
North Korea’s hacking collective, ScarCruft, mounted a massive cyberattack in May that exploited an Internet Explorer zero-day vulnerability to infect targets with the RokRAT malware and steal sensitive data.
ScarCruft, also known as APT37 or RedEyes, is a state-sponsored threat actor that has been observed targeting individuals and organizations in South Korea and North Korea, as well as North Korean human rights activists and defectors. The group’s tactics include phishing, watering hole attacks, and social engineering.
South Korea’s Nationwide Cyber Safety Center, in partnership with AhnLab’s ASEC division, has unveiled a report detailing the “Code on Toast” ScarCruft campaign, a novel tactic that utilizes toast-style pop-up ads to silently infect targets with zero-click malware.
The vulnerability exploited in zero-day attacks is tracked as CVE-2023-2523 and is a critical severity remote code execution (RCE) flaw in Microsoft Internet Explorer.
The UK’s National Cyber Security Centre (NCSC), along with ASEC, swiftly responded to a marketing campaign by demonstrating their expertise as they worked closely with Microsoft to address the vulnerability CVE-2024-39178 in August 2024.
The researchers found a striking resemblance between ScarCruft’s exploit and their previous work on CVE-2022-41128, with the added twist of three distinct code snippets engineered to evade Microsoft’s initial mitigations.
From ‘Toast advertisements’ to malware
Toast notifications are popup windows typically appearing in the corner of software programs like antivirus or freeware applications, used to display alerts, messages, and advertisements.
According to AhnLab, cybercriminals from APT37 exploited a vulnerability in a popular, free software widely used by millions of South Koreans, compromising one of many servers of a home-promoting company to deliver carefully crafted “Toast” ads.
The malicious commercials employed an iframes that, when rendered by Internet Explorer, triggered the execution of a distant JavaScript file named ‘ad_toast’ via the exploit of the CVE-2024-39178 vulnerability in Internet Explorer’s JScript9.dll file, leveraging its Chakra engine.
The malware deployed in this attack is a variant of RokRAT, a strain that ScarCruft has leveraged in its operations for several years, showcasing the group’s persistence and adaptability in utilising evolving threats to further their malicious objectives.
RokRAT’s primary purpose is to surreptitiously extract and transmit data corresponding to 20 specific file types – including but not limited to .doc, .mdb, .xls, .ppt, .txt, and .amr – to a Yandex cloud storage facility every half hour.
The malware engages in keylogging, logs clipboard changes, and takes screenshots at three-minute intervals.
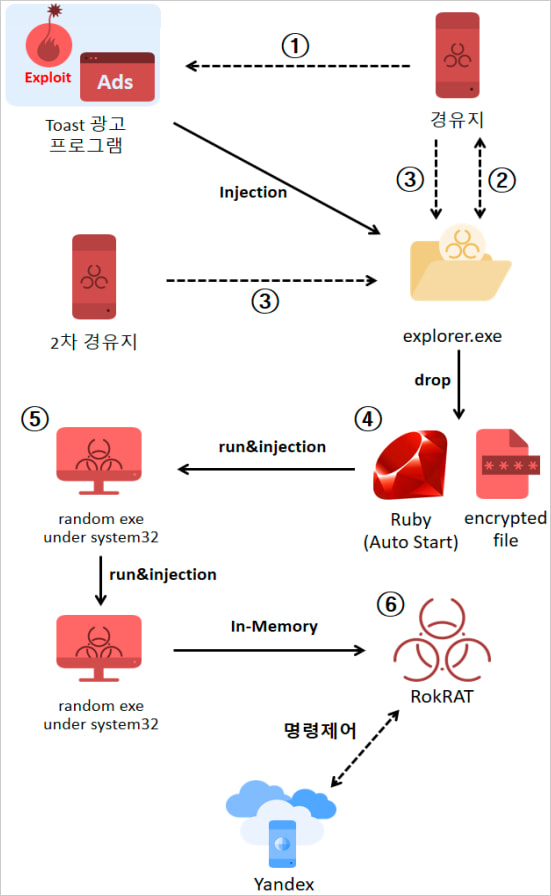
A malicious infection is delivered through a four-stage process, wherein an identical quantity of payloads are injected into the “explorer.exe” process, successfully circumventing security software’s detection capabilities.
If Avast or Symantec antivirus software is detected on the host, the malware will be injected into a randomly selected executable within the C:\Windows\System32 folder as an alternative.
By incorporating a discreet executable file (‘rubyw.exe’) into Windows’ startup sequence, persistence can be ensured through scheduling its periodic execution every four minutes via the operating system’s built-in task scheduler.
Despite Microsoft’s efforts in mid-2022, many components of the browser remain embedded within Windows or are leveraged by third-party software, allowing threat actors to exploit these vulnerabilities in their attacks.
Without customers realising, outdated software programmes can quietly harbour vulnerabilities, making them vulnerable to zero-click attacks and setting the stage for mass-scale exploitation by sophisticated threat actors.
Despite Microsoft’s prompt acknowledgement of the Web Explorer vulnerability in August, there remains a significant concern that legacy devices may not quickly adopt the fix due to outdated hardware components. Given that free software programs relying on outdated Internet Explorer components persistently puts users at risk.
BleepingComputer has inquired about the number of affected users and the name of the vulnerable free software program, and we will provide further information as it becomes available.

