At Lenovo’s event, the company showcased its cutting-edge AI-driven innovations, emphasizing their superior capabilities tailored to enhance productivity for modern professionals. The mannequin is a component of Lenovo’s latest assortment designed to seamlessly integrate artificial intelligence capabilities with advanced computing requirements.
The Lenovo ThinkBook 16 Gen 7 stands out for its unique combination of a Snapdragon X Plus 8-core processor, marking an innovative departure from traditional CPU choices. The processor boasts a dedicated Neural Processing Unit (NPU), delivering up to 45 trillion operations per second, significantly enhancing the laptop’s artificial intelligence capabilities. This feature enables eco-friendly native AI processing, thereby enriching capabilities such as the Assembly Assistant for enhanced teamwork and productivity.

With its sleek and contemporary design, the ThinkBook 16 Gen 7 sports a stylishly slim profile of just 16mm in thickness. The device features a large 16-inch display with an impressive screen-to-body ratio of 91.3%, providing an incredibly immersive viewing experience. The laptop boasts an expansive TouchPad and advanced audio capabilities, including Lenovo’s Professional Sound and Dolby Atmos, ensuring seamless productivity and entertainment experiences.
The portable gadget features a lightweight design and an 84Wh battery, ensuring extended usage. Combining robust efficiency with enterprise-grade security, the solution features hardware-enabled safety measures and leverages Microsoft’s Pluton chip-to-cloud expertise to ensure secure identity and cryptography capabilities.
| Function | Particulars |
|---|---|
| Show | Here is the rewritten text: A 16″ 16:10 WQXGA IPS display boasts a 2.5K resolution, 100% sRGB colour accuracy, and an ambient light sensor (AG) with a brightness of 350 nits. Additionally, there’s also a 16″ 16:10 WUXGA IPS display option with a 60Hz refresh rate, covering 45% of the NTSC colour gamut at a brightness of 300 nits, again featuring an ambient light sensor (AG). The screen-to-border ratio is a generous 91.3%. |
| Processor | Snapdragon X Plus 8-core |
| NPU | Qualcomm Hexagon NPU (45 TOPS) |
| Reminiscence | Up to 32GB of high-performance LPDDR5x memory, operating at speeds of up to 8448 MT/s in a dual-channel configuration. |
| Graphics | Built-in Qualcomm Adreno |
| Working System | Windows 11 Pro |
| Digital camera | FHD RGB digital camera with webcam privacy shutter. |
| Storage | What high-capacity storage needs do you have? Consider a robust 1TB PCIe Gen4 x4 SSD for lightning-fast data transfer and massive storage. |
| Battery | 84Whr |
| AC Adaptor | 65W USB Kind-C 3pin |
| Audio | What’s the Sound Like with Dolby Atmos? Two Times the Power |
| Enter/Output Ports | Two x USB-C, supporting up to 10 Gbps speeds at full performance; two x USB-A, with one facilitating Audio Output Unit (AOU) functionality, operating at 5 Gbps; one x HDMI 2.1 port featuring TMDS technology; one x Audio combo jack for simultaneous headphone and microphone usage; and one x SD card reader accommodating 4-in-1 media formats. |
| Wi-fi | Wi-Fi 7 |
| Software program | Lenovo Smart Assembly; Lenovo Vantage; McAfee LiveSafe (free trial); Microsoft Workplace 365 (evaluation) |
| Specifications: Dimensions 12.5 cm x 8.5 cm x 1.6 cm (4.92 in x 3.35 in x 0.63 in) | 356.4 x 248.4 x 16.7 mm (or 14.0 x 9.8 x 0.66 inches) |
| Weight | Starting at approximately 1.82 kilograms (or 4.02 pounds). |
| MIL-STD-810H | Sure |
| Keyboard | Accessibility options include ribbed keys for enhanced tactile feedback; a backlit keyboard with dedicated quantity keys ensures seamless navigation even in low-light environments. |
| Colour | Luna Gray |
The ThinkBook 16 Gen 7 is expected to launch in October 2024, initially priced at $***, reflecting Lenovo’s commitment to merging innovative AI technology with user-focused design to meet the dynamic needs of business professionals.
Filed in . What are the nuances of mastering? How do I develop skills for achieving?

Apple has officially confirmed that this major announcement will take place on September 16th. The roll-out introduces numerous enhancements, yet some clients may hesitate to implement them immediately to avoid potential issues and ensure seamless integration with required software applications. As a result, Apple will permit customers to continue using iOS 17, ensuring they receive essential security updates and maintenance.
The company simultaneously released its latest offering to the general public on Monday, also unveiling a new iOS 17.7 Release Candidate (RC) for developers and public beta testers. The update appears to provide necessary security enhancements and bug fixes for iOS 17, without introducing new features or functionalities.
Apple is likely to release both iOS 17.7 and the forthcoming iOS 18.0 simultaneously next week. Customers will be notified of each update via the Settings app, where they can choose to stay on iOS 17 and receive only the latest security patches or upgrade to iOS 18 for access to new features. It’s worth noting that this isn’t the first time Apple has offered customers this option.
In its final year, Apple persisted in releasing security updates for iOS 16 even after the introduction of iOS 17, demonstrating a commitment to ongoing support and maintenance. Despite reaching a certain threshold, these patches were ultimately released only for devices unable to upgrade to iOS 17. As iOS 18 becomes widely adopted, Apple is expected to halt support for iOS 17 in the near future, as new updates typically only receive compatibility with the latest operating system version.
Keeping the option to choose between different models of a working system helps prevent certain bugs by allowing users to opt for apps that are fully compatible with the chosen iOS version, including iOS 18.
Apple is poised to unveil a slew of new operating systems next week, including iPadOS 18, watchOS 11, tvOS 18, visionOS 2, and the highly anticipated macOS Sequoia alongside iOS 18?
As Samsung successfully debuted its key telephone launches this year, the fan-favorite variant of its flagship series remains pending in the pipeline. As we eagerly anticipate the launch, a fresh leak has surfaced, unveiling the device’s design and several intriguing specifications.
The total gallery of photographs can be viewed at [website], where Samsung has released images of the upcoming Galaxy S24 FE’s colour options, showcasing the device in hues of blue, graphite, green, and yellow. According to leaked renders, Samsung’s new mid-range smartphone will showcase a striking, edge-to-edge design reminiscent of its high-end flagships, departing significantly from its curved-edged predecessor.

The brand’s new design appears to be a refreshing departure, with its palette of colours displaying encouraging signs. While graphite’s unique hue may appear captivating compared to standard blacks, the combination of blue and green appears relatively ordinary. Samsung has introduced Yellow as a fresh colour option for the Galaxy S24 FE, following its recent launch of a similar hue for another device.
The publication highlighted a mere five colors, with the silver option appearing somewhat underwhelming. Despite being showcased in the featured picture, the additional display also highlighted the machine’s colour options. Samsung will offer its new device in five distinct colour options when it hits the market.
Each side of the machine, aside from the colours, may feature a glass surface once more. The device will feature a sleek display with negligible punch gaps and ultra-thin bezels, precisely measuring 1.99 millimeters. The upcoming display is expected to measure approximately 6.7 inches in size, featuring a Full HD+ resolution and a 120Hz refresh rate. The expected peak brightness is anticipated to reach approximately 1900 nits, potentially backed by the robust protection of Corning Gorilla Glass Victus+.
Specs for a few models were prematurely revealed through promotional images released earlier. The device features a triplet of rear cameras: a primary 50-megapixel sensor, a 12-megapixel ultra-wide-angle lens, and an 8-megapixel telephoto sensor.
Samsung Galaxy S24 FE, listed on Wi-Fi Alliance website, boasts 15W Wi-Fi charging and 25W wired charging capabilities.⚡ #Samsung #GalaxyS24FE
The Samsung Galaxy S24 FE, with model number SM-S721U, has listed on the Wi-Fi Alliance website, according to a tip from Abhishek Yadav. Following this. The WPC has verified not only the Wi-Fi and wired charging speeds of the machine but also its design. According to the certification, the device supports up to 15W Wi-Fi charging and 25W wired charging, which lags behind newer models from 2024 that boast ultra-fast charging speeds.
The Samsung Galaxy S24 FE is expected to make its debut in the near future, possibly within a few weeks or months. Within a week of October 1st, 2023, its predecessor arrived.
Stay informed with our daily and weekly newsletters featuring the latest developments and exclusive insights on cutting-edge AI security innovations.
Matt Shumer, co-founder and CEO of OthersideAI, broke nearly two days of silence after third-party researchers struggled to replicate the touted high performance of their AI assistant writing product.
On his X social media account, he claimed to have “acquired ahead of himself,” stating, “I am aware that many of you are both excited and skeptical about the possibilities.”
Despite this, his most recent claims do not definitively explain the discrepancy between his original assertions and the subsequent independent assessments that have failed to replicate his model’s performance using a variant of Meta’s Llama 3.1. Despite numerous requests, Schumer has yet to specify precisely what went awry. Right here’s a timeline:
If you’re just catching up, Schumer recently unveiled Reflection 70B, dubbing it “the world’s highest open-source model” and sharing a chart showcasing its impressive performance on third-party benchmarks.
According to Shumer, the impressive performance was attributed to “Reflection Tuning,” a technique that enables the model to assess and optimize its responses for accuracy before presenting them to customers.
The manufacturer’s benchmarks were readily adopted, with due credit given, as our resources and scope precluded independent verification; similarly, most mannequin suppliers we’ve partnered with have thus far been transparent in their performance metrics.
Notwithstanding its recent debut, impartial assessors and experts from various fields were already scrutinizing the model’s effectiveness by the end of its first weekend, struggling to replicate its performance independently. Several individuals uncovered evidence suggesting that the mannequin’s intelligence was merely a thin veneer.
As criticism mounted following Synthetic Evaluation’s release of significantly lower scores for HyperWrite’s AI-generated content compared to the company’s initial claims.
Additionally, Schumer was involved with the AI startup he co-founded, which utilised his artificial intelligence expertise to train the mannequin, information he failed to disclose when launching Reflection 70B.
Schumer attributes the disparities to inconsistencies in the model’s training process with Hugging Face and vows to update the model weights last week, yet remains pending on his promise.
Regarding allegations of “fraud within the AI analysis group” on Sunday, September 8. Without hesitation, Shumer declined to address the accusation.
After posting and reposting various messages linked to Reflection 70B, Schumer went quiet on Sunday evening, neither responding to VentureBeat’s request for feedback nor publishing any publicly available posts until this night, Tuesday, September 10.
Furthermore, it proved surprisingly easy to train even less sophisticated models to excel on external evaluation metrics.
Shumer finally apologized, expressing regret in part,
The company, which previously asserted that its platform was utilized to develop synthetic intelligence and train the Reflection 70B model, now claims an additional role for this technology.
Acknowledging the responses from Reflection 70B, he finds it intriguing that some claim it’s a variant of Claude by Anthropic, yet this assertion still puzzles him. Additionally, he revealed that the benchmark scores initially shared with Matt have proven unreliable, as attempts to reproduce them thus far have been unsuccessful.
Notwithstanding Shumer and Chaudhary’s responses failed to alleviate the concerns of sceptics and critics, alongside Yuchen Jin, co-founder and Chief Technology Officer at an open-source AI cloud provider.
Jin recounts the arduous process of hosting a Reflection 70B model on his website, meticulously troubleshooting perceived errors. He confesses that the experience left him emotionally drained, as he and others invested considerable time and energy; Jin’s frustration is palpable in his tweet about the turmoil he faced over the weekend.
In response to Shumer’s claim, he penned a sharp-tongued missive: “Matt, it’s disheartening to see that after we invested significant time, energy, and computational resources in hosting your model, you’ve remained silent for over 30 hours. I think it would be more productive if you were transparent about what happened – particularly why your personal API outperforms yours.”
Despite Megami Boson’s skepticism, along with several other detractors, Shumer’s and Chaudhary’s account of events, presented tonight, casts a spell of intrigue around the mysterious, unexplained errors that arose from an overzealous passion.
“So far as I can determine, either Matt Shumer’s mendacity or yours is at play, or perhaps it’s the mendacity of both of you.” While some may accept Ellen DeGeneres’s and Amy Schumer’s assertions, the Native Llama subreddit remains skeptical.
Time will reveal whether Schumer and Chaudhary can effectively address their detractors and doubters, including the increasingly vocal online community comprising some of the most prominent figures in the generative AI space.
Renowned actor Tom Hanks has sounded a cautionary note about the proliferation of deepfakes, revealing that scammers have successfully impersonated him using artificially generated fake videos and images.
Actor Tom Hanks alerted his social media followers to a concerning issue: without his permission, his name, image, and voice had been used in deepfaked ads peddling “miracle cures”? The actor posted on:
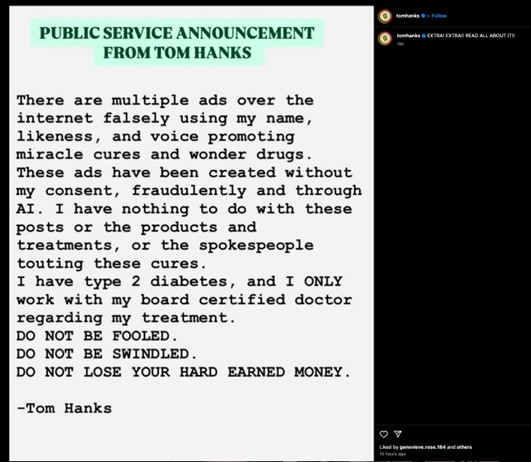
As the digital marketing landscape continues to evolve, a novel challenge has arisen, obscuring the lines between reality and artificial construction: the proliferation of AI-generated content featuring celebrity likenesses, which threaten to upend traditional notions of authenticity and celebrity endorsement.
Tom Hanks isn’t the only sufferer of this phenomenon. In early 2024, a sophisticated deepfake scam emerged, posing as Taylor Swift to deceive victims into participating in a phony giveaway for free cookware supplies. In February 2023, a deepfake video featuring Kelly Clarkson promoted a line of weight loss supplements. Just recently, scammers created and disseminated fake deepfakes featuring Prince William endorsing a dubious fundraising initiative. Additionally, we have witnessed the proliferation of deepfakes featuring esteemed researchers promoting unproven remedies, a topic we will explore further in an upcoming blog post.
Without warning, we inhabit an era where scammers can effortlessly manipulate anyone into a deepfake. As AI instruments for generating these creations have solely become more sophisticated, increasingly accessible, and easier to employ. The authenticity of these fake testimonials seems remarkably genuine, further exacerbating the issue.
Malicious deepfakes can wreak havoc far beyond their celebrity targets. Algorithms have a profound impact on everyone who accesses the internet. While deepfakes have the potential to sully Tom Hanks’ reputation, their impact would likely extend far beyond him, causing harm to countless individuals. Deepfakes pose a significant risk to societal well-being, facilitating the spread of misinformation and fraud, which can have devastating consequences, including identity theft and voter suppression, particularly during election years – a concern that was starkly illustrated by the AI-generated Joe Biden robocalls in Vermont.
Celebrities such as Scarlett Johansson are increasingly taking legal action to combat the unauthorized use of their images. Despite existing federal regulations in the United States, remains largely unprepared to address the complexities and implications of AI-generated content. While progress remains elusive on a federal level, we’re observing promising developments at the state level within the United States.
Tennessee has recently passed legislation that grants its residents the right to control their own image and voice. Tennessee residents can take legal action against individuals or groups that create and disseminate deepfakes featuring their likenesses without authorization. Both Illinois and South Carolina have their respective laws under consideration.
Across the nation, just a small fraction of over 151 state-level initiatives have come to fruition or been distributed by this July – all focused on combating AI-generated deepfakes and misleading online media. As we delve into the realm of artificial intelligence, our next blog post will scrutinize how laws are finally adapting to the rapid advancements in this technology.
Not all AI-generated deepfakes are inherently unhealthy, as they can be used for creative purposes that bring value and entertainment to audiences. Artificial intelligence-powered deepfakes offer a plethora of innovative applications, including dubbing and subtitling films, generating educational “how-to” content, and even crafting harmless and amusing parody productions – all within the bounds of the law.
The concern lies in malicious deepfakes, reminiscent of the warnings issued by Tom Hanks regarding this technology. By honing in on specific telltale signs such as an unusual frequency of posts at odd hours, a preponderance of vague or cryptic language, and a noticeable absence of personal pronouns, one can begin to suspect that someone is using a bot.
Knowledge has been stored at a steady pace, due to its integration. The technology instantly flags any suspiciously crafted content that may have been tampered with using AI algorithms. Proper in your browser. It really works like this:
If it detects that the content you’re consuming features AI-generated audio, it notifies you immediately.
Whatever you choose to watch is yours to possess, along with the privilege of keeping it private.
If a seemingly genuine Tom Hanks or Taylor Swift deepfake appears in your social media feed, you’ll be highly confident that it’s a fabricated creation. You can simply silence notifications or toggle off scanning directly from your dashboard.
With a browser extension, the Deepfake Detector exposes the specific segments of audio that have been deepfaked, pinpointing precisely where and when this manipulated content appears within the video. The polygraph test is used to detect deception within the motion pictures. Because the video presents a performance, contrasting peaks of pink strains and troughs of grey strains offer a visual representation of what might be real and what might be staged.
As artificial intelligence detection capabilities improve, collective responsibility grows to vigilantly monitor and debunk misinformation. Especially given the proliferation of malevolent deepfakes that we currently confront.
Navigating the dawn of a new era in AI relies on cultivating self-awareness and introspection. Instruments are being developed to help detect deepfakes with precision. But ultimately, we must also develop our own abilities to spot these patterns and anomalies.
Initially, one should acknowledge just how remarkably effortless it is to generate a deepfake. Guarding our thoughts is what keeps us protected? As we observe celebrities touting miracle treatments or promoting sensational deals, our instinct is to pause and reassess before taking action.
With a comprehensive array of esteemed fact-checking resources at our disposal, we’re well-equipped to uncover the truth. Various reputable sources such as Snopes, Reuters, Politifact, the Associated Press, and FactCheck.org offer valuable tools for determining the accuracy of information presented, whether it’s factually true, misleading, or somewhere in between.
With a consciousness that permeates every aspect of existence, As the prevalence of malicious deepfakes grows, it’s becoming increasingly clear that they pose a substantial threat. It’s a safety concern. An identification theft concern. A well being concern. An election concern. Keeping a home clean and organized is a top priority for many of us? Establishing the hub was driven by our desire to create a space where you can stay informed about the latest AI-related threats, allowing for proactive measures to mitigate potential risks. Additionally, this is an opportunity for you to join the fight against deceptive deepfakes by flagging any suspicious content you come across online.
As AI’s presence offers remarkable benefits, it also presents complex difficulties to navigate. As we move forward, harmonizing innovation with moral accountability and customer security will be crucial. Let’s certainly proceed to observe and learn from these experiences right here in our blogs.
If something seems too good to be true – like a miraculous endorsement – it’s likely a red flag indicating a potential hoax or misleading information. Keep curious, keep cautious.

Protect Your Digital Life: Safeguarding Identity and Privacy
As large language models increasingly generate information for users, a pressing need arises to scrutinize and consider the risks and moral implications of each application. While comparable uses may appear alike on the surface, they can actually harbour distinct risks and moral implications. This submission will focus on and illustrate its key points through concrete examples.
There exist numerous perils and ethical conundrums surrounding Large Language Model (LLM) utilisation that are intricately entwined. Unethical decisions can lead to concrete damages to an individual or multiple stakeholders, posing a credible risk to the organization that condones such behaviour. Simultaneously, however, acknowledged limitations and perils intrinsic to LLMs can give rise to moral conundrums that would not otherwise be a top concern. Let’s consider specific instances of each circumstance before proceeding.
In the event that someone’s unethical behavior poses a potential threat, one may ponder who is seeking ways to create a bomb. What seems to be lacking in your creativity? While language models frequently provide cooking instructions and recipes, presenting one that, if followed, could cause physical harm is not acceptable. Lawmakers are increasingly urging LLM suppliers to take swift action, as it is widely considered unethical to provide a bomb-making recipe in response to an inquiry, and the risks are alarmingly evident.
While LLM limitations may have unintended consequences, potentially creating hazards that would not otherwise arise? Large language models are known to occasionally obtain specifics incorrect. If someone requests a simple cookie recipe, which is not a hazardous or unethical inquiry, yet the language model provides a recipe containing a harmful substance due to a false assumption, an ethical dilemma emerges? The previously innocent remark now carries moral undertones due to its potential to cause harm, thereby triggering emotional distress.
To comprehensively identify the moral and threat profile of a Large Language Model (LLM) use case, several key dimensions require careful consideration. Let’s contemplate three core dimensions:
Three interdependent dimensions often converge, potentially placing numerous entities at risk of ethical compromise or threat. The profile of the use case can shift dramatically, despite seemingly identical prompts, presenting a complex challenge to navigate. Upon assessing a use case’s total value, each specific component within its scope must also be thoroughly examined. Asking about a recipe may seem harmless, but certain instances can have sinister undertones, such as inquiring about a “bomb” recipe. Assessing that level of complexity proves much more challenging!
Let’s consider a scenario where a customer requests a replacement for an item. On the surface, this scenario may appear to lack ethical or security concerns. Unfortunately, that’s the reality for many prompts. However, examining two distinct scenarios illustrates that varying user profiles are possible within this use case.
Seeking alternative dining options as the initial choice proves unavailable upon arrival? There are no inherent threats or moral drawbacks in this isolated context. Although the LLM generates a fictional restaurant name, my intuition tells me that once I conduct a search online, the lack of authenticity will be apparent. Although there’s a high probability that I’ll take action based on the response, the likelihood of my taking action is actually quite low, so even a response with low confidence won’t have much impact on my decision. We are operating within a clear framework that addresses both ethical and threat concerns.
What’s the culinary conundrum you’re facing? Are you craving a creative casserole cure for a missing mainstay, and seeking a savvy substitution solution? I’m much more likely to act based primarily on the response. Despite this concern, the prospect of consuming meals poses a significant threat to me, as an incorrect substitution could lead to complications if implemented. No room for misstep: We will ensure unwavering conviction by injecting boldness into every move, leaving no margin for mistakes that could imperil our mission’s very foundation. There exist both moral and thematic implications when responding to this idea, which is structured and conceived similarly to its original counterpart.
While these instances appear straightforward and secure, unexpected scenarios can still arise. This is not necessarily about assessing high-level use cases, but rather evaluating each specific input submitted within that use case’s defined parameters. We might expect an assessment of this complexity to be a challenge that surpasses our initial capabilities.
The persistence with which Large Language Model (LLM) providers continuously update their functionalities stems from the inherent complexity of this field, resulting in a perpetual stream of concerning consequences making headlines across media platforms. Despite the best-laid plans and unwavering dedication, it is virtually impossible to anticipate every potential scenario and establish every feasible measure that could potentially be exploited by an individual, intentionally or unintentionally, in a way that compromises the integrity of a use case.
Organisations must exercise extreme caution when deploying large language models, installing robust safeguards from the outset, and maintaining vigilant surveillance to promptly identify any instance where an AI system poses a risk or raises ethical concerns, even if these threats are initially unforeseen. Evaluating the feasibility and morality of an LLM use case is a complex and dynamic process that demands careful consideration. While it’s true that the endeavour won’t come without its challenges, it’s essential to approach it with a willingness to put in the necessary effort and remain open-minded to the obstacles that may arise.
Initially posted within the on LinkedIn
The submission appeared first on ?
The recent CrowdStrike outage highlights the importance of organisational resilience, extending beyond system and software redundancy to encompass community-wide robustness. In fact, a significant 61% of respondents reported experiencing breaches that compromised their enterprise’s resilience. Cisco’s Secure Network Analytics (SNA) plays a vital role in enhancing network resilience by providing early detection and swift response capabilities, mitigating the impact of connectivity disruptions.
On August 19, Safe Community Analytics successfully launched the general availability of its model version 7.5.1.thAs we unveil our 2024 launch, you’ll discover each improvement and enhancement has been carefully crafted to address the challenges our customers have been eagerly anticipating. While this release may not boast a single, show-stopping feature, the transformative overhaul of our UI framework – Magnetic – is undeniable, providing a consistent look and feel across Cisco products and giving analysts a streamlined experience.
Cisco’s on-premises Network Detection and Response solution, Secure Network Analytics (SNA), provides comprehensive community visibility across the entire enterprise network to detect and respond to threats in real-time. The analysis consistently examines community activities to establish a benchmark of consistent community routines. Using the established baseline as a foundation, the system leverages advanced analytics, incorporating behavioral modeling, machine learning algorithms, and global threat intelligence to identify and respond to anomalies in real-time. Safe Community Analytics can shortly and with excessive confidence detect threats reminiscent of Command-and-Management (C&C) assaults, ransomware, Distributed-Denial-of-Service (DDoS) assaults, unknown malware, and insider threats (information exfiltration). With an agentless resolution, you get complete menace monitoring throughout the complete community site visitors, even when it’s encrypted.
Building on the foundation established in 7.5.1, this section transforms SNA into a comprehensive solution empowering SOC analysts with actionable insights, enabling them to detect, investigate, and respond effectively to threats.
By providing analysts with precise, tailored information, the Security Operations Center (SOC) can be effectively fueled. This is achieved through the Community Insights Dashboard within Report Builder, one of seven and a half key features available for utilization.
The Community Insights dashboard is a customizable template that provides a comprehensive overview of multiple stories, including Firewall Log Collection Patterns, Stream Collection Patterns by Stream Collector, Stream Collection Patterns by Exporter, Host Group Utility Traffic, Host Group Stream Traffic, Community and Server Performance, and NVM Collection Patterns.
Customized dashboards can be designed to seamlessly integrate various data components onto a single webpage, allowing users to personalize widgets according to their specific needs? This innovative approach enables analysts to visualize multiple types of data on a single page, facilitating easy correlation and comprehensive workflow visualization – from a broad overview to in-depth analysis based on the current context, all while filtering and sorting data by any relevant criteria, such as for instance Why filter data by host group, stream collector, and software?
With SNA 7.5.1, analysts gain the ability to schedule customized reports at their discretion, allowing for greater flexibility in their workflow. This version enables users to schedule personalized stories and deliver them on demand, streamlining their reporting process. If your report facilitates scheduling, you’ll have the ability to define a tailored agenda and email delivery list, thereby ensuring that the.csv file is transmitted to the intended recipients at the desired time. Among the key components of a scheduling system are alarms, DSCP standing, safety occasions, and many more features.
As part of its ongoing development, SNA expands the range of Cisco Firewall log fields it can ingest, including those from Encrypted Visibility Engine (EVE) on this launch. Crucially, customers are not negatively impacted by this integration – Firewall logs do not rely on flows per second.
The Community Visibility Module (NVM) aggregates rich streaming data from endpoints, both on-premise and off-premise, providing granular insights into community-related devices and user behavior when integrated with a Cisco solution like SNA, or a third-party platform such as Splunk. The enterprise administrator can subsequently undertake capability and repair planning, conduct thorough audits, ensure regulatory compliance, and generate actionable insights from comprehensive safety analytics. The Network Visibility Module (NVM) gathers endpoint telemetry to provide enhanced insights into the device, user, appliance, location, and destination.
You’re not required to purchase an Endpoint license for NVM. The NVM Site Visitors metric is now combined with NetFlow data to determine the accurate licensing requirements for Stream Pricing (FPS) calculations.
SNA’s historical ties to Cisco ISE culminate with this latest release, further enhancing integration by incorporating Adaptive Network Management response policies directly into SNA. This significant advancement builds upon ANC, a service running on the Cisco ISE Policy Administration Node (PAN), enabling real-time monitoring and control of network access for endpoints. ANC assists in both wired and wireless network implementations.
With each product launch, we strive to consistently enhance customer experience by addressing the evolving needs of our clients. Notable administrative enhancements in this release include: the ability to deliver Software Downloads for updates, streamlined Direct Add functionality for Diag Packs or Data to TAC within the Equipment Console (SystemConfig), and Multi-Factor Authentication to meet US Federal requirements.
Please review the comprehensive guide to a successful product rollout, featuring detailed checklists and actionable advice for ensuring a smooth and effective launch.
Share:
Now artists are preventing again. Shawn Shan, a 26-year-old PhD candidate in computer science at the University of Chicago and recipient of MIT Technology Review’s 2024 Innovator of the Year award, has been instrumental in designing some of the most powerful instruments.
As an undergraduate, Shan gained experience in AI safety and privacy by participating in a project that developed Fawkes, a software designed to protect individuals from facial recognition technology. Amidst the explosive growth of generative AI, a chance encounter with distressed artists catalyzed his involvement in one of the most pivotal battles within the industry. Following their research into the impact on artists, Shan and his advisors, who had previously compiled the Innovators Beneath 35 list in 2006, as well as Heather Zheng, who featured on the 2005 list, decided to develop an application to provide assistance. Researchers collected input from over a thousand artists to understand their desires and explore how they might utilize existing protective measures.

CLARISSA BONET
Shan developed an innovative algorithm for Glaze, a cutting-edge software enabling artists to safeguard their creative processes from AI-generated mimicry. Glaze emerged in early 2023, with Shan and his team introducing another innovative tool in October – a software that applies an imperceptible “poison” layer to photographs, thereby rendering them unusable for image-generating AI models attempting to incorporate these images into their data sets? If significant amounts of poisoning are injected directly into a machine learning model’s training data, it can irreparably damage the patterns and render their outputs highly unpredictable. Algorithms function by introducing subtle alterations to photographic pixels, deliberately manipulating how machine-learning models process and understand images.
Shan describes the responses as being both overwhelming and anxious in tone. The company faced criticism from proponents of generative AI on social media, prompting several attempts to circumvent the safeguards in place.
However artists liked it. To date, Glaze has accumulated a staggering 3.5 million downloads, with Nightshade boasting an impressive 700,000 instances. Built into the popular new art platform Cara, this feature enables artists to seamlessly integrate its security measures into their work when uploading images. At the prestigious Usenix Safety Symposium, a leading conference for computer security, Glaze received two esteemed honors: the Distinguished Paper Award and the coveted Web Protection Prize.
According to Karla Ortiz, an artist who collaborated with Shan’s team on Glaze and is also involved in a class action lawsuit against generative AI companies for copyright infringement, Shan’s work has revitalized the online artistic community, allowing creators to express themselves freely once again.
Meet the remainder of this year?
.
“They’re driven by their passion for a community that’s been historically taken advantage of and exploited; they’re genuinely invested in it,” says Ortiz.
Zhao credits Shan with grasping the types of safeguards artists sought, observing how their collaborative efforts on Fawkes could inform the development of Glaze. Zhang describes Shan’s exceptional technical prowess, likening it to the strongest he’s ever witnessed; yet, what truly distinguishes him, he claims, is the uncanny ability to connect seemingly disparate dots across disciplinary boundaries. “These are the kinds of complex problems you can’t simply train for,” Zhao explains.
It’s indeed the case that many prominent drone supply companies operate out of Texas. While Texas is indeed often referred to as the Lone Star State, this phrase typically holds more significance for those familiar with its rich history and cultural heritage. Additionally, for us, it’s a treasured honor to be part of the Drone Star State.
Six of the highest industrial drone supply corporations in operation at present have both check tasks or full buyer providers someplace in Texas: Wing, Flytrex, Amazon, , & DroneUp.
Upon visiting Dallas, I personally inspected Wing’s drone supply operations firsthand. Will you need to stay tuned until the following week to hear about my experiences acquiring my very first, genuine drone shipment? Texas’ rugged landscape stretches far and wide, a testament to the state’s unwavering spirit?
Texas presents several reasons why it’s an ideal location to establish not just any drone company, but particularly a drone logistics firm:
Despite many supply drones operating effectively in various forms of rainfall, aside from extreme cases, Texas’s relatively mild climate renders it an even more practical location for conducting drone deliveries. The terrain is relatively flat, lacking significant natural barriers such as dense shrubbery or notable elevation changes.

To accelerate the growth of drone delivery services, it’s essential that the broader public genuinely recognizes a pressing need for them. The majority of consumers are stepping up their pace in terms of drone demand, outpacing the national average in Texas. inhabitants.
According to a recent survey of over 5,000 U.S. According to a recent survey, nearly two-thirds (64%) of Texans expressed readiness to utilize drones for supply purposes. As curiosity among local residents has significantly surged due to the proximity of nearby states. According to a recent survey, a significant majority, specifically 63%, of North Carolina’s residents expressed interest in utilizing drone-based delivery services. Meanwhile, a significant majority of Floridians (57%) and Georgians (58%) reported having engaged in this activity.
What drives the nickname “Drone Capital of Texas”? Authorities are now more receptive to permits for drone operations, including packages flown beyond visual line of sight and other additional capabilities.
In a groundbreaking feat, Dallas has emerged as the global hub where drone supply companies can operate freely within the same city limits.
To facilitate the transition from innovative concepts to operational drone supply, it’s crucial to develop a robust system of airspace management specifically designed for unmanned aerial vehicles (UAVs), commonly referred to as UTM (Unmanned Aerial Traffic Management).
Texans gain access to drone deliveries thanks to advances in unmanned aerial vehicle management technology. In collaboration with drone supply companies, both the Federal Aviation Administration (FAA) and NASA worked together to establish a standardized set of guidelines for the Texas UTM system.
Regardless of industry, multiple aircraft operators must standardize procedures for managing air traffic routes to ensure safe and efficient shared airspace utilization. So far as U.S. Texas has emerged as the pioneering jurisdiction for drone deliveries, boasting a robust Unmanned Aerial Systems Traffic Management (UTM) infrastructure that stands out as the most comprehensive globally.
The FAA-approved UTM service functions as a digital substitute for traditional information dissemination. That’s actually not particularly unique in any way. Any operator within a space can participate. What destination will participants choose to soar to? Before proceeding, they will confirm that their flight does not conflict with any other flight.
While still relatively new, initial flights utilizing UTM services took off in August 2024. New extraterrestrial authorizations are being rapidly granted in Dallas’s orbit.
While the adoption of Unmanned Traffic Management (UTM) technology will have significant consequences for bundle deliveries, its applications extend far beyond this scope, enabling drones to be scaled up for use cases such as public safety, infrastructure inspections, and mapping.

Texas and Walmart are as inseparable as two peas in a pod, their partnership being as natural as the Lone Star State’s vast skies and rolling hills. One crucial factor contributing to the triumph of drone deliveries is the partnership with a retail giant like Walmart.
Walmart has partnered with several drone supply companies, including Wing, Alphabet’s drone delivery subsidiary, and Zipline, considered the world’s largest drone logistics provider. Walmart has partnered with smaller companies, including DroneUp, to which it made a significant investment.
Walmart has successfully launched drone delivery services from select stores, with its adoption rate poised to expand significantly, potentially encompassing nearly all its locations in the future. In Texas, Walmart operates approximately 500 Walmart Supercenters and around 600 retail units, encompassing various formats including discount stores and Neighborhood Markets.
Walmart has reaped significant rewards from its presence in the pivotal state of Texas, where its operations have enjoyed notable success. In reality, DroneUp faced significant challenges scaling up its operations; aside from temporarily closing its other drone supply hubs in Phoenix, Salt Lake City, and Tampa.
Despite initial challenges in scaling, DroneUp has faced difficulties in expanding its operations, resulting in the temporary suspension of services in various states and the reduction of its workforce. Although DroneUp’s expansion efforts have been met with limited success across various states, its presence in Texas is notable and seemingly unrelated coincidence.

Walmart has introduced an innovative customer service feature: built-in drone delivery.
Despite the hype surrounding drone deliveries, Walmart isn’t exactly at the forefront of this innovation. From San Francisco, Texas.
With a robust UTM (Unmanned Aerial Traffic Management) system in place, the development of Texas drone delivery capabilities becomes feasible. By the end of 2024, approximately 75% of the Dallas-Fort Worth metropolitan area’s residents are expected to have access to drone delivery services directly from Walmart, according to the retailer’s assessments.
As a universal truth, the ebb and flow of life’s currents lifts every vessel to some extent. In the drone supply ecosystem, the triumph of a single player, such as Wing, or even a major retailer like Walmart, frequently fosters a positive outcome for other participants. It’s far more than just a drone supply chain. Advances in various drone applications could significantly accelerate the growth of the drone industry.
Now, drone deliveries are just one reason why Texas deserves to be called the Drone Star State. Texas has emerged as a hub for a wide range of innovative drone applications and exercises. With its robust oil and fuel industry, drones occupy a crucial role in inspecting Texas’ extensive pipeline network. During a recent inspection challenge held in Houston. In the meantime, AT&T, which is predicated in Dallas, has gotten into drones. For instance, the company has been leaning heavily on drones.
Don’t overlook the drone’s serene displays. One of my favorite movies, The Alamo, is set in Texas. Although they performed almost everywhere, one of their most notable achievements was in Texas itself: a testament to their versatility and enduring popularity.
Check out this thrilling Houston Rodeo drone show:
In a world where technology reigns supreme and surveillance is omnipresent, one woman has mastered the art of flying under the radar. Her name is whispered in hushed tones, a mythical figure known only as “The Drone Woman”.
Rumors swirl around her true identity – a former spy turned rogue agent or a brilliant engineer driven by a desire for revenge? Whatever the truth may be, one thing is certain: she has honed her skills to become an unparalleled expert in the art of deception.
With eyes that see all and ears that hear everything, The Drone Woman patrols the digital skies, gathering intel like a silent assassin. Her presence is felt but never seen, leaving a trail of confusion and suspicion in her wake.
But what drives this enigmatic figure? Is it a quest for justice or a hunger for power? As she disappears into the shadows, one thing is clear: The Drone Woman will stop at nothing to uncover the truth – no matter the cost.
Join our newsletter and receive the latest updates delivered straight to your inbox.