Is a forward-thinking safety initiative taken to identify and mitigate potential dangers in a community before they cause irreparable harm? To identify and mitigate one of these risks, safety professionals utilize advanced cyber threat-hunting tools. Sophisticated software programs leveraging advanced analytics, machine learning, and artificial intelligence identify anomalous patterns within a system’s network and endpoints, empowered by superior predictive capabilities. Utilizing cutting-edge techniques such as behavioral analytics, sample matching, statistical evaluation, and AI-driven machine learning modeling.
In light of the alarming statistic that a staggering 72% of global companies have fallen victim to ransomware attacks in 2023, an increasing number of organizations are now seeking effective cyber risk mitigation strategies for the year ahead.
Here is the rewritten text in a professional tone:
This report highlights the most effective cyber threat-hunting tools for 2024, scrutinizing their features, benefits, and limitations.
High risk looking options comparability
The table below outlines key risks associated with various investment options and how they are evaluated.

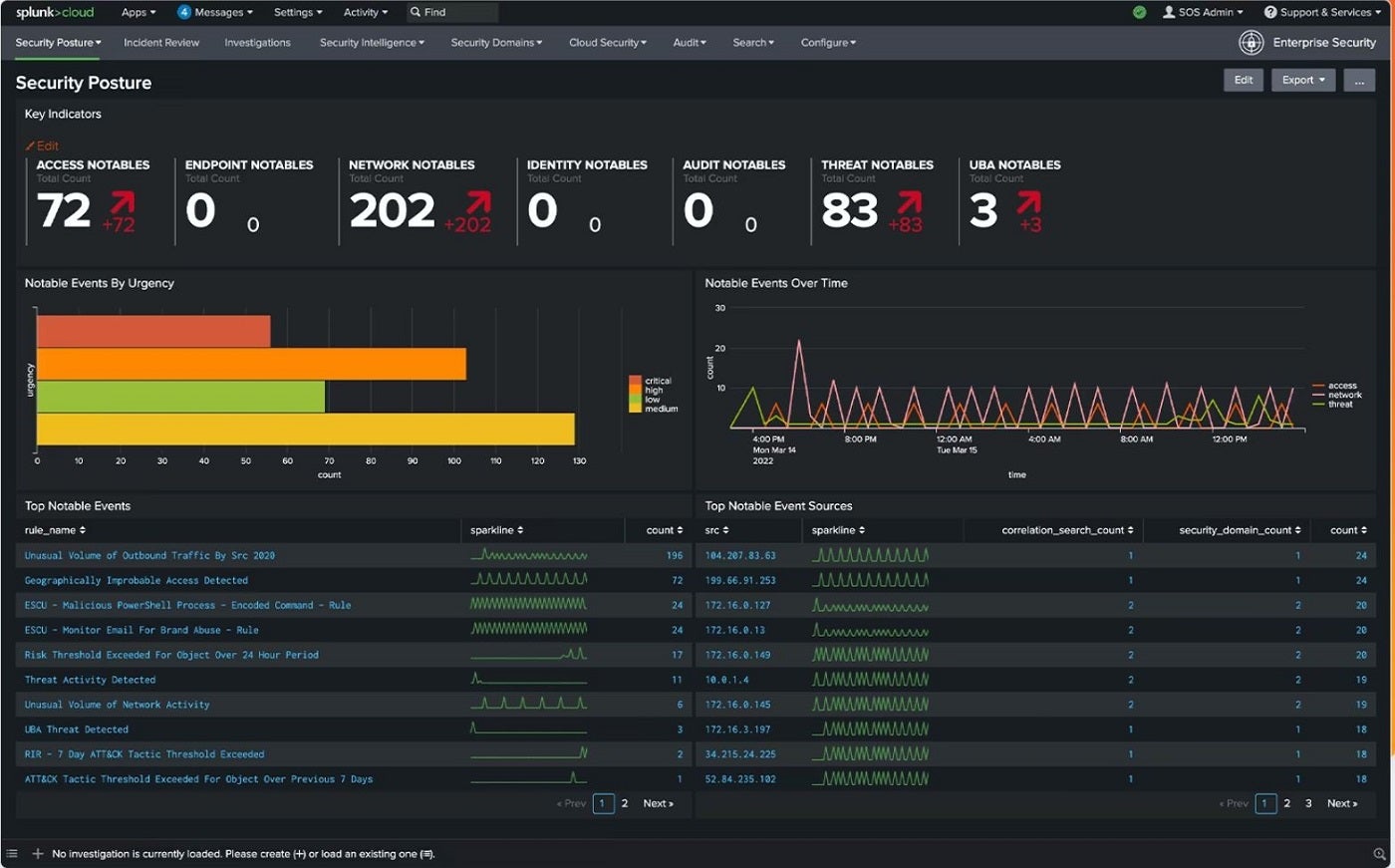
While Splunk is a powerful tool for analyzing and monitoring network traffic, it’s essential to consider other options when seeking the perfect general cyber risk-looking software. By offering cloud, on-premises, and hybrid solutions, Splunk stands out as a premier platform for preemptively addressing undetected security vulnerabilities. This innovative solution delivers comprehensive knowledge assessment capabilities, aligning with the elevated risk management demands of large-scale enterprises.
Through Splunk, safety groups can craft sophisticated threat-hunting queries, develop rigorous evaluation routines, and establish proactive automatic defensive protocols. A key strength of Splunk’s Security Information and Event Management (SIEM) solution lies in its swift threat detection capabilities, enabling organizations to identify potential security breaches quickly and initiate timely remediation efforts. With its advanced risk detection capabilities, the system boasts a robust array of approximately 1,400 detection frameworks, further enhanced by an open, extensible knowledge monitoring platform.
Why I selected Splunk
I chose Splunk for its advanced risk analysis features, providing swift identification and assessment regardless of risk magnitude. I’ve consistently demonstrated exceptional aptitude in effectively serving as a go-to expert, particularly in handling complex organizational structures, ensuring seamless integration with large-scale businesses. The solution’s effectiveness is evident through its versatility in cloud, on-premises, or hybrid deployment scenarios, coupled with an in-depth detection framework that offers robust threat intelligence.
Pricing
During this 14-day trial period, you’re afforded a chance to test. For pricing, contact the seller.
Options
- Multi-platform integration.
- Open, extensible knowledge monitoring platform.
- Real-time threat incident evaluation dashboard for swift and informed prioritization of emerging security concerns.
- What are the key performance indicators for effective risk management in your organization?
- Superior risk detection.
- Threat-based alerting.
Professionals and cons
| Professionals | Cons |
|---|---|
| Provides risk intelligence administration. | Pricing is ambiguous. |
| Are publicly available guidelines for mitigating risks in plain sight? | |
| Customizable occasion prioritization. | |
| Versatile deployment choices. | |
| Timely and agile delivery of high-quality safety information. | |
| Holistic risk assessment solutions, tailored to the evolving needs of large-scale organizations. |
VMware Carbon Black Endpoint: A Leading Choice for Offline and Hybrid Environments

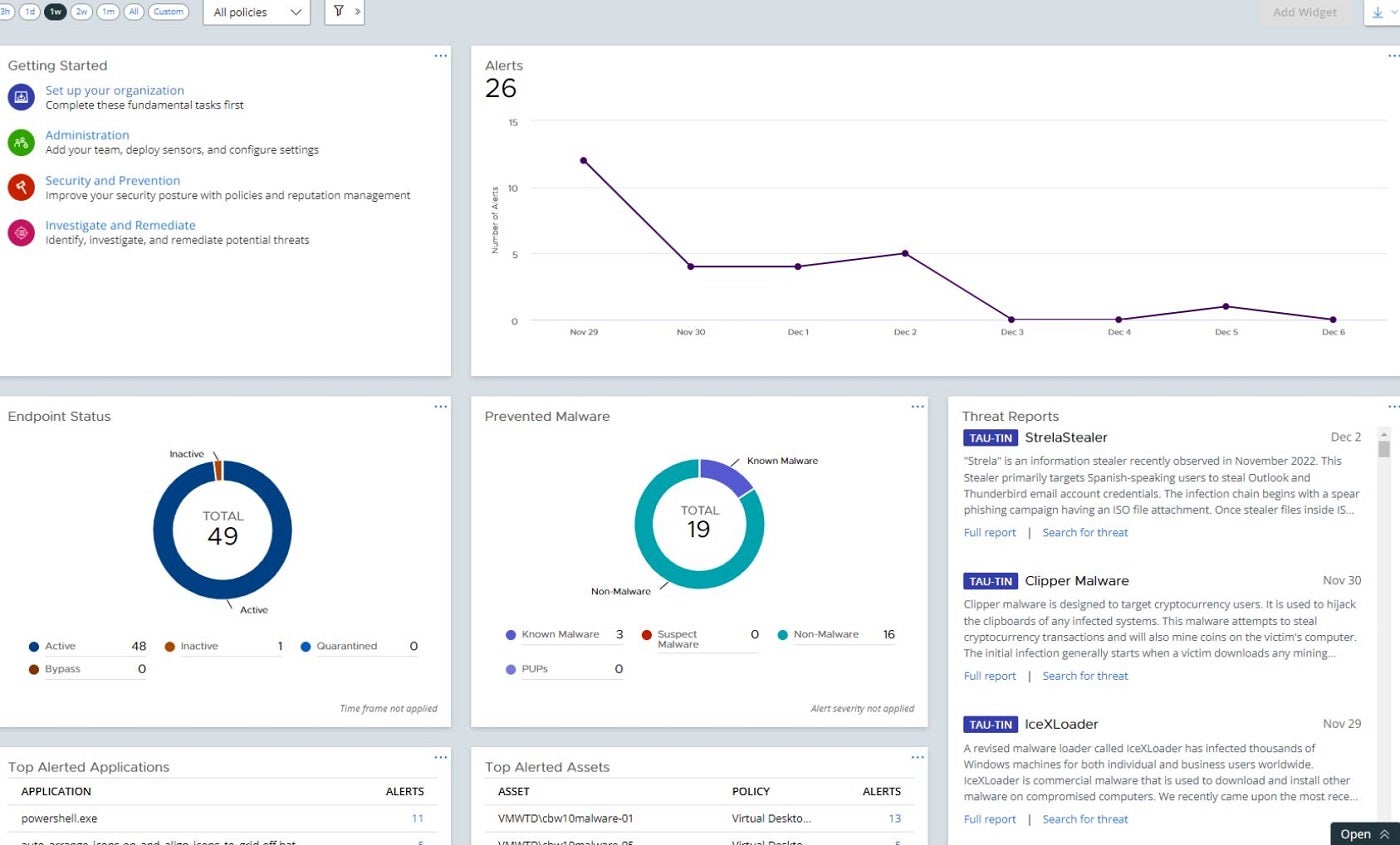
In environments that blend online and offline settings, I recommend leveraging the robust features of VMware Carbon Black Endpoint, a trusted solution developed by VMware. This comprehensive threat-hunting software combines cutting-edge technologies: behavioral endpoint detection and response (EDR), extended detection and response (XDR), and advanced next-generation antivirus (NGAV) capabilities. These options combine with their machine learning functionality to deliver superior risk scouting. The system continually gathers information, analyzes endpoint exercises, and monitors behaviors to identify potential superior threats.
Carbon Black Endpoint excels at harnessing the power of unsupervised machine learning models, enabling it to identify anomalous behavior that may indicate malicious activity throughout the cyber kill chain, thereby providing unparalleled visibility and threat detection capabilities. While our traditional approach may fall short on auditing and remediating capabilities, we confidently assert that organizations can still attain comprehensive EDR visibility across offline, hybrid, and disconnected settings.
I chose VMware Carbon Black Endpoint for several compelling reasons. Firstly, it offers unparalleled endpoint visibility and control, empowering me to detect and respond to even the most sophisticated threats in real-time. Secondly, its lightweight agent ensures minimal impact on system performance while maintaining a strong security posture. Additionally, its comprehensive feature set allows me to manage all endpoints from a single pane of glass, streamlining my workflow and improving overall security efficacy.
I’ve deployed VMware Carbon Black Endpoint on this checklist due to its comprehensive endpoint detection and response (EDR) visibility, which extends to offline, air-gapped, and disconnected environments.
Pricing
Contact the vendor to inquire about the price.
Options
- Subsequent-gen antivirus.
- What’s the key to effective Behavioral Endpoint Detection and Response (EDR)?
- Anomaly detection.
- Elevated endpoint and container visibility.
- Automated risk looking.
Professionals and cons
| Professionals | Cons |
|---|---|
| The seamless integration of our solution with widely used safety instruments such as Splunk, LogRhythm, and Proofpoint. | No traditional auditing and remediation processes exist in this conventional framework. |
| Helps compliance and audit options. | |
| Real-time endpoint visibility both within and beyond the boundaries of your organization’s network. | |
| Superior Predictive Cloud Safety. | |
| Mutual risk change between purchasers. |
CrowdStrike Falcon Overwatch: The Ultimate Solution for Superior Risk Management

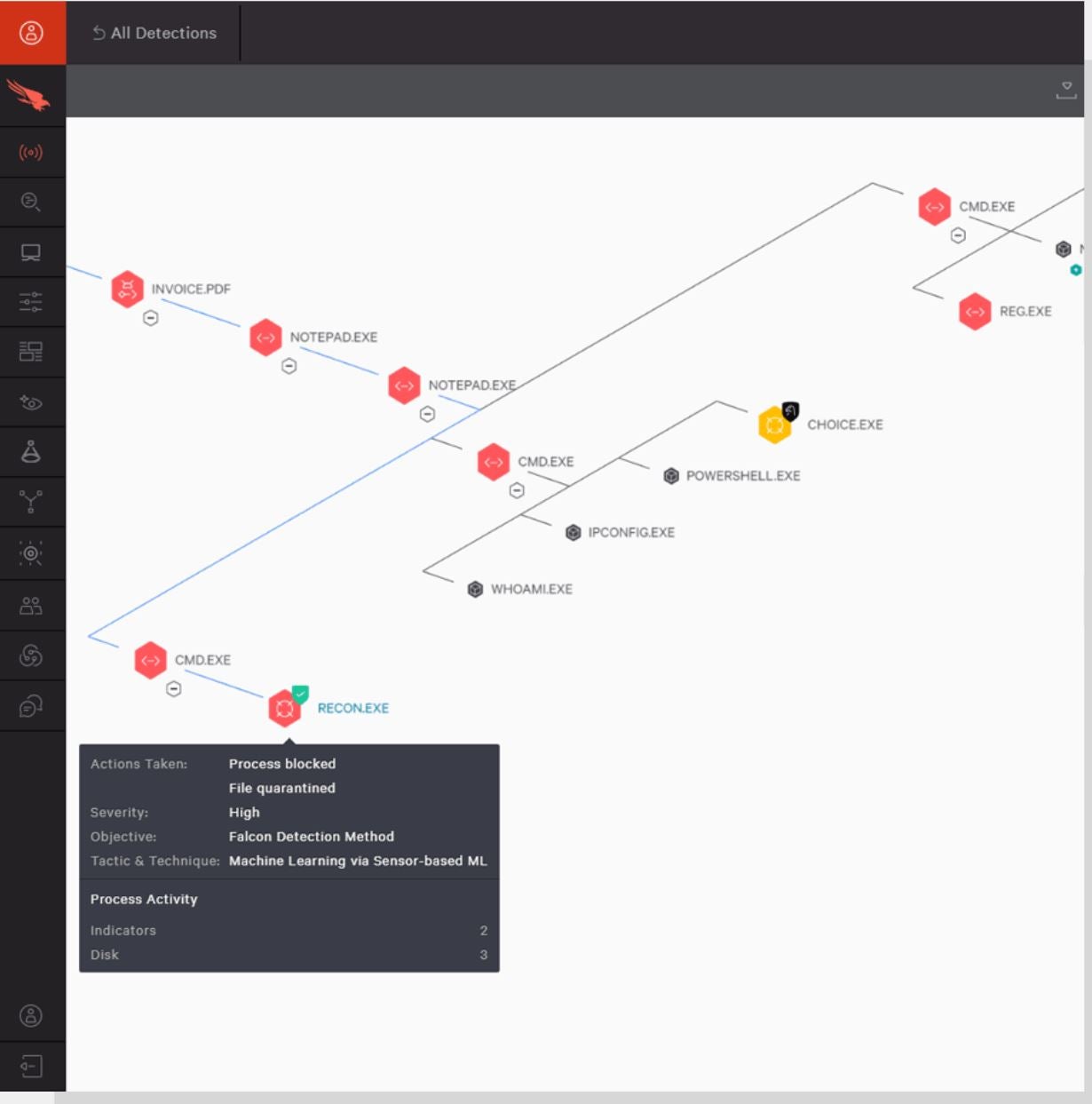
I recommend conducting a thorough risk assessment specifically, advising the implementation of CrowdStrike Falcon Overwatch for superior endpoint detection and response capabilities. CrowdStrike’s Overwatch leverages its proprietary SEARCH methodology to proactively detect, hunt, and neutralize emerging threats. Through its proprietary Overwatch technology, CrowdStrike aggregates vast amounts of data, combining cloud-based analytics with the expertise of in-house threat hunters and advanced risk intelligence capabilities to identify subtle patterns indicative of potential cyber intrusions or attacks. The system’s lightweight sensors continuously monitor and gather data from a vast array of endpoint events, storing it securely in the cloud for thorough analysis.
One notable feature of Overwatch that caught my attention is its risk graph, a tool that enables cyber analysts to pinpoint the sources of threats and predict how they may evolve over time. This could provide valuable insights into taking proactive steps to prevent further attacks from occurring.
I chose to implement CrowdStrike Falcon Overwatch as our security information and event management (SIEM) solution due to its comprehensive threat detection capabilities and ease of integration with our existing infrastructure. Additionally, the solution’s real-time visibility into cyber threats allowed us to respond swiftly and effectively to potential incidents, thereby minimizing their impact on our operations.
I selected CrowdStrike Falcon Overwatch due to its dedicated approach to proactively identifying high-risk threats and responding automatically, which stems from the integration of advanced Endpoint Detection and Response (EDR), Extended Detection and Response (XDR) capabilities, and proprietary technologies.
Pricing
The CrowdStrike Falcon Overwatch offers a 15-day free trial, with two plan options: Falcon Overwatch and Falcon Overwatch Elite. Obtain a quote from the vendor.
Options
- Superior EDR and XDR.
- Enhanced Visibility through Falcon’s USB Machine Management Solution?
- Automated risk intelligence.
- Menace Graph.
- Firewall administration.
Professionals and cons
| Professionals | Cons |
|---|---|
| Menace alerts are now bolstered by contextual relevance. | Exclusive access to Menace-looking and investigative training programs defines the Falcon Overwatch Elite customer experience. |
| Contains choices for managed service. | |
| Provides a 15-day free trial. | |
| Extensive Detection and Response Capabilities via XDR: Elevating Risk Mitigation to New Heights. | |
| Quarterly risk looking studies. |
SolarWinds Security Event Manager: Exceptional Choice for Centralized Risk Management and Compliance.

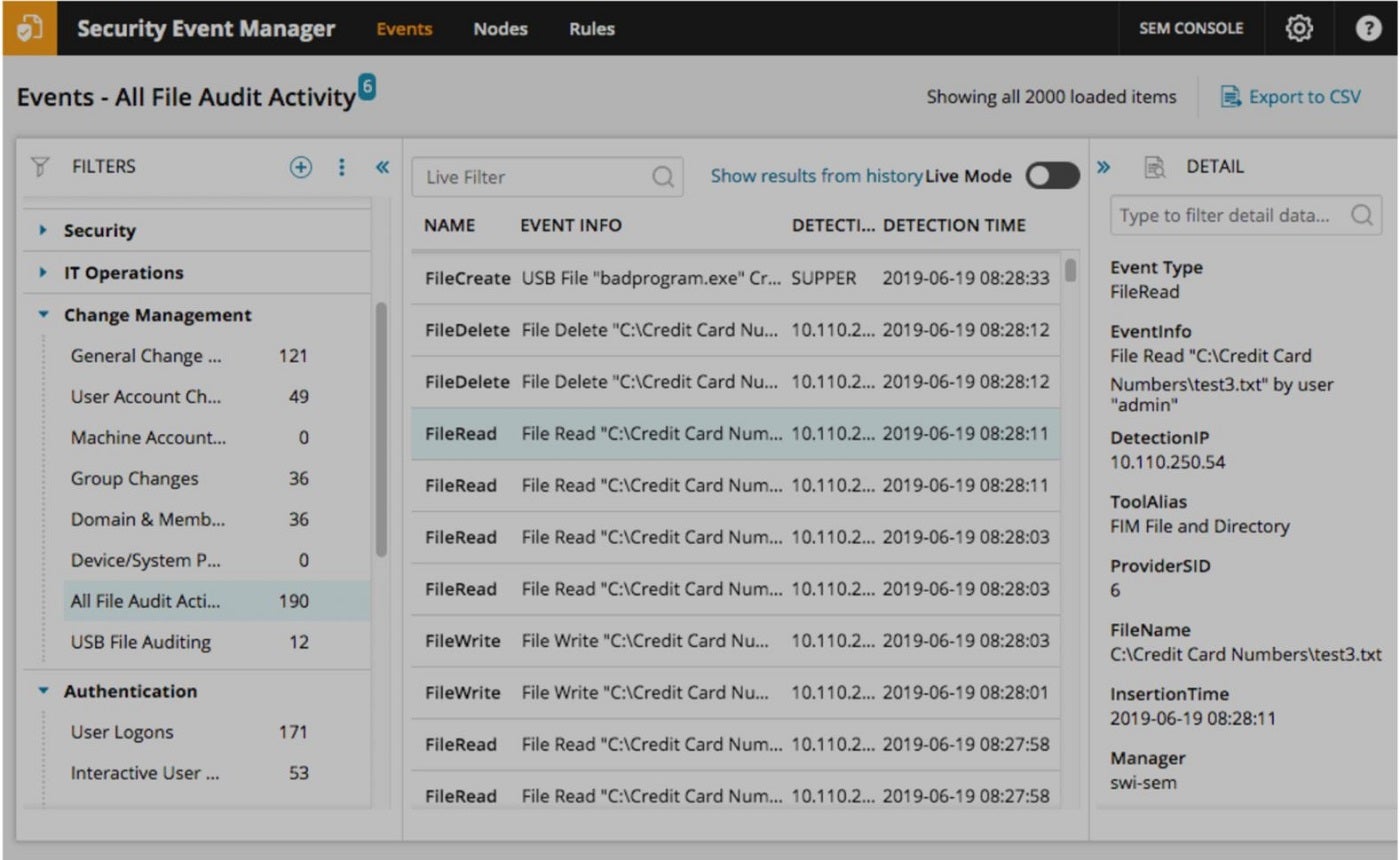
To streamline centralized risk management for our clients, I find that SolarWinds Security Event Manager proves highly effective. SolarWinds provides robust risk monitoring capabilities through a blend of real-time network performance metrics and intelligence garnered from diverse sources, including the Simple Network Management Protocol (SNMP) and log entries. SNMP-derived knowledge enables systems to gather insights on community devices, monitor efficiency metrics, and track critical factors in real-time.
Through rigorous parsing and analysis of log data, SEM systems are able to uncover patterns, identify anomalies, and detect potential security threats. SEM’s central hub is a standout feature that sets it apart from other search marketing tools. The system enables safety teams to aggregate, scrutinize, and respond to safety incidents triggered by diverse security technologies, such as firewalls, intrusion detection methods, and endpoint security measures.
I chose SolarWinds Safety Occurrence Manager because its comprehensive feature set enables me to streamline my incident management processes, ensuring swift response times and minimizing downtime.
I chose SEM for its centralized platform and effortless integration with diverse security technologies, enabling cohesive safety management. This facilitates a comprehensive understanding for safety experts, providing a bird’s-eye view of potential risks and intelligence gathering to identify vulnerabilities or possible weaknesses.
Pricing
SolarWinds Occurrence Supervisor offers both subscription-based and perpetual licensing options for customers. Request a personalized quotation from the vendor.
Options
- Constructed-in file integrity monitoring.
- Centralized log assortment and normalization.
- Built-in compliance reporting instruments.
- Superior pfSense firewall log analyzer.
- Advanced Persistent Threat Protection Software Solution.
Professionals and cons
| Professionals | Cons |
|---|---|
| Provides real-time community efficiency statistics. | Absence of cloud model. |
| Centrally monitored logon audits track and analyze security events to ensure optimal safety measures are in place. | |
| Enhance your network’s security with a powerful pfSense firewall log analyzer that offers real-time monitoring and swift troubleshooting capabilities. | |
| Provides enhanced visual awareness through seamless integration with diverse safety technologies. | |
| Provides meticulous analysis of log entries to significantly enhance risk identification capabilities. |
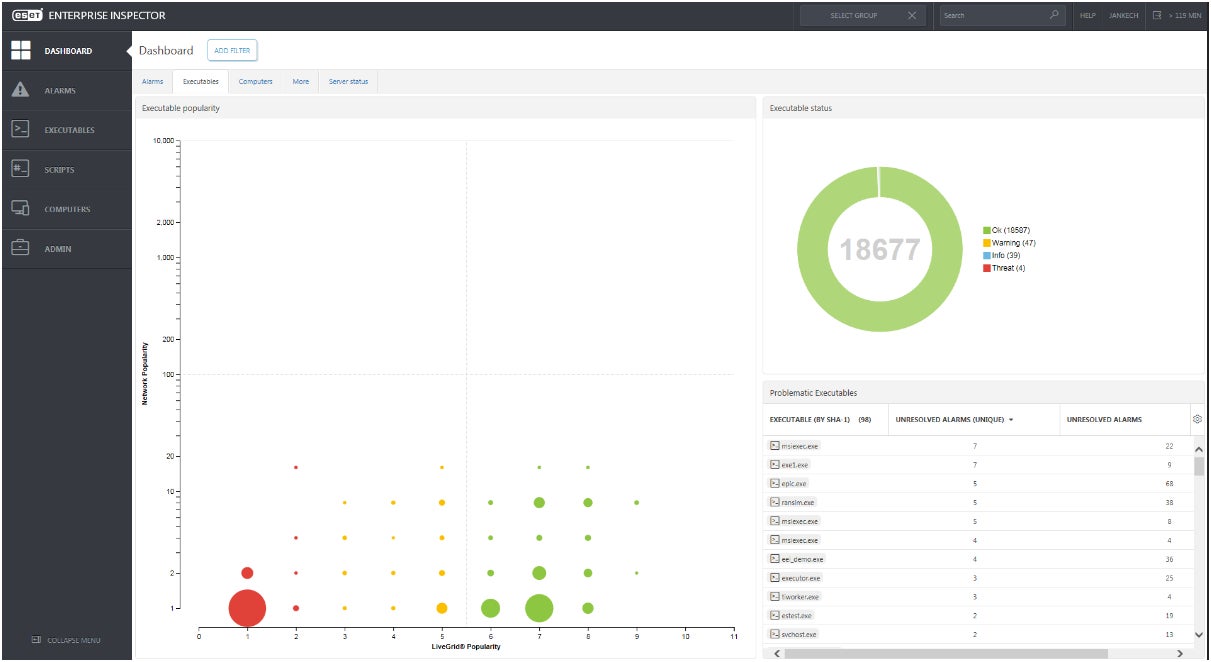
ESET’s Enterprise Inspector provides unparalleled visibility and control in detecting and mitigating tandem risks across your organization.

Are you seeking reliable partners and robust software to mitigate risks? Consider ESET Enterprise Inspector for comprehensive solutions. Enterprise Inspector is ESET’s Endpoint Detection and Response (EDR) solution, engineered to provide real-time visibility into endpoint data and uncover sophisticated, persistent threats as they emerge. The EDR’s ability to rescan entire occasion databases provides unparalleled flexibility, rendering it the ideal solution for retrospective risk analysis. By refining detection parameters, risk hunters can readily uncover novel indicators of compromise while querying the database.
ESET’s unique offering is its ESET Menace Searching service, seamlessly integrated with the ESET Enterprise Inspector. For organizations lacking dedicated resources or personnel to manage and mitigate cybersecurity risks, this solution is particularly well-suited.
Why I selected ESET Inspector
The ESET Inspector is added to this checklist due to its dedicated threat hunting service, which complements its ESET Enterprise Inspector EDR capabilities. While small companies may lack extensive IT or safety resources, they still require effective cyber risk management solutions to reap the benefits of robust security measures.
Pricing
Contact ESET’s Sales team to negotiate custom pricing and secure an accurate quote.
Options
- Habits and reputation-based detection.
- Automated risk looking capabilities.
- Will be accompanied by a devoted risk management service.
- Prevention of attacks takes precedence over potential harm.
- Customizable alerts.
Professionals and cons
| Professionals | Cons |
|---|---|
| Simply adjustable detection guidelines. | This could also be a significant drain on resources for older methods. |
| In cloud or on-premises deployment. | |
| Ideal for businesses with limited safety knowledge, this program provides a solid foundation in workplace risk management. | |
| Provides seamless integration with various ESET options to ensure a synchronized and cohesive response. | |
| Seamless deployment. |
Pattern Micro Managed XDR: A Game-Changer for Dedicated SOC Teams?

Are you seeking dedicated Security Operations Center (SOC) support? Consider Pattern Micro’s Managed Extended Detection and Response (XDR) solution for comprehensive assistance. Our comprehensive safety services ensure seamless 24/7 monitoring and evaluation, distinguished by its ability to integrate insights from diverse sources – including email, endpoint, server, cloud, workload, and network platforms.
I highly recommend Pattern Micro’s innovative approach, as it significantly improves threat visibility and provides a more comprehensive understanding of targeted attack trajectories. The system continuously monitors for signs of compromise or attacks, incorporating those provided by US-CERT and third-party advisories, thereby ensuring a proactive approach to risk mitigation.
Managed XDR provides dedicated support for Security Operations Center (SOC) teams, significantly reducing the time required to detect, investigate, and respond to threats. As part of the Pattern Service One suite, this offering comprises a range of premium assistance and incident response providers, thereby enhancing its overall value proposition across the product portfolio.
I was drawn to Pattern Micro Managed Extended Detection and Response (XDR) due to its comprehensive threat detection capabilities, enhanced security posture, and streamlined incident response.
I selected Pattern Micro Managed XDR for its round-the-clock support to empower Safety Operations Center teams, as well as its sophisticated threat-hunting features that significantly enhance the speed of threat detection and response.
Pricing
Pattern’s Micro Managed Extended Detection and Response (XDR) solution offers a complimentary 30-day trial period. Contact the seller for pricing.
Options
- Endpoint detection and response.
- 24/7 evaluation and monitoring.
- Superior risk intelligence.
- Cross-layered detection and response.
- Optimized safety analytics.
Professionals and cons
| Professionals | Cons |
|---|---|
| Professional-grade support services for SOC and IT security teams? | Lack of on-premises answer. |
| Ensures robust security measures for servers and email systems to safeguard against potential threats. | |
| Continuously seek out potential risks that could pose a significant threat to organizational success. | |
| Consisting of threats, the system robotically generates Indicators of Compromise (IoCs) to prevent future attacks. | |
| Produces timely risk alerts and comprehensive incident investigations. |
What’s the most effective way to ensure seamless risk management? Here’s a revolutionary concept: Heimdal Menace Searching and Motion Heart (HMSMH). This innovative solution empowers you to streamline risk mitigation with a single command, drastically reducing the complexity of your operations.

I’ve implemented mitigations with ease using Heimdal’s Menace Searching and Motion Heart tools. Heimdal’s risk assessment and detection capabilities empower SecOps teams and IT directors to equip themselves with the tools necessary for identifying and monitoring abnormal behavior across devices and networks, thereby ensuring proactive threat mitigation and optimal security posture. Leveraging its superior XTP engine, the Heimdall suite, and the MITRE ATT&CK framework, this platform visualizes related data associated to endpoints for network-level risk detection.
By leveraging danger scores and forensic evaluations, customers gain valuable insights that reinforce their comprehension of potential risks and threats. While I appreciate the ongoing scrutiny provided by the XTP engine’s strategic layer for risk identification and monitoring? This feature enables instant mitigation of detected threats with a simple, one-step command.
As an avid enthusiast of innovative technologies, I opted for Heimdal Menace, Searching, and Motion Heart due to their distinctive capabilities in safeguarding my digital experiences. The cutting-edge features offered by these tools enable me to detect and thwart potential threats, monitor system performance, and gain valuable insights into network activities.
With its seamless one-click implementation of core functions such as scanning, quarantining, and isolating threats, Heimdal’s robust capabilities truly set it apart – particularly when coupled with the insightful analysis provided by its innovative Motion Heart technology, enabling comprehensive incident investigation.
Pricing
Get a quote from the seller directly.
Options
- Future-generation antivirus, firewall, and mobile device management (MDM).
- Incident investigation and administration.
- Exercise monitoring and monitoring.
- XTP Engine and MITRE ATT&CK framework.
- Quarantine performance.
Professionals and cons
| Professionals | Cons |
|---|---|
| Provides a concise, centralized summary of identified threats. | Lack of accessible pricing information online. |
| Real-time risk monitoring and instantaneous alert notifications are provided. | |
| Provides real-time data for swift analysis and metrics. | |
| Single-command remediation is indeed feasible with the motion middleware. | |
| Unifies perspectives on intelligence, appearance, and reaction. | |
Cyber threat detection tools are critical components in today’s digital landscape, providing organizations with the necessary capabilities to identify and mitigate potential cyber attacks. Some key options include:
* Nmap: A widely used open-source network scanner that can be employed for reconnaissance purposes.
* Nessus: A powerful vulnerability scanner capable of identifying weaknesses on networks and hosts.
* OpenVAS: An open-source vulnerability assessment tool offering advanced scanning capabilities.
* Wireshark: A network protocol analyzer ideal for inspecting network traffic and identifying potential security threats.
These tools are essential in the quest to uncover cyber menaces, providing valuable insights that can aid organizations in their efforts to safeguard against cyber attacks.
By leveraging log evaluations, proactive risk assessments, and intelligence sharing, innovative risk mitigation solutions can differentiate themselves through a range of unique features not typically found in conventional safety monitoring tools. The following are essential features that every threat-hunting software should possess:
Information assortment and evaluation
Advanced analytics tools gather and aggregate massive volumes of data from diverse sources, including logs, events, endpoint telemetry, and community engagement metrics. Utilizing advanced analytics and machine learning capabilities, subtle trends and outliers are effectively identified. These professionals enhance their awareness of potential security breaches by thoroughly examining and analyzing alerts generated by both Security Information and Event Management (SIEM) systems and Intrusion Detection Systems (IDS), thereby refining their threat assessment skills. They scrutinise data garnered from firewalls, IDS systems, DNS logs, file archives, consumer feedback, antivirus software, and various security tools to derive a comprehensive understanding of potential threats and develop effective mitigation strategies.
Cyber threat detection: Anticipating and recognizing vulnerabilities.
This trait enables safety experts to uncover and meticulously explore a comprehensive body of knowledge gathered from diverse sources. The advanced search and query capabilities enable users to efficiently seek out, refine, and interrogate the available data. To optimize their searches, safety groups can tailor and refine their queries according to specific organizational requirements, extracting information such as time frames, unique IP addresses, user accounts, or types of actions. This characteristic’s significance lies in its capacity for both real-time assessment and historical data analysis; the former enables prompt identification of emerging threats through queries of live knowledge streams, while the latter uncovers previously overlooked incidents or patterns by examining past events.
Collaboration and intelligence sharing
While individual efforts may appear menacing, they often go unnoticed because the data collected and processed privately is inherently limited in its impact. Collaboration and intelligence sharing among organizations, safety groups, and business partners require seamless integration of sharable risk intelligence feeds within risk monitoring tools to achieve optimal results? The evolution of risk intelligence, tactics, techniques, and procedures enables a proactive approach to risk identification and mitigation across diverse organisational structures.
Behavioral evaluation
Systems utilizing menace-hunting instruments rely on the analysis of behavioral patterns to understand and interpret consumer and system behavior. Utilizing a combination of consumer and entity behavior analytics (UEBA), machine learning algorithms, and continuous monitoring, they leverage these methods to identify anomalies, provide contextual insights, and facilitate early risk detection. This characteristic further reduces false positives and optimizes proactive identification and swift response to potential security threats.
Automated response
This characteristic prioritises alerts primarily based on pre-defined standards, ensuring that critical or acknowledged threats receive swift attention. The solution comprises dynamic playbooks that leverage real-time data, seamless integration with leading safety orchestration platforms, and actionable responses that swiftly contain and isolate incidents, remediating affected consumer accounts while prioritizing critical alerts. Organisations can significantly reduce dwell time, streamline incident response processes, and ensure compliance with security policies while safeguarding their network and systems against evolving security risks and threats through the effective utilisation of automated responses.
To effectively identify and mitigate threats, you should consider a cyber threat-hunting software that offers advanced analytics, real-time monitoring, and actionable insights. Key factors to evaluate include scalability, ease of use, and integration with existing security tools. A solution that leverages AI-powered detection, customizable dashboards, and automated incident response can help optimize your organization’s threat posture.
To choose the ideal cyber threat-hunting software for an individual or organization, several factors must be considered, including personal or business objectives, how the software integrates with existing security infrastructure, and budget constraints. These seven instruments offer effective threat-hunting capabilities tailored to individual and enterprise requirements.
If you seek a dedicated threat hunting service in addition to the threat hunting answer, something like ESET Enterprise Inspector is your best bet. If you’re seeking a comprehensive solution integrating scanning, quarantine, and isolation alongside rigorous incident analysis, look no further than the Heimdal Menace Searching and Motion Heart for optimal results. While identical methods may apply to different instruments, each instrument has its unique approach to appearance and repair.
Notwithstanding the software’s potential, its true value hinges on seamless integration into a company’s existing infrastructure and robust security frameworks. When utilizing these tools, it’s crucial to assess their effectiveness within the unique context of your organization, taking into account its specific needs and obstacles.
Evaluate methodology
I evaluated various threat-hunting options, considering key aspects such as detection methods employed by different software tools, their respective remediation processes, integrations with existing technologies, and the level of personalized support provided by vendors. After aggregating information from diverse distributors’ websites, I conducted a comprehensive evaluation of various software solutions by consulting industry-leading sources such as Gartner to gain a deeper understanding of each application’s capabilities and limitations. I also considered the reputation of the builders and their standing in the industry.

