
At least 35 Chrome browser extensions, including ones from cybersecurity firm Cyberhaven, were compromised by a sophisticated phishing campaign targeting developers, allowing attackers to inject malicious code that steals sensitive information.
Investigations into Cyberhaven’s security-focused extension led to a startling discovery: the same malicious code was found in software used by approximately 2.6 million people worldwide, collectively.
Based on experiences shared by focused builders, our latest marketing campaign kicked off on December 5th, 2024. Despite early warnings from BleepingComputer’s discovery of command and management subdomains in March 2024, the issue persisted.
“I wanted to bring to attention a particularly sophisticated phishing email that our team recently encountered, which mimicked a Chrome Extension policy violation notification with the subject line ‘Futile details in the description’.”
“The email contains a suspicious hyperlink resembling the company’s webstore, but actually leads to a phishing website attempting to seize control of your Chrome extensions, potentially replacing them with malicious code.”
A misleading OAuth assault chain
The attack typically commences with a phishing email sent directly to Chrome extension developers or indirectly via a seemingly relevant email linked to their specific domain name.
According to available information, the following domains were utilized in this marketing campaign to disseminate the phishing emails.
supportchromestore.com forextensions.com chromeforextension.com A fake email masquerading as a legitimate notification from Google claims that an extension is non-compliant with Chrome’s internet retailer policies, threatening its potential deletion.
The company strictly prohibits submissions that include misleading, poorly presented, non-descriptive, unrelated, exaggerated, or improper metadata, encompassing but not limited to the extension description, developer title, title, icon, screenshots, and promotional images.
The extension’s developer is compelled to reassess whether their software program’s description contains misleading information that must conform to Chrome Web Store policy guidelines.
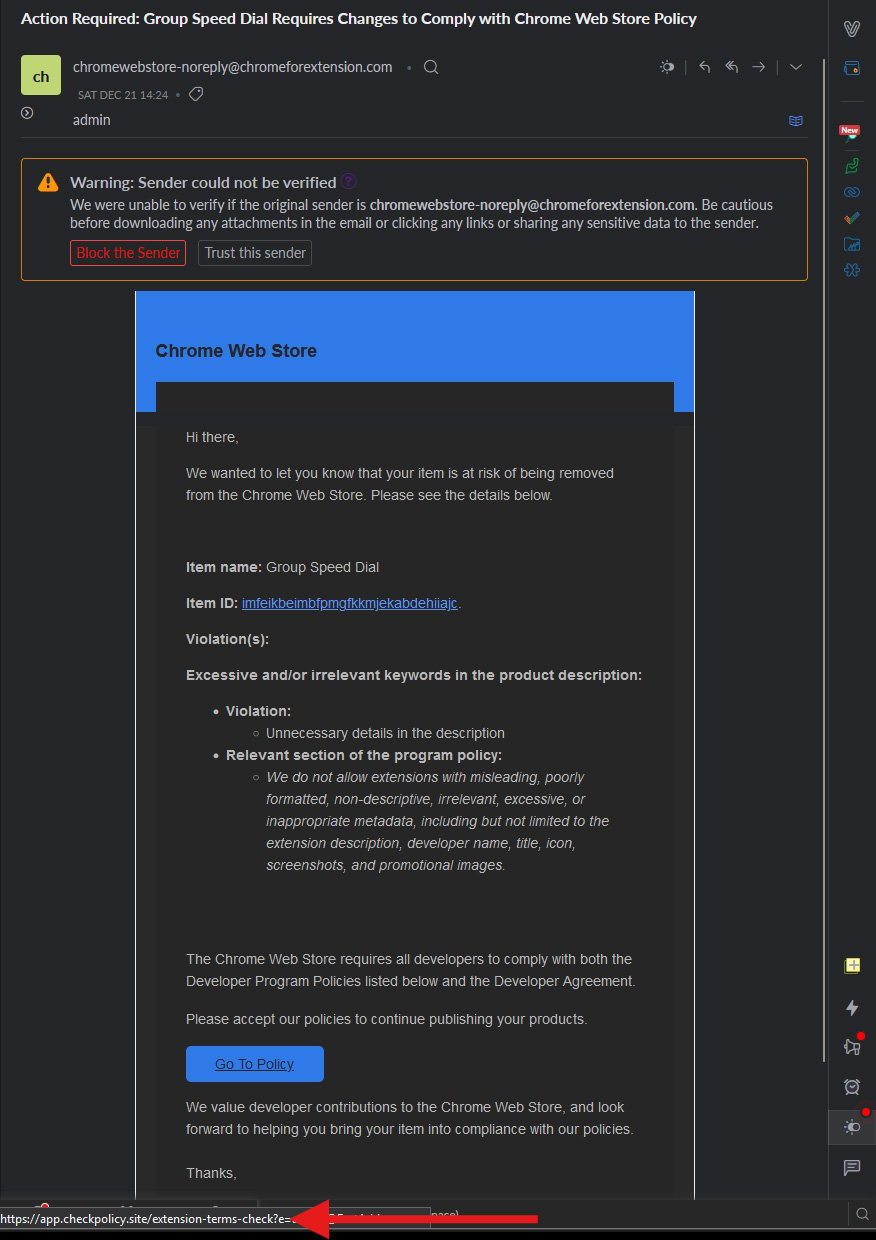
When developers attempt to investigate alleged guideline violations by clicking the “Go To Coverage” button, they are unexpectedly redirected to a legitimate-looking Google login page within their own domain, actually a part of a sophisticated OAuth attack.
The webpage forms part of Google’s commonplace authorization process, intended for securely granting permission to third-party applications to access specific Google account resources.
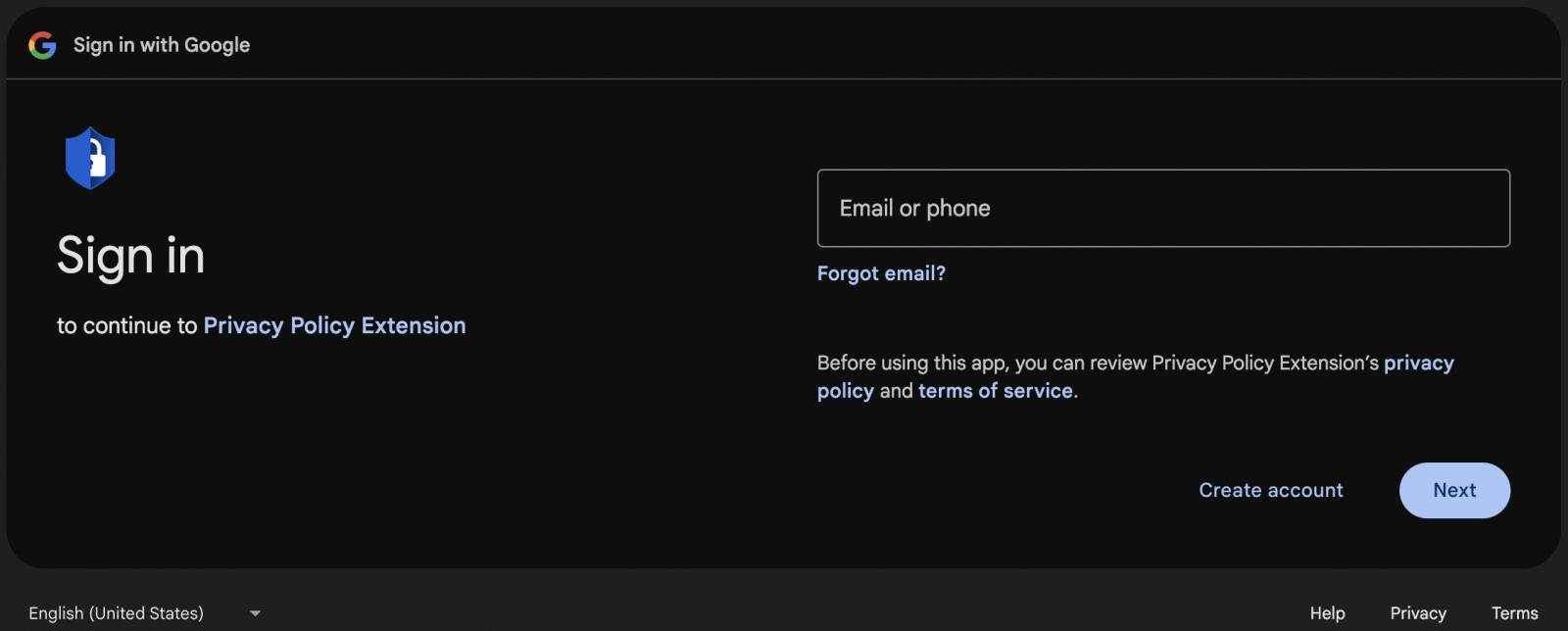
The attacker exploited the platform by hosting a deceitful OAuth application, dubbed “Privateness Coverage Extension”, which tricked victims into authorizing it to manage Chrome Web Store extensions on their behalf.
“If you grant permission for this entry, the Privateness Coverage Extension will be able to: view, modify, update, or share your Chrome Internet Store access to extensions, themes, apps, and licenses.”
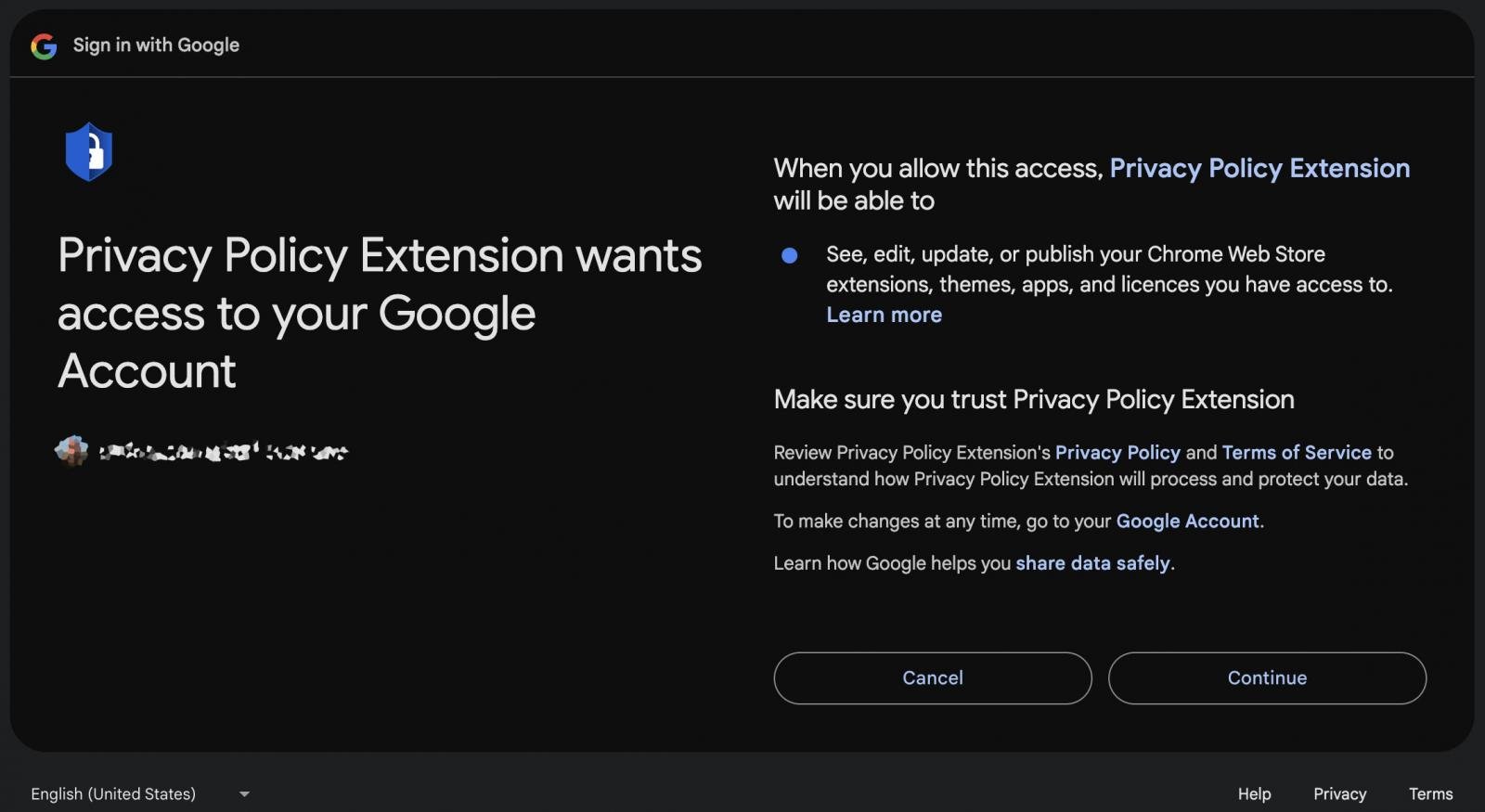
Despite its presence, multi-factor authentication proved ineffective in safeguarding accounts because OAuth authorization flows do not mandate explicit approvals, relying instead on the individual’s comprehension of the permissions being granted.
Upon conducting a thorough investigation into the incident, it was discovered that the employee involved in the process inadvertently accepted the suspicious third-party software, thereby unwittingly permitting its installation.
The employee’s Google account featured Super Vision Safety activated, with Multi-Factor Authentication safeguarding their login credentials. The employee failed to secure a Master of Fine Arts degree promptly. The company’s employee’s Google login details were not breached.
As soon as attackers compromised the extension developer’s account, they injected two malicious files: ’employee.js’ and ‘content.js’, embedding code designed to steal Facebook user data.
The hijacked extension was subsequently exposed as a novel product on the Chrome Internet Retailer platform.
While Extension Whole was directly affected by this phishing campaign, indicators of compromise (IOCs) suggest that many more victims were targeted.
Despite this, malicious actors often pre-register domain names with targeted top-level domains (TLDs), even if they aren’t vulnerable to the attack.
Researchers at BleepingComputer revealed that the malicious actors behind a recent cyberattack had been conducting test runs as early as March 2024, defying the typical pattern of domain creation occurring primarily during November and December.
Concentrating on Fb enterprise accounts
The evaluation of compromised machines has conclusively revealed that the malicious actors were targeting Facebook accounts belonging to customers whose browsing data had been hijacked by the tainted browser extensions.
Notably, a malicious data-stealing code attempted to acquire an individual’s Facebook ID, entry token, personal account details, advertising account information, and business account credentials.
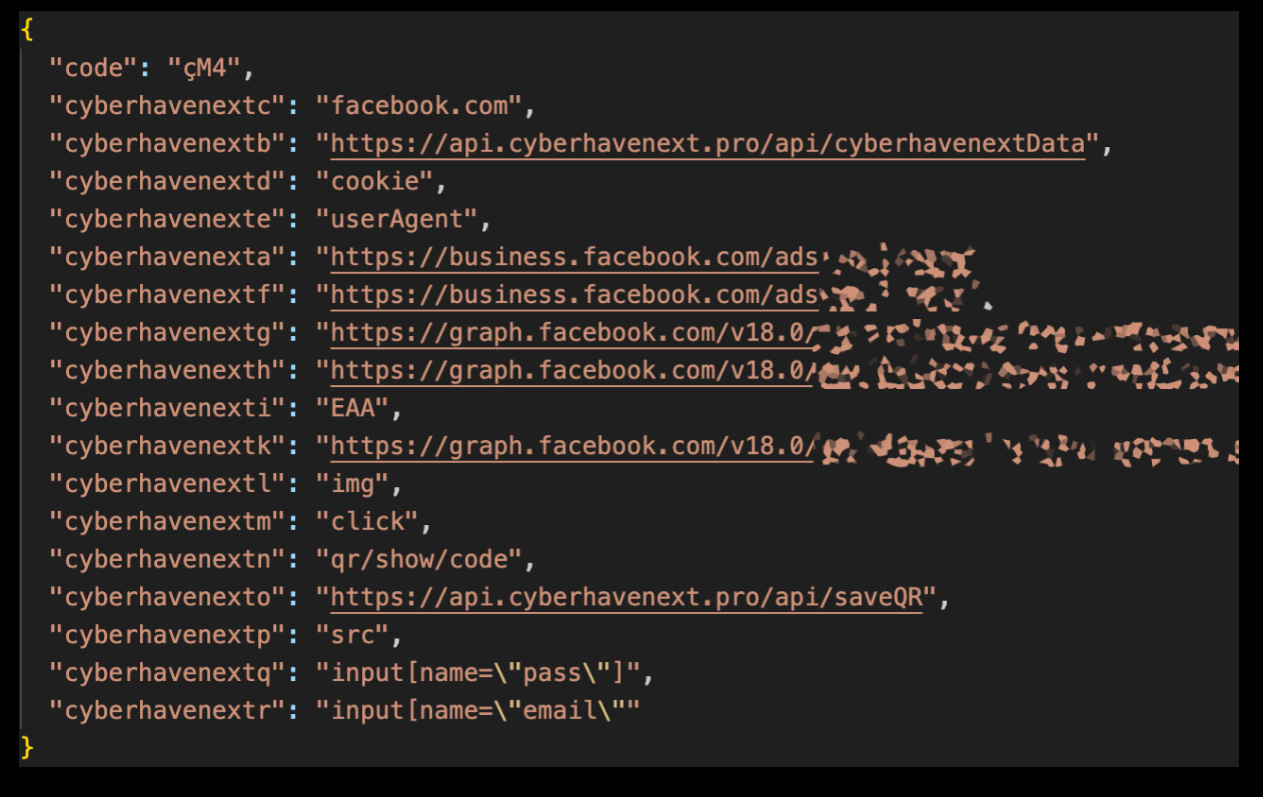
Furthermore, the malware injected an opportunistic mouse click event listener, specifically designed to capture users’ interactions on Fb.com while searching for QR code images linked to the platform’s two-factor authentication or CAPTCHA mechanisms.
Hackers sought to circumvent Facebook’s two-factor authentication (2FA) protocols, thereby enabling them to take control of the targeted account.
Sensitive information pilfered from Facebook accounts can be covertly bundled with cookies, user agent strings, IDs, and other data gleaned through mouse clicks, ultimately exfiltrated to an attacker’s Command and Control (C2) server for manipulation.
Malicious actors have exploited vulnerabilities to directly siphon funds from victims’ credit accounts into their own, launched disinformation and phishing attacks on social media platforms, and profited from compromised credentials by reselling them to other cybercriminals.

