How To
Ever taken a peek at what Google has to say about you? Were you satisfied with what arrived on your doorstep? Consider requesting removal of personal information from search results to ensure privacy protection.

In today’s digitally saturated era, safeguarding control over one’s personal data has never been more crucial. Whether concerns about privacy, security, or simply managing your online presence drive your inquiry, understanding how to minimize your visibility in search results is an invaluable skill.
Let’s explore the reasons why you might want to use incognito mode when searching online, along with tips on how to protect your data from unwanted exposure using Google Search.
Search results from various sources such as websites, articles, and other online content.
Let’s start by examining how our website displays titles and various data online, as well as identifying any potential privacy concerns that may arise.
“When Google Knows Your Name: ‘AI Weirdness’ Director Tim Urban” Typically, it’s your online presence, such as a social media profile, blog, or professional website.
Refine your search with a further parameter by incorporating a specific keyword, such as a well-known website (e.g., Google), or perhaps the name of your street or a notable landmark, to significantly narrow down the results and ensure you find exactly what you’re looking for. Notably, search results become increasingly precise, highlighting the impressive capabilities of search engines in pinpointing an individual’s expertise.
If you’ve listed an email address on a company website, details can easily be collated to create a comprehensive picture of your online persona, often including your interests, habits, and affiliations. Despite its benefits, this accumulation of data may also have several drawbacks.
The hazards of social engineering
As a staggering 68% of all knowledge breaches were found to have been triggered by human error. A significant portion of these incidents stemmed from unsuspecting individuals succumbing to various forms of social engineering, including sophisticated phishing tactics, pretexting schemes, fraudulent email scams, and coercive extortion attempts.
Malicious individuals can leverage readily available public data to execute sophisticated social engineering attacks. These schemes aim to deceive individuals into sending money or divulging sensitive information, such as account credentials.
Are you tired of searching for the same information over and over? With Google’s advanced search features, you can easily manage your knowledge and streamline your research. Here are a few tips to get started:
* Use the “I’m feeling lucky” button: This feature allows you to bypass the search results page and go directly to the top result.
* Utilize filters: Google offers various filters that allow you to refine your search by date, region, and more.
By implementing these simple strategies, you can improve your online research skills and become a master of finding the information you need.
As you reflect on the insights gathered during your journey, think critically about how they intersect with the preceding discussion of fraudulent schemes.
Consequently, Google responded to users’ concerns that their personal information was just a search away by introducing various tools to help users manage their data effectively. Google also provides a tool called “Digital Garage” that enables users to track their online presence and see if sensitive information such as their home address, phone number, or email address appear in search results.
To leverage Google’s “About Me” feature for personal branding and online reputation management, follow these steps:
Firstly, claim your custom URL by verifying your identity via phone or email. Then, optimize your profile with relevant keywords that best describe your professional background, skills, and achievements.
Next, ensure your contact information is accurate and up-to-date, including your email address, phone number, and physical address. This will facilitate connections with potential clients, employers, and collaborators.
Thirdly, utilize the “Posts” feature to share updates about your projects, accomplishments, and expertise. You can even embed videos, images, or links to make your content more engaging.
Moreover, take advantage of the “Reviews” section by requesting feedback from satisfied clients, colleagues, or mentors. This will help establish a strong online reputation and boost credibility.
Finally, regularly monitor and update your profile to reflect changes in your professional journey, ensuring that it remains an accurate reflection of who you are and what you do.
To effectively utilize this feature, having a valid Google account is highly recommended. You can access it through a browser on your computer or via the Google app on your mobile device.
, comply with these steps:
- Sign in to your Google account, navigate to your profile picture, and click on it.
- Select “Manage your Google Account,” then navigate to “Privacy & personalization.”
- In the Historical Past settings, select “My Exercise” and then “Different Exercise”.
- Discover and click on “Manage Outcomes About You”.
Choose either “Get Started” or “Settings”. Enter the information you’d like to find, such as personal names, phone numbers, or physical addresses. You can also customize notifications to alert you when Google detects results connected to your personal information.
Click on your Google Account’s profile avatar within the Google account settings and navigate to the “About me” or “Manage Your Google Profile” section, where you’ll find the option to view or edit your publicly visible information.
As the search concludes, you’ll receive timely notifications upon its completion. If the desired outcomes are not satisfactory, you may opt to discontinue through the predetermined mechanism.
Please remove all unnecessary search outcomes from this database to streamline our results and reduce confusion.
Can you also ensure that any remaining entries are thoroughly reviewed for relevance and accuracy? This will help prevent any irrelevant data from being displayed.
To prevent unwanted exposure, you can also submit a direct request to Google to evaluate and remove search results that meet specific criteria, such as exposing your email address or home address, login credentials, or other personal details?
To initiate a removal request, start by completing the necessary details from the provided template.
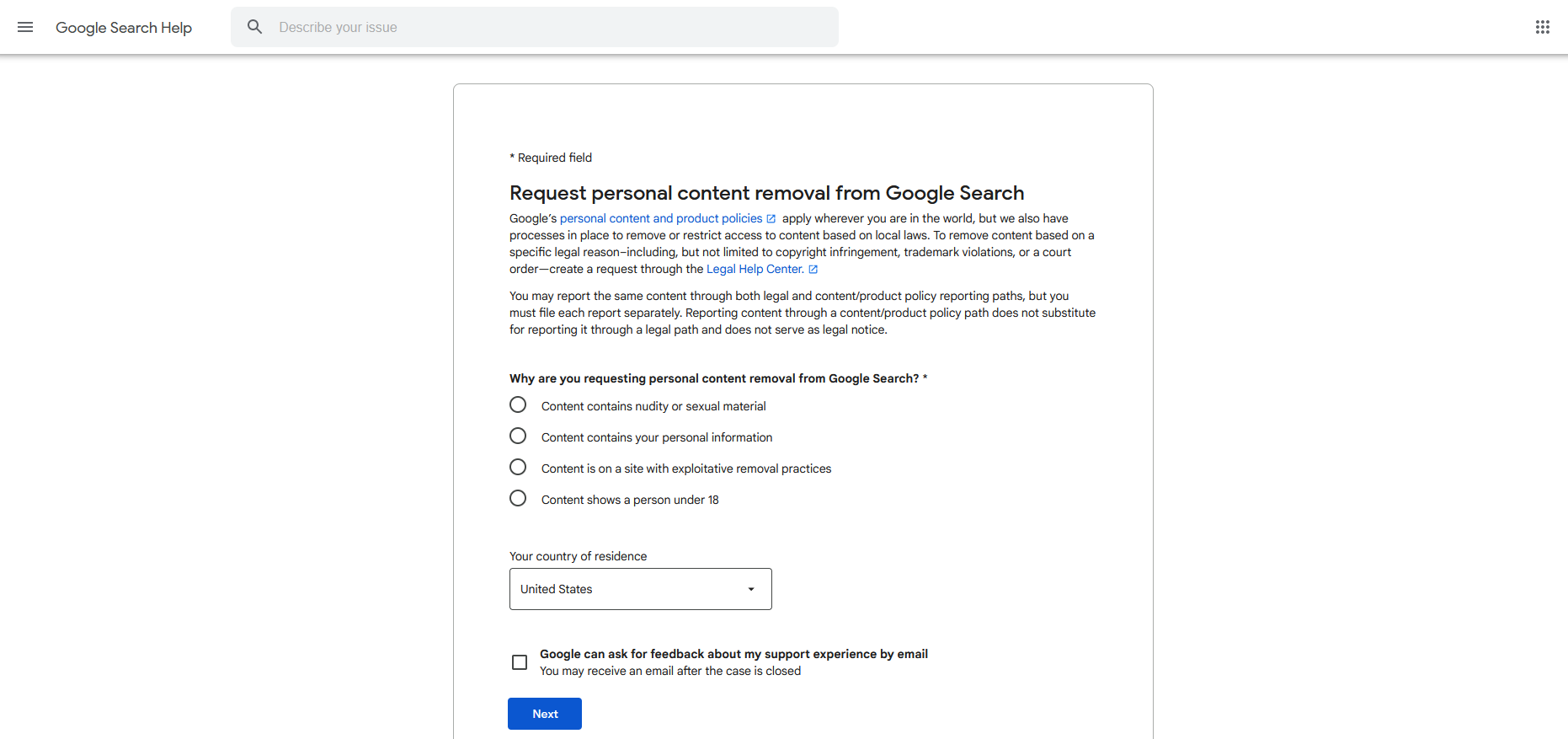

If the difficulty cannot be definitively diagnosed or Google needs supplementary information to accurately identify the problem, a request will be sent via email seeking further clarification.
Cybersecurity, privacy, and a scam-free existence.
While some people are comfortable sharing their personal information online, others prioritizing privacy will not. While prominent individuals and institutions may have a duty to share their expertise publicly, they must also be mindful of the need to safeguard certain information to prevent privacy and security breaches.
By restricting your online presence, you can easily maintain a private life. Ultimately, success hinges on grasping which personal data is publicly available and remaining proactive to thwart potential threats before they materialize.

