As the proliferation of cloud-native technologies continues to accelerate, containers and Kubernetes have emerged as the cornerstone of modern software implementations, revolutionizing the way applications are designed, deployed, and managed. Microservices-based containerised workloads are significantly simpler to scale, even more movable, and resource-efficient. Organizations can seamlessly deploy advanced AI and machine learning applications across diverse compute environments using Kubernetes, leading to significantly enhanced operational efficiency at scale. With this
As cloud-native technologies continue to gain widespread acceptance, containers and Kubernetes have emerged as the linchpin of contemporary software implementations. Microservices-based container workloads simplify scaling, become even more portable, and optimize resource utilization. With Kubernetes orchestration in place, organisations can seamlessly deploy advanced AI and machine learning applications across diverse compute resources, thereby significantly enhancing operational efficiency at scale. As software architecture evolves to incorporate containerized environments, there is a pressing need for intrinsic, granular security measures and in-depth visibility? However, the transient nature of containers poses significant challenges to achieving these goals. Where is Azure available?
We’re thrilled to announce the general availability of Superior Container Networking Providers, a cloud-native solution designed specifically to enhance security and visibility in Kubernetes and containerized environments. Superior Container Networking Providers specializes in delivering seamless, integrated solutions that enable you to maintain robust security postures and gain valuable insights into your network traffic and application performance.
By leveraging containerization, you can ensure both the security and performance of your applications, allowing you to confidently deploy and scale your infrastructure while meeting your reliability and efficiency goals.
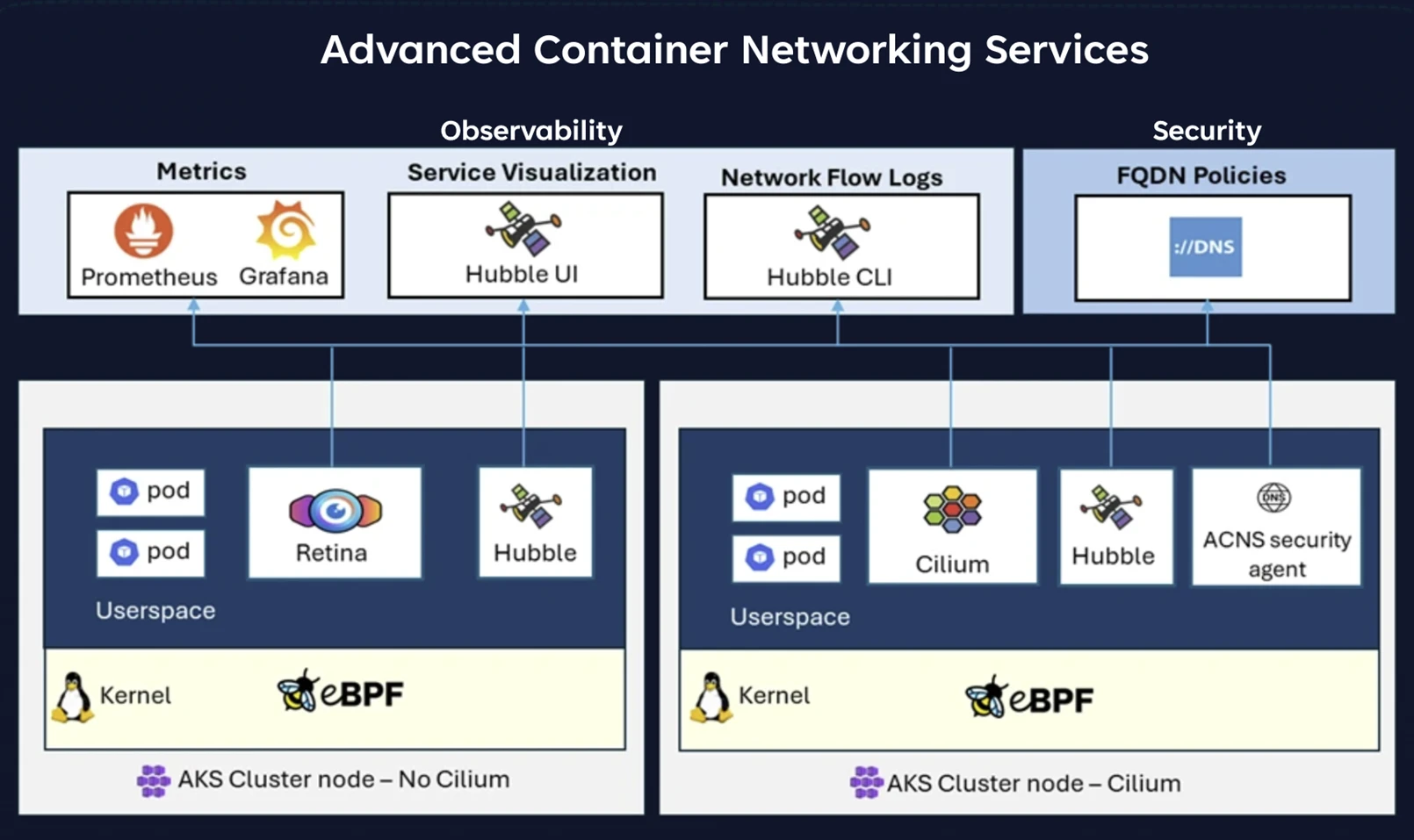
Let’s examine the container community safety and observability features of this release.
Container Community Observability
While Kubernetes excels at orchestrating and managing cloud-native applications, a critical challenge remains: How can we gain meaningful insights into the interplay between multiple cloud providers? Monitoring community visitors to microservices, assessing the effectiveness of those efforts, and grasping interdependencies between components are crucial for ensuring overall reliability and safety? Without this level of perception, the risk of undiagnosed inefficiencies, outages, and potentially hazardous situations escalates significantly.
To gain a genuine understanding of your microservices’ performance, you need more than just basic cluster-level metrics and digital network logs. To achieve comprehensive community observability, a combination of detailed community metrics is essential, accompanied by in-depth views at the node, pod, and Domain Name System (DNS) levels. Metrics enable clusters to pinpoint bottlenecks, troubleshoot issues, and track the overall health of each individual service.
Superior Container Networking Providers offers bespoke observability solutions specifically designed to address the unique challenges of Kubernetes and containerized environments, ensuring seamless performance and visibility across complex architectures. Our container networking provider delivers real-time, granular insights across multiple levels – nodes, pods, TCP, and DNS – ensuring no aspect of your network remains undetected or overlooked. These key metrics are crucial for identifying efficiency bottlenecks and addressing community concerns before they impact workloads.
- These metrics provide valuable insights into visitor volume, packet loss rates, connection diversity, and more. by node. Metrics are stored in Prometheus format and can be visualized in Grafana for easy analysis.
- Superior Container Networking Providers leverages Hubble’s metric-gathering capabilities in tandem with Kubernetes context, including pod identifiers and namespace information, thereby enabling the precise identification of network-related issues at a finely grained level? Metrics track visitor quantities, dropped packets, TCP resets, Layer 4/7 packet flows, and more. Additionally, there are DNS metrics that effectively mask DNS errors and unresponsive DNS requests.
- By capturing movement logs, organizations gain valuable insights into their workload’s communication patterns, thereby facilitating a deeper comprehension of how microservices interact and collaborate with one another. Movement logs also facilitate responses to inquiries such as:
- Visitors’ circulation patterns can be effectively visualized using Hubble UI, which generates a comprehensive service-connection graph by analyzing circulation logs, allowing users to view real-time logs for a specific namespace.
Container Community Safety
One significant challenge in container security arises from the fact that Kubernetes, by its default configuration, allows unrestricted communication between endpoints, thereby creating excessive security vulnerabilities? Superior container networking providers, powered by Cilium and Azure CNI, enable fine-grained community insurance policies using Kubernetes identities to securely permit only authorized traffic and protect sensitive endpoints.
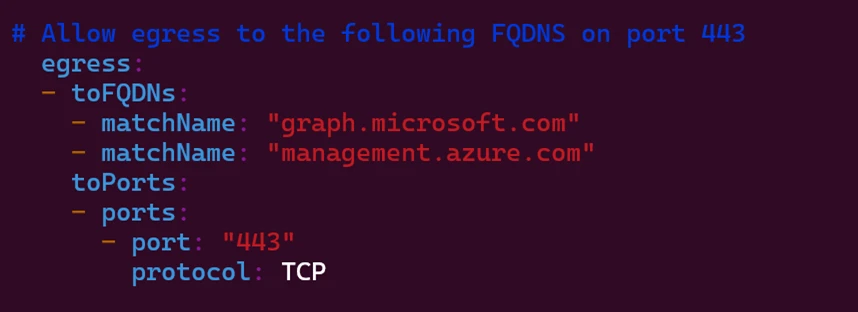
While traditional community insurance plans rely on IP-based protocols for managing external visitor access, external service providers frequently alter their IP addresses, thereby rendering these approaches obsolete. Implementing this requires careful consideration to ensure consistent workload safety within the cluster. Superior Container Networking Providers’ FQDN-based domain identification enables the insulation of network policies from IP address changes through their certified security agent DNS proxy functionality.
The organization’s Domain Name System (DNS) proxy implementation for FQDN filtering and safety agent configuration requires careful consideration to ensure seamless communication between internal services and external networks. To achieve this, administrators must carefully configure the DNS proxy server to forward all requests to specified FQDNs while blocking those deemed malicious or unwanted.
The key elements that comprise a successful strategy consist of both the data-driven approach and the security component. While mixed with Kubernetes clusters, they effortlessly integrate FQDN filtering, thereby enabling a more eco-friendly and manageable approach to managing external communications.
The Cilium agent is a critical networking component that operates as a DaemonSet within clusters, leveraging. The agent manages networking, load balancing, and community insurance policies for clusters of pods. When enforcing FQDN insurance policies on pods, the Cilium Agent directs traffic to the DNS Proxy for identification purposes, then updates its community coverage by leveraging FQDN-to-IP mapping data retrieved from the DNS Proxy.
In an Azure CNI-powered Cilium cluster, the DNS proxy, which is a component of the safety agent, operates as a DaemonSet with superior container networking capabilities enabled. The service accurately processes DNS decisions for pods, and upon a successful outcome, updates the Cilium Agent with fully qualified domain name (FQDN) to Internet Protocol (IP) mappings seamlessly.
By running the safety agent’s DNS proxy as a separate DaemonSet, alongside the Cilium agent in acns-security-agent, pods continue to have reliable DNS resolution even if the Cilium Agent experiences downtime or improves overall performance. Kubernetes’ `maxSurge` feature ensures that the DNS proxy remains fully operational and accessible during upgrades. This design guarantees uninterrupted community connectivity for critical buyer workloads, eliminating potential disruptions caused by DNS decision points.
Buyer adoption and situations
Several clients, both internal and external, successfully deployed Superior Container Networking Providers during its preview phase, paving the way for seamless adoption in diverse scenarios.
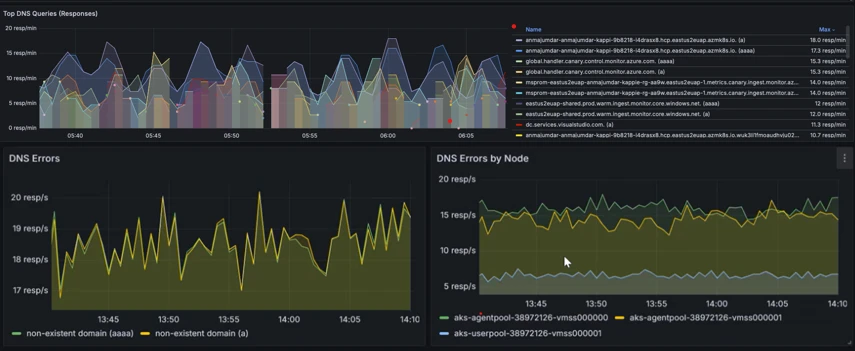
- Determining and rectifying software deterioration and Domain Name System (DNS) resolution delays through the analysis of DNS anomalies and performance indicators.
- Purposes and pods occasionally experience intermittent disconnections from various pods or external endpoints. Pod metrics provide cluster administrators with insights into dropped packet counts, TCP errors, and retransmissions, enabling them to identify and debug connectivity issues more quickly.
- Movement Logs: Debugging Community Connectivity Points
- By enabling cluster safety and bolstering insurance policies’ resilience when addressing IP-related adjustments, employing Cilium community insurance policies that leverage fully qualified domain names (FQDNs) instead of IP addresses significantly streamlines coverage management.
—
—
Conclusion
As you navigate the realm of cloud-native development, the imperative to harmoniously integrate safety and observability across every stratum of your infrastructure cannot be overstressed. With the necessary tools and mechanisms established, you’ll be able to relocate promptly, pioneer new initiatives more efficiently, and accomplish all of this with unwavering assurance that your tasks are comprehensively monitored and safeguarded.

