Researchers at ESET have uncovered a sophisticated crimeware marketing campaign specifically targeting the customers of three major Czech banks. The NGate malware, identified as such after thorough analysis, possesses a unique capability: it can intercept and transmit sensitive data from victims’ online gaming sessions, via a compromised Android app installed on their devices, directly to the attacker’s hacked Android phone.
- Malicious actors combined customary tactics – including social engineering, phishing, and Android malware – in a sophisticated attack scenario, allegedly targeting random cellphone numbers and ensnaring unsuspecting customers of at least three financial institutions.
- Since its inception in November 2023, the group has been operating in Czechia, leveraging malicious Progressive Web Apps (PWAs) and Web Application Packages (WebAPKs). By March 2024, the group’s innovative approach was taken to a new level by leveraging the sophisticated NGate Android malware.
- Attackers have successfully cloned NFC data from victims’ physical credit cards using NGate, relaying it to a malicious device that can subsequently emulate the genuine card and withdraw cash from an ATM.
- For the first time ever, Android malware with this capability has been observed in circulation.
- The victims didn’t need to root their devices.
The primary objective of this malicious scheme is to orchestrate fraudulent ATM transactions that drain unsuspecting individuals’ funds from their financial institution accounts without their consent. Victims’ personal data was stolen by exploiting a vulnerability in their compromised Android devices using the NGate malware, which transmitted sensitive information back to the attackers via NFC communication. The attacker leveraged this sensitive data to execute a series of unauthorized ATM withdrawals. In the event that the initial approach proved unsuccessful, the attacker possessed a contingency strategy, which involved transferring funds from the targeted individuals’ accounts to alternative financial institutions.
While no precedent exists for this NFC relay method among previously discovered Android malware? The NGate family of malware is founded on a device developed by students at Germany’s Technical University of Darmstadt, capable of capturing, analyzing, and manipulating NFC traffic.
Overview
Victims were tricked into installing malware, believing they were interacting with their financial institution to resolve a suspected device compromise. Unbeknownst to the victims, their Android devices were compromised after they downloaded and installed an app linked to a deceitful SMS message promising a tax return, ultimately rendering their devices vulnerable. The disturbing details of this violent attack are readily available in the accompanying video.
Notwithstanding its popularity, NGate was unavailable for direct download from the official Google Play store.
The NGate Android malware has been linked to phishing activities carried out by a malicious actor operating in Czechia since November 2022, according to reports. Notwithstanding, we have taken measures to put these actions on hold as per the instructions issued after interviewing the suspect in March 2024.
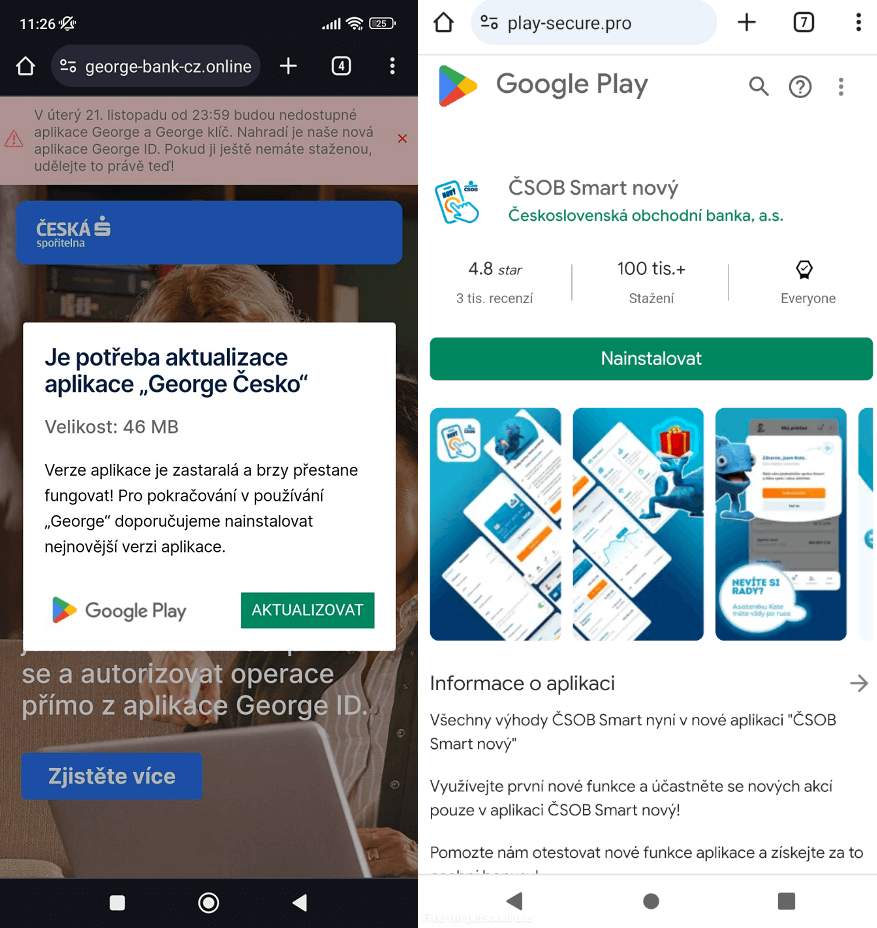
We initially detected the malicious actor targeting customers of prominent Czech banks towards the end of November 2023. Malware was distributed via temporary domains mimicking legitimate banking websites or official mobile banking apps available on the Google Play store, as depicted in Figure 1. These fraudulent domains have been identified through the system, which provides real-time monitoring of threats tailored to a customer’s specific profile. Within the same month, we presented our research findings to our valued clients.
Victimology
During our investigation, we identified six distinct NGate applications specifically targeting customers of three banks in the Czech Republic from November 2023 to March 2024.
Police in the Czech Republic have achieved a significant milestone with the arrest of a 22-year-old individual suspected of perpetrating a string of ATM robberies in the capital city of Prague. When apprehended, the individual was found to be in possession of 160,000 Czech korunas, a substantial amount equivalent to approximately €6,000 or $6,500. The nationality of the arrested individual has not been publicly disclosed. According to investigations, the funds retrieved from the perpetrator were likely taken from only the last three victims; consequently, it is reasonable to assume that the total amount stolen by the mastermind behind this operation is substantially higher.
Evolution of assault situations
Attackers exploited the capabilities of progressive web apps (PWAs), initially refining their tactics by employing an even more discreet variant, known as WebAPKs. The operation ultimately culminated in the successful deployment of the NGate malware.
In all assault scenarios detailed here, a crucial point to note is that the victim’s device does not need to be rooted; rather, the attacker’s device must emulate the obtained NFC traffic.
Progressive net apps
Initially, however, fraudulent websites exploited PWA expertise. This know-how enables users to install an app directly from a website via a prompt; the installation process can be initiated either automatically through a pop-up notification or manually by selecting the option from the browser’s menu. Android supports a range of browsers, including Chrome, Firefox, Edge, and Opera. Upon installation, a novel icon emerges on the smartphone’s home screen, featuring a miniature browser logo situated discreetly at the bottom right corner, primarily functioning as a website link.
In Determine 2, we demonstrate an instance where we compare the icon of a Progressive Web App (PWA) on the left side to that of a standard app on the right side.

PWAs are essentially apps, but unlike traditional apps that require download and installation through an app store, they can be accessed and utilized directly within a web browser. Developed using prevalent web development languages like HTML, which enables structure, CSS, responsible for visual presentation, and JavaScript, crucial for interactive elements, these technologies mirror those employed in website creation. Progressive Web Apps (PWAs) stand out for their seamless compatibility and versatility, engineered to function flawlessly on any device featuring a standards-compliant web browser. With this, a consumer can access the same Progressive Web App (PWA) across various devices – desktop PC, laptop, tablet, or smartphone – without needing to download separate apps for each platform.
If a Progressive Web App (PWA) is installed from a phishing website, it can masquerade as an authentic banking application by mimicking its icon, accompanied only by a faint browser indicator. When users launch this compromised progressive web app (PWA), they are immediately presented with a fake login page that demands their sensitive bank account information.
WebAPKs
Subsequently, the malicious actor refined their tactics in this attack scenario, continuing to target customers of the same banks they had previously targeted, but leveraging an even more sophisticated type of Progressive Web App (PWA), namely a. When users install Progressive Web Apps (PWAs) on their Android devices, the Google Chrome browser often creates WebAPKs – specialized Android apps that provide seamless integration with native device features. While distinguishing between them, Progressive Web Apps (PWAs) are built using web technologies, whereas WebAPKs leverage a technology to integrate PWAs as native Android applications? Unlike traditional PWAs, WebAPKs offer a distinctive characteristic: their icons don’t feature the small browser logo, making them appear more akin to native Android applications. The lack of a distinctive browser brand can deceive consumers into believing that a potentially harmful WebAPK is a genuine application, as depicted in Figure 3.

The distribution scheme remained unchanged – customers were able to download and install a standalone app directly from phishing websites, rather than just a PWA web shortcut. While setting up the WebAPK does require a handbook process, consumers are not explicitly asked to authorize installing applications from unknown sources or enabling browser installations of unknown apps, given that this is not a typical everyday application. Because of this, customers may unwittingly download an application from an unfamiliar or unverified source. As cybercriminals attempt to deceive unsuspecting users into installing malware by disguising the malicious website as a legitimate one, Determine 4 demonstrates the moment when customers unintentionally stumble upon such phishing sites, which then prompt them to install and configure the harmful WebAPK.
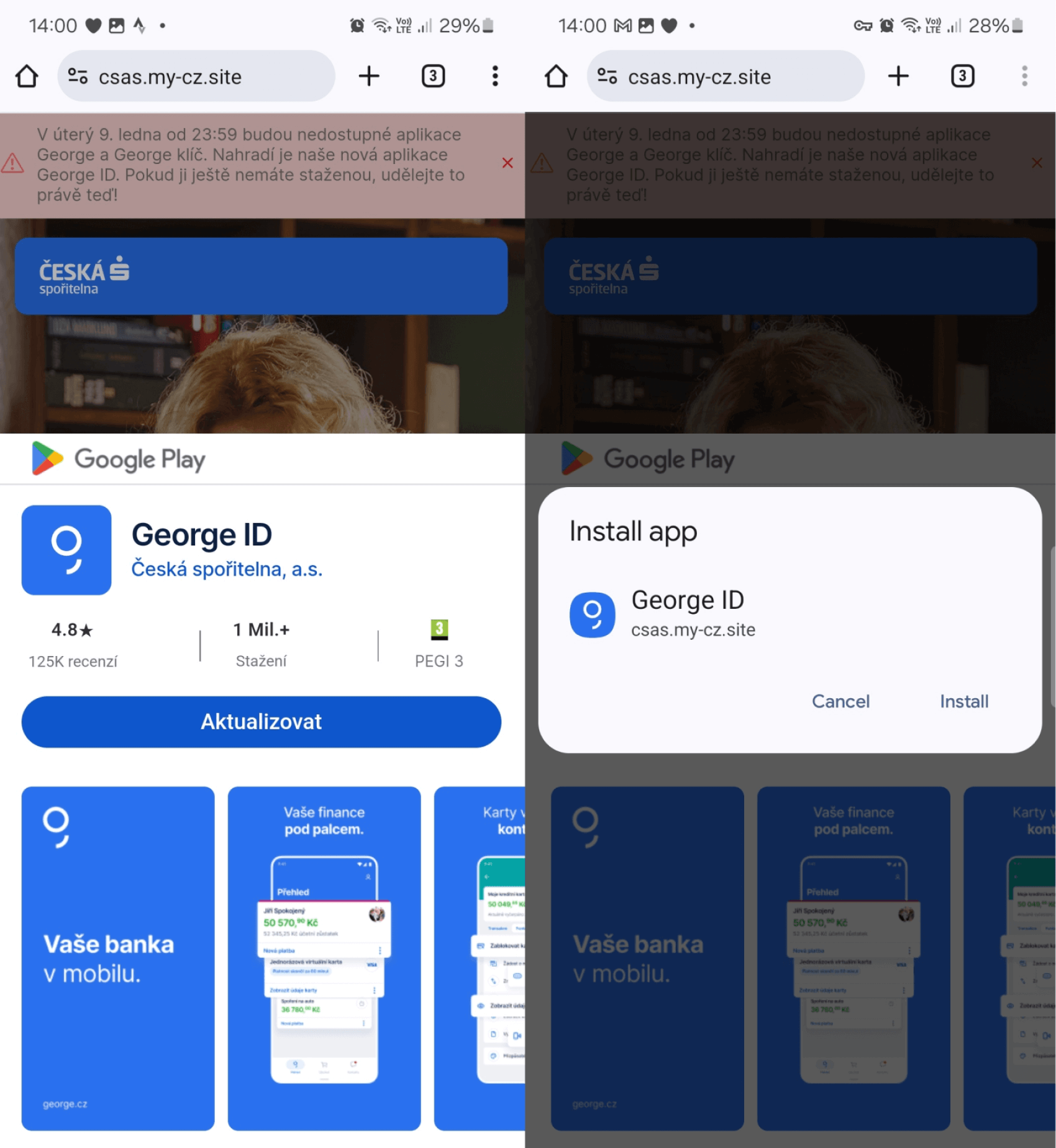
The moment an unsuspecting user installs and launches the compromised application, it promptly demands their banking login information. Phishing campaigns utilizing Progressive Web Apps (PWAs) and Web Application Packages (WebAPKs) have garnered attention in recent .
NGate malware
By mid-March 2024, researchers discovered that the notorious NGate Android malware had expanded its reach by becoming available on the same distribution platforms previously exploited for phishing schemes involving malicious Progressive Web Apps (PWAs) and Web Application Packages (WebAPKs).
After installation and activation, NGate displays a deceptive website, masquerading as a legitimate online platform, where it requests sensitive banking information from unsuspecting consumers. This compromised data is subsequently transmitted to the attacker’s remote server. With its phishing capabilities, NGate malware also features NFCGate, a malicious device that hijacks NFC communication, enabling the unauthorized relay of sensitive information between a victim’s and an attacker’s devices. The NFCGate device was created by a team of innovative college students from the University of Stuttgart in Germany, and it’s now available for purchase online. NFCGate’s primary operation involves transmitting an NFC signal from one Android device to another through a server, effectively mimicking the signal as illustrated in Figure 5.
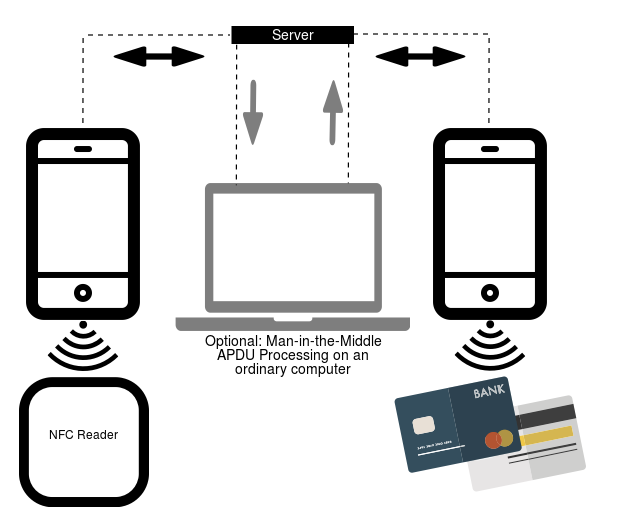
The NFC Gate is a device capable of collaborating seamlessly with NFC visitors on a platform. On the device where NFCGate is installed, it likely
1. Capture NFC site visitors through seamless interactions with apps utilizing Near Field Communication technology.
2. Transfer data wirelessly between devices using NFC technology.
3. Replay previously captured data on the target device.
While some options function exclusively on rooted devices, it’s still possible to relay NFC traffic from non-rooted gadgets as well. The NGate malware exploits a single option from NFCGate’s arsenal. The malware does not interfere with other accessible data on the infected device, nor does it attempt to imitate or replicate such information. The app exploits NFC technology primarily to transfer data between devices.
Notwithstanding this, NGate deceitfully entreats its unwitting targets to disclose sensitive information such as their bank account number, date of birth, and personal identification numbers for their credit cards. The app will also request that users enable their phone’s near-field communication (NFC) functionality. Victims are directed to place their credit card at the back of their smartphone until the rogue application recognizes the information.
As the unsuspecting victim swipes their credit card, a clandestine process unfolds: the NFC data is transmitted via a server to the attacker’s compromised Android device. This allows attackers to mimic the victim’s financial institution card on their own device. The attacker can now utilize the copied card information on their Android device to initiate transactions and withdraw cash from compatible ATMs, leveraging near-field communication (NFC) technology.
Backup Resolution: Situation Report
The full-scale assault on our position has commenced. Enemy forces are converging from multiple directions, displaying a high level of coordination and aggression.
We have received reports of heavy artillery fire, supported by infantry advances on the eastern and western flanks. Our forward positions are under intense pressure, with multiple breaches already reported.
Current status:
* Forward positions compromised
* Main defensive line breached in two locations
* Reinforcements en route but delayed due to logistical issues
Recommendations:
1. Implement emergency recall of all available forces to strengthen the main defensive line.
2. Launch targeted airstrikes against enemy command and control centers to disrupt their coordination.
3. Activate secondary defensive measures to minimize further breaches.
Estimated time to execute: 30 minutes
Police investigations in the Czech Republic uncovered that the assaults started with perpetrators sending targeted SMS messages to prospective victims, accompanied by a link to a phishing website masquerading as a bank’s online platform, alongside demands for fake tax returns. The hyperlinks were likely linked to malicious Progressive Web Apps. Upon installing the compromised application, the unsuspecting user unwittingly granted the malicious actor access to their account, following a seamless login with their authenticated credentials. The attacker, posing as a financial institution employee, claimed to be the victim of their own ruse. The individual realised their account had been compromised, possibly due to an earlier suspicious text message they had sent or received. As the attacker revealed the truth – the victim’s online identity had been breached – a new falsehood emerged, fueled by the very revelation meant to expose the original deceit.
In an attempt to safeguard their finances, victims were compelled to modify their PIN and authenticate their bank cards using the NGate malware’s mobile application. A link to download N-Gate was sent via SMS. Users are likely to input their outdated PIN within the NGate app to generate a fresh one, while concurrently inserting their card into the rear of their smartphone to verify or implement the update.
Because the attacker has already gained access to the compromised account, they may modify the withdrawal limits. If the NFC relay methodology proves unsuccessful, a possible fallback option could be transferring the funds to an alternative account. Regardless of efforts to remain under the radar, using an NGate facilitates the attacker’s ability to seamlessly siphon the victim’s funds without leaving a digital footprint that can be traced back to their own bank account. The detailed assault sequence diagram is depicted in Figure 6.
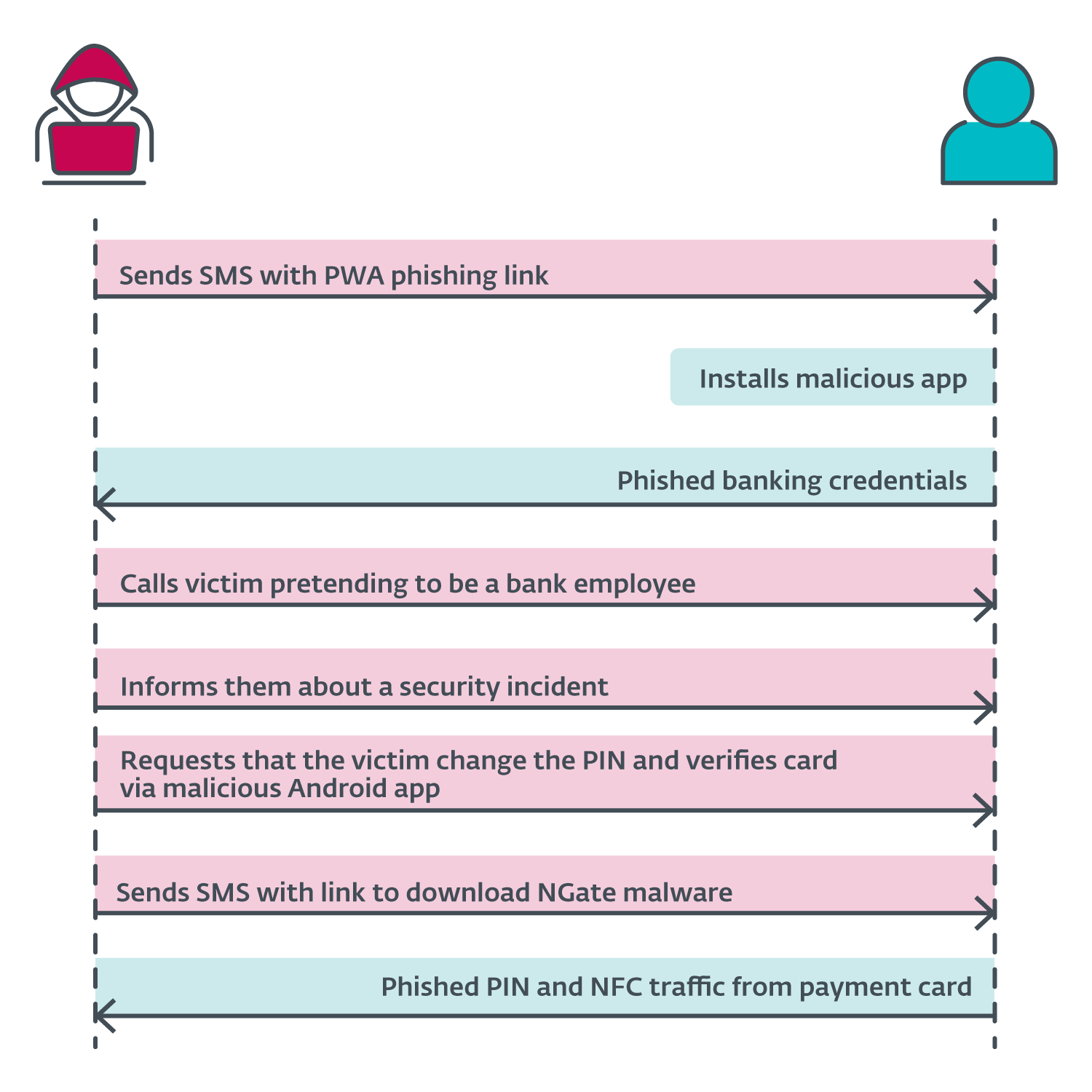
Different potential assault situations
The deployment of NGate malware or a customised variant of NFCGate creates a heightened risk of exploitation opportunities, particularly in scenarios where an attacker possesses physical access and can replicate NFC tags or credit cards. To successfully execute and replicate future attacks, the perpetrator needs a specially modified Android device with root access.
Gaining entry through NFC tags
An NFC tag or token is a small, contactless device capable of storing and transmitting data. These versatile tags can fulfill a multitude of roles in addition to serving as identifiers and controllers for switching between different types of content. NFC tags can be leveraged to create custom applications such as virtual transit passes, secure building access cards, and wearable health monitors, among others.
Each NFC tag features a unique identifier (UID) and an information section where keys are stored. As tags approach a card reader, a seamless handshake ensues, confirming the tag’s authenticity by validating its possession of the requisite authorization keys. Despite this, a few readers still rely solely on confirming the unique identifier (UID) of the token for authorisation purposes, thereby circumventing the requirement for the associated cryptographic keys. The unique identifier (UID) typically has a length of four bytes.
Any non-rooted Android device can learn NFC tags that adapt to various applications and uses. Nonetheless, only stock-rooted Androids can seamlessly emulate the unique identifier (UID) of an NFC tag. If a reader solely verifies the token’s Unique Identifier (UID), it is possible to leverage NFCGate to relay and emulate the tag seamlessly. Since NFC tags store their keys internally and cannot be replicated by NFCGate, users seeking access must retain the saved keys, rendering it impossible to clone the tag in these instances.
An attacker, possessing physical access to an NFC-enabled tag or manipulating a user into placing the tag behind their smartphone, where the malicious application is installed, can successfully replicate the Unique Identifier (UID) of the NFC entry token. This technique enables the duplication of a unique identification number (UID), thereby granting unauthorized access to secure locations, premises, and facilities.
During rigorous testing, we successfully transmitted the unique identifier (UID) from a MIFARE Traditional 1K card, commonly utilized in applications such as public transportation tickets, employee identification badges, membership and student ID cards, and similar scenarios. With the capability of NFCGate, an attacker can execute a real-time NFC relay attack, capturing an NFC token at one location and subsequently gaining access to a different location by mimicking its unique identifier (UID), as illustrated in Figure 7.
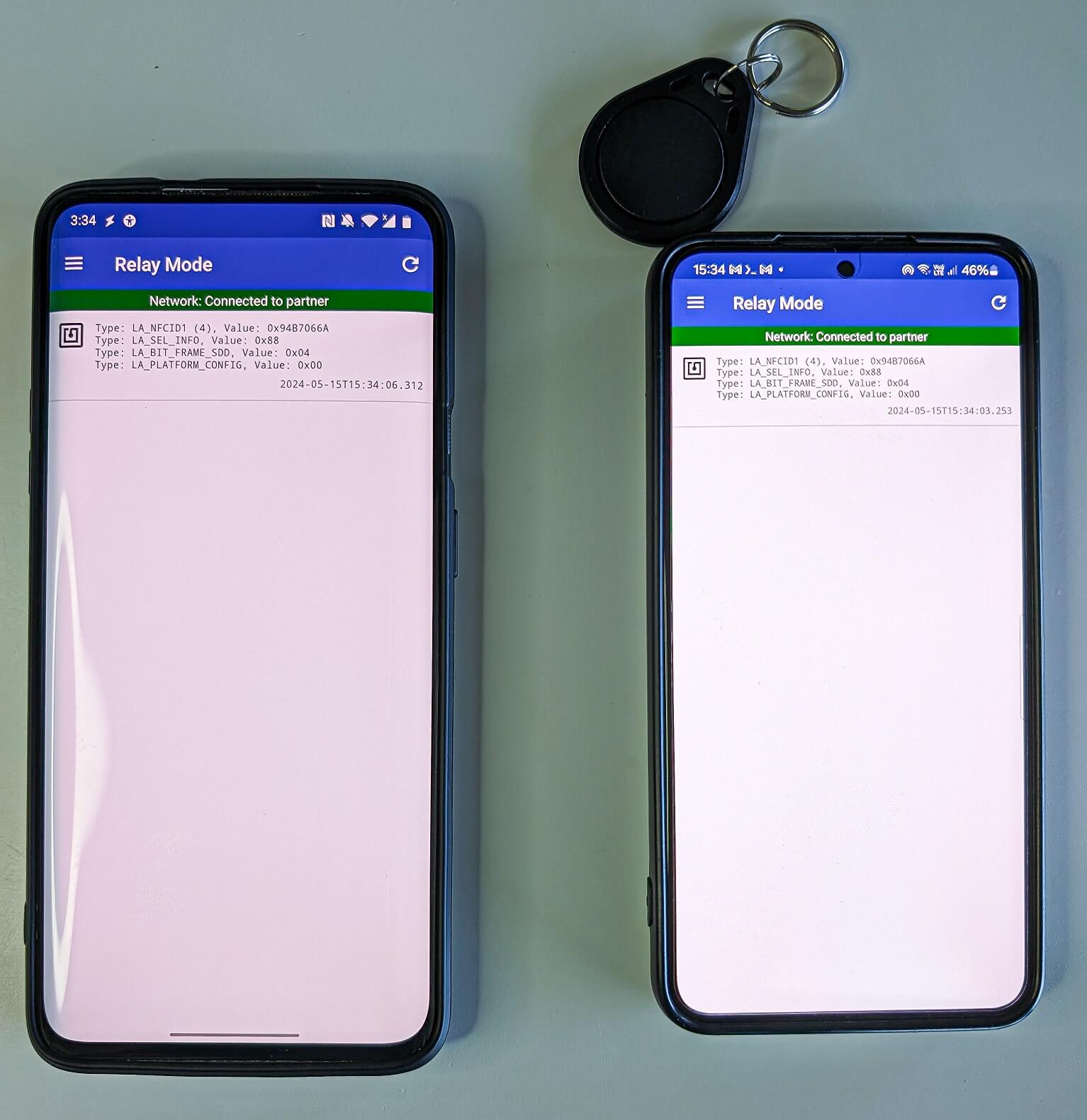
Despite our attempts to mimic the UID, NFCGate ultimately transmitted distinct UIDs to the reader instead of relaying the original one. We discovered that our testing device, a OnePlus 7 Pro, is ineffective in supporting UID cloning functionality. As a result, we leveraged the app and manually inputted the unique identifier (UID) to effectively replicate the data with ease.
The targeted nature of this assault indicates a high degree of planning and familiarity with the victim’s systems, implying that the attacker has prior knowledge of the potential vulnerabilities.
Disbursements of small, unmonitored funds utilizing low-value playing cards.
An attacker gaining physical access to casino-issued chips can easily duplicate and replicate them using the same techniques employed by the notorious NGate malware. This system may be exploited by attackers seeking to gather information about playing cards by accessing unattended bags, purses, wallets, or phone cases containing card collections, particularly in densely populated areas.
While this scenario is typically limited to establishing modest, contactless transactions at payment terminals, subject to the restrictions imposed by the issuing financial institution, it does not extend to ATM withdrawals, as these would necessitate the attacker possessing the card’s PIN.
What would happen if we were to clone a credit card saved in our smartphone’s digital wallet? The ability exists to transmit NFC signals from Android phones equipped with digital wallets such as Google Pay. Despite this, Google demands that clients provide a separate fee for each NFC transaction. Although users may unlock their device, they are still required to provide verification within the Google Pay app before processing a payment. Before processing a payment, the Apple Pockets app also requires authorization. These enhanced security features complicate attempts to replicate or mimic gameplay interactions between physical playing cards and their digital counterparts on Google and Apple’s mobile payment apps, thanks to the NFCGate device.
Technical evaluation of NGate malware
Preliminary entry
The initial point of entry for this malicious device is typically achieved through deception, where victims are tricked into installing a fraudulent application under the pretext of claiming an overstated income tax refund. This request is frequently sent via SMS, whereupon we deem the messages have been transmitted to arbitrary mobile phone numbers. Regrettably, we were unable to procure samples of these SMS messages, nor were any screenshots made publicly available by the Czech authorities.
Victims are typically tricked into downloading and authenticating an imposter app, whereupon the cybercriminal pretends to be a legitimate financial institution representative via a phone call. The financial institution notifies customers whose accounts have been breached, prompting them to update their PINs and verify their bank cards through a dedicated mobile application. The newly released app, accessible via a single SMS link, has been found to contain the malicious NGate malware. None of the malicious apps we examined were available for download from Google Play.
Two domains were identified as mimics of the Czech Raiffeisenbank (as depicted in Figure 8) and the ČSOB financial institution, where NGate was available for download. At the time of writing, all of them remained lethargic.
![Figure 8. One of the distribution websites (raiffeisen-cz[.]eu) for NGate malware](https://web-assets.esetstatic.com/wls/2024/8-2024/ngate/figure8.png)
Toolset
All six samples of NGate malware exhibit consistent characteristics throughout our analysis. Each pattern leverages an identical bundle title, utilizing a hardcoded phishing URL uniquely identified by a singular ID embedded within the key query parameter to render specific web content. All sample apps were built using the same developer certificates, with a SHA-1 fingerprint of . Throughout the six samples, a consistent pattern emerges, underscoring the uniform quality and deployment of their improvement.
The entire sample’s functionality remains identical with the hardcoded phishing URL; however, each application possesses a unique key associated with it. This unique key links to a specific banking phishing website, designed to deceive unsuspecting victims into revealing sensitive financial information. The provided link is intended solely for redirecting users to a fraudulent website with malicious intent, disguising itself as its intended destination. Based on the analyzed samples, we identified five distinct phishing websites, specifically:
The icons and titles of each pattern have been meticulously crafted to mimic the specific design aesthetics of prominent mobile banking applications, further amplifying their deceptive appearance.
When initially infected, the NGate malware displays a phishing website within a WebView interface. A web view is essentially a self-contained browser window within an application, enabling users to navigate and interact with online content seamlessly. The feature is designed to display net content material or net pages without requiring users to exit the application or open a separate internet browser? The website solicits customers’ personal information, including customer IDs and dates of birth, as shown in Figure 9.
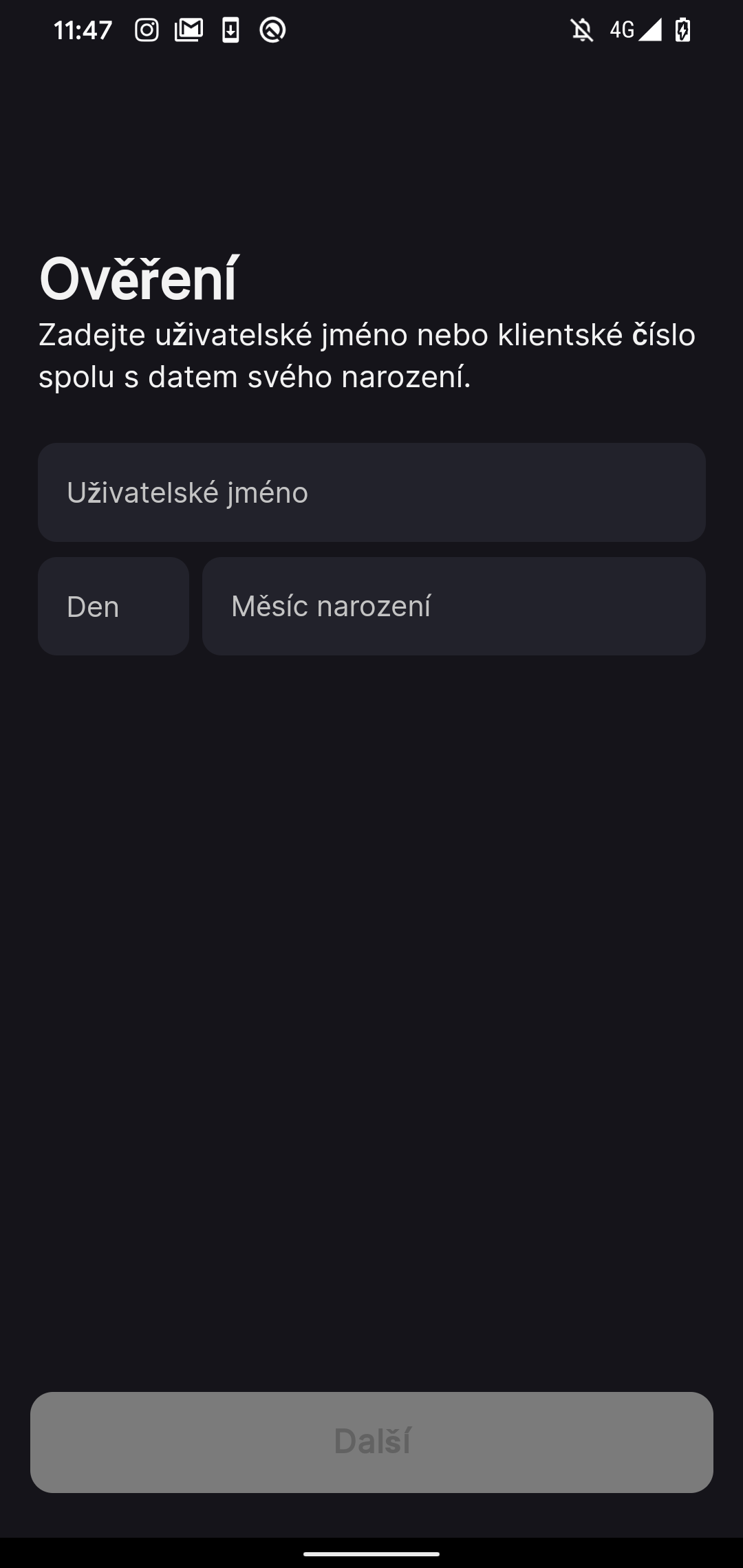
A malicious phishing website deceives victims into not only entering their bank card’s PIN code, but also enabling Near Field Communication (NFC) on their device. When prompted, the individual is directed to position their card at the bottom of their smartphone, unwittingly paving the way for a potential Near Field Communication (NFC) relay attack.
Not like typical malware, NGate doesn’t obtain particular directions from a Command and Management (C&C) server. The compromised device is controlled remotely through the phishing website, enabling hackers to exploit its vulnerabilities. Android features are accessed via a JavaScript interface that enables the execution of specific capabilities. Here is the rewritten text:
This feature set enables the retrieval of gadget-specific information, including model and NFC status, sets up a redirect server for NFC traffic, and initiates an NFC relay attack.
Here is the rewritten text:
The Determine 10 code snippet demonstrates an operation responsible for setting up an NFC relay server, allowing devices to learn from and forward NFC traffic.
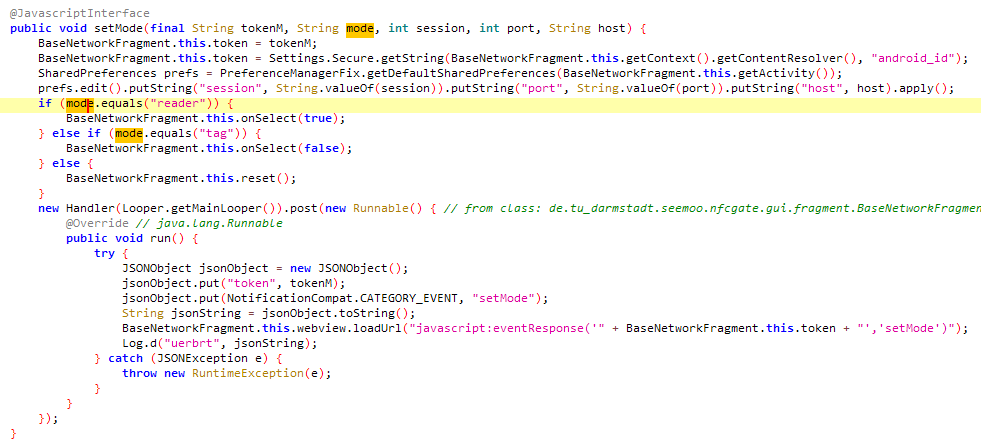
NGate leverages a dual-server infrastructure to efficiently manage its processes. The primary purpose of this website is to deceive users into divulging sensitive information and facilitate the execution of near-field communication (NFC) relay attacks, ultimately compromising their security. The second component is a sophisticated NFC relay server, designed to surreptitiously redirect unsuspecting victims’ devices to the attacker’s command center, thereby compromising their sensitive information and potentially exposing them to further cyber threats? During our initial assessment of the NGate samples, we found that the NFC server’s primary configuration setting may potentially be influenced by responses received from suspected phishing websites. Despite this, subsequent samples of the NGate malware appeared to have these servers hardcoded within them.
If a victim complies with all directives provided by NGate, it enables the attacker to redirect NFC site visitors from the victim’s credit card. This enables attackers to exploit the victim’s financial information for fraudulent transactions, such as withdrawing cash or making payments at contactless payment terminals.
Prevention
To effectively counter sophisticated attacks that exploit vulnerabilities like phishing, social engineering, and Android malware, it is crucial to employ robust protection measures. These steps embody:
- Checking the web site’s authenticity. This can be achieved by carefully examining the URL to verify that the website is not a fraudulent imitation of a genuine one.
- Downloading applications solely from official sources, including the Google Play Store. This precaution significantly minimizes the risk of inadvertently installing malicious software.
- Ensuring the confidentiality of cost card PIN codes remains paramount in today’s digital landscape? All essential data should be consistently stored securely at all times.
- By employing safety applications on mobile devices capable of terminating the installation of potentially unwanted software and malware, such as NGate, thereby preventing harmful downloads. These innovative safety apps provide an enhanced layer of security by continuously scanning and monitoring for potential dangers.
- Disabling NFC functionality on devices when not in use. This step prevents any unauthorised access or data transfer through NFC.
- Implementing protective encasements or RFID card shields to safeguard radio frequency identification cards. With the installation of a barrier that effectively shields against unwanted RFID scans, unauthorized individuals are prevented from siphoning NFC data from the cardboard, thereby ensuring its secure and confidential handling.
- Playing card games on mobile devices via digital interfaces. Digital playing cards are stored securely on devices and can be safeguarded with additional security features like biometric authentication, offering a safer and more convenient alternative to traditional plastic cards.
Conclusion
Researchers at ESET have delved into a sophisticated attack scenario that combines familiar tactics, such as phishing, with a novel malware approach that enables attackers to relay NFC traffic from victims’ physical payment cards to their own Android devices. Prior to leveraging the brand-new NGate malware, the attackers had previously employed a range of tactics to pilfer banking credentials from unsuspecting individuals, initially utilizing Progressive Web Apps (PWAs) and later transitioning to WebAPKs. The sophistication of these attacks testifies to the perpetrators’ unwavering commitment and meticulous approach to carrying out their illegal schemes.
While a specific incident has been thoroughly investigated and identified, it is crucial to acknowledge the potential for further abuse scenarios to exist in theory. These actions could potentially involve the duplication of physical credit cards or accessing near-field communication tokens, possibly escalating the threat’s severity and consequences.
The crimeware marketing campaign targeting the Czech Republic remains active, likely suspended temporarily following the arrest of a suspected individual. The scope for its expansion into various regions or countries cannot be ruled out entirely. Moreover, the actual arrest of one individual with a significant amount of money at their disposal serves as concrete evidence of the severe consequences faced by perpetrators of these “digital” crimes in the real world. It’s crucial to remain vigilant against social engineering tactics, exercise prudence when online, and employ robust mobile security software to safeguard your digital presence.
IoCs
A comprehensive list of Indicators of Compromise (IoCs) and corresponding samples may reside within a .
Recordsdata
| Android/Spy.NGate.B | NGate Android malware. | ||
| Android/Spy.NGate.C | NGate Android malware. | ||
| Android/Spy.NGate.C | NGate Android malware. | ||
| Android/Spy.NGate.C | NGate Android malware. | ||
| Android/Spy.NGate.A | NGate Android malware. | ||
| Android/Spy.NGate.C | NGate Android malware. |
Community
| Internet hosting Ukraine LTD | 2024‑03‑05 | NGate distribution web site. | ||
| Cloudflare, Inc. | 2024‑03‑03 | Phishing web site. | ||
| Divya Quamara | 2024‑04‑07 | NGate C&C server. | ||
| Internet hosting Ukraine LTD | 2024‑03‑12 | NGate distribution web site. | ||
| Serverius | 2024‑02‑21 | NGate C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing of the MITRE ATT&CK framework
| Phishing | Malicious actors have been disseminating NGate through deceptive websites masquerading as legitimate sources. | ||
| Enter Seize: GUI Enter Seize | NGate attempts to surreptitiously acquire sensitive user information by masquerading as a legitimate banking institution through a deceptive phishing WebView. | ||
| System Info Discovery | The NGate tool enables accurate extraction of gadget information, including model type, corresponding Android version, as well as NFC-related details. | ||
| Utility Layer Protocol: Net Protocols | The NGate malware leverages a JavaScript-based interface to transmit and execute malicious commands on infected devices. | ||
| Non-Customary Port | NGate exploits port 5566 to communicate with its server, facilitating the exfiltration of NFC website users. | ||
| Out of Band Knowledge | A vulnerability in NGate allows attackers to secretly siphon off sensitive information from unsuspecting NFC site visitors, exposing them to potential security breaches and data theft. |

