
A newly found Android malware dubbed Crocodilus methods customers into offering the seed phrase for the cryptocurrency pockets utilizing a warning to again up the important thing to keep away from shedding entry.
Though Crocodilus is a brand new banking malware, it options totally developed capabilities to take management of the machine, harvest information, and distant management.
Researchers at fraud prevention firm ThreatFabric say that the malware is distributed through a proprietary dropper that bypasses Android 13 (and later) safety protections.
The dropper installs the malware with out triggering Play Defend whereas additionally bypassing Accessibility Service restrictions.
What makes Crocodilus particular is that it integrates social engineering to make victims present entry to their crypto-wallet seed phrase.
It achieves this via a display overlay warning customers to “again up their pockets key within the settings inside 12 hours” or threat shedding entry to their pockets.
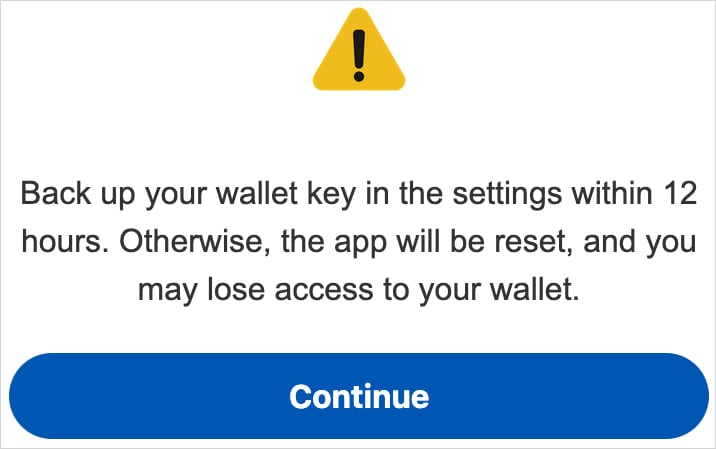
Supply: ThreatFabric
“This social engineering trick guides the sufferer to navigate to their seed phrase (pockets key), permitting Crocodilus to reap the textual content utilizing its Accessibility Logger,” ThreatFabric explains.
“With this info, attackers can seize full management of the pockets and drain it utterly,” the researchers say.
In its first operations, Crocodilus was noticed focusing on customers in Turkey and Spain, together with financial institution accounts from these two international locations. Judging from the debug messages, it seems that the malware is of Turkish origin.
It’s unclear how the preliminary an infection happens, however sometimes, victims are tricked into downloading droppers via malicious websites, pretend promotions on social media or SMS, and third-party app shops.
When launched, Crocodilus positive aspects entry to Accessibility Service, usually reserved for aiding individuals with disabilities, to unlock entry to display content material, carry out navigation gestures, and monitor for app launches.
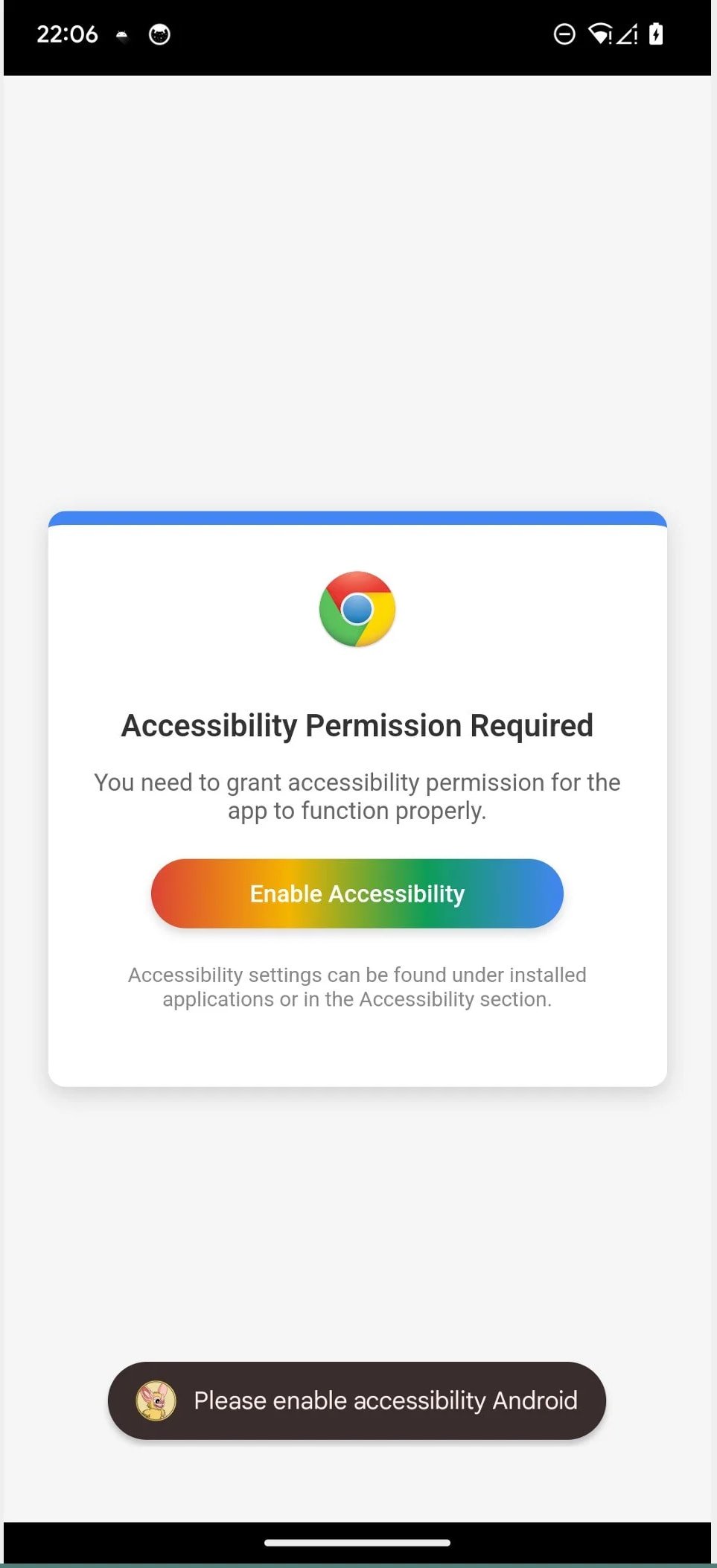
Supply: ThreatFabric
When the sufferer opens a focused banking or cryptocurrency app, Crocodilus masses a pretend overlay on high of the actual app to intercept the sufferer’s account credentials.
The bot element of the malware helps a set of 23 instructions that it might execute on the machine, together with:
- Allow name forwarding
- Launch a selected software
- Put up a push notification
- Ship SMS to all contacts or a specified quantity
- Get SMS messages
- Request System Admin privileges
- Allow a black overlay
- Allow/disable sound
- Lock display
- Make itself the default SMS supervisor
The malware additionally presents distant entry trojan (RAT) performance, which allows its operators to faucet on the display, navigate the person interface, carry out swipe gestures, and extra.
There’s additionally a devoted RAT command to take a screenshot of the Google Authenticator software and seize one-time password codes used for two-factor authentication account safety.
Whereas executing these actions, Crocodilus operators can activate a black display overlay and mute the machine to cover the exercise from the sufferer and make it seem as if the machine is locked.
Though Crocodilus seems to have a selected focusing on restricted to Spain and Turkey proper now, the malware may develop operations quickly, including extra apps to its goal record.
Android customers are suggested to keep away from downloading APKs from exterior Google Play and to make sure that Play Defend is all the time lively on their units.


