Recent research from cybersecurity firm Netskope uncovers disturbing details about coordinated attack campaigns exploiting vulnerabilities in Microsoft Sway and CloudFlare’s Turnstile, with attackers employing QR codes to deceive users into surrendering their Microsoft Office login credentials to the malicious platform.
These initiatives have targeted individuals in Asia and North America across multiple sectors driven by expertise, production, and financial services.
What’s quishing?
Offering a convenient way to access websites or enter data without requiring manual URL input on a mobile device. While QR codes offer convenience and efficiency, they also pose a risk of being exploited by cybercriminals to direct users to malicious content.
Quishing refers specifically to the act of redirecting unsuspecting individuals to harmful websites or tricking them into downloading malicious software by prompting them to scan a suspicious QR code. As you arrive at the site, hackers swiftly set out to plunder your sensitive financial and personal information. The unpredictability of QR codes’ destination following a scan is inherently unclear to consumers.
According to Thomas Damonneville, head of anti-phishing firm, phishing has become a burgeoning trend, posing a significant threat as its simplicity makes it increasingly difficult to distinguish between authentic and fraudulent content.
What’s driving you to think about Quishing and Microsoft Sway?
In July 2024, the researchers at Netskope’s Menace Labs discovered a staggering 2,000-fold surge in website traffic directed towards phishing pages through Microsoft Sway. Most malicious web pages employed QR codes.
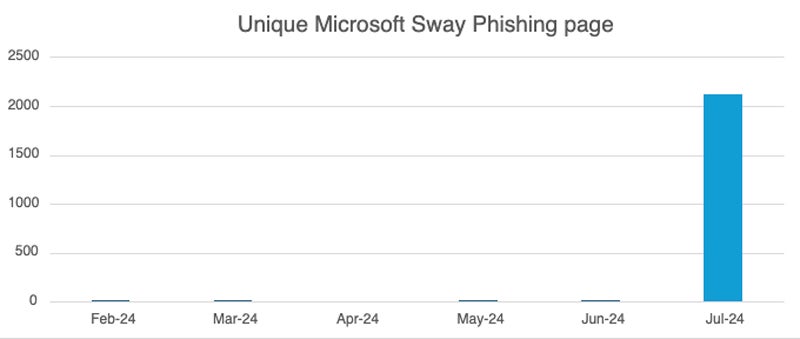
Microsoft Sway is a complimentary internet application from the Microsoft Workplace suite that enables users to easily craft interactive stories, presentations, or other digital content with minimal effort. As the app becomes freely available, it presents a tantalizing target for malicious hackers.
Netskope’s researcher, Jan Michael Alcantara, has uncovered malicious assault campaigns that target victims with Microsoft Sway pages designed to execute phishing attacks and steal Microsoft Office 365 login credentials.
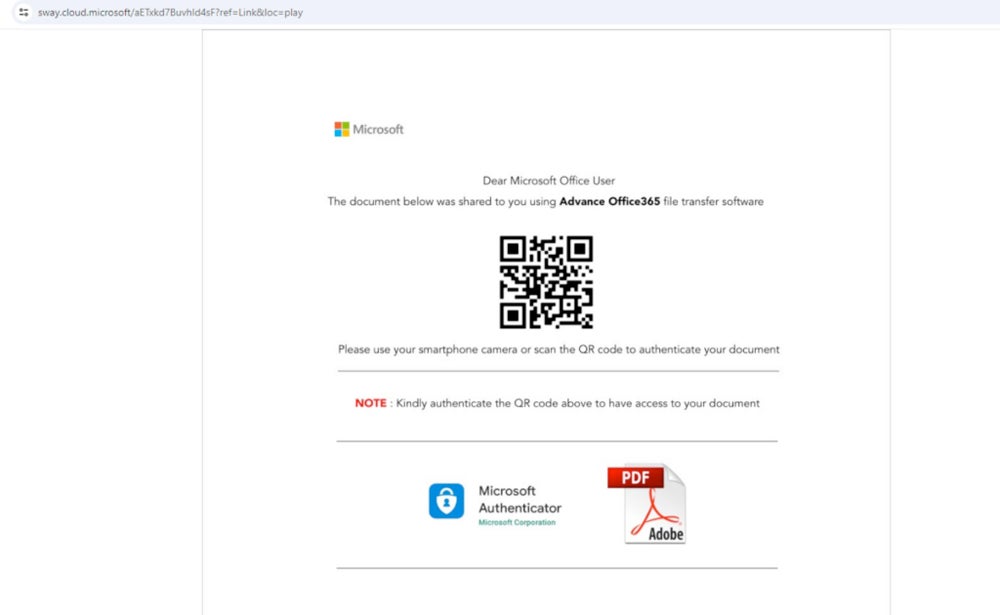
Netskope’s analysis fails to detail the manner in which fraudulent hyperlinks are disseminated to unsuspecting individuals. Despite these limitations, it is still possible to expand these connections through email, social networks, SMS, or instant messaging software.
The ultimate payload bears a striking resemblance to Microsoft’s reputable Workplace login webpage, discovered by the same researcher in May 2024.
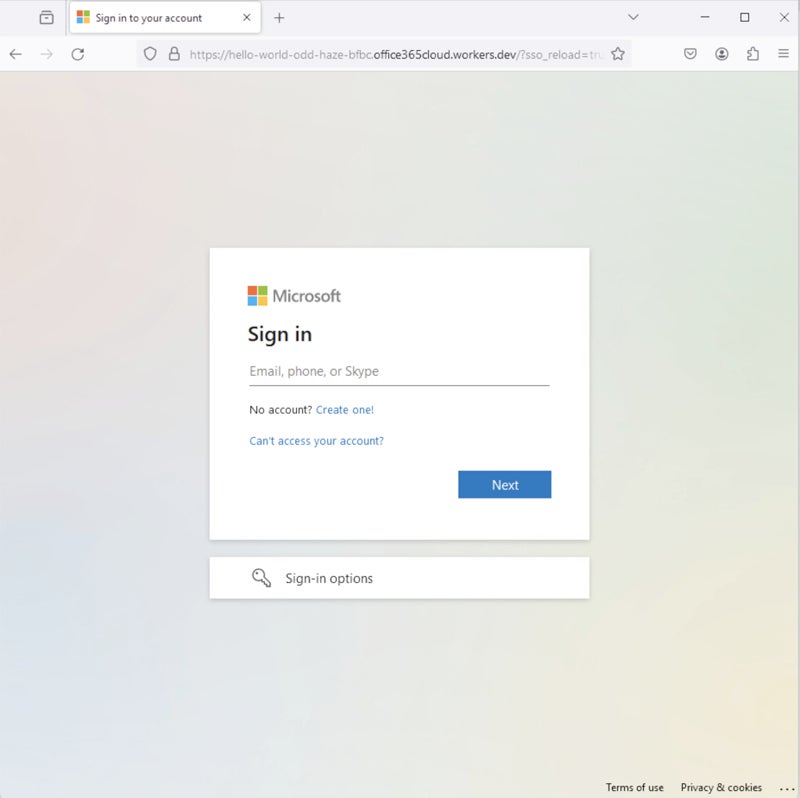
Stealthier assault utilizing CloudFlare Turnstile
CloudFlare’s Turnstile offers a free solution to replace traditional captchas, which have been exploited in reported attacks and are vulnerable to abuse. The Turnstile solution empowers website administrators to seamlessly integrate its verification code into their content, allowing users to effortlessly authenticate via a clickable code rather than navigating a traditional CAPTCHA.

By leveraging this no-cost tool, attackers find it intriguing that users are initially prompted to activate Cloudflare’s Turnstile before being redirected to the phishing webpage, necessitating an explicit click. This provides a layer of safety against detection for the attacker, as the ultimate phishing payload remains hidden from online URL scanners.
Attacker-in-the-middle phishing method
Phishing tactics typically obtain user credentials before presenting a misleading error message or redirecting the individual to what appears to be their authentic login page? This strategy’s unintended consequence is that customers may mistakenly believe their login information was incorrect, potentially remaining oblivious to the fraudulent activity.
The attacker-in-the-middle phishing technique exhibits exceptional subtlety. Consumer credentials are swiftly utilized to authenticate and seamlessly log in to the relevant service. This methodology, also known as transparent phishing, enables users to be swiftly authenticated following the unauthorized credential capture, thereby diminishing the attack’s detectability.
Malicious QR code detection difficulties
“No one can learn a QR code solely through their own visual inspection,” Damonneville said. “You can simply scan documents using your smartphone.” While some hyperlinks might be excessively long to test thoroughly, do people actually verify them?
Textual content-based detections are often ineffective against QR codes, as they are image-based entities. Currently, there is no universally accepted standard for validating the legitimacy of a QR code. The lack of standardised safety mechanisms for digital signatures on QR codes poses a significant challenge in verifying the authenticity and integrity of the transmitted data.
To mitigate the risk of QR code phishing, consider implementing the following measures: implement authentication mechanisms such as SSL/TLS for secure data transmission; ensure that your users understand how to verify the authenticity of a QR code by checking the URL it directs to, and educate them on how to report any suspicious activity.
Some QR code readers offer a pre-scan preview of the URL, allowing customers to view the destination address before actually scanning the code. Any hint of suspicious activity surrounding a URL should prompt consumers to exercise caution and refrain from using the associated QR code. Moreover:
- QR codes triggering actions linked to login or data exposure should raise significant alarm bells and necessitate meticulous scrutiny.
- Implementing additional safety options could potentially enhance security by detecting and blocking suspicious phishing URLs. URLs should always be scanned by such an instrument.
- Shouldn’t transactions be facilitated through secure means, rather than relying on a QR code, unless you’re certain of the recipient’s credibility?
Microsoft Sway isn’t a singularly respectable product that’s often targeted by cybercriminals to host phishing pages.
“We’re frequently seeing reputable websites or platforms exploited to host malicious activities like quishing or phishing, including Github, Gitbooks, and Google Docs, among others, every day,” the expert said. “To omit mentioning the numerous URL shortening services and free web hosting platforms widely utilized for simplifying URLs.”
The importance of distinguishing between trustworthy and deceitful URLs is reiterated, emphasizing the need for heightened customer awareness and employee education.

