Microsoft’s Threat Intelligence team has identified a novel attack campaign launched by the notorious Russian threat actor, Midnight Blizzard, targeting thousands of users across more than 100 organizations. Attackers leverage spear-phishing emails containing RDP configuration files, enabling them to potentially gain unauthorized access to compromised systems.
The comprehensive assault marketing campaign successfully targeted thousands of individuals across various sectors, including higher education, security, non-governmental organizations, and government agencies. Dozens of countries have been affected, with significant impacts observed in the UK, Europe, Australia, and Japan, consistent with previous Midnight Blizzard phishing attacks.
Phishing emails were found to harbour a Remote Desktop Protocol (RDP) configuration file.
Victims received highly targeted phishing emails leveraging social engineering tactics centered on Amazon Web Services and the concept of Zero Trust.
According to Microsoft Risk Intelligence, the malicious actors dispatched the emails using email addresses affiliated with professional organizations that were compromised in previous attacks. The emails consistently carried a RDP configuration file, digitally certified by a freely issued Let’s Encrypt certificate, which stored multiple sensitive parameters.
Upon opening the file, an unsecured Remote Desktop Protocol (RDP) connection was enabled, allowing hackers to initiate a session with their maliciously controlled device. The configuration of the established RDP connection would permit the malicious actor to collect information about the targeted system, including files and folders, network drives, peripherals such as printers, microphones, and graphics cards.
This innovative solution will also enable the collection of clipboard data, Windows Hello-based net authentication, passkey usage, and secure key storage, as well as integration with Point-of-Sale terminals. Such a connection could potentially allow a malicious actor to install malware on the targeted system or mapped network shares.
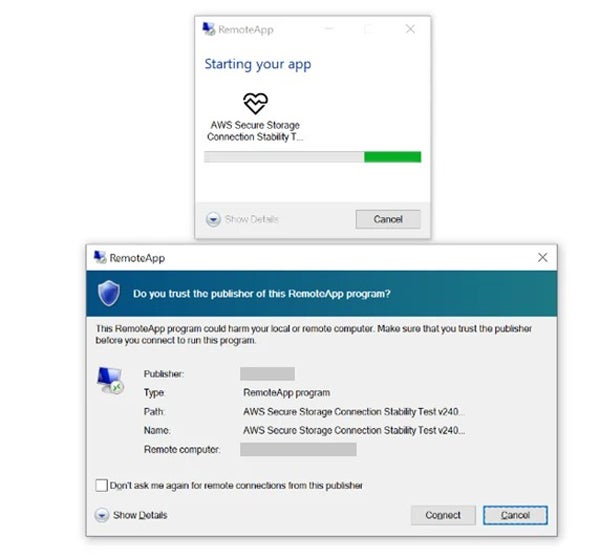
Outbound RDP connections were initially set up to mimic AWS domains, deceiving the target into thinking they were legitimate AWS domains. Amazon swiftly collaborated with Ukrainian authorities to promptly implement measures to impede the malicious activities by seizing affected domains and disrupting the operation’s functionality. While Microsoft acted swiftly, it promptly informed affected customers whose information had been accessed or stolen.
In recent years, Midnight Blizzard has concentrated its efforts across multiple industries.
According to a joint cybersecurity assessment, Midnight Blizzard, which poses a threat alongside malicious actors APT29, Cozy Bear, and the Dukes, is linked to the Russian Federation’s Foreign Intelligence Service.
Since at least, Midnight Blizzard has consistently targeted U.S., European, and global entities within the Protection, Technology, and Financial sectors, carrying out sophisticated cyberespionage campaigns to support further cyber operations.
In January 2024, Microsoft and Hewlett Packard Enterprise gained unauthorized access to email archives belonging to multiple employees. After the incident, Microsoft revealed that initial attacks targeted email accounts seeking information related to the Midnight Blizzard project.
In March 2024, the malicious actor is expected to shift their attention to additional cloud environments.
According to Microsoft, Midnight Blizzard is considered a highly elusive and covert cyber threat actor. A recent Microsoft report highlights that the group had previously disabled the group’s Endpoint Detection and Response features following a system restart. As they patiently waited for a full month, they seized the opportunity presented by vulnerable computer systems that had yet to be updated with critical patches.
The Menace actor, capable of being extremely technical, was observed deploying a malicious Dynamic Link Library (DLL) onto the servers of Lively Listing Federated Companies to maintain persistence and siphon sensitive information. The Midnight Blizzard software also allows for token generation, enabling it to circumvent Active Directory Federation Services (AD FS) policies by impersonating any user.
As temperatures plummet and the winds howl, it’s crucial to master the art of shielding against a Midnight Blizzard. To begin with, ensure you’re equipped with top-tier gear, including high-quality armor and a trusty shield. When the storm hits, anticipate the blizzard’s fury by watching out for telltale signs like swirling snow clouds and an eerie green glow on the horizon. As the first gusts hit, swiftly raise your shield to deflect the initial assault, taking care not to overextend yourself by getting too close to the maelstrom’s epicenter.
Multiple measures can be implemented to counteract this threat.
- Outbound RDP connections to external or public networks should be strictly prohibited or heavily restricted.
- Remote Desktop Protocol (RDP) files must be prevented from being accessed by email clients or webmail.
- RDP (Remote Desktop Protocol) files containing executable code must be prevented from running by end-users.
- Multi-factor authentication should be enabled wherever attainable.
- To mitigate phishing attacks, organizations must deploy robust authentication strategies, specifically leveraging the capabilities of FIDO-based tokens. SMS-based MFA should not be utilized, as it may be circumvented by SIM-jacking attacks.
- Conditional Entry Authentication Powers should be leveraged to mandatorily enforce phishing-resistant authentication.
Moreover, organizations should deploy Endpoint Detection and Response (EDR) solutions to detect and respond promptly to suspicious activity. Organisations must also consider deploying robust antiphishing and antivirus solutions to effectively detect and block such threats.

