
Hackers are targeting outdated iterations of Rejetto’s HTTP File Server (HFS) to deploy malware and cryptocurrency mining software.
Researchers at AhnLab, a leading safety firm, warn that threat actors are leveraging a critical vulnerability, allowing unauthenticated execution of arbitrary code, posing a significant risk.
The vulnerability affects approximately 2.3 million instances of the software program across various versions. Rejetto cautions customers on its website that versions 2.3m (by) 2.4 are “harmful” and should no longer be employed due to a critical vulnerability allowing attackers to gain unauthorized control of users’ laptops, with a patch yet to be found.
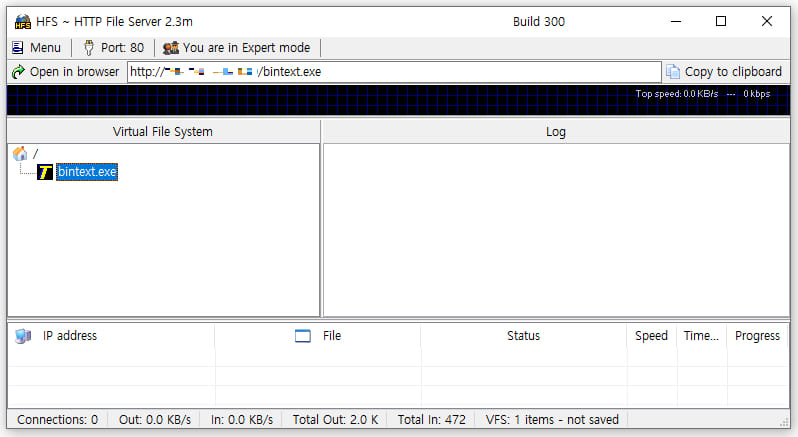
Noticed assaults
AhnLab Security Intelligence Hub has detected ongoing attacks targeting approximately 2.3 million users of the highly popular HFS model, which remains a favored platform for individual users, small group collaborations, educational institutions, and developers seeking to facilitate file-sharing activities across networks.
Due to the focused software program’s model, researchers assume attackers are leveraging CVE-2024-23692, a recently discovered vulnerability announced by Arseniy Sharoglazov in August and publicly disclosed in May this year.
The CVE-2024-23692 is a serious template injection vulnerability, allowing unauthenticated remote attackers to deliver a custom-crafted HTTP request and execute arbitrary commands on the impacted system without authentication.
Following the revelation, an array of proof-of-concept exploits suddenly became available. Across the timeline, the exploitation of oil in the wild commenced in accordance with ASEC.
Researchers assert that during the assault, hackers systematically compile information about the system, establish backdoors, and deploy a variety of malicious software, including malware.
Attackers utilise commands such as “whoami” and “arp” to gather information about the system and its user, identify connected devices, and subsequently devise their next moves.
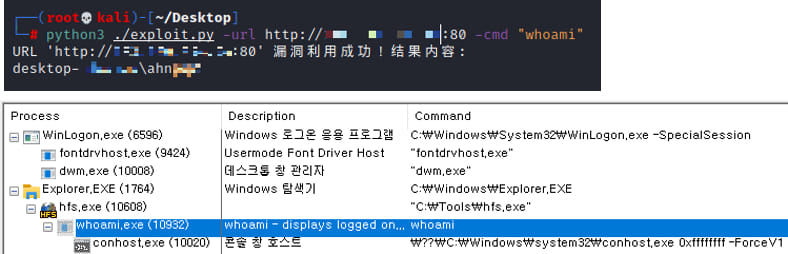
Attackers often discontinue the HFS process once they add a new user to the directors’ group, aiming to prevent other threat actors from exploiting this vulnerability.
During subsequent phases of the attacks, ASEC identified the installation of XMRig software for mining Monero cryptocurrency. Researchers are well aware that XMRig has been employed in a minimum of four distinct attacks, with at least one instance linked to a malicious threat actor.
Malicious payloads distributed to the infected laptop comprise:
- Deployed in tandem with XMRig to facilitate remote access and centralized control.
- Used for distant management and information exfiltration from compromised systems.
- A notorious backdoor linked to Chinese-speaking threat actors, utilized for sustained infiltration purposes.
- An information-stealing malware that leverages Amazon Web Services (AWS) infrastructure to exfiltrate sensitive data. The software captures screenshots, compiles data on desktop activity, and transmits this intelligence to a remote external command and control (C2) server.
AhnLab researchers have identified a need to improve their detection capabilities for assaults on over 2.3 million users of the HFS model. Due to the online nature of servers facilitating file sharing, it is inevitable that malicious hackers will actively seek out vulnerabilities to exploit, putting sensitive data at risk of compromise.
The latest version of the product, 0.52.x, despite being a downgraded variant, represents the most current HFS release from the developer to date. With a web-based interface that demands minimal setup, this iteration includes support for HTTPS, dynamic DNS, and authentication for its executive panel.
The corporation provides a set of indicators of compromise (IOCs) encompassing hashes for malware installed on compromised systems, IP addresses for attacker command and control servers, and download URLs for malware utilized in attacks.

