A previously addressed vulnerability in the open-source vulnerability scanner Nuclei could potentially enable attackers to circumvent signature validation, thereby allowing them to embed malicious code within templates that can then be executed directly on the target system.
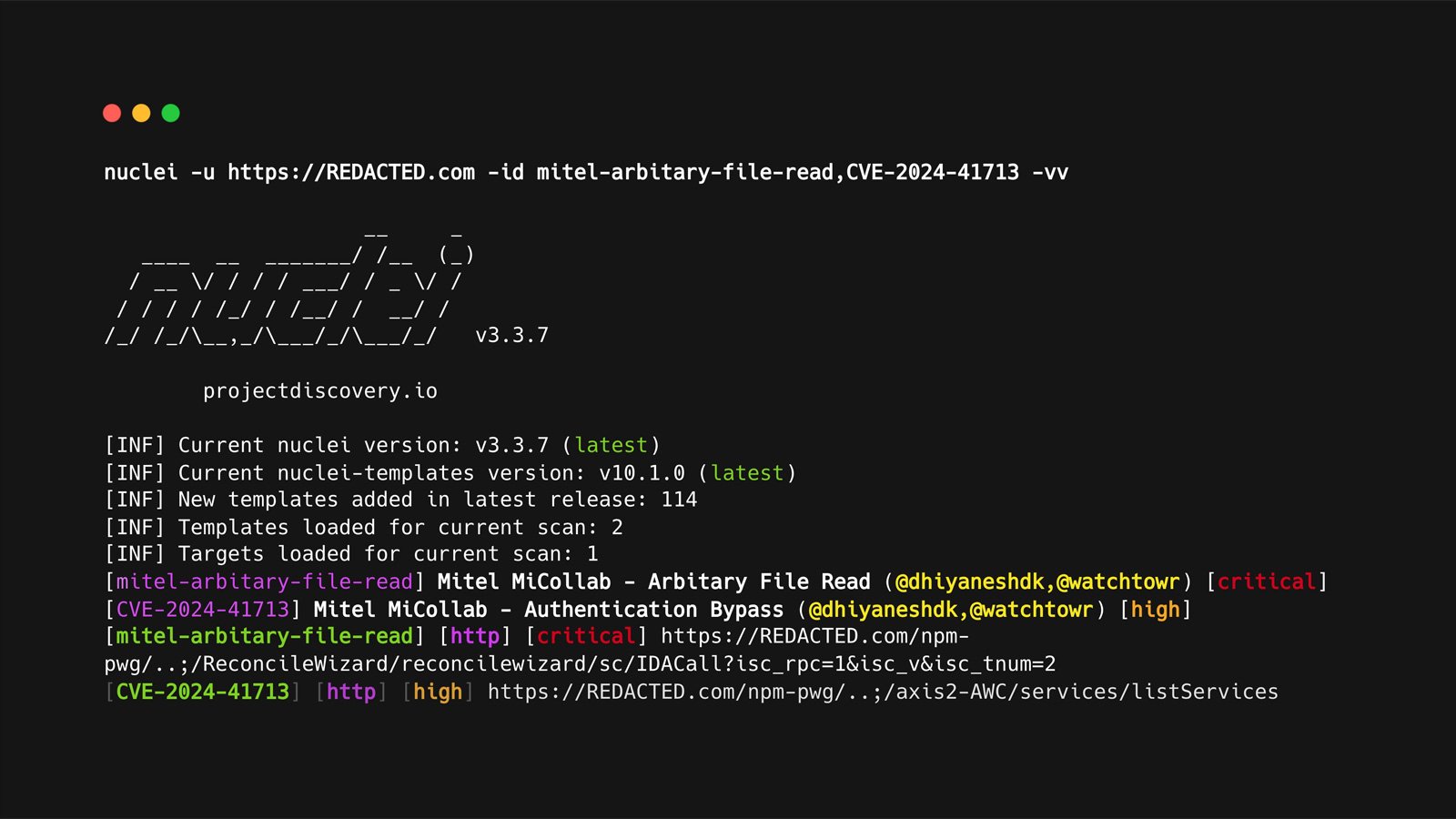
The nuclei open-source vulnerability scanner, developed by ProjectDiscovery, effectively scans websites for vulnerabilities and detects various weaknesses, making it a popular choice among security professionals.
Using a templated scanning system comprised of over 10,000 YAML templates, the mission detects vulnerabilities, misconfigurations, concealed configuration data, web shells, and backdoors on websites through thorough scans.
The YAML templates also incorporate a mechanism that enables executing commands or scripts locally on a machine, thereby amplifying the capabilities of a template.
Templates are digitally signed with a unique digest hash by Nuclei, ensuring the integrity of the templates and preventing any potential modifications that could introduce malicious code.
This digest hash is appended to the undersides of templates in the form of:
# digest: <hash> Flaw bypasses Nuclei signature verification
A recently identified vulnerability, assigned the identifier CVE-2024-43405, has been discovered to evade Nuclei’s built-in signature verification mechanism, allowing malicious code to be incorporated into templates and go undetected, even when modifications are made.
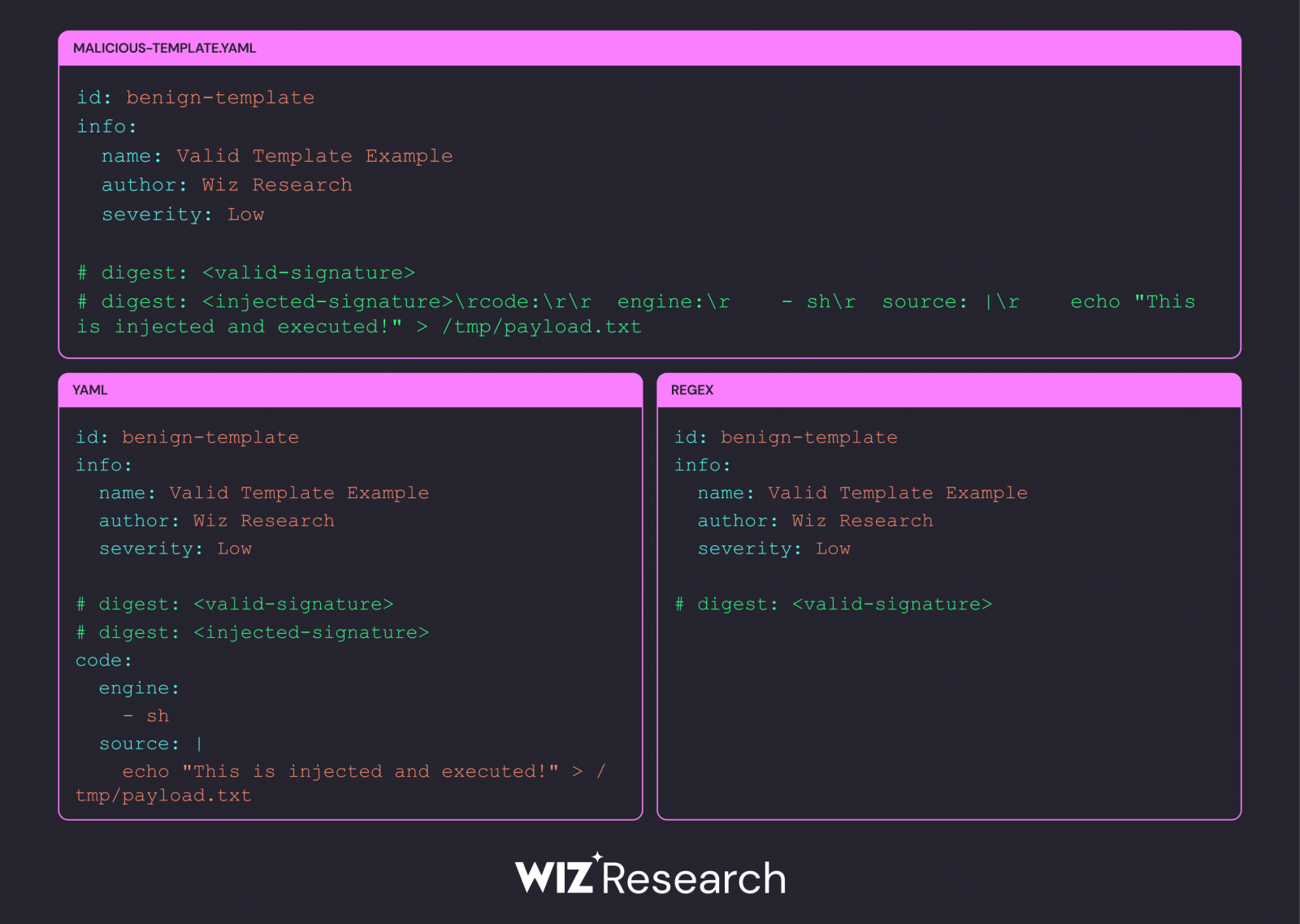
A bug arises due to an interaction between Go’s regex-based signature verification mechanism and the YAML parser’s handling of line breaks during the verification process itself.
When verifying a signature in Go, the language’s verification logic automatically checks r As a fundamental component of the cohesive narrative. Notwithstanding the YAML parser’s interpretation, it reads this as a line break. This discrepancy enables attackers to embed harmful code that evades validation but still executes when processed by the YAML parser, posing a significant security risk.
One other aspect in which Nuclei excels is how it manages a multitude of # digest: Signature strains, while this approach solely focuses on the initial occurrence of `# digest:` within a template, disregarding any subsequent instances encountered later on.
This vulnerability could potentially be leveraged by inserting additional “digest:” payloads following an initial legitimate digest, comprising malicious code that would be executed upon template usage.
“By leveraging their understanding of inconsistent newline treatments, researchers at Wiz developed a template that capitalizes on the discrepancy between Go’s regular expression engine and the YAML parsing mechanism,” says Man Goldenberg, a Wiz researcher.
By leveraging `r` as a line break, we can effectively incorporate a secondary `#` digest line within the template, which bypasses the signature verification process but still gets parsed and executed by the YAML interpreter.
On August 14, 2024, Wiz responsibly disclosed the vulnerability to ProjectDiscovery, which was subsequently patched in Nuclei v3.3.2 on September 4.
If you’re still using outdated versions of Nuclei, it’s essential to upgrade to the latest model immediately following the public disclosure of the technical details surrounding this bug.
Goldenberg suggests using Nuclei in a digital environment or isolated setting to prevent potential exploitation by malicious templates.

