A week after their son’s arrest, the parents of the 19-year-old accused of orchestrating an unprecedented $243 million cryptocurrency heist found themselves in a bizarre and unsettling situation: they were carjacked while house-hunting in a brand-new Lamborghini. According to prosecutors, the family was briefly held captive by six young men from Florida, who had travelled with a flawed plan to kidnap the parents in an attempted ransom demand.

Picture: ABC7NY. youtube.com/watch?v=xoiaGzwrunY
As dusk descended on August’s sweltering afternoon, On February 25, 2024, in Danbury, Connecticut, a married couple in their 50s found themselves at the center of an unusual incident when they drove a brand-new Lamborghini Urus (temporarily registered, according to investigators) and were deliberately rear-ended by a Honda Civic.
As they observed, three males emerged from a van that had been trailing the Honda, and immediately began attacking the couple and coercing them into the vehicle. Native law enforcement officials gave chase after observing the van speeding away from the scene, primarily to investigate the abandoned vehicle that had been involved in a crash a short distance down the road.
Detectives found the pair restrained in the immobilized vehicle, their arms and legs bound by duct tape, the victim displaying visible signs of brutal assault, with evident bruises and injuries consistent with having been struck by a baseball bat. Within hours of the kidnapping, Danbury police swiftly apprehended six male suspects, ranging in age from 18 to 26 and hailing from Florida. Additionally, they managed to recover the abandoned Lamborghini from a wooded area.
A PDF file was submitted on September The prosecutor presented a stark contrast between 24 lives lost and six male perpetrators, deliberately withholding specific details about the victims, citing only their identity as a married couple from Danbury, abbreviated by the same initials. Despite this, prosecutors in Connecticut revealed that their attention was instead piqued by the notion that the alleged co-conspirators thought the victims’ son possessed access to significant amounts of digital currency.
The camaraderie that developed among the Miami males was rooted in their shared experiences and sense of belonging, which fostered a deep-seated satisfaction and contentment within their tight-knit group? Was South Carolina’s son burdened with digital currency? About seven days prior to that momentous day, circa August In a sophisticated phone-based phishing attack, a group of cybercriminals, reportedly including the victim’s own son, defrauded a resident of Washington, D.C., out of approximately $243 million worth of cryptocurrency.
The investigation, led by a renowned expert in cryptocurrency crimes, meticulously revealed how the heist unfolded and ultimately exposed by the culprits themselves.
The publication by ZachXBT featured a transcript from a Discord chat session conducted by one of the participants in the $243 million heist, with the notable detail that two individuals involved inadvertently revealed their usernames for the Microsoft Windows PCs they used during the chat.
The username leaked through the chat was reportedly. In a development echoing ZachXBT, authorities have identified a 19-year-old suspect from Danbury who allegedly uses the pseudonym “Z.” Although he may go by one alias, footage reveals him using another, reportedly “S.” According to reports, Swag was allegedly involved in orchestrating the early stages of the cryptocurrency heist, gaining unauthorized access to the victim’s Gmail and iCloud accounts.
A screenshot was taken during a video screenshare initiated by a member in the Discord voice chat who utilized the Windows username “Veer Chetal”. Picture: x.com/zachxbt
On the same day that ZachXBT disclosed his discoveries, a statement was released in Washington D.C. Charging two individuals, whom he had identified as being directly involved in the heist, according to his testimony. Prosecutors accuse two individuals, 20-year-old Miami resident and 21-year-old Los Angeles resident, of conspiring to steal and launder more than $230 million in cryptocurrency from a victim in Washington, D.C. The indictment suggests that Lam and Serrano received assistance from unidentified accomplices.
According to sources, Lam and Serrano allegedly utilized the illicit cryptocurrency funds for a lavish lifestyle, indulging in international travel, high-end nightlife, luxury vehicles, premium timepieces, exquisite jewelry, top-tier handbags, and opulent rentals in Los Angeles and Miami.
Investigating the diverted funds, ZachXBT found that Wiz held a significant portion of the stolen assets, with additional insight gained from multiple recordings in which accomplices referred to him as “Veer” in audio and chat communications.
“A cluster of cryptocurrency addresses linked to each Field/Wiz transactional entity garnered more than $41 million in transactions from two exchanges within a short period, with funds primarily allocated towards high-end purchases through luxury goods dealerships to acquire vehicles, timepieces, fine jewelry, and designer attire,” ZachXBT noted.
KrebsOnSecurity reached out to Veer Chetal for comment, as well as to his parents. The status of this story’s update will be determined once anyone from the Chetal family provides a response. Although Veer Chetal’s name has surfaced in various investigations and speculations, he remains uncharged by the authorities, with no formal allegations brought against him to date.
According to a private Catholic high school in Danbury, Veer Chetal successfully completed a unique pre-professional program in 2022, under the guidance of certified Harvard undergraduate instructors. He learned how to build a case, write persuasive papers, and navigate the path to law school. In an interview, class of 2024 student Veer Chetal credited the Harvard program with his decision to pursue a career in law.
It remains ambiguous as to which Chetal family member procured the 2023 Lamborghini Urus, boasting an initial price tag of approximately $233,000. Sushil Chetal, Vice President at the funding financial institution, claims.
Multiple supposed accomplices to the $243 million heist demonstrated a striking pattern of excessive spending in the aftermath, suggesting a possible link between their financial outlays and the massive robbery. Zach XBT’s publication reveals his alleged misuse of pilfered funds, lavishly spending them on more than 10 vehicles, opulent real estate, and extravagant excursions with friends on chartered flights. He allegedly squandered vast sums—estimated at $250,000 to $500,000 per night—at exclusive clubs in Los Angeles and Miami.
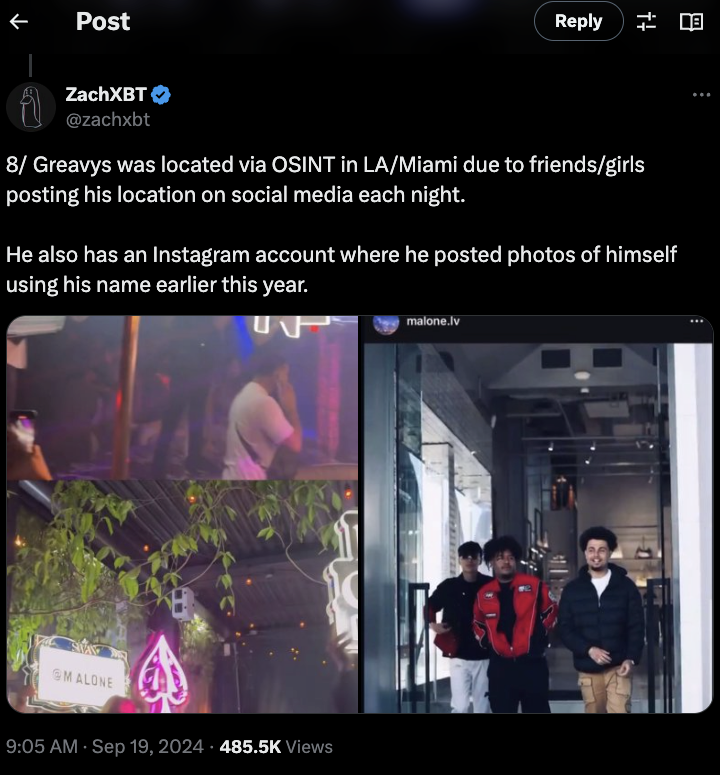
In this photograph taken from beneath, Lam/Greavy, the individual on the left, wears sunglasses. The duo is snapped stepping out of a high-end boutique, its opulent wares no doubt tempting them with their sleek designs and premium materials. Picture: x.com/zachxbt
In Miami, where a large rented waterfront dwelling stood, Malone and Serrano had been arrested across time. A local news outlet spoke to a neighbour of the household’s residents, who revealed that the property is currently hosting an extravagant bash, complete with a procession of high-end luxury vehicles lining the street – each bearing temporary licence plates.
A video surfaced showing Wiz at a Miami nightclub earlier this year, whereupon they were spotted dancing to chants while brandishing a lit-up sign reading, “I win everything.”
The investigation suggests that all suspected individuals involved in the high-profile cyber heist, and likely some of those implicated in related carjacking incidents, have ties to Finsta, a network of criminal-focused online forums that enables seamless coordination among its members.
In some cases, The Com serves as a platform where cybercriminals showcase their illicit accomplishments, flaunting their notoriety within the community or diminishing the reputation of others in a bid for dominance. Professional cybercriminals within the esteemed Com group continue to bicker over the distinction of executing the most daring digital heists and accumulating the largest haul of illicit cryptocurrencies.
As usual, members of The Com exploit and plunder their unsuspecting prey for financial gain, but in a surprising twist, they now seek to reclaim pilfered funds from their cybercrime counterparts – often through methods that have unintended consequences.
In 2022, a Miami-area man was shot twice while parked in his bright yellow Corvette in the city’s trendy Design District, one of six males arrested as part of a carjacking and extortion plot gone awry. According to Diaz, his attention was primarily drawn to the jewelry he was wearing, specifically noting it as “fairly expensive.”
According to KrebsOnSecurity, a pseudonym known as “” was allegedly used by Diaz in Telegram chat groups focused on pilfering cryptocurrencies. Prior to being caught, Pantic had earned notoriety by participating in several smaller-scale cybercrimes, using the majority of his ill-gotten gains to fund his extravagance, including a fondness for high-end fashion and luxury jewelry.
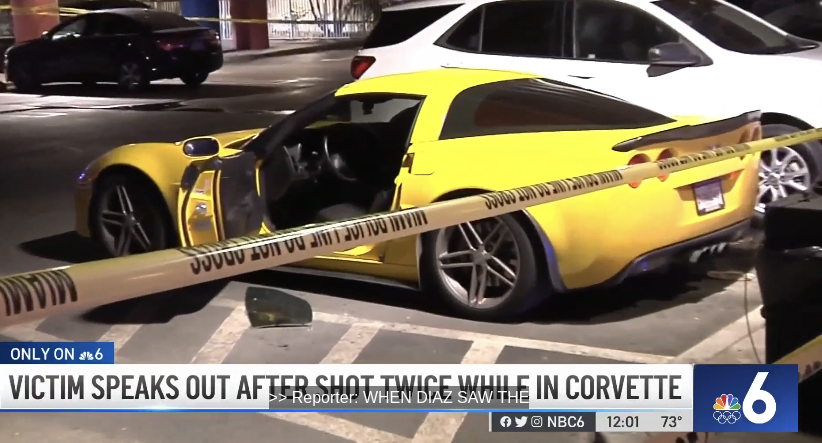
The Corvette in which Diaz was seated at the time of his shooting in 2022? Picture: NBC 6, South Florida.
In earlier years, Diaz suffered the humiliating ordeal of being “doxed,” or publicly exposed as Pantic, with intimate details about his personal life and family disseminated through a notorious online forum notorious for its malicious intent, frequented by supporters of The Com. The purported justification for Pantic’s doxing was thoroughly vindicated by multiple Com associates: Pantic had shockingly held up two close acquaintances at gunpoint, including one who recently succumbed to a drug-related death.
Prosecutors claim that the audacious daytime carjacking was orchestrated and financed by 23-year-old Miami resident Borrero, who had a prior arrest record in Miami dating back to 2022.
Six Miami males are charged with multiple crimes, including first-degree assault, kidnapping, and reckless endangerment; five of the suspects are being held on a $1-million bond. The suspect facing charges of reckless driving and resisting arrest can potentially be held accountable for their actions, with a bond set at a substantial $2 million to ensure their appearance in court. Lam and Serrano have been formally accused of conspiring to commit wire fraud and laundering money.
While cybercriminals come from diverse socioeconomic backgrounds, many advanced cryptocurrency thieves often possess higher educational attainments and come from relatively affluent families. These individuals aren’t pilfering food to simply put plates on the table; they’re driven by a desire to accumulate the trappings of sudden affluence and subsequently brag about their nefarious exploits to an audience on The Channel.
It’s not uncommon for individuals within this particular group to flaunt their alleged wrongdoings by drawing attention to themselves, effectively expediting the legal consequences that come with such reckless behavior. As the investigation into the $243 million heist unfolds, the narratives of the young men allegedly involved begin to mirror those of their fictional counterparts in a compelling tale of unexpected twists and turns.
Ortiz’s Instagram feeds flaunted extravagant lifestyles, featuring videos of himself and accomplices boarding private jets and reveling in LA nightclubs alongside scantily-clad women holding large placards bearing their coveted “OG” usernames – highly sought-after, single-letter social media handles pilfered or purchased from unsuspecting owners.
Ortiz stands out as the first person convicted of SIM-swapping, a serious crime involving the exploitation of insider connections or compromised employee accounts to hijack a target’s phone number and redirect it to a device controlled by the attackers. Without there being additional measures in place to secure the authentication process, the attacker can potentially intercept any password reset hyperlinks, as well as one-time passcodes dispatched via SMS or automated voice calls.
As mobile carriers intensify efforts to safeguard personal accounts, crypto criminals are finding it increasingly difficult to execute SIM-swaps and pilfer enormous sums of cryptocurrency. Despite its reputation as a somewhat questionable tactic, tricking people over the phone remains an impressively effective way to get what you want.
According to reports citing ZachXBT, fraudsters behind the $243 million heist first breached the cryptocurrency exchange’s private accounts by posing as Google Assistant using a fake phone number. Attackers further masqueraded as account support representatives at the cryptocurrency exchange, falsely alleging that the target’s account had been compromised.
The goal was socially engineered over the phone to trick victims into resetting their multi-factor authentication and transferring Gemini funds to a malicious account. ZachXBT alleges that the attackers coerced the victim into sharing their screen, which ultimately led to the unauthorized disclosure of their private keys.

