
Picture: Shutterstock, iHaMoo.
He remains incredulous about being swindled out of nearly half a million dollars’ worth of cryptocurrencies with such haste. A fraudster exploited an authentic phone number to notify his Gmail account of suspected hacking, then sent urgent email security warnings from google.com, culminating in taking control of the account after convincing the user to grant access with a “yes” response on their mobile device.
As a battalion chief firefighter in Seattle, Griffin received an alarming call on May 6: someone claiming to be from Google Support alerted him that his account was being accessed from Germany, purportedly without his knowledge or consent. The initial search results for the mysterious phone number led me to discover that it belonged to, a cutting-edge AI-powered service capable of facilitating engaging two-way conversations.
At roughly the same moment, he received an email notification from Google.com, alerting him that his account had been compromised. The email contained information regarding a “Google Help Case ID” and particulars about the supposed phone conversation with a Google consultant, detailing his title as “Ashton”, mirroring the same title provided by the caller to him on the phone.
Although Griffin didn’t study this until much later, the email he received had a genuine Google.com address because it was sent via SurveyMonkey, a service available to all customers that makes it easy to send surveys, quizzes, and other communications.
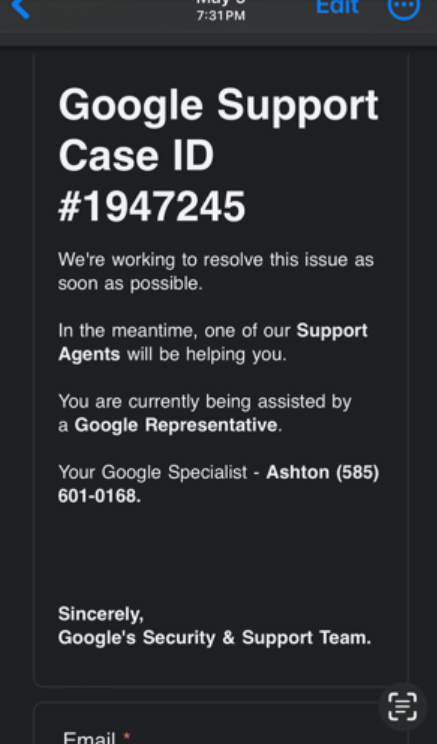
A bogus safety alert that Griffin had procured prior to his bitcoin heist via Google Forms.
According to Tripwire.com’s warnings, scammers might exploit Google Forms by crafting a deceptive safety alert message and then manipulating the form’s settings to automatically distribute identical copies of the completed form to any email address entered, potentially spreading misinformation. The attacker sends a fake completion invitation to themselves, not the intended victim.
Accordingly, when the attacker receives an invitation to complete the form, they proceed by filling it out, subsequently entering their intended victim’s email address into the form rather than their own. The attackers are exploiting the fact that Google Forms sends emails immediately from the google.com domain. This longstanding reputable region enhances the appearance of an email, making it significantly less susceptible to being intercepted by email-filtering systems as it travels.
The faux Google consultant exuded a sense of professionalism, displaying mannered affability, technical expertise, and confidence-inspiring reassurance. Ashton informed Griffin that he would procure a notification allowing them to potentially reclaim control of the compromised account from the hackers. A message from Google suddenly popped up on his phone, inquiring: “Are you trying to recover your account?”
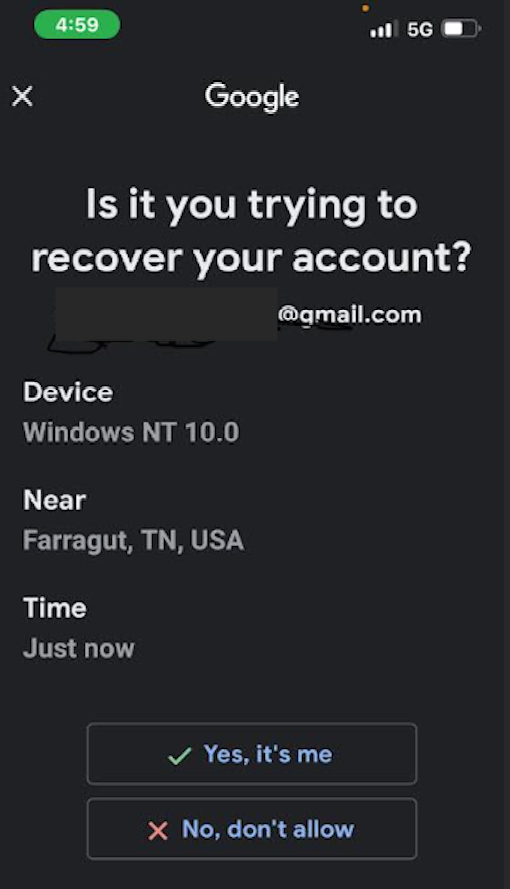
On May 6, Adam Griffin swiftly approved the account restoration notification, mirroring this identical prompt.
After receiving a pop-up notification from Google on his phone, Griffin felt reassured that he was actually interacting with someone at the tech giant. The thieves managed to gain access to Griffin’s phone by exploiting Google’s account recovery process for his Gmail address simply by passing through it.
“When I clicked ‘yes’, I swiftly granted access to my Gmail account, which was already synced with,”
Unfortunately, Griffin’s mistake lies in having stored the password for his cryptocurrency wallet on an unsecured platform like Google Photos years ago. With this crucial information, scammers may swiftly deplete his entire account balance.
As Griffin reflected on the situation, she remembered that from that point onward, they were able to transfer approximately $450,000 from her Exodus account to their own.
Immediately following the grant of access to his Gmail account, Griffin received a call from a purported Coinbase representative, who informed him that someone in Germany was attempting to take control of his account.
A subsequent inquiry revealed that Griffin’s attackers exploited his compromised Gmail account to gain access to his Coinbase profile via a VPN link in California, subsequently leveraging his Google Authenticator app to obtain the multi-factor authentication code. What’s more, users often remained unaware that Google Authenticator also stores the same codes within their online Google account settings.
When would-be thieves attempted to siphon a substantial $100,000 worth of cryptocurrency from his account, Coinbase swiftly intervened by sending an email notifying him that the account had been temporarily frozen, requiring additional verification documentation before any transactions could be processed.
GRAND THEFT AUTOMATED
Just two weeks after Griffin’s ordeal, a cunning scam artist posing as Google successfully phished 45 Bitcoins, equivalent to approximately $4,725,000 at today’s value, from a 42-year-old tech professional in northern California. Tony agreed to share his harrowing expertise on condition that his professional title would remain confidential.
After a successful first venture into Bitcoin in 2013, Tony resumed his investment in the digital currency and has continued to do so consistently ever since. On the evening of May 15, 2024, Tony gently tucked in his three- and one-year-old sons before retiring to bed when he received an unexpected message from Google about an account security issue, swiftly followed by a phone call from “Daniel Alexander” at Google, who informed him that his account had been compromised by hackers.
With a mix of surprise and embarrassment, Tony revealed that he had unwittingly enrolled in Google’s artificial intelligence platform, previously known as “Bard”, and had misinterpreted the opportunity as a feature within the service itself. Daniel warned Tony that someone in Frankfurt, Germany was accessing his account and advised him to click “yes” as soon as a notification from Google arrived on his phone to verify and regain access.
The Google search results immediately appeared just a few seconds later. As he would forever regret, Tony’s cursor drifted down to the “Sign in” confirmation.
Then came another anonymous submission, reportedly from a security expert at a prominent company specializing in developing tamper-evident and secure hardware solutions for storing cryptographic keys and sensitive data offline. A request was submitted to suspend the caller’s Trezor account, reportedly from their own Gmail address, which forwarded unusual information including name, social security number, date of birth, address, phone number, and email address to Tony for unknown reasons.
After verifying the transaction history on his Trezor account, Tony began to suspect that his digital wallet had indeed been breached. The unsuspecting individual was tricked into accessing a fraudulent website (), which posed as the legitimate Trezor portal, and subsequently divulged their sensitive cryptocurrency seed phrase in an attempt to recover their account.
As the stakes rose, Tony found himself reverting to a primal response, slipping into either fight-or-flight mode. “I’ve witnessed my kids breaking into tears; my partner is left wondering what’s going on?” My mind went haywire. I naively entered my seed phrase directly onto a phishing website, sealing my fate.
In a flash, every penny intended for his retirement and his children’s education was siphoned out of his account.
“Tone admitted that he had made mistakes due to his hectic schedule, revealing a lack of careful consideration in his decision-making process.” As life had undergone significant changes since having children, I had become disconnected from the initial safety protocols surrounding my bitcoin investments.
Following my attempt to improve the style:
They had taken 45 precious bitcoins from me.
The theft had a profound impact on Tony, leaving him feeling traumatised and deeply offended for several months.
He once derived immense enthusiasm from fiercely advocating for his sons’ well-being, a passion that ultimately came at a great personal cost. “I’m clearly heartbroken, struggling to cope with the aftermath.”
MISERY LOVES COMPANY
Within days of losing 45 bitcoins to thieves, Tony confessed to KrebsOnSecurity that he sank into a vortex of despair, his anger and shame so overwhelming that he seriously contemplated taking his own life. One day, while searching online for signs that others may have fallen victim to Daniel’s phishing tactics, he stumbled upon Griffin’s post on Reddit regarding the phone number tied to his recent bitcoin theft.
Initially, Griffin and Tony were wary of each other, engaging in cautious communication over the course of two weeks before Griffin eventually decided to trust Tony after verifying his claims with an FBI agent who claimed to be working on the case. Investigations revealed a pattern: prior to individual bitcoin thefts, victims encountered fake Google safety alerts referencing the same bogus “Google Help Case ID” number.
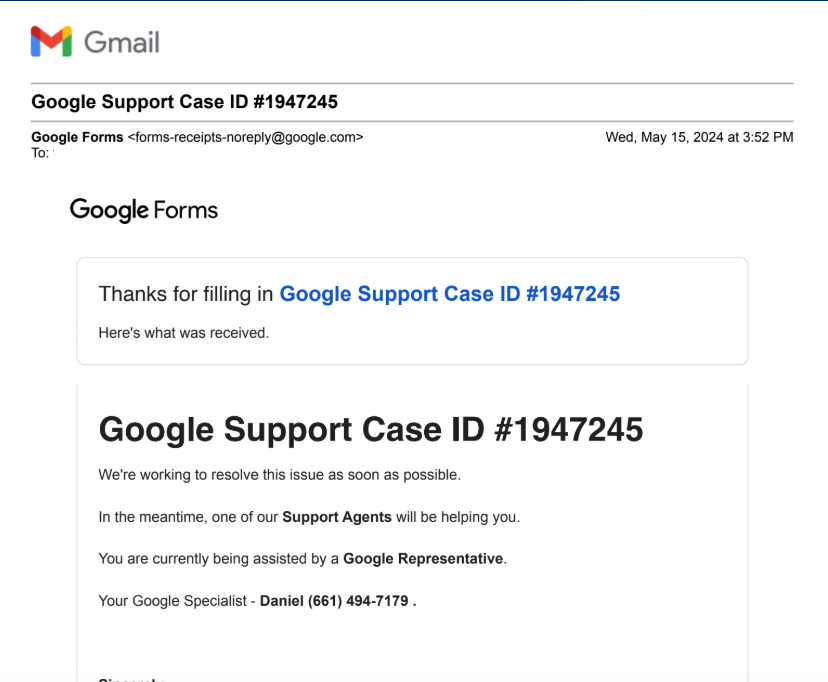
Adam Griffin and Tony claimed to have received the same Google Help Case ID number before their respective thefts. Each was dispatched via Google Forms, sending notifications directly from the google.com domain name.
Notably, Tony recognized and credited “Daniel from Google” after being interviewed by a podcast host who specialises in uncovering cryptocurrency fraud cases. The same persuasive voice that had convinced Tony to liquidate his significant cryptocurrency assets just days prior also attempted to deceive Junseth, who initially played along before recognizing the scam and exposing its illegitimacy after a few minutes.
Daniel warned Junseth that he was once a teenager, and had struggled alongside various fraudulent callers who all crossed paths years prior while playing an online game; additionally, he recently enjoyed a streak of consecutive Gmail account breaches that culminated in profitable cryptocurrency heists.
As Daniel enthusiastically assured Junseth during their May 7 podcast interview, which quickly gained widespread traction on social media platforms. With the current system, it seems that infractions are essentially going unpunished. Here are my findings:
“I operate a few legitimate side ventures, including businesses that allow me to direct all revenue through them.” If you ever encountered me in person, I would be an unassuming teenager carrying a backpack and ordinary attire, but beneath the façade lies a complex individual capable of stealing valuable possessions.
When initiating calls, Daniel’s team employs an automated bot that alerts potential targets about suspicious activity on their accounts, prompting them to press “1” to connect with a dedicated consultant. The course, as he defined it, inherently selects individuals who are more susceptible to his social engineering tactics due to their inherent inclinations. Although uncertain, it’s plausible that Daniel’s bot might have triggered the Google Assistant call prompting Griffin’s bitcoin theft.
Daniel informed Junseth that he and his accomplices had successfully executed a $1.2 million heist, which was currently pending settlement on the Bitcoin-based funding platform Swan Bitcoin. Promptly, Junseth informed the CEO of Swan that they had successfully detected the $1.2 million suspicious transaction earlier that morning.
It appears that Daniel’s dissatisfaction stemmed from having his voice publicly broadcasted and his $1.2 million bitcoin heist compromised due to someone, allegedly Junseth, reporting the audio file to Soundcloud, its online host.
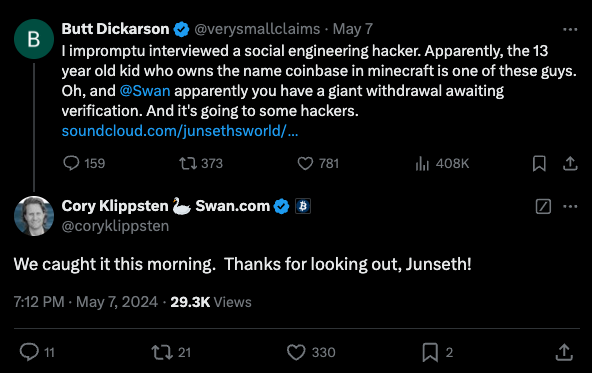
The grievance mistakenly claimed the recording featured copyrighted music, but this was quickly debunked when Junseth shared an early, unfinished version of the audio on Telegram, revealing no music was present in the background. Despite this setback, Soundcloud eliminated the audio file.
“All these firms are extremely wary of copyright infringement,” Junseth explained in a conversation published in May 2024, which offers several key takeaways from his discussion with Daniel.
“It’s puzzling that copyright infringement claims often lead to content being taken down, as if the mere accusation is enough to silence the accused,” Junseth explained. When dealing with a SoundCloud copyright claim, a crucial aspect of disputing the infringement is providing thorough documentation, including your property rights information, as explicitly stated in the platform’s guidelines: “This may be shared with the individual making the copyright declaration.”
AFTERMATH
Daniel explained that if a potential victim’s Google Authenticator is not synced to their Google cloud account, scammers cannot easily pivot into the affected individual’s accounts at cryptocurrency exchanges, as seen in Griffin’s case.
By default, Google Authenticator synchronizes all one-time codes with a user’s Google account, implying that if an unauthorized party gains access to the account, they can subsequently access all generated codes, compromising security.
To modify this setting, access Authenticator on your mobile device, navigate to your profile icon, and then opt for “Use without an account” from the dropdown menu. When disabling this feature, it is advisable to store your settings securely and keep them in a reliable location.
You may also consider transferring Google Authenticator to another mobile device that you control. If you disable cloud syncing and lose your primary mobile device with the Google Authenticator app, regaining access to your account might prove challenging or even impossible if you become locked out.
When Griffin consulted KrebsOnSecurity, he expressed surprise that it was straightforward for hackers to compromise his account and exploit numerous Google services.
“He acknowledged that he likely made mistakes, but also believed Google could have done a much better job of protecting people.”
According to KrebsOnSecurity, Google indicated that the potential phishing attack may have targeted a “very small group of people”, possibly confirming the scope of the campaign.
The company issued a statement highlighting its awareness of targeted efforts to disrupt their operations, stating unequivocally that genuine Google representatives will never initiate contact with users.
“While social engineering attacks continually adapt and evolve, our team remains committed to staying ahead by investing in innovative tools and technologies, as well as collaborating with our clients to collectively anticipate and outmaneuver emerging threats.”
Without disclosing their true identities, Griffin and Tony claim that they initiate conversations with individuals masquerading as representatives from Google or various cryptocurrency entities, seeking to acquire “account safety” assurances.
As Tony explained, “You become a mere checkbox item, perpetually cycling through the same worn-out lists.”
For several months following his traumatic experience, Griffin found himself naively accepting every fraudulent cryptocurrency scheme that came his way, indulging in a futile attempt to coax the perpetrators into revealing their true identities. Although his provocative remarks had initially sparked a slew of scams, he eventually ceased posting after one particularly menacing scammer began making personal threats against him.
Despite hindsight suggesting otherwise, Griffin conceded he probably made a mistake by recording lengthy discussions with those individuals, admitting that antagonizing cybercriminals who already possessed intimate knowledge of his digital footprint wasn’t an astute move. When discussing someone’s personal life, I was approached by a stranger who later confided in their friend that they intended to reveal my identity and engage in harmful activities against me. My FBI liaison subsequently cautioned me against further engaging with that particular group.
Sound recommendation. Is being forced to hang up every time someone calls due to a couple of potential safety risks with one of your accounts? While many individuals prioritize digital security, they often grossly underestimate the evolving threat of phone-based phishing attacks, putting themselves at risk by doing so.
When unsure: . If you respond to most scam calls in ways other than simply hanging up, looking into the suspicious number, and reaching out to the entity claiming to call, you may be preparing yourself for an expensive and embarrassing learning experience.
Please verify your email credentials. Ensure the adoption of a prolonged, intricate passphrase for your email address, exercising utmost caution to avoid utilizing any passphrase previously employed elsewhere – not even a modified version of a prior password.
Ultimately, leveraging the most robust multi-factor authentication methods available is highly recommended for optimal security. For Google Accounts, such as Gmail, several features have been implemented to effectively resist phishing attacks. For Google customers holding significant amounts of cryptocurrency, the safest option is Google’s Crypto custody solution, a free program that integrates advanced account security measures to safeguard your assets.

