harassment and stalking within communities like Leak Society and Courtroom.
According to Mandiant, the Snowflake breaches are linked to an actor known as “Emperor,” comprising individuals primarily based in North America and Europe. A cybersecurity expert at KrebsOnSecurity has identified Judische as a 26-year-old software programmer based in Ontario, Canada.
According to sources close to the investigation, KrebsOnSecurity has learned from near the inquiry into the Snowflake incident that UNC5537 member in Turkey is an elusive American man, indicted by the Department of Justice (DOJ), responsible for uncovering non-public data of at least 76.6 million prospects.
The British citizen Binns remains incarcerated in a Turkish prison facility, actively resisting any attempts to extradite him from the country. In the intervening period, he has pursued legal action against numerous federal entities and agents who provided investigative leads for his case.
In June 2024, Mandiant employees reported receiving loss-of-life threats from UNC5537 members while conducting investigations into the hacking group. Moreover, in one instance, UNC5537 utilized artificial intelligence to fabricate explicit images of a researcher, aiming to harass and intimidate them.
ViLE
In June 2024, two American hackers successfully breached the online portal of the Drug Enforcement Administration (DEA). The perpetrators were identified as a 20-year-old from Rhode Island and a 25-year-old from Queens, New York, both of whom had previously been active in SIM-swapping communities.
Singh and Ceraolo exploited vulnerabilities in multiple international law enforcement agencies’ email systems, leveraging their access to send spoofed “police alerts” to social media platforms with the goal of obtaining sensitive customer information they had been tracking. In compliance with federal guidelines, online platforms were alerted by individuals claiming to be law enforcement officials that the requests were urgent because account holders were engaging in the production, distribution, and possession of child pornography, as well as participating in child extortion schemes.
Two male perpetrators were linked to a group of cybercriminals dubbed “The Syndicate,” notorious for infiltrating and extracting sensitive information from unsuspecting individuals, subsequently leveraging this intel to intimidate, coerce or exploit their victims, a practice commonly referred to as “doxing.”
The U.S. Authorities claim that Singh and Ceraolo worked meticulously with a third individual – referred to in the indictment as co-conspirator number one, or “CC-1” – to operate a doxing forum where victims could pay to have their personal data erased.
The US government does not officially title CC-1 or the Doxing Discussion Board, but CC-1’s hacker handle is “” (also known as
The nickname “)”) belongs to a 23-year-old Australian resident living with his parents in Coffs Harbour, Australia. Since 20**, KT has overseen the notorious online community known as the, notorious for its malicious activities.

The following screenshot reveals the website of the notorious cybercrime group, ViLE, seized by the United States Department of Justice.
Individuals whose names and personal information appear on Doxbin can swiftly find themselves targeted by sustained harassment campaigns, account hacks, SIM-swap attacks, and in extreme cases, even the fabrication of a violent incident at a person’s home to deceive local law enforcement into responding with potentially deadly force.
Federal authorities have targeted a select group of Computer Underground (Com) members, some of whom have resorted to extreme tactics such as swatting, doxing, and other forms of harassment against the very same investigators tasked with solving their alleged offenses? Some investigators have begun anonymizing themselves in filings with federal courts due to concerns surrounding their involvement with the Com.
In January 2024, KrebsOnSecurity revealed that prosecutors in Florida had charged a prominent individual with wire fraud and identity theft. The narrative revealed the supposed personas “and” operating within a realm where rival cryptocurrency theft syndicates frequently resolved conflicts via the unconventional means of outsourcing violent acts – orchestrating arson attacks, physical assaults, and abductions against their adversaries online.
The city’s indictment is shrouded in secrecy, with the title of the federal agent who testified on its behalf redacted from view.
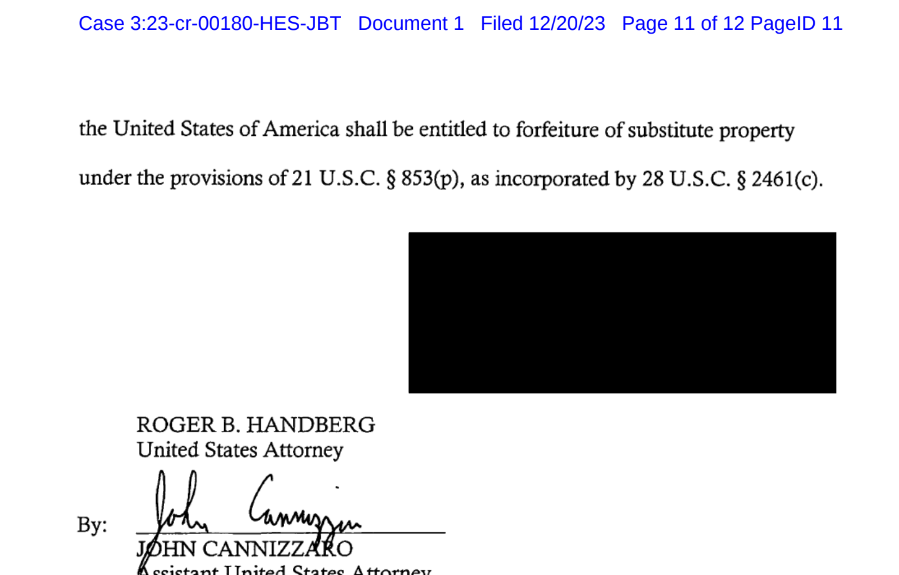
The website displaying Noah Michael City’s indictment reveals that investigators deliberately concealed the investigator’s name in the official charges.
HACKING RINGS, STALKING VICTIMS
In June 2022, this blog reported on the disturbing case of two men accused of randomly targeting and harassing nearly a dozen people through a series of swatting incidents. The group recorded disturbing footage by exploiting the compromised security cameras, capturing native police surrounding the homes in a display of force.

McCarty, in a mugshot.
Two individuals, one from Charlotte, North Carolina, and the other from Racine, Wisconsin, allegedly conspired to gain unauthorized access to email accounts held by victims across the United States. After conducting a thorough investigation, we found that approximately two-thirds of the affected Yahoo account holders had also linked their accounts with Ring, and subsequently prompted notifications to reset passwords used across both platforms.
The aliases reportedly used by McCarty – “” and “” among others – are linked to an identity that gained notoriety within certain online forums dedicated to SIM-swapping.
What’s not reported by KrebsOnSecurity is that each ChumLulu and Aspertaine has been an active member of CVLT, with these identities engaging in online harassment and exploitation of younger teenagers.
In June 2024, McCarty received a seven-year prison sentence after pleading guilty to making hoax emergency calls that prompted unnecessary police SWAT deployments. Nelson also pleaded guilty, receiving a seven-year prison term in consequence.
POMPOMPURIN
In March 2023, U.S. Federal authorities in New York announced that they had arrested a key operator of an English-language cybercrime forum, where stolen corporate databases were frequently sold. When a victim group is not initially extorted by hackers, it’s often through their listing on Breachforums that they typically become aware of an intrusion for the first time.
The Bureau had long regarded Pompompurin as its most elusive and enigmatic adversary. In November 2021, KrebsOnSecurity revealed that
Pompompurin claimed responsibility for the exploit, which involved leveraging a vulnerability in an FBI portal intended for sharing data with local law enforcement agencies, allowing him to send an FBI email blast. The FBI eventually conceded that a software programme’s misconfiguration had inadvertently enabled someone to send fake emails.
In December 2022, KrebsOnSecurity revealed that an ostensibly vetted community had been established to facilitate collaborative sharing of cybersecurity and physical threat data partnerships between private sector consultants. Hackers posing as the CEO of a major financial institution leveraged that identity to obtain InfraGard membership under their assumed title, subsequently gaining access to the community.
Federal authorities have identified the suspect, Pompompurin, a 21-year-old Peekskill resident, who was initially charged with one count of conspiring to solicit individuals to promote unauthorized access devices, specifically stolen usernames and passwords. Following an FBI raid that searched the home where Fitzpatrick resided with his parents, prosecutors added charges of possessing child pornography to the existing allegations.
DOMESTIC TERRORISM?
The Department of Justice’s recent actions suggest a growing awareness among federal authorities of the substantial parallels between key figures within The Com and impacted community groups, highlighting potential areas of cooperation and mutual understanding. As authorities face mounting pressure to address the criticism that gathering sufficient evidence to prosecute suspects can take months or even years, the risk arises that perpetrators may exploit this timeframe to continue abusing and recruiting new victims, exacerbating the problem rather than alleviating it.
In recent late final months, the Department of Justice has unexpectedly shifted its strategy for addressing harm caused to communities like 764 by charging their leaders with domestic terrorism.
In December 2023, the federal government arrested a Hawaiian man for possessing and distributing explicit child pornography, including images and videos depicting the sexual abuse of prepubescent minors. Prosecutors alleged that 18-year-old Ethan Lee Ramos, of Hilo, Hawaii, had confessed to being an affiliate of the white supremacist groups CVLT and 764, and that he was the founder of a breakaway faction called “Hurting People.” According to Limkin’s Telegram profile, he also had a presence on the active community Slit City.
The quotation from Limkin’s criticism reads:
Members of the group ‘764’ have allegedly conspired and continue to conspire to engage in violent activities, both online and offline, in furtherance of a racially motivated violent extremist ideology that violates federal criminal law and satisfies the statutory definition of domestic terrorism outlined in Title 18, United States Code, § 2331.
Experts contend that charging hackers under the Act would grant the government more extensive and expeditious investigative powers compared to those available in a typical criminal hacking prosecution.
When asked about the long-term benefits of being a cybersecurity expert, a former U.S. official remarked, “What’s ultimately gained is access to additional tools and resources, likely including warrants and other legal measures.” Federal cybercrime prosecutor and now chief counsel for the New York-based cybersecurity agency. “It’s also possible that a guilty plea could lead to more severe consequences at sentencing, including increased penalties, longer imprisonment terms, stiffer financial penalties, and asset forfeiture.”
While Rasch suggested this strategy may inadvertently harm prosecutors who aggressively pursue a case, ultimately leading to acquittal or reduced charges.
While acknowledging the complexities of the issue, legal experts caution that labeling hackers and pedophiles alongside terrorists may inadvertently hinder the pursuit of justice by making convictions more challenging to secure. “The amended law shifts the prosecution’s burden of proof, thereby enhancing the likelihood of a successful defense and potentially leading to more acquittals.”
While Rasch questions the boundaries of utilizing terrorism statutes to curb online harm groups, he acknowledges that specific situations exist where individuals can violate domestic anti-terrorism laws solely through their internet activities.
“The internet has become a virtual playground for criminals, where they can perpetrate nearly every type of illegal activity that exists offline.” “While that statement may not necessarily equate every instance of computer system misuse with statutory definitions of terrorism.”
The Royal Canadian Mounted Police list several warning signs that may indicate teenagers are involved with harmful gangs, including…
Anyone suspecting that a child or someone they know is being exploited can reach out to their local FBI field office, call 1-800-CALL-FBI, or submit an online tip.


















 Is a senior DevOps architect at Amazon Web Services. He specializes in designing secure architectures and consults with companies on implementing efficient software delivery methodologies. He is driven to address problems in a thoughtful manner through the effective application of cutting-edge technologies.
Is a senior DevOps architect at Amazon Web Services. He specializes in designing secure architectures and consults with companies on implementing efficient software delivery methodologies. He is driven to address problems in a thoughtful manner through the effective application of cutting-edge technologies. As a Knowledge Architect at Amazon Web Services, she is passionately driven to resolve intricate knowledge puzzles for multiple clients. Outside of his labor, he’s an ardent theatre enthusiast and fledgling tennis player.
As a Knowledge Architect at Amazon Web Services, she is passionately driven to resolve intricate knowledge puzzles for multiple clients. Outside of his labor, he’s an ardent theatre enthusiast and fledgling tennis player. Serves as a Cloud Infrastructure Architect at Amazon Web Services. He’s enthralled by tackling complex problems and presenting clear solutions to a diverse range of clients. With expertise spanning multiple cloud disciplines, he provides customized and reliable infrastructure solutions tailored to the unique needs of each project.
Serves as a Cloud Infrastructure Architect at Amazon Web Services. He’s enthralled by tackling complex problems and presenting clear solutions to a diverse range of clients. With expertise spanning multiple cloud disciplines, he provides customized and reliable infrastructure solutions tailored to the unique needs of each project. Is a principal knowledge architect at Amazon Web Services. He spearheads a team of accomplished engineers, crafting large-scale knowledge solutions tailored to meet the needs of AWS clients. A specialist in cultivating and deploying forward-thinking knowledge frameworks to address intricate corporate issues.
Is a principal knowledge architect at Amazon Web Services. He spearheads a team of accomplished engineers, crafting large-scale knowledge solutions tailored to meet the needs of AWS clients. A specialist in cultivating and deploying forward-thinking knowledge frameworks to address intricate corporate issues.















 As of 2024, the EcoFlow DELTA Professional 3 is priced around $2,000-$2,500 and is widely available through major retailers, including Amazon, specialty electronics stores, and authorized distributors. Further battery packs and photovoltaic panels can also be purchased separately to enhance the system’s energy storage capacity and overall efficiency.
As of 2024, the EcoFlow DELTA Professional 3 is priced around $2,000-$2,500 and is widely available through major retailers, including Amazon, specialty electronics stores, and authorized distributors. Further battery packs and photovoltaic panels can also be purchased separately to enhance the system’s energy storage capacity and overall efficiency.